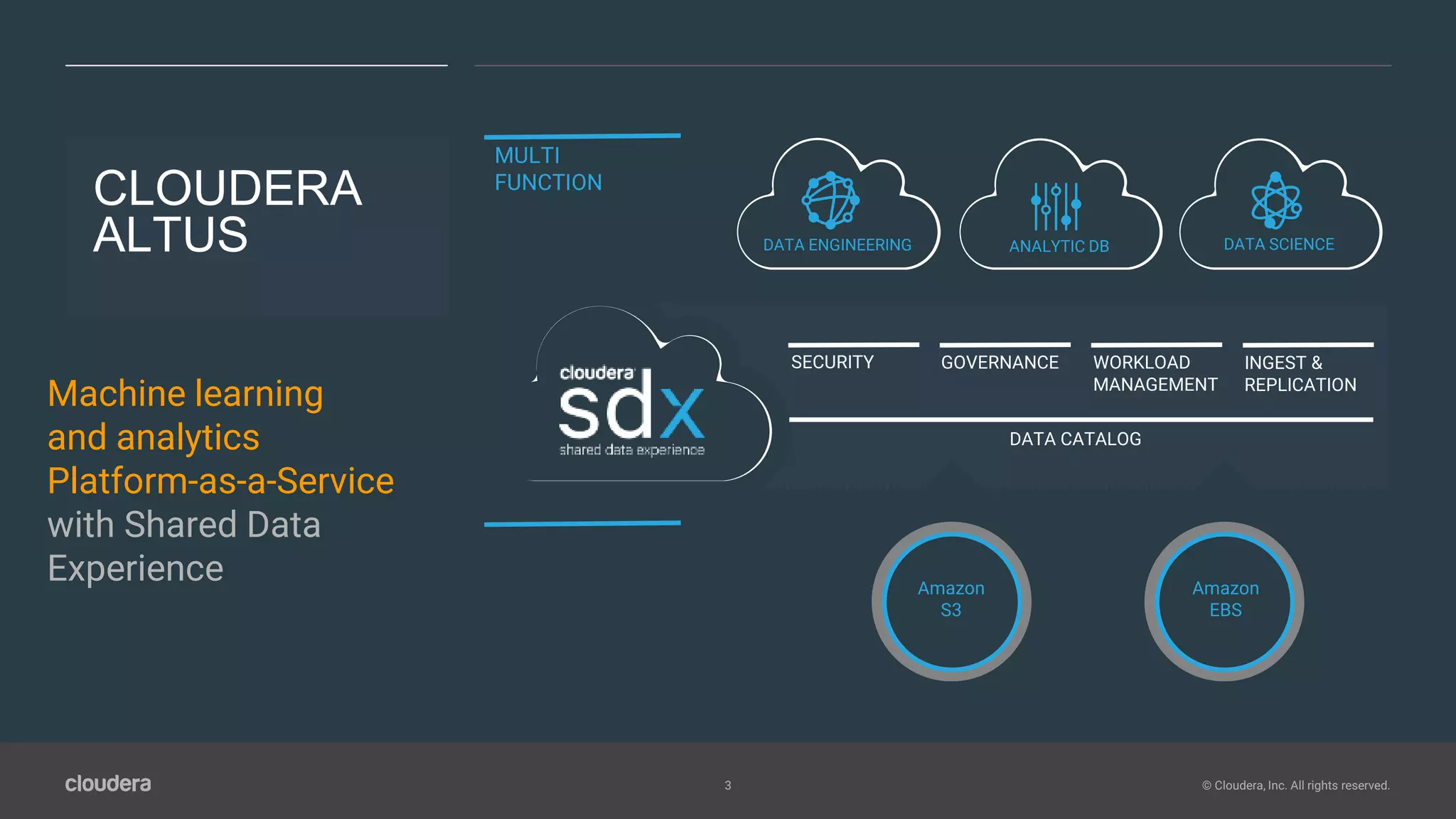
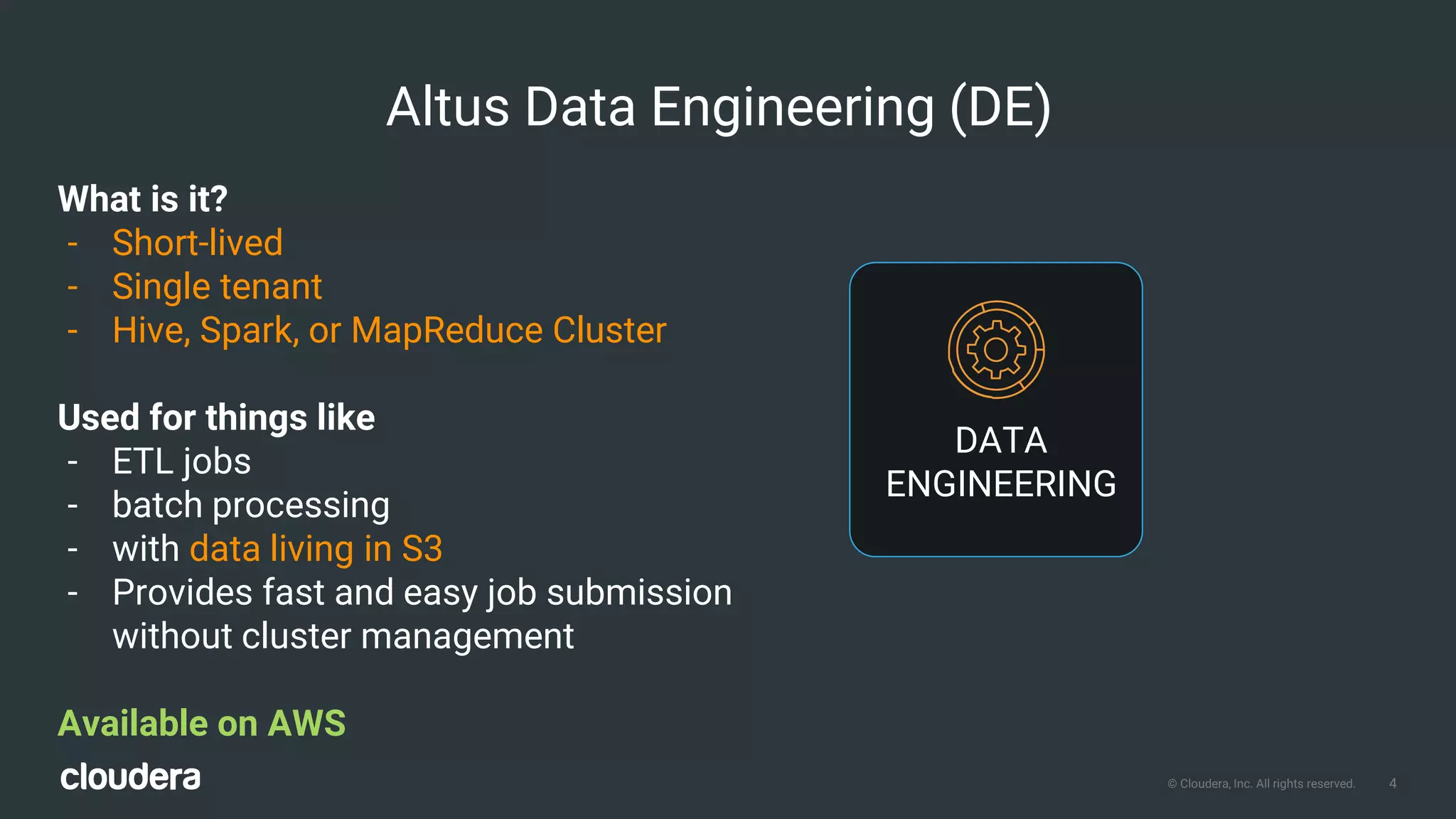
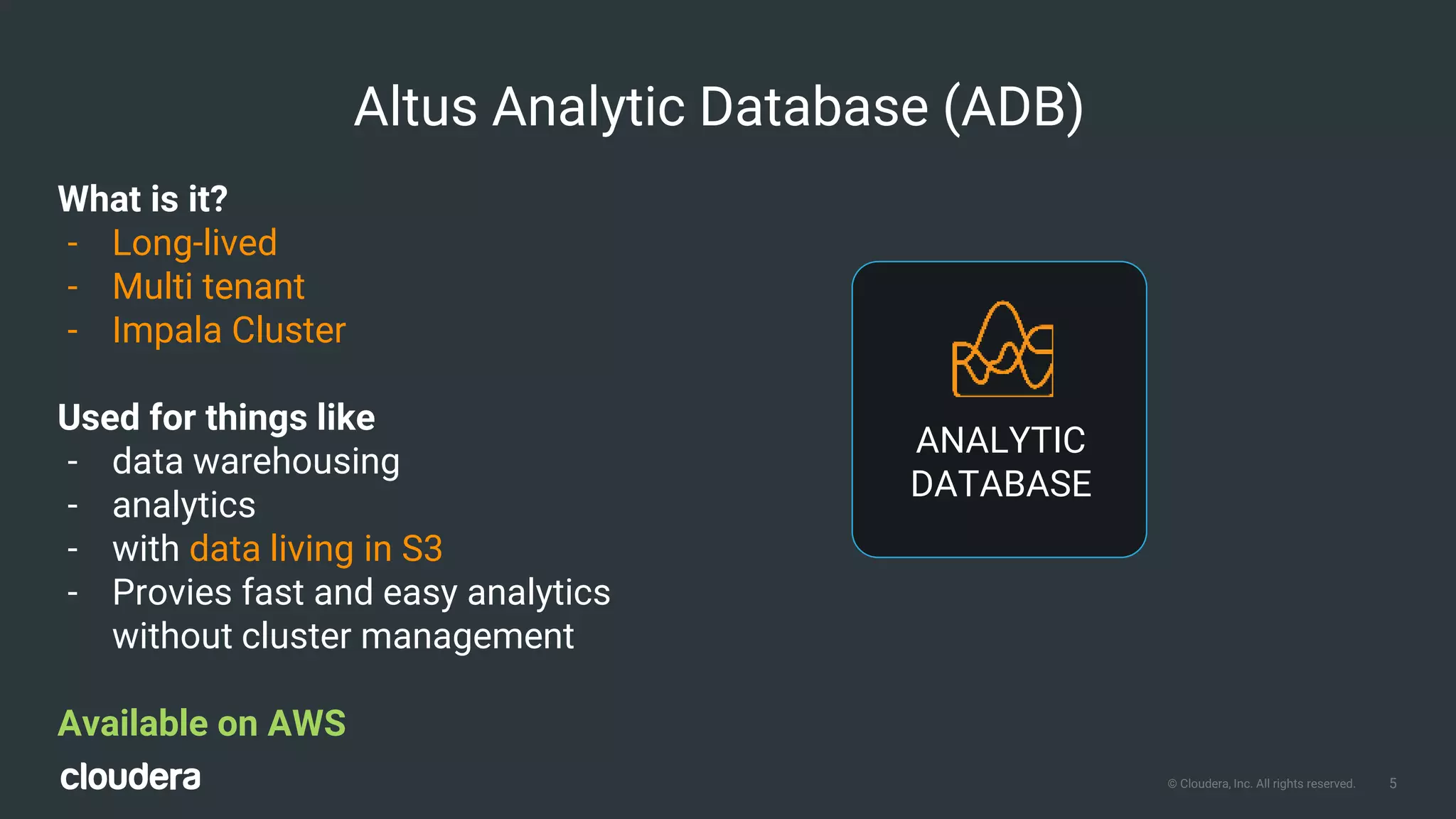
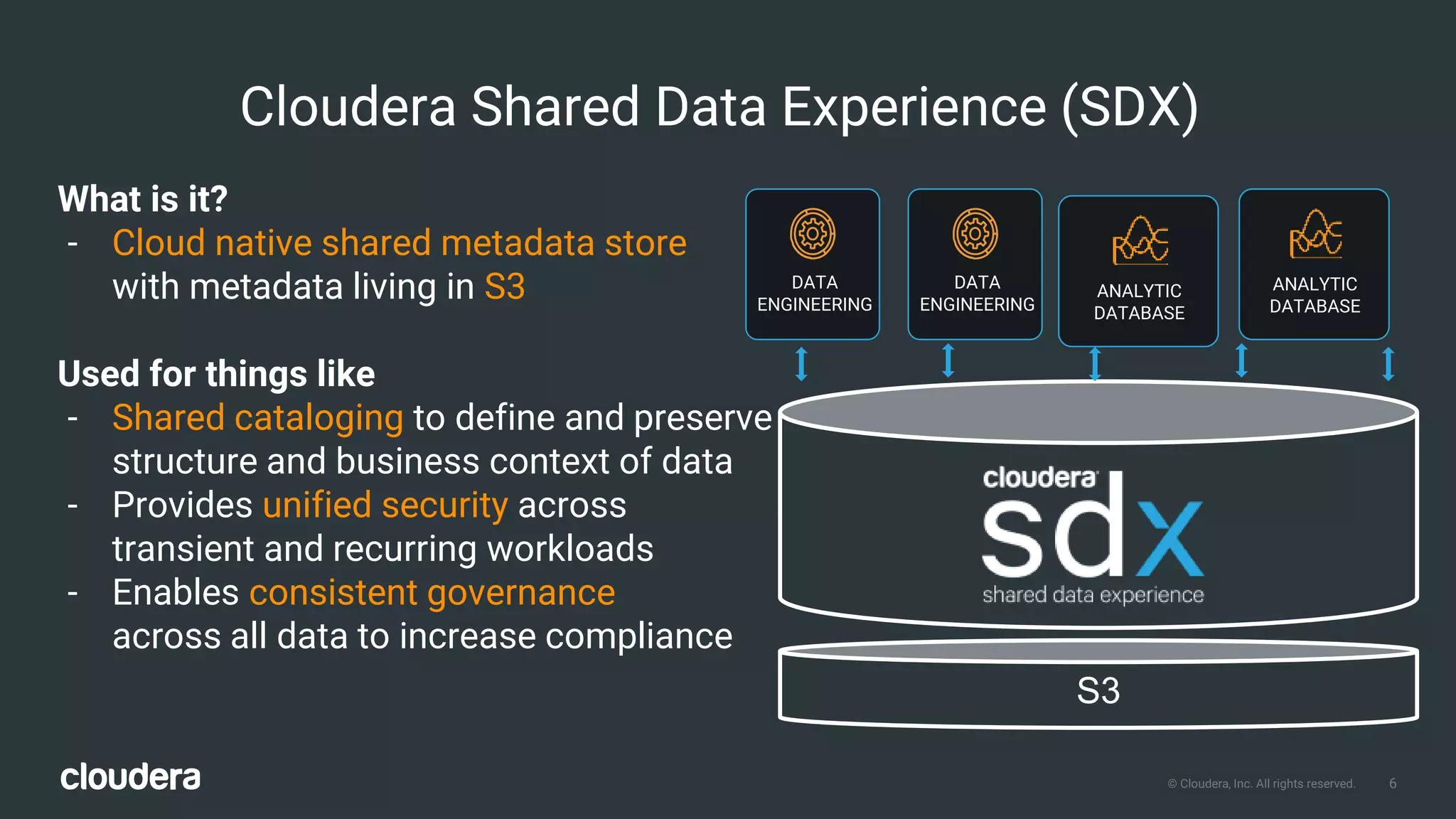
