Paper nctsn
•
0 likes•59 views
The document discusses an open redirect vulnerability found on the website nctsnet.org. An open redirect occurs when a website redirects a user's browser to a different URL, allowing an attacker to perform phishing attacks or distribute malware. The vulnerability on nctsnet.org was found in the pubdlcnt.php script, which did not validate or verify the redirect URL. An attacker could exploit this by crafting a malicious URL with the vulnerability and tricking users into clicking on the link. Open redirects abuse a site's trust and can be used to steal user information or credentials from a trusted domain.
Report
Share
Report
Share
Download to read offline
Recommended
Webspoofing

This document discusses web spoofing and phishing attacks. It defines web spoofing as creating a fake website to mislead users into thinking it was created by a different person or organization. The document outlines different types of spoofing attacks, including IP, email, and web spoofing. It provides details on how a web spoofing attack works, including creating a shadow copy of the real website and funneling traffic through the attacker's machine to tamper with data. The document also discusses challenges with current technologies to fully prevent phishing and web spoofing attacks.
Classifying fake news articles using natural language processing to identify ...

Classifying fake news articles using natural language processing to identify in articleattribution as a supervised learning estimator
Security Protection for WordPress

This document discusses various security vulnerabilities that can affect WordPress websites, including vulnerabilities in the WordPress core, themes, and plugins. It notes that while the WordPress core is generally secure, vulnerabilities can arise from themes and plugins. It then outlines several specific vulnerabilities like brute force login attempts, content injection, cross-site scripting, SQL injection, and arbitrary file deletion. It encourages scanning websites for vulnerabilities and provides contact information for a company that offers website security solutions.
Anatomy of a Ransomware Attack - Paubox SECURE Conference 2017

Keynote speech by Paubox CEO Hoala Greevy on 2 November 2017 during Paubox SECURE Conference in San Francisco.
Warningbird

This document describes WarningBird, a system for detecting suspicious URLs in Twitter streams. It uses URL redirection chains and tweet context to extract 11 features for classifying URLs. WarningBird crawls URLs to obtain redirection chains, then performs domain grouping, feature extraction and logistic regression classification. It achieved low false positive and negative rates on real Twitter data. WarningBird can process URLs quickly and detect suspicious accounts faster than Twitter's own systems.
How Twitter Usage Differs Between Humans and Company Accounts

The document analyzes differences between tweets from company accounts and personal accounts that one user follows. It finds that company accounts tweet much more often, with their tweets making up around 80% of tweets in the user's timeline even though they only represent around 46% of followed accounts. Company tweets also tend to receive more engagement in the form of favorites and retweets. In contrast, personal accounts interact with each other more by mentioning each other in tweets. Finally, company tweets are much more likely to include a URL, with around 95% doing so compared to a lower rate for personal accounts.
WARNINGBIRD: A NEAR REAL-TIME DETECTION SYSTEM FOR SUSPICIOUS URLS IN TWITTER...

This document describes WarningBird, a near real-time system for detecting suspicious URLs in Twitter streams. It analyzes correlated redirection chains of URLs, where attackers often reuse the same redirection routes. When WarningBird observes over w tweets, it groups URLs with the same domains and identifies frequently shared URLs. It extracts 11 features from redirection chains and uses supervised learning to flag tweets containing URLs from suspended accounts as suspicious. Compared to prior work, WarningBird enables real-time detection without account information and is resistant to fabrication through correlated URL analysis.
Security for javascript

An attacker can inject malicious scripts into a web page by exploiting security vulnerabilities in the browser environment. Once a foothold is gained, an attacker can access additional scripts from any server, make unauthorized requests to the vulnerable server, read data in the document, and send data to other servers. These attacks have been issues since Netscape 2 in 1995. Ultimately, JavaScript and the DOM need to be replaced with more secure alternatives to prevent cross-site scripting (XSS) attacks.
Recommended
Webspoofing

This document discusses web spoofing and phishing attacks. It defines web spoofing as creating a fake website to mislead users into thinking it was created by a different person or organization. The document outlines different types of spoofing attacks, including IP, email, and web spoofing. It provides details on how a web spoofing attack works, including creating a shadow copy of the real website and funneling traffic through the attacker's machine to tamper with data. The document also discusses challenges with current technologies to fully prevent phishing and web spoofing attacks.
Classifying fake news articles using natural language processing to identify ...

