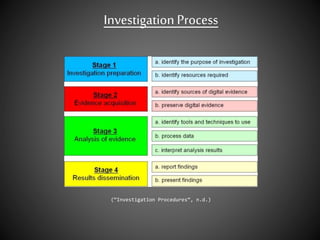
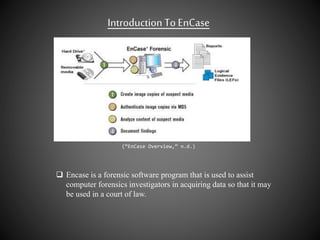
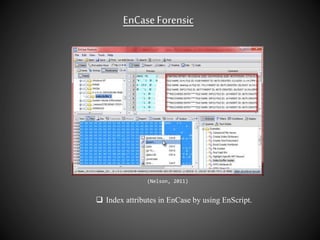
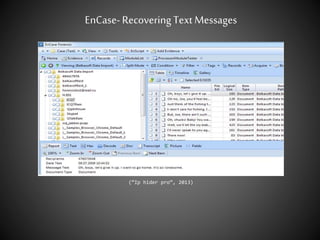
The document discusses the use of EnCase forensic software in criminal investigations. It describes how computer forensics has become important for investigating crimes involving technology. EnCase allows investigators to acquire digital evidence from computers in a way that is admissible in court. The document also briefly mentions indexing attributes in EnCase using EnScript and recovering deleted text messages.