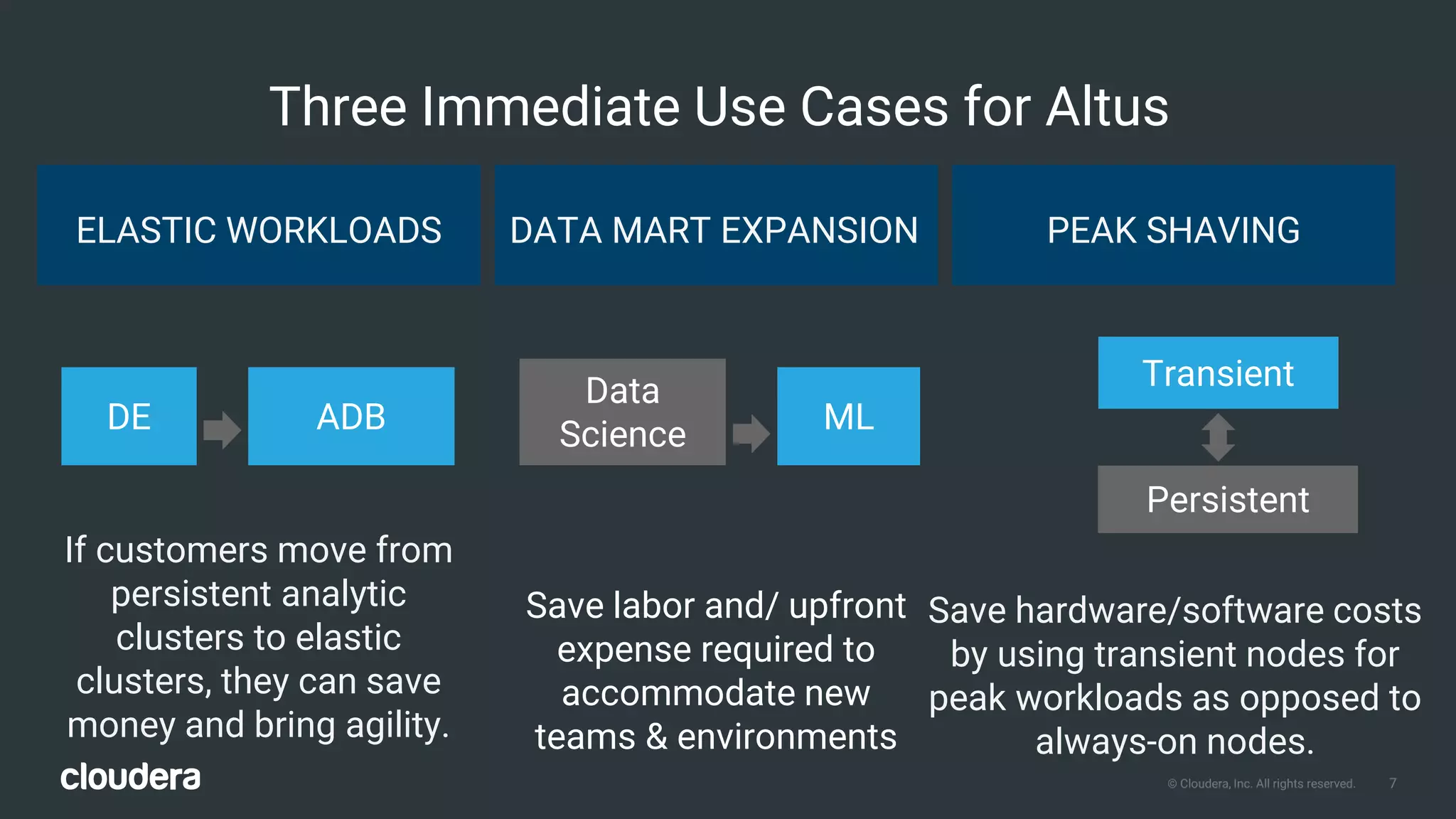
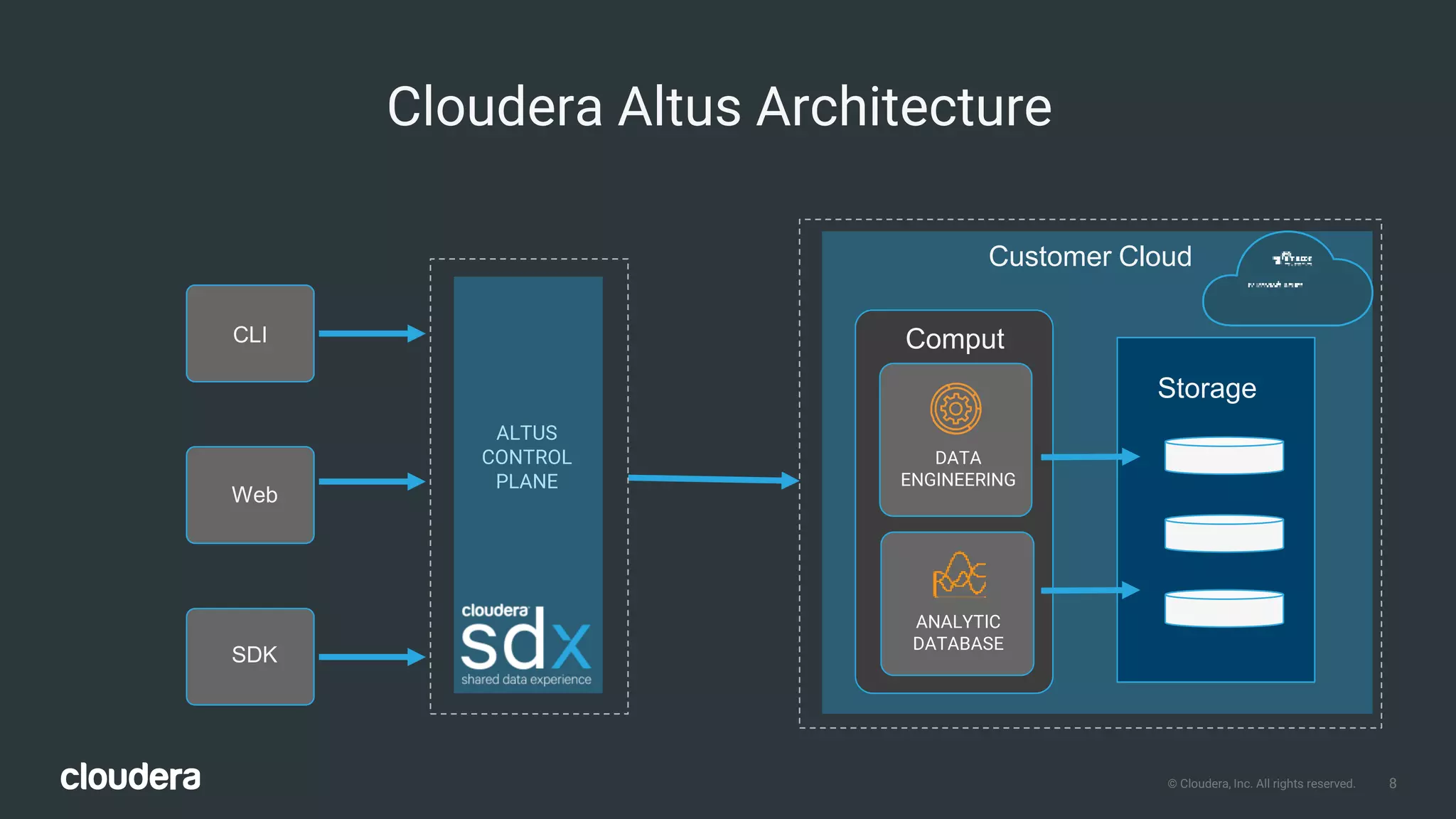
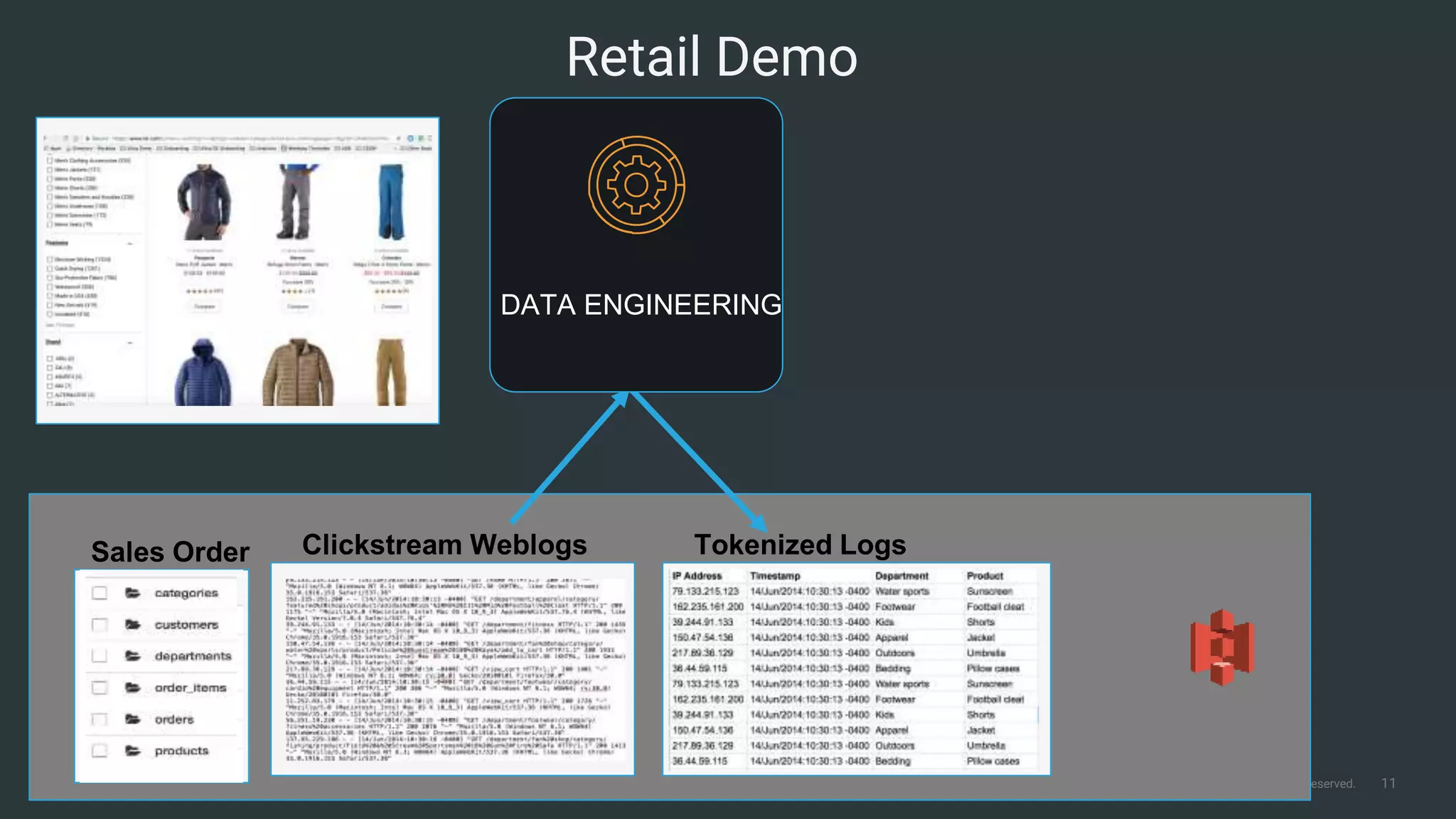
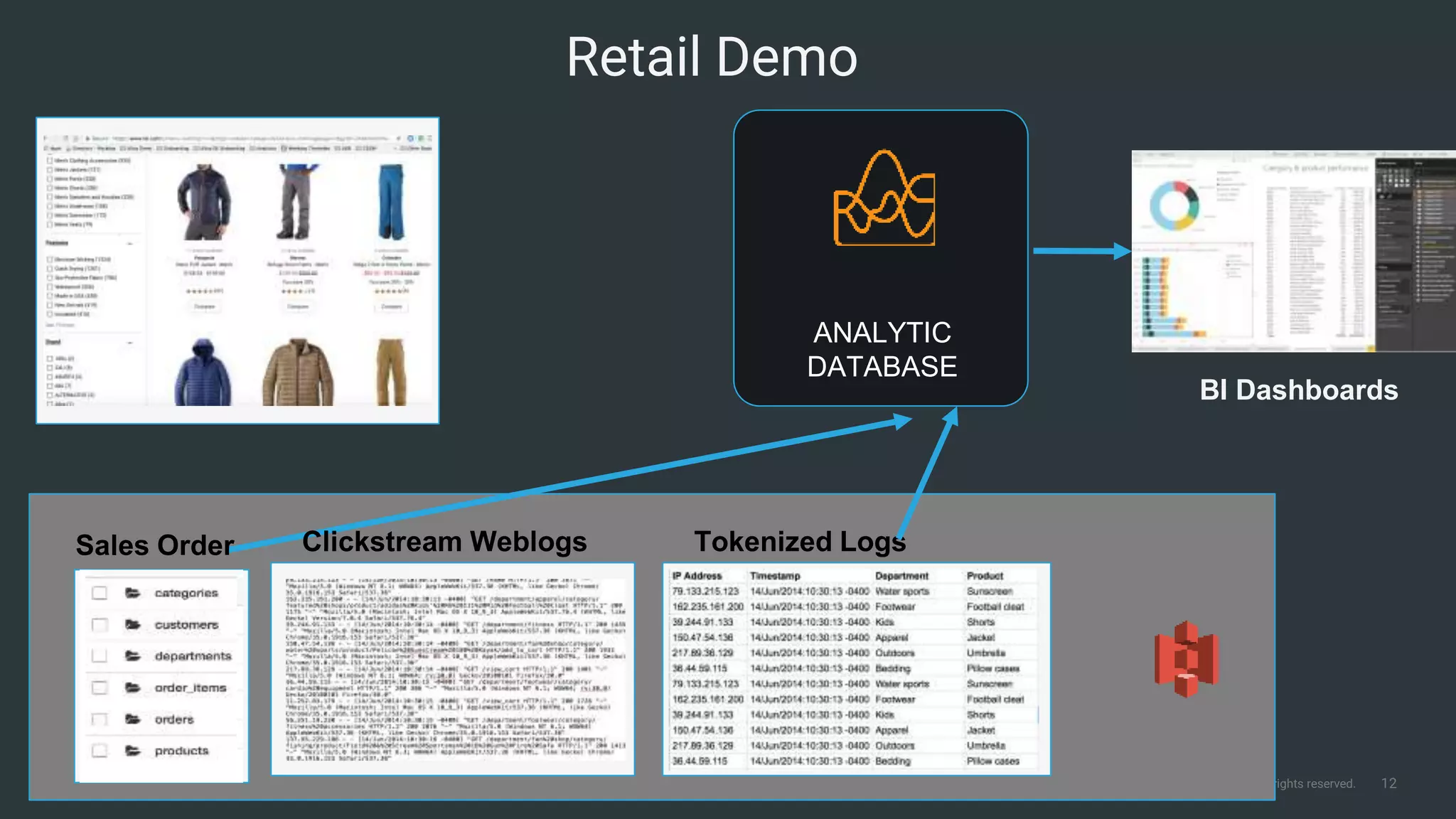
