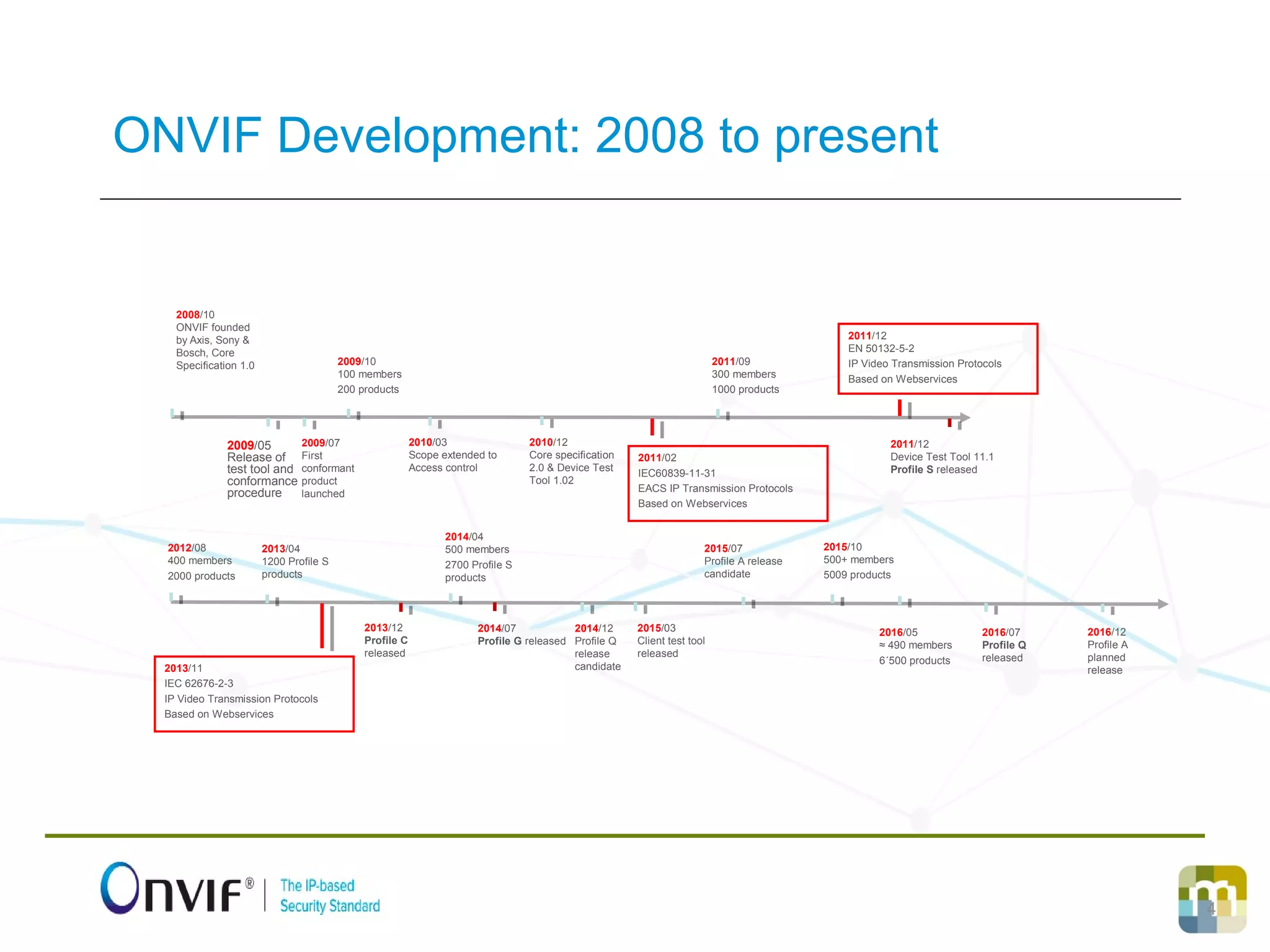
ONVIF promotes open interfaces for interoperability among IP-based physical security products, ensuring standardization and collaboration across brands. Since its founding in 2008, ONVIF has expanded its scope and membership, now overseeing numerous profiles and thousands of products. The document emphasizes the importance of security standards in the Internet of Things (IoT) and the need for continuous improvement in cybersecurity practices.