Classifying fake news articles using natural language processing to identify in articleattribution as a supervised learning estimator
Security Protection for WordPress

This document discusses various security vulnerabilities that can affect WordPress websites, including vulnerabilities in the WordPress core, themes, and plugins. It notes that while the WordPress core is generally secure, vulnerabilities can arise from themes and plugins. It then outlines several specific vulnerabilities like brute force login attempts, content injection, cross-site scripting, SQL injection, and arbitrary file deletion. It encourages scanning websites for vulnerabilities and provides contact information for a company that offers website security solutions.
Anatomy of a Ransomware Attack - Paubox SECURE Conference 2017

Keynote speech by Paubox CEO Hoala Greevy on 2 November 2017 during Paubox SECURE Conference in San Francisco.
Warningbird

This document describes WarningBird, a system for detecting suspicious URLs in Twitter streams. It uses URL redirection chains and tweet context to extract 11 features for classifying URLs. WarningBird crawls URLs to obtain redirection chains, then performs domain grouping, feature extraction and logistic regression classification. It achieved low false positive and negative rates on real Twitter data. WarningBird can process URLs quickly and detect suspicious accounts faster than Twitter's own systems.
How Twitter Usage Differs Between Humans and Company Accounts

The document analyzes differences between tweets from company accounts and personal accounts that one user follows. It finds that company accounts tweet much more often, with their tweets making up around 80% of tweets in the user's timeline even though they only represent around 46% of followed accounts. Company tweets also tend to receive more engagement in the form of favorites and retweets. In contrast, personal accounts interact with each other more by mentioning each other in tweets. Finally, company tweets are much more likely to include a URL, with around 95% doing so compared to a lower rate for personal accounts.
WARNINGBIRD: A NEAR REAL-TIME DETECTION SYSTEM FOR SUSPICIOUS URLS IN TWITTER...

This document describes WarningBird, a near real-time system for detecting suspicious URLs in Twitter streams. It analyzes correlated redirection chains of URLs, where attackers often reuse the same redirection routes. When WarningBird observes over w tweets, it groups URLs with the same domains and identifies frequently shared URLs. It extracts 11 features from redirection chains and uses supervised learning to flag tweets containing URLs from suspended accounts as suspicious. Compared to prior work, WarningBird enables real-time detection without account information and is resistant to fabrication through correlated URL analysis.
Security for javascript

An attacker can inject malicious scripts into a web page by exploiting security vulnerabilities in the browser environment. Once a foothold is gained, an attacker can access additional scripts from any server, make unauthorized requests to the vulnerable server, read data in the document, and send data to other servers. These attacks have been issues since Netscape 2 in 1995. Ultimately, JavaScript and the DOM need to be replaced with more secure alternatives to prevent cross-site scripting (XSS) attacks.
NTXISSACSC3 - How I hacked the Government and Got Away with It by Seven Hatfield

NTXISSACSC3 - How I hacked the Government and Got Away with It by Seven HatfieldNorth Texas Chapter of the ISSA
This document summarizes how the speaker hacked into a government training website and downloaded training videos without authentication. They describe their multiple unsuccessful attempts to report the vulnerability to the government via email, Twitter, and other means. The document suggests ways for the government to improve security, such as implementing a bug bounty program, conducting code audits, and having a vulnerability management program. It concludes that the government is currently unresponsive to security issues and that improvements are needed to address vulnerabilities.How I Hacked The Government And Got Away With It

In this presentation I spoke about how I found an information disclosure vulnerability within a Federal CyberSecurity training website, was able to report it responsibly, and the issues that came up as I attempted to do so.
Stateless Anti-Csrf

The document discusses stateless anti-CSRF techniques. It proposes a "triple submit" approach where the server sets an HTTP-only cookie with a random name and value, tells the client the value but not name, and the client submits both the name and value as request parameters. However, an attacker can still bypass this via cross-site scripting (XSS) by overflowing the browser's cookie jar and overwriting the HTTP-only cookie. The document demonstrates how to do this in different browsers.
2018 Hacked Website Trends

Our Website Hacked Trend Report provides insights on the top open-source CMS security, out-of-date software, and specific malware families we see on hacked websites in the Sucuri environment.
We’ve built this analysis from prior reports to identify the latest tactics, techniques, and procedures (TTPs) detected by our Remediation Group. A total of 18,302 infected websites and 4,426,795 cleaned files were analyzed in our recent publication.
Tony will discuss high-level findings on a range of topics, including:
- Affected open-source CMS applications
- Outdated CMS and blacklist analysis
- Malware families and their effects
Grey H@t - Cross-site Request Forgery