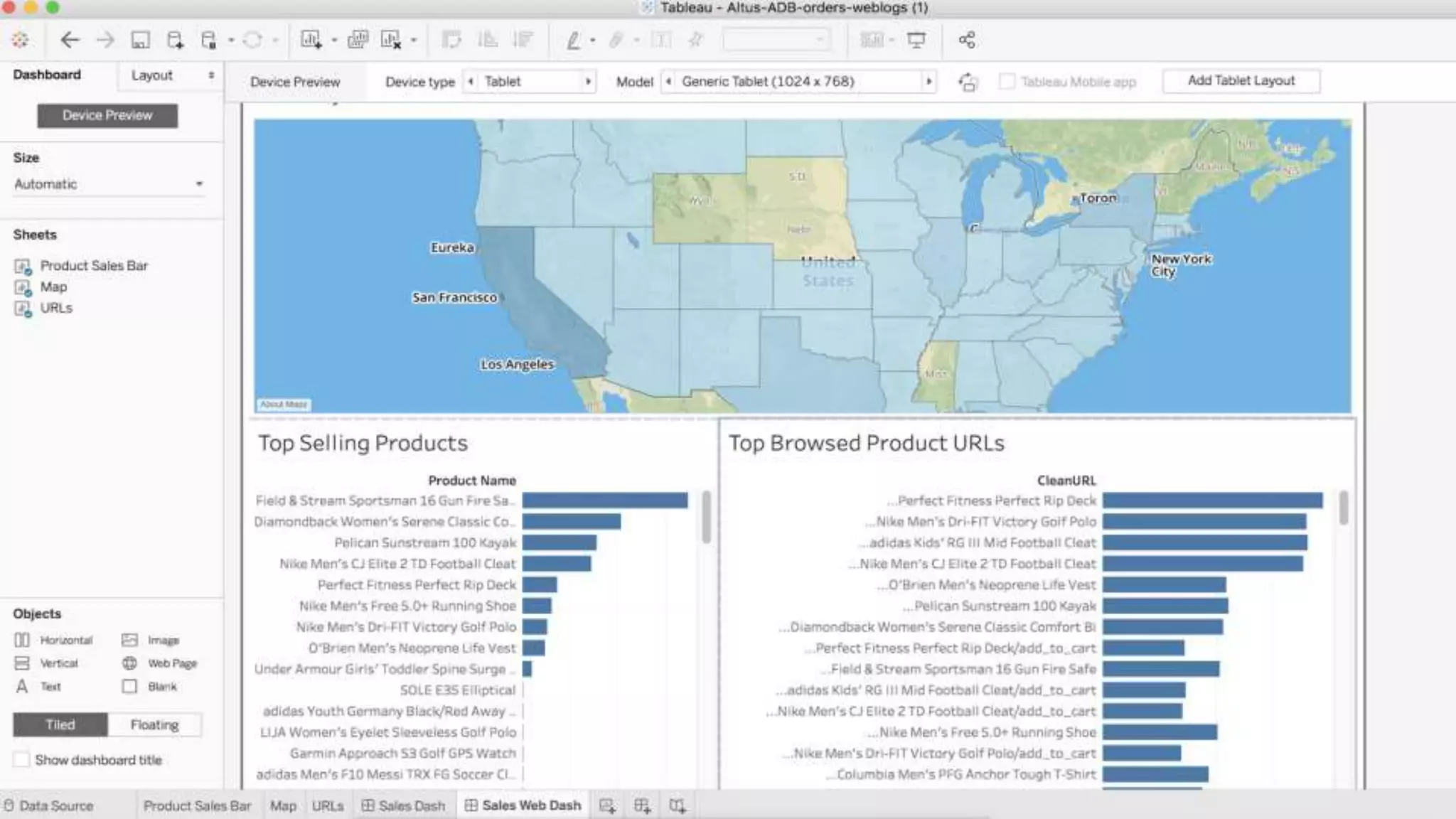
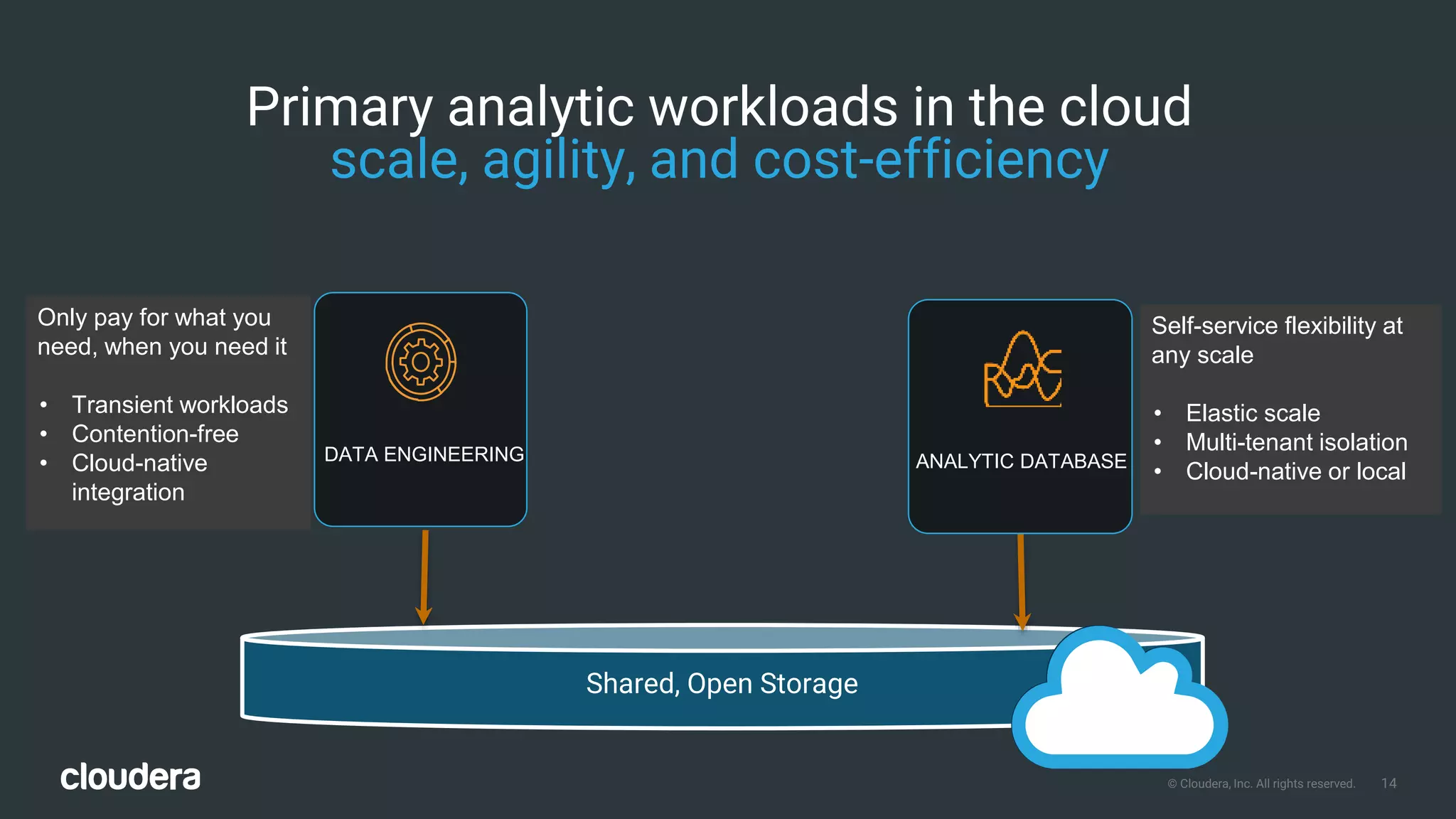
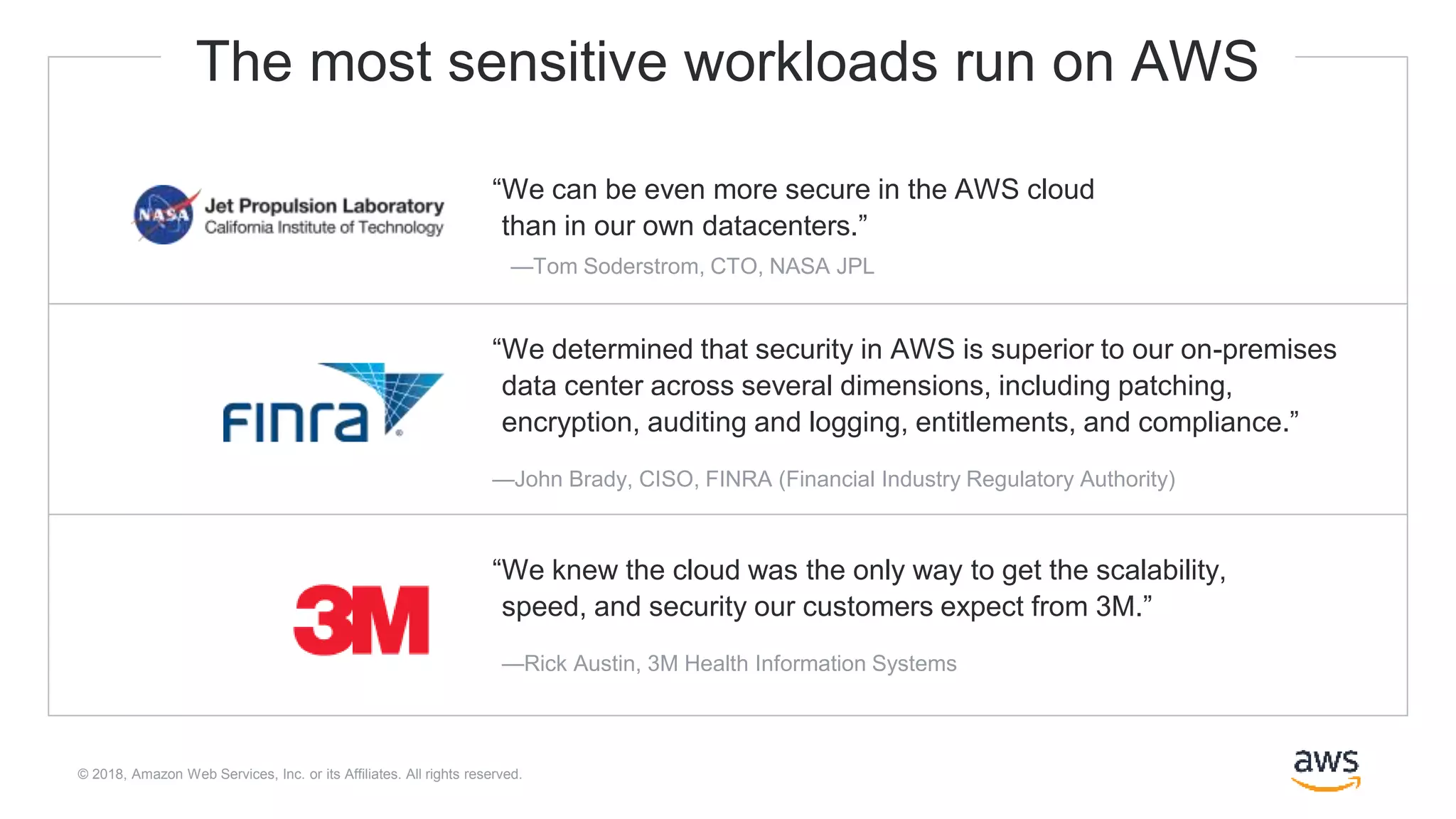
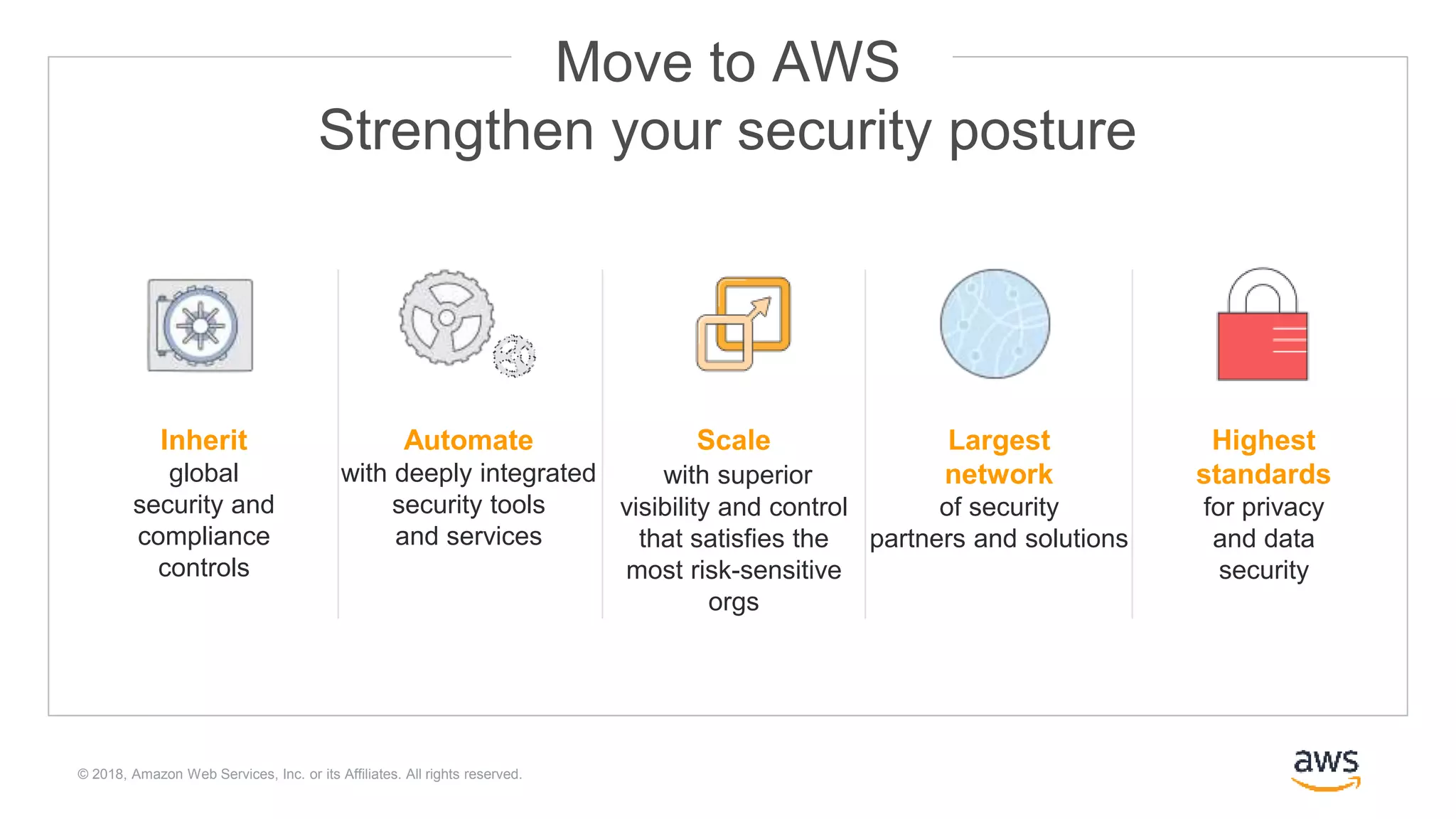
