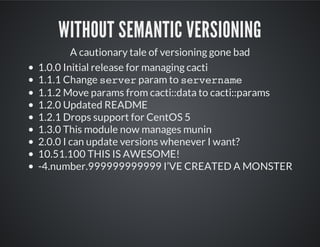
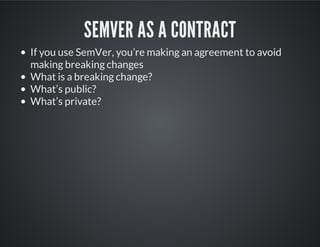
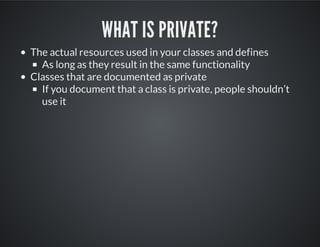
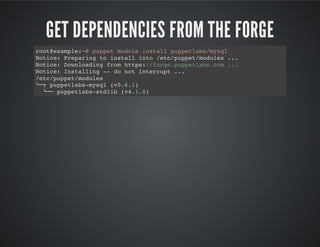
This document provides best practices and guidance for writing and sharing Puppet modules. It discusses separating logic from data, using semantic versioning (SemVer), creating modules as interfaces, reusing existing modules from the Puppet Forge, and establishing a community to collaborate on modules. The key recommendations are to separate configuration data from logic, use SemVer to avoid breaking changes, make modules opinionated but allow overrides, leverage existing modules, and engage the community to improve modules.








![PACKAGE/FILE/SERVICE
Humble beginnings for many modules
class mysql::server {
package { 'mysql-server':
ensure => present,
}
file { '/etc/mysql/my.cnf':
ensure => present,
content => template('mysql/server/my.cnf.erb'),
require => Package['mysql-server'],
}
service { 'mysqld':
ensure => running,
enable => true,
subscribe => File['/etc/mysql/my.conf'],
}
}](https://image.slidesharecdn.com/pcboston2013greatmodules-130613001848-phpapp01/85/Writing-Sharing-Great-Modules-Puppet-Camp-Boston-9-320.jpg)

![RUDIMENTARY DATA/LOGIC SEPARATION
class mysql::server {
include mysql::params
package { 'mysql-server':
name => $mysql::params::server_package,
ensure => present,
}
file { 'my.cnf':
path => $mysql::params::server_config,
ensure => present,
source => 'puppet:///modules/mysql/my.cnf',
require => Package['mysql-server'],
}
service { 'mysql-server':
name => $mysql::params::server_service,
ensure => running,](https://image.slidesharecdn.com/pcboston2013greatmodules-130613001848-phpapp01/85/Writing-Sharing-Great-Modules-Puppet-Camp-Boston-11-320.jpg)





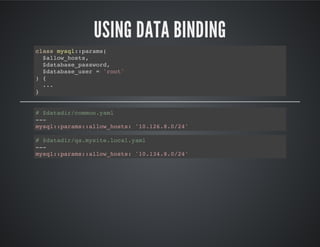



![CREATING A PARTIAL TEMPLATE
<%# nginx/templates/vhost/_listen.conf.erb %>
<%# Configuration fragment for listening on IPv4 and IPv6 with SSL %>
<% unless @sslonly -%>
listen <%= port %>;
<% if scope.lookupvar('::ipaddress6') -%>
listen [::]:<%= port %>;
<% end -%>
<% end -%>
<% if ssl -%>
listen <%= ssl_port %> ssl;
<% if scope.lookupvar('::ipaddress6') -%>
listen [::]:<%= ssl_port %> ssl;
<% end -%>
<% end -%>](https://image.slidesharecdn.com/pcboston2013greatmodules-130613001848-phpapp01/85/Writing-Sharing-Great-Modules-Puppet-Camp-Boston-24-320.jpg)
![USING PARTIAL TEMPLATES
Example: my_nginx_app/templates/nginx-
vhost.conf.erb
server {
<%= scope.function_template(['nginx/vhost/_listen.conf.erb']) %>
root /usr/share/empty;
location / {
proxy_pass <%= @proto %>://workers;
proxy_redirect off;
proxy_next_upstream error timeout invalid_header http_500 http_503;
proxy_connect_timeout 5;
}
}](https://image.slidesharecdn.com/pcboston2013greatmodules-130613001848-phpapp01/85/Writing-Sharing-Great-Modules-Puppet-Camp-Boston-25-320.jpg)