Cross-site scripting (XSS) and cross-site request forgery (XSRF) are two related web application vulnerabilities. XSS involves injecting malicious scripts into a web application to steal user data or perform actions on the user's behalf. XSRF tricks authenticated users into performing actions in a web application by submitting forged requests, since their browser will automatically include authentication cookies. While mitigations like validating HTTP referrers can help prevent XSRF, XSS can still be used to bypass these by scraping tokens or directly launching attacks from within compromised pages. Together, XSS and XSRF pose serious risks if not properly mitigated in web applications that handle sensitive data or perform sensitive actions.
Sucuri Webinar: Simple Steps To Secure Your Online Store

During this webinar, we'll discuss some basic security concepts for your online store that include what tools you'll need to remain PCI compliant as well as how to keep your data safe. Some key takeaways will include:
- Reducing Your Attack Surface
- Protecting Cardholder Data
- Creating a Disaster Recovery Plan
We'll also identify principles and practices that can address multiple PCI requirements at once to help save time and effort.
Webinar: CWAF for Mid Market/Enterprise Organizations

In today's complex security landscape, web applications pose a significant risk to Mid-Market and Enterprise organizations.
The question is, how can an organization secure their web properties without sacrificing performance. The answer may be a Cloud-based Web Application Firewall.
This webinar will introduce the concept of the CWAF, and the benefits of web application security in the cloud.
Samples of topics covered include:
- What is a cloud-based web application firewall
- The benefits of using a CWAF
- How to improve security and performance
- How to implement a CWAF in complex web environments
This live Q&A-based webinar is designed for development managers, large websites with unique and complex infrastructure/server environments, and anyone who is concerned about securing their web applications.
Insights provided in the webinar will help you operate more secure networks, infrastructure, and web applications.
You can see the video recording of this webinar at the end of the slides.
CROSS-SITE REQUEST FORGERY - IN-DEPTH ANALYSIS 2011

Cross-Site Request Forgery (CSRF in short) is a kind of a web application vulnerability which allows malicious website to send unauthorized requests to a vulnerable website using active session of its authorized users.
VodQA3_PenetrationTesting_AmitDhakkad

This was a full length talk presented by Amit Dhakkad in vodQA-3 : A QA Meet held in ThoughtWorks, Pune.
AtlasCamp 2010: Securing your Plugin - Penny Wyatt

This document discusses common security vulnerabilities in plugins and how to prevent them. It covers cross-site scripting (XSS) vulnerabilities, which can allow attackers to run JavaScript in a victim's browser. It also discusses cross-site request forgery (XSRF) vulnerabilities, which trick a victim into performing unwanted actions. The document provides guidance on using HTML encoding, generating secure random numbers, restricting file system access, and other techniques to prevent these vulnerabilities. It focuses on securing plugins used in Atlassian products like JIRA, Confluence and Bamboo.
CSRF Attack and Its Prevention technique in ASP.NET MVC

As the name suggests Cross Site Request Forgery Attack deals with the forgery of the trusted website of an authorized user with unwanted action. . These attacks have been called the “sleeping giant” of web-based vulnerabilities, because many sites on the Internet fail to protect against them and because they have been largely ignored by the web development and security communities . Our project aims at attacking the victim user by including a link or script in a page that accesses a site to which the user is known or is supposed to have been authenticated. Deep analysis of CSRF attack and finding the possibilities to mitigate the CSRF attack is our main focus and our objective on this project.
Web spoofing (1)

Web spoofing allows an attacker to create a fake version of the World Wide Web to trick victims. The attacker lures victims to their fake site, which looks identical to the real site. On the fake site, the attacker can observe any sensitive information entered by the victim. Current browsers are vulnerable to web spoofing attacks even on secure connections. Users should disable JavaScript, always check the URL bar, and be wary of any requests for sensitive information over email.
A10 - Unvalidated Redirects and Forwards

A10 - Unvalidated Redirects and Forwards
IT6873
Southern Polytechnic State University
William Stanley
State of the Art Analysis Approach for Identification of the Malignant URLs

Malicious URLs have been universally used to ascend various cyber attacks including spamming, phishing and malware. Malware, short term for malicious software, is software which is developed to penetrate computers in a network without the user’s permission or notification. Existing methods typically detect malicious URLs of a single attack type. Hence such detection systems are failed to protect the users from various attacks. Malware spreading widely throughout the area of network as consequence of this it becomes predicament in distributed computer and network systems. Malicious links are the place of origin of all attacks which circulated all over the web. Hence malicious URLs should be detected for the prevention of users from these malware attacks. In this paper we described a novel approach which analyze all types of attacks by identifying malicious URLs and secure the web users from them. This technique prevents the users from malignant URLs before visiting them. Therefore efficiency of web security gets maintained. For such anatomization we developed an analyzer which identifies URLs and examine as malicious or benign. We also developed five processes which crawl for suspicious URLs. This approach will prevent the users from all types of attacks and increase efficiency of web crawling phase.
Web Application Penetration Tests - Vulnerability Identification and Details ...