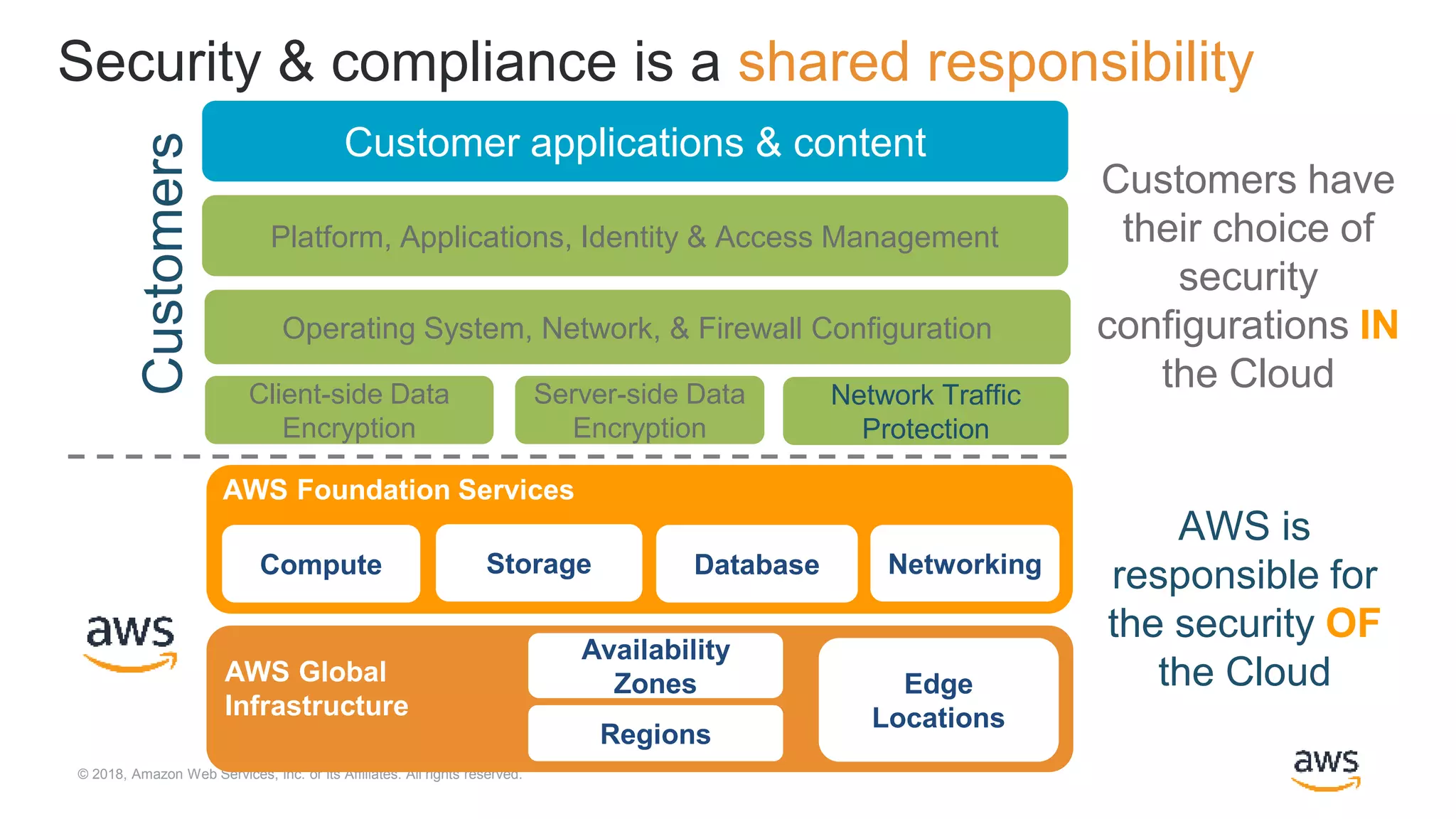
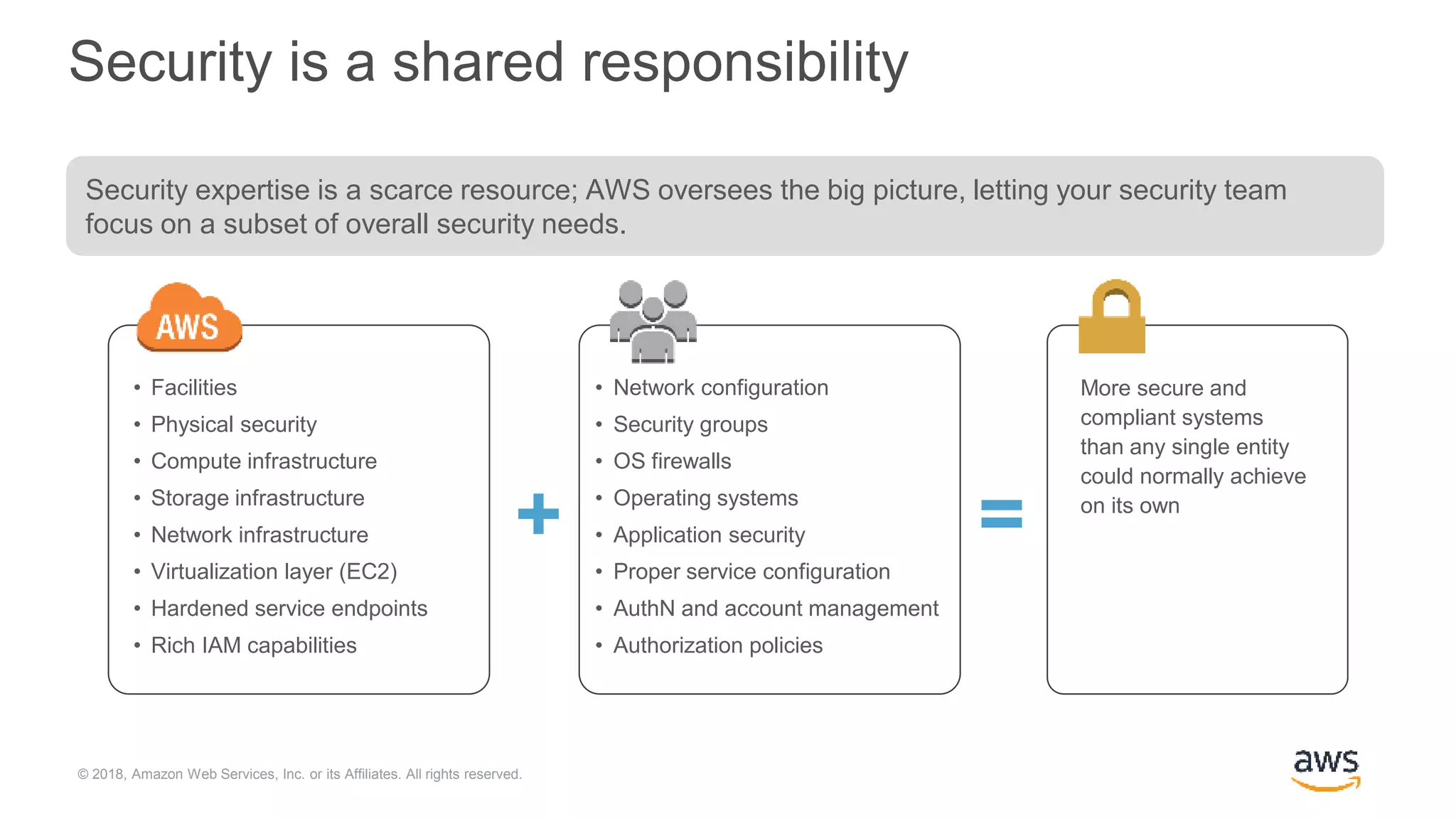
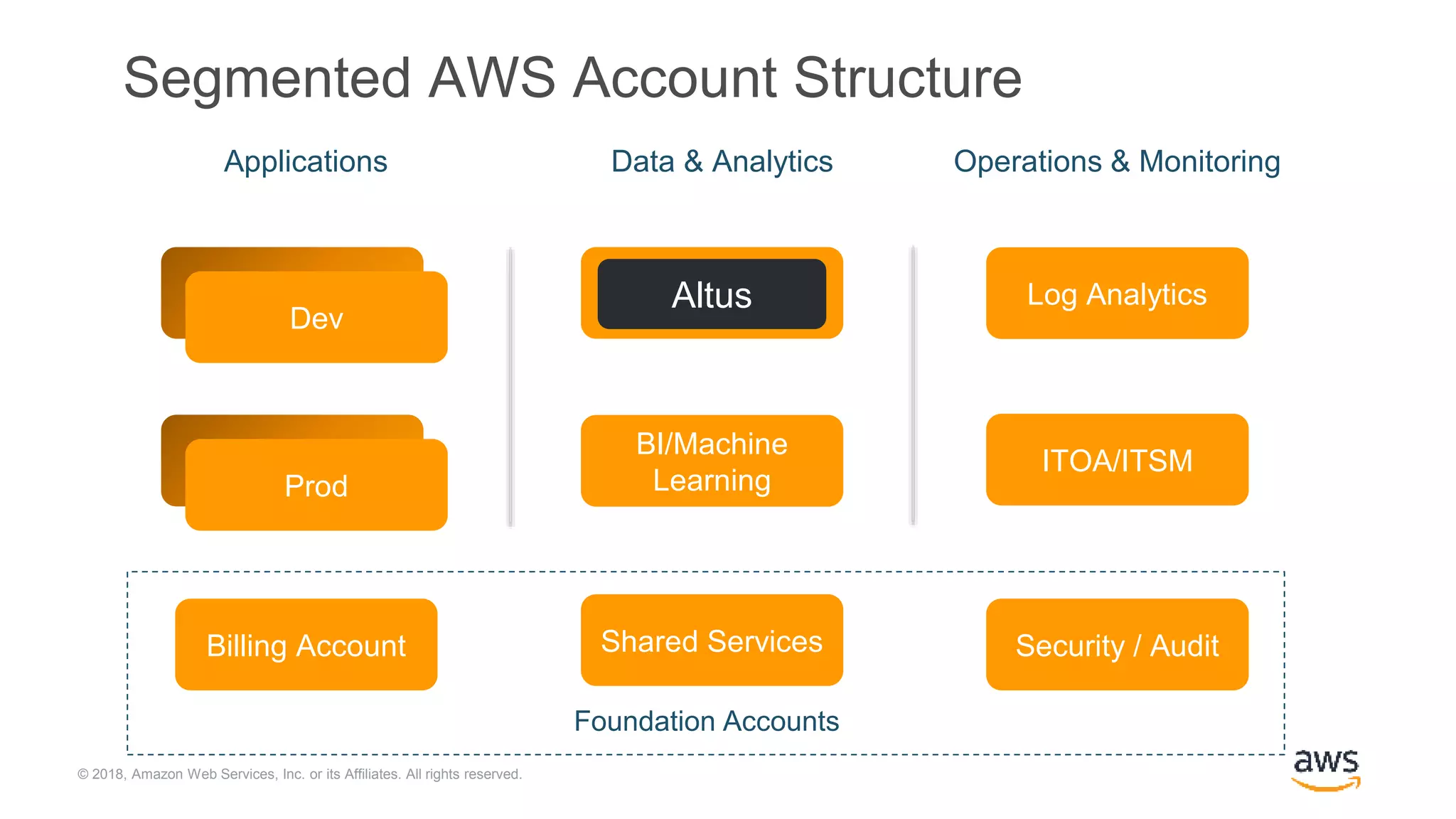
