The document describes the use of poem codes during World War II by Britain's Special Operations Executive to communicate secretly with agents. It explains the encryption process involving a pre-arranged poem and how to encode and decode messages using Morse code. The example provided illustrates these procedures using the poem 'Jabberwocky'.





![2. ENCRYPTION AT THE SENDER (6/6)
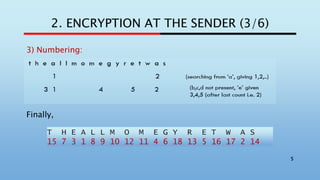
8) Add the indicator group with this, group into five, complete:
8
[Send out]
dnuha eesde tugym oacan nchis eoelx nsjmh
yiocn hdani etead cremh asvs](https://image.slidesharecdn.com/soecodepresentationforslideshare-200523132909/85/Poem-code-SOE-code-an-early-cryptographic-scheme-used-in-WW2-8-320.jpg)

![3. DECRYPTION AT THE RECIPIENT (3/6)
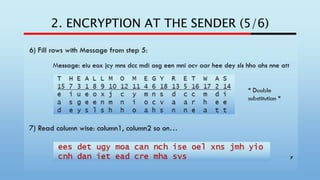
3) Fill Column with Cipher:
• Cipher: eesde tugym oacan nchis eoelx nsjmh yiocn hdani etead cremh asvs
• (Total column of key 18, elements in cipher = 54:: so row= 54/18 = 3)
• Cipher: ees det ugy moa can nch ise oel xns jmh yio cnh dan iet ead cre mha
svs
11
T H E A L L M O M E G Y R E T W A S
15 7 3 1 8 9 10 12 11 4 6 18 13 5 16 17 2 14
e i u e o x j c y m n s d c c m d i
a s g e e n m n i o c v a a r h e e
d e y s l s h h o a h s n n e a t t
[Fill
column1,
column2
and so
on..]](https://image.slidesharecdn.com/soecodepresentationforslideshare-200523132909/85/Poem-code-SOE-code-an-early-cryptographic-scheme-used-in-WW2-11-320.jpg)
![3. DECRYPTION AT THE RECIPIENT (4/6)
4) Read row wise (row1, row 2 and so on):
12
T H E A L L M O M E G Y R E T W A S
15 7 3 1 8 9 10 12 11 4 6 18 13 5 16 17 2 14
e i u e o x j c y m n s d c c m d i
a s g e e n m n i o c v a a r h e e
d e y s l s h h o a h s n n e a t t
eiu eox jcy mns dcc mdi asg een mni ocv aar
hee dey sls hho ahs nne att
Row Wise (row1, row2 so
on):
[Table
from step
3]](https://image.slidesharecdn.com/soecodepresentationforslideshare-200523132909/85/Poem-code-SOE-code-an-early-cryptographic-scheme-used-in-WW2-12-320.jpg)

![3. DECRYPTION AT THE RECIPIENT (6/6)
* Remove null characters i.e. ‘xs’
14
[Original Message]
HAJEE MOHAMMAD DANESH SCIENCE AND
TECHNOLOGY UNIVERSITY CSE](https://image.slidesharecdn.com/soecodepresentationforslideshare-200523132909/85/Poem-code-SOE-code-an-early-cryptographic-scheme-used-in-WW2-14-320.jpg)