These slides explain what the Vulnerability Identification stage consists of during a web application security assessment.
These slides are part of the course Introduction to Web Application Security and Penetration Testing with Netsparker, which can be found here: https://www.netsparker.com/blog/web-security/introduction-web-application-penetration-testing/
How not to make a hacker friendly application

Presentation on application security basics and some common vulnerabilities like XSS, SQL Injection, IDOR etc.
Web spoofing

Web spoofing allows an attacker to create a fake version of the entire web in order to trick victims. The attacker rewrites URLs on web pages so they link to the attacker's server instead of the real server. When the victim interacts with forms or links, their data and browsing is redirected to the attacker's server without their knowledge. While the victim sees secure connections, these are actually to the attacker's server, not the intended site. The attacker can then observe and modify any private information submitted by the victim.
Cookie surveillance

This document analyzes the privacy risks of mass surveillance by leveraging third-party HTTP tracking cookies. The researchers find that over 90% of a typical user's web visits can be linked together through shared unique cookies. Additionally, nearly half of popular websites leak a logged-in user's real identity in unencrypted traffic. This allows a passive network observer to cluster a user's entire browsing history and attach their real identity, violating expectations of privacy. The researchers discuss implications for targeted and mass surveillance online.
Unauthorized access, Men in the Middle (MITM)

In this type of attack, the attacker attempts to insert himself in the
middle of a communication for purposes of intercepting client’s data.
50063

Vulnerability Alert from Symantec reports that SilverStripe, an open source content management system, is prone to multiple cross-site scripting vulnerabilities in its admin URIs. This allows attackers to execute arbitrary script code in users' browsers to steal cookies or launch other attacks. The vulnerabilities are due to a failure to sanitize user input passed through various admin URIs. SilverStripe 2.4.5 is confirmed vulnerable.
Search Engine Poisoning

This report from Imperva’s Hacker Intelligence Initiative (HII), describes a Search Engine Poisoning (SEP) campaign from start to finish. SEP abuses the ranking algorithms of search engines to promote an attacker-controlled Web site that contains malware. Imperva’s Application Defense Center (ADC) has witnessed these types of automated attack campaigns, which cause search engines to return high-ranking Web pages infected with malicious code that references an attacker-controlled Web site.
owasp_meetup_12_10

The document summarizes an OWASP and Rails Security meetup. It discusses common web application vulnerabilities like injection, cross-site scripting, insecure direct object references, missing authorization, cross-site request forgery, and unvalidated redirects. It provides examples of vulnerable code and solutions to prevent these issues. The document also introduces OWASP's Top 10 list of most critical web app vulnerabilities and tools like Brakeman and Code Climate that can detect vulnerabilities in Rails applications.
More Related Content
What's hot
NTXISSACSC3 - How I hacked the Government and Got Away with It by Seven Hatfield

NTXISSACSC3 - How I hacked the Government and Got Away with It by Seven HatfieldNorth Texas Chapter of the ISSA
This document summarizes how the speaker hacked into a government training website and downloaded training videos without authentication. They describe their multiple unsuccessful attempts to report the vulnerability to the government via email, Twitter, and other means. The document suggests ways for the government to improve security, such as implementing a bug bounty program, conducting code audits, and having a vulnerability management program. It concludes that the government is currently unresponsive to security issues and that improvements are needed to address vulnerabilities.How I Hacked The Government And Got Away With It

In this presentation I spoke about how I found an information disclosure vulnerability within a Federal CyberSecurity training website, was able to report it responsibly, and the issues that came up as I attempted to do so.
Stateless Anti-Csrf

The document discusses stateless anti-CSRF techniques. It proposes a "triple submit" approach where the server sets an HTTP-only cookie with a random name and value, tells the client the value but not name, and the client submits both the name and value as request parameters. However, an attacker can still bypass this via cross-site scripting (XSS) by overflowing the browser's cookie jar and overwriting the HTTP-only cookie. The document demonstrates how to do this in different browsers.
2018 Hacked Website Trends

Our Website Hacked Trend Report provides insights on the top open-source CMS security, out-of-date software, and specific malware families we see on hacked websites in the Sucuri environment.
We’ve built this analysis from prior reports to identify the latest tactics, techniques, and procedures (TTPs) detected by our Remediation Group. A total of 18,302 infected websites and 4,426,795 cleaned files were analyzed in our recent publication.
Tony will discuss high-level findings on a range of topics, including:
- Affected open-source CMS applications
- Outdated CMS and blacklist analysis
- Malware families and their effects
Grey H@t - Cross-site Request Forgery