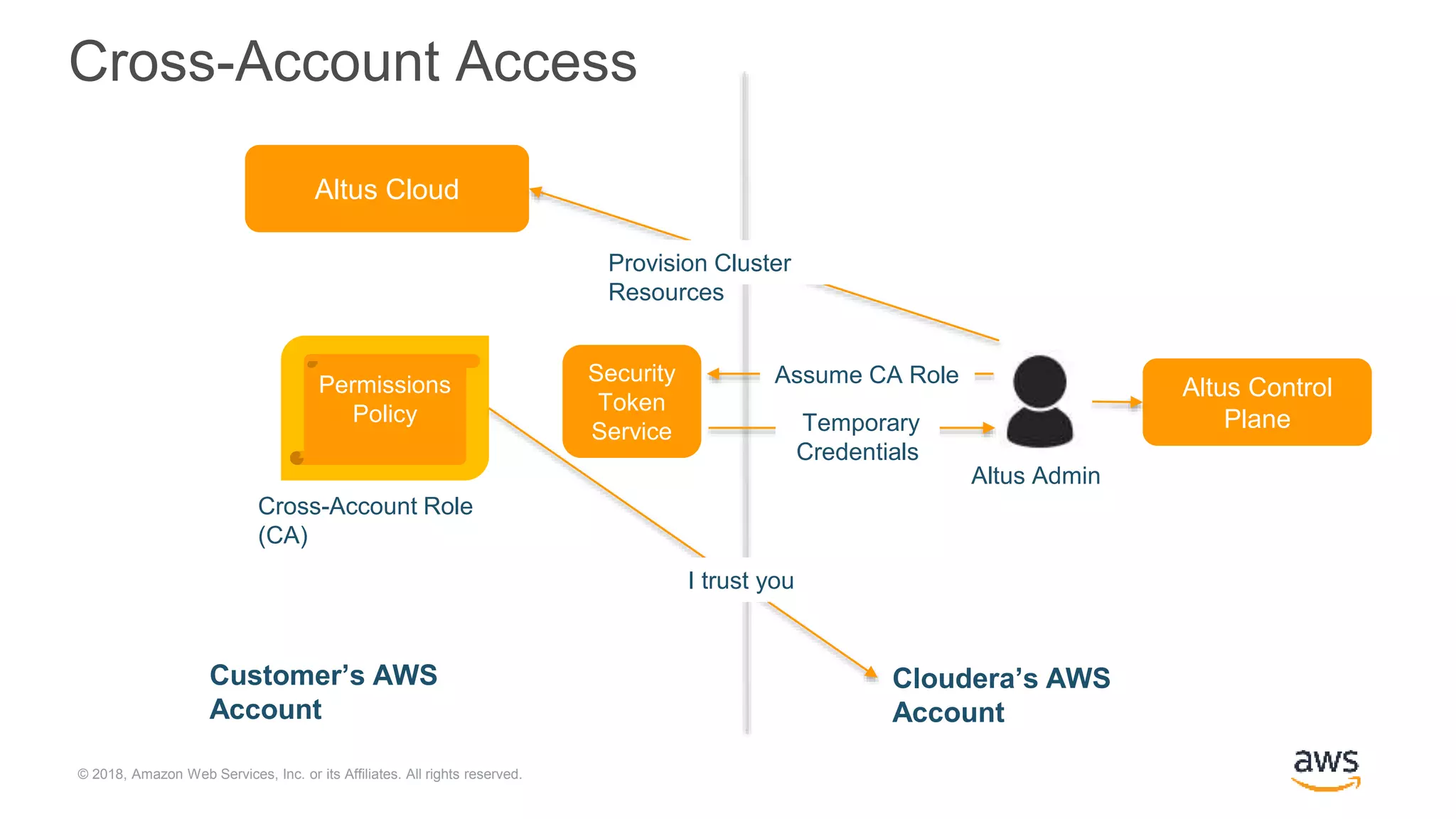
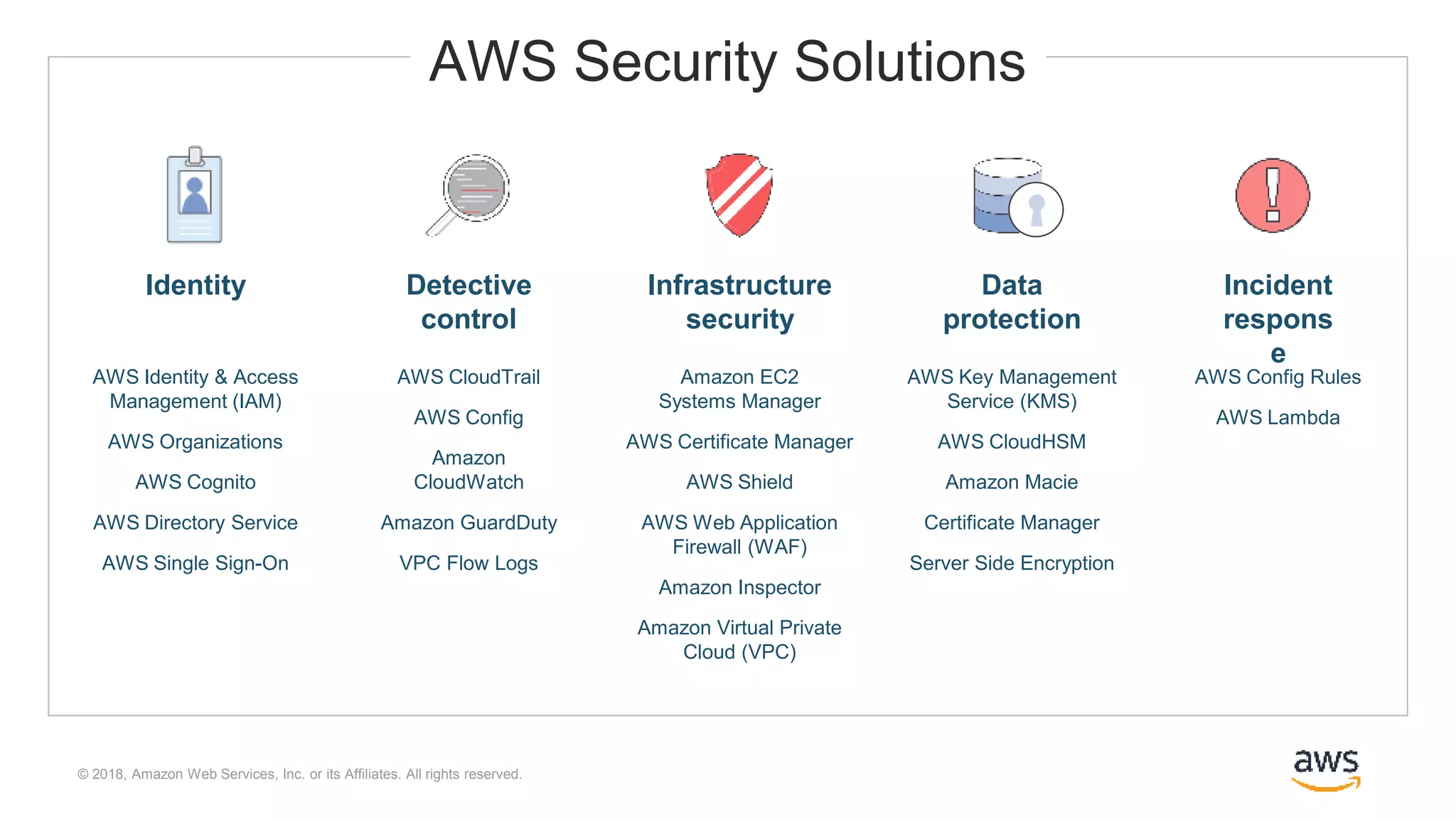
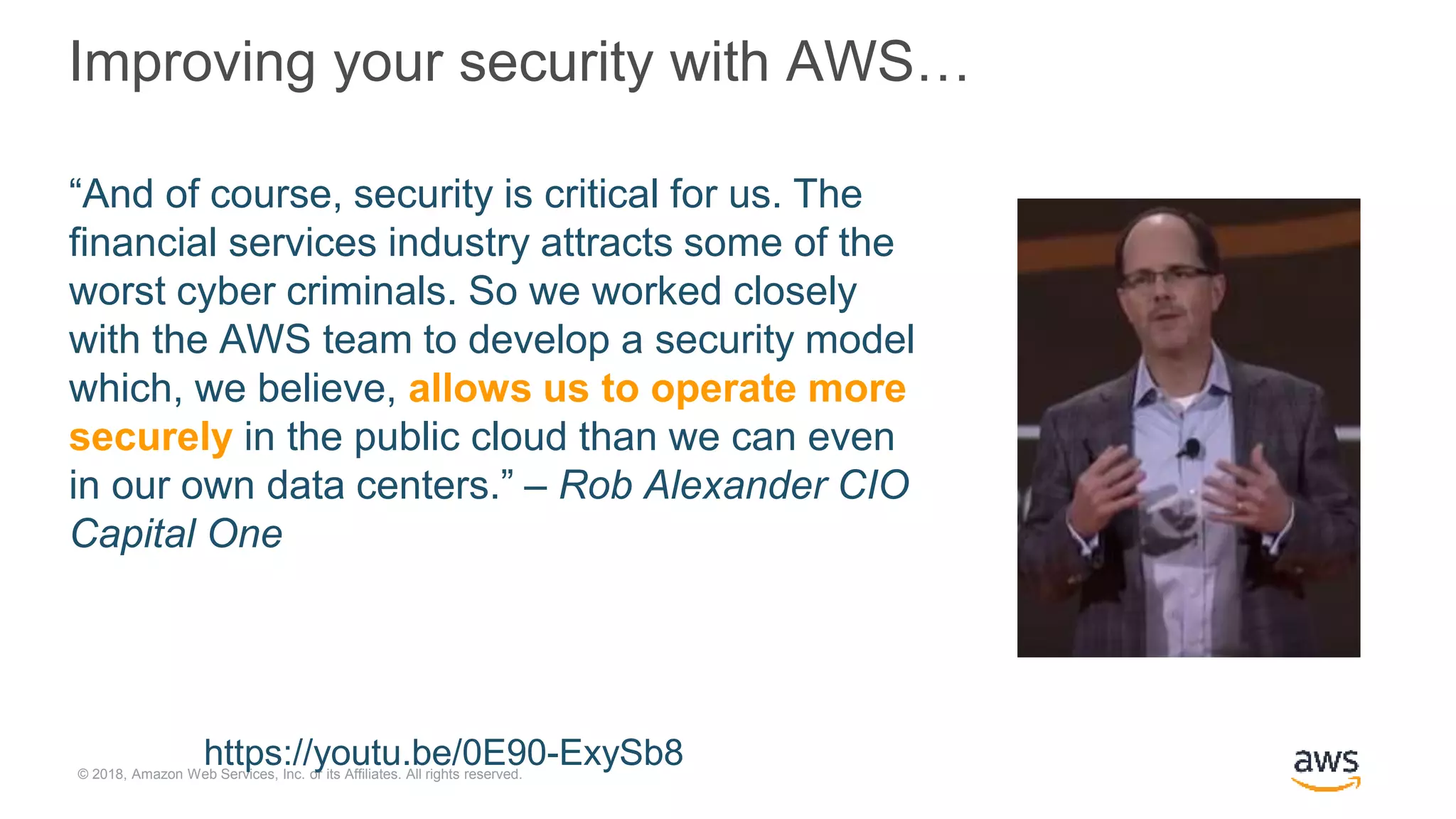
The document outlines Cloudera Altus, a machine learning and analytics platform-as-a-service available on AWS, offering features like data engineering, analytics, and governance with free AWS credits and a 90-day trial. It emphasizes the platform's architecture, use cases, and its cost-efficient and elastic data handling capabilities while highlighting the importance of security and compliance in cloud environments. The content also conveys that AWS can provide superior security compared to traditional on-premises data centers.