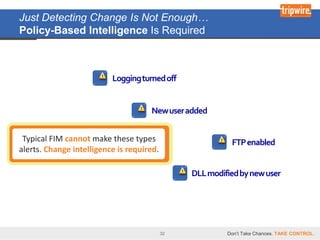
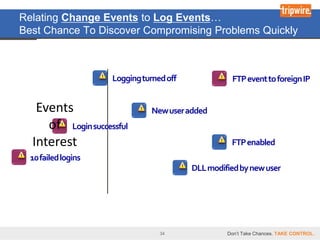
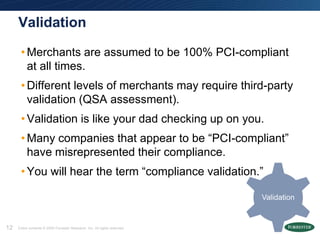
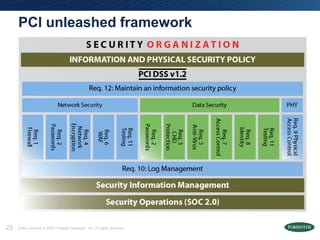
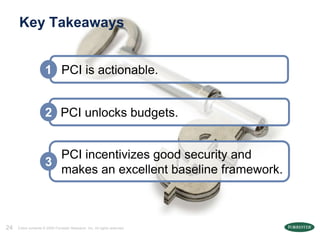
The document discusses the Payment Card Industry Data Security Standard (PCI DSS) as a crucial framework for enhancing data security practices for businesses handling credit cards. It emphasizes that while PCI compliance is necessary, it does not equate to security and requires continuous diligence to avoid risks. Moreover, the document highlights the value of PCI in fostering an understanding of data security, unlocking budgets, and providing best practices for protecting customer data.




















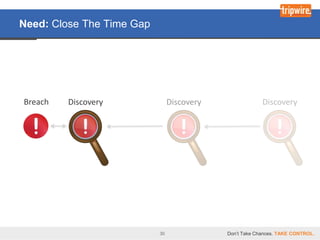
![Problem: Taking Too Long to Find Breaches/Risks
Breaches go undiscovered and uncontained
for weeks or months in 75 % of cases.
2009
Breach Average time between a breach and the detection of Discovery
it: 156 days [5.2 months]
Feb. 2010
“…breaches targeting stored data averaged 686 days
[of exposure]”
2010
“More than 75,000 computers … hacked” -- The attack
began late 2008 and discovered last month
Feb. 2010
28 Don’t Take Chances. TAKE CONTROL.](https://image.slidesharecdn.com/pciavaluablesecurityframeworknotapunishment-110627103808-phpapp01/85/PCI-A-Valuable-Security-Framework-Not-a-Punishment-28-320.jpg)