Cross-site scripting (XSS) and cross-site request forgery (XSRF) are two related web application vulnerabilities. XSS involves injecting malicious scripts into a web application to steal user data or perform actions on the user's behalf. XSRF tricks authenticated users into performing actions in a web application by submitting forged requests, since their browser will automatically include authentication cookies. While mitigations like validating HTTP referrers can help prevent XSRF, XSS can still be used to bypass these by scraping tokens or directly launching attacks from within compromised pages. Together, XSS and XSRF pose serious risks if not properly mitigated in web applications that handle sensitive data or perform sensitive actions.
Sucuri Webinar: Simple Steps To Secure Your Online Store

During this webinar, we'll discuss some basic security concepts for your online store that include what tools you'll need to remain PCI compliant as well as how to keep your data safe. Some key takeaways will include:
- Reducing Your Attack Surface
- Protecting Cardholder Data
- Creating a Disaster Recovery Plan
We'll also identify principles and practices that can address multiple PCI requirements at once to help save time and effort.
Webinar: CWAF for Mid Market/Enterprise Organizations

In today's complex security landscape, web applications pose a significant risk to Mid-Market and Enterprise organizations.
The question is, how can an organization secure their web properties without sacrificing performance. The answer may be a Cloud-based Web Application Firewall.
This webinar will introduce the concept of the CWAF, and the benefits of web application security in the cloud.
Samples of topics covered include:
- What is a cloud-based web application firewall
- The benefits of using a CWAF
- How to improve security and performance
- How to implement a CWAF in complex web environments
This live Q&A-based webinar is designed for development managers, large websites with unique and complex infrastructure/server environments, and anyone who is concerned about securing their web applications.
Insights provided in the webinar will help you operate more secure networks, infrastructure, and web applications.
You can see the video recording of this webinar at the end of the slides.
CROSS-SITE REQUEST FORGERY - IN-DEPTH ANALYSIS 2011

Cross-Site Request Forgery (CSRF in short) is a kind of a web application vulnerability which allows malicious website to send unauthorized requests to a vulnerable website using active session of its authorized users.
VodQA3_PenetrationTesting_AmitDhakkad

This was a full length talk presented by Amit Dhakkad in vodQA-3 : A QA Meet held in ThoughtWorks, Pune.
AtlasCamp 2010: Securing your Plugin - Penny Wyatt

This document discusses common security vulnerabilities in plugins and how to prevent them. It covers cross-site scripting (XSS) vulnerabilities, which can allow attackers to run JavaScript in a victim's browser. It also discusses cross-site request forgery (XSRF) vulnerabilities, which trick a victim into performing unwanted actions. The document provides guidance on using HTML encoding, generating secure random numbers, restricting file system access, and other techniques to prevent these vulnerabilities. It focuses on securing plugins used in Atlassian products like JIRA, Confluence and Bamboo.
CSRF Attack and Its Prevention technique in ASP.NET MVC

As the name suggests Cross Site Request Forgery Attack deals with the forgery of the trusted website of an authorized user with unwanted action. . These attacks have been called the “sleeping giant” of web-based vulnerabilities, because many sites on the Internet fail to protect against them and because they have been largely ignored by the web development and security communities . Our project aims at attacking the victim user by including a link or script in a page that accesses a site to which the user is known or is supposed to have been authenticated. Deep analysis of CSRF attack and finding the possibilities to mitigate the CSRF attack is our main focus and our objective on this project.
What's hot (11)
NTXISSACSC3 - How I hacked the Government and Got Away with It by Seven Hatfield

NTXISSACSC3 - How I hacked the Government and Got Away with It by Seven Hatfield
Sucuri Webinar: Simple Steps To Secure Your Online Store

Sucuri Webinar: Simple Steps To Secure Your Online Store
Webinar: CWAF for Mid Market/Enterprise Organizations

Webinar: CWAF for Mid Market/Enterprise Organizations
CROSS-SITE REQUEST FORGERY - IN-DEPTH ANALYSIS 2011

CROSS-SITE REQUEST FORGERY - IN-DEPTH ANALYSIS 2011
AtlasCamp 2010: Securing your Plugin - Penny Wyatt

AtlasCamp 2010: Securing your Plugin - Penny Wyatt
CSRF Attack and Its Prevention technique in ASP.NET MVC

CSRF Attack and Its Prevention technique in ASP.NET MVC
Similar to Paper nctsn
Web spoofing (1)

Web spoofing allows an attacker to create a fake version of the World Wide Web to trick victims. The attacker lures victims to their fake site, which looks identical to the real site. On the fake site, the attacker can observe any sensitive information entered by the victim. Current browsers are vulnerable to web spoofing attacks even on secure connections. Users should disable JavaScript, always check the URL bar, and be wary of any requests for sensitive information over email.
A10 - Unvalidated Redirects and Forwards

A10 - Unvalidated Redirects and Forwards
IT6873
Southern Polytechnic State University
William Stanley
State of the Art Analysis Approach for Identification of the Malignant URLs

Malicious URLs have been universally used to ascend various cyber attacks including spamming, phishing and malware. Malware, short term for malicious software, is software which is developed to penetrate computers in a network without the user’s permission or notification. Existing methods typically detect malicious URLs of a single attack type. Hence such detection systems are failed to protect the users from various attacks. Malware spreading widely throughout the area of network as consequence of this it becomes predicament in distributed computer and network systems. Malicious links are the place of origin of all attacks which circulated all over the web. Hence malicious URLs should be detected for the prevention of users from these malware attacks. In this paper we described a novel approach which analyze all types of attacks by identifying malicious URLs and secure the web users from them. This technique prevents the users from malignant URLs before visiting them. Therefore efficiency of web security gets maintained. For such anatomization we developed an analyzer which identifies URLs and examine as malicious or benign. We also developed five processes which crawl for suspicious URLs. This approach will prevent the users from all types of attacks and increase efficiency of web crawling phase.
Web Application Penetration Tests - Vulnerability Identification and Details ...

These slides explain what the Vulnerability Identification stage consists of during a web application security assessment.
These slides are part of the course Introduction to Web Application Security and Penetration Testing with Netsparker, which can be found here: https://www.netsparker.com/blog/web-security/introduction-web-application-penetration-testing/
How not to make a hacker friendly application

Presentation on application security basics and some common vulnerabilities like XSS, SQL Injection, IDOR etc.
Web spoofing

Web spoofing allows an attacker to create a fake version of the entire web in order to trick victims. The attacker rewrites URLs on web pages so they link to the attacker's server instead of the real server. When the victim interacts with forms or links, their data and browsing is redirected to the attacker's server without their knowledge. While the victim sees secure connections, these are actually to the attacker's server, not the intended site. The attacker can then observe and modify any private information submitted by the victim.
Cookie surveillance

This document analyzes the privacy risks of mass surveillance by leveraging third-party HTTP tracking cookies. The researchers find that over 90% of a typical user's web visits can be linked together through shared unique cookies. Additionally, nearly half of popular websites leak a logged-in user's real identity in unencrypted traffic. This allows a passive network observer to cluster a user's entire browsing history and attach their real identity, violating expectations of privacy. The researchers discuss implications for targeted and mass surveillance online.
Unauthorized access, Men in the Middle (MITM)

In this type of attack, the attacker attempts to insert himself in the
middle of a communication for purposes of intercepting client’s data.
50063

Vulnerability Alert from Symantec reports that SilverStripe, an open source content management system, is prone to multiple cross-site scripting vulnerabilities in its admin URIs. This allows attackers to execute arbitrary script code in users' browsers to steal cookies or launch other attacks. The vulnerabilities are due to a failure to sanitize user input passed through various admin URIs. SilverStripe 2.4.5 is confirmed vulnerable.
Search Engine Poisoning

This report from Imperva’s Hacker Intelligence Initiative (HII), describes a Search Engine Poisoning (SEP) campaign from start to finish. SEP abuses the ranking algorithms of search engines to promote an attacker-controlled Web site that contains malware. Imperva’s Application Defense Center (ADC) has witnessed these types of automated attack campaigns, which cause search engines to return high-ranking Web pages infected with malicious code that references an attacker-controlled Web site.
owasp_meetup_12_10

The document summarizes an OWASP and Rails Security meetup. It discusses common web application vulnerabilities like injection, cross-site scripting, insecure direct object references, missing authorization, cross-site request forgery, and unvalidated redirects. It provides examples of vulnerable code and solutions to prevent these issues. The document also introduces OWASP's Top 10 list of most critical web app vulnerabilities and tools like Brakeman and Code Climate that can detect vulnerabilities in Rails applications.
SeanRobertsThesis

The document presents a hierarchical classification of web vulnerabilities organized into two main groups: general vulnerabilities that affect all web servers and service-specific vulnerabilities found in particular web server programs. General vulnerabilities are further divided into three sub-groups: feature abuse involving misuse of legitimate features, unvalidated input where user input is not checked before being processed, and improper design flaws. Validating user input and disabling vulnerable features can help eliminate certain vulnerability types like cross-site scripting resulting from unvalidated input or cross-site tracing from feature abuse. The hierarchy aims to help webmasters understand and address vulnerabilities by grouping similar issues.
Web Application Security

This document discusses web application security from the perspectives of web developers and attackers. It covers common issues web developers face, such as tight deadlines and lack of security standards. It also describes how attackers exploit vulnerabilities like injection attacks and XSS. Recent attacks are presented as examples, such as compromising a power grid operator's website through SQL injection. The document aims to raise awareness of web security challenges.
Pantallas escaneo Sitio Web

The document describes a vulnerability where the target server supports weak TLS/SSL ciphers and protocols, including SSLv2. This could allow attackers to decrypt encrypted communications and compromise sensitive data through man-in-the-middle attacks. Recommendations include disabling weak ciphers and protocols like SSLv2 to strengthen the security of encrypted connections.
OWASP

OWASP is an open community dedicated to enabling organizations to conceive, develop, acquire, operate, and maintain applications that can be trusted. All of the OWASP tools, documents, forums, and chapters are free and open to anyone interested in improving application security.
A8 cross site request forgery (csrf) it 6873 presentation

The document discusses Cross Site Request Forgery (CSRF) attacks. It defines CSRF as an attack where unauthorized commands are transmitted from a user that a website trusts. The attack forces a logged-in user's browser to send requests, including session cookies, to a vulnerable website. This allows the attacker to generate requests the site thinks are from the user. The document outlines how CSRF works, example attacks, defenses for users and applications, and myths about CSRF. It recommends using unpredictable CSRF tokens or re-authentication to prevent CSRF vulnerabilities.
OWASP Top 10 and Securing Rails - Sean Todd - PayNearMe.com

Silicon Valley Ruby on Rails Meetup - December 10th, 2013
OWASP Top 10 and Securing Rails
An introduction to the OWASP Top 10 and how to use it and other tools to secure your Rails code.
T04505103106

International Journal of Engineering Research and Applications (IJERA) is an open access online peer reviewed international journal that publishes research and review articles in the fields of Computer Science, Neural Networks, Electrical Engineering, Software Engineering, Information Technology, Mechanical Engineering, Chemical Engineering, Plastic Engineering, Food Technology, Textile Engineering, Nano Technology & science, Power Electronics, Electronics & Communication Engineering, Computational mathematics, Image processing, Civil Engineering, Structural Engineering, Environmental Engineering, VLSI Testing & Low Power VLSI Design etc.
A4 A K S H A Y B H A R D W A J

CSRF, or cross-site request forgery, occurs when a malicious website causes a user's browser to perform unintended actions on a website where the user is authenticated. Attackers can use CSRF to perform actions like transferring money from a user's bank account without their knowledge or consent. To prevent CSRF, websites should use POST requests instead of GET, assign random tokens for requests, and include CSRF protections in frameworks. Major sites have been vulnerable to CSRF in the past, so defenses against it are important.
Secure Form Processing and Protection - Devspace 2015 

Joe Ferguson discusses common web application vulnerabilities like cross-site scripting (XSS) and cross-site request forgery (CSRF). He explains different types of XSS exploits and how CSRF works. To prevent these issues, he recommends sanitizing user input, using cryptographic nonces, and leveraging security features in frameworks like Angular, Zend, Symfony, Laravel and others. He also provides examples of widespread exploits on sites like Twitter, Facebook and MySpace to demonstrate the importance of secure form processing.
Similar to Paper nctsn (20)
State of the Art Analysis Approach for Identification of the Malignant URLs

State of the Art Analysis Approach for Identification of the Malignant URLs
Web Application Penetration Tests - Vulnerability Identification and Details ...

Web Application Penetration Tests - Vulnerability Identification and Details ...
A8 cross site request forgery (csrf) it 6873 presentation

A8 cross site request forgery (csrf) it 6873 presentation
OWASP Top 10 and Securing Rails - Sean Todd - PayNearMe.com

OWASP Top 10 and Securing Rails - Sean Todd - PayNearMe.com
Secure Form Processing and Protection - Devspace 2015 

Secure Form Processing and Protection - Devspace 2015
Recently uploaded
Connector Corner: Seamlessly power UiPath Apps, GenAI with prebuilt connectors

Join us to learn how UiPath Apps can directly and easily interact with prebuilt connectors via Integration Service--including Salesforce, ServiceNow, Open GenAI, and more.
The best part is you can achieve this without building a custom workflow! Say goodbye to the hassle of using separate automations to call APIs. By seamlessly integrating within App Studio, you can now easily streamline your workflow, while gaining direct access to our Connector Catalog of popular applications.
We’ll discuss and demo the benefits of UiPath Apps and connectors including:
Creating a compelling user experience for any software, without the limitations of APIs.
Accelerating the app creation process, saving time and effort
Enjoying high-performance CRUD (create, read, update, delete) operations, for
seamless data management.
Speakers:
Russell Alfeche, Technology Leader, RPA at qBotic and UiPath MVP
Charlie Greenberg, host
zkStudyClub - LatticeFold: A Lattice-based Folding Scheme and its Application...

Folding is a recent technique for building efficient recursive SNARKs. Several elegant folding protocols have been proposed, such as Nova, Supernova, Hypernova, Protostar, and others. However, all of them rely on an additively homomorphic commitment scheme based on discrete log, and are therefore not post-quantum secure. In this work we present LatticeFold, the first lattice-based folding protocol based on the Module SIS problem. This folding protocol naturally leads to an efficient recursive lattice-based SNARK and an efficient PCD scheme. LatticeFold supports folding low-degree relations, such as R1CS, as well as high-degree relations, such as CCS. The key challenge is to construct a secure folding protocol that works with the Ajtai commitment scheme. The difficulty, is ensuring that extracted witnesses are low norm through many rounds of folding. We present a novel technique using the sumcheck protocol to ensure that extracted witnesses are always low norm no matter how many rounds of folding are used. Our evaluation of the final proof system suggests that it is as performant as Hypernova, while providing post-quantum security.
Paper Link: https://eprint.iacr.org/2024/257
Demystifying Knowledge Management through Storytelling

The Department of Veteran Affairs (VA) invited Taylor Paschal, Knowledge & Information Management Consultant at Enterprise Knowledge, to speak at a Knowledge Management Lunch and Learn hosted on June 12, 2024. All Office of Administration staff were invited to attend and received professional development credit for participating in the voluntary event.
The objectives of the Lunch and Learn presentation were to:
- Review what KM ‘is’ and ‘isn’t’
- Understand the value of KM and the benefits of engaging
- Define and reflect on your “what’s in it for me?”
- Share actionable ways you can participate in Knowledge - - Capture & Transfer
Fueling AI with Great Data with Airbyte Webinar

This talk will focus on how to collect data from a variety of sources, leveraging this data for RAG and other GenAI use cases, and finally charting your course to productionalization.
Crafting Excellence: A Comprehensive Guide to iOS Mobile App Development Serv...

Crafting Excellence: A Comprehensive Guide to iOS Mobile App Development Serv...Pitangent Analytics & Technology Solutions Pvt. Ltd
Discover top-tier mobile app development services, offering innovative solutions for iOS and Android. Enhance your business with custom, user-friendly mobile applications."Frontline Battles with DDoS: Best practices and Lessons Learned", Igor Ivaniuk

At this talk we will discuss DDoS protection tools and best practices, discuss network architectures and what AWS has to offer. Also, we will look into one of the largest DDoS attacks on Ukrainian infrastructure that happened in February 2022. We'll see, what techniques helped to keep the web resources available for Ukrainians and how AWS improved DDoS protection for all customers based on Ukraine experience
Columbus Data & Analytics Wednesdays - June 2024

Columbus Data & Analytics Wednesdays, June 2024 with Maria Copot 20
Astute Business Solutions | Oracle Cloud Partner |

Your goto partner for Oracle Cloud, PeopleSoft, E-Business Suite, and Ellucian Banner. We are a firm specialized in managed services and consulting.
Apps Break Data

How information systems are built or acquired puts information, which is what they should be about, in a secondary place. Our language adapted accordingly, and we no longer talk about information systems but applications. Applications evolved in a way to break data into diverse fragments, tightly coupled with applications and expensive to integrate. The result is technical debt, which is re-paid by taking even bigger "loans", resulting in an ever-increasing technical debt. Software engineering and procurement practices work in sync with market forces to maintain this trend. This talk demonstrates how natural this situation is. The question is: can something be done to reverse the trend?
LF Energy Webinar: Carbon Data Specifications: Mechanisms to Improve Data Acc...

This LF Energy webinar took place June 20, 2024. It featured:
-Alex Thornton, LF Energy
-Hallie Cramer, Google
-Daniel Roesler, UtilityAPI
-Henry Richardson, WattTime
In response to the urgency and scale required to effectively address climate change, open source solutions offer significant potential for driving innovation and progress. Currently, there is a growing demand for standardization and interoperability in energy data and modeling. Open source standards and specifications within the energy sector can also alleviate challenges associated with data fragmentation, transparency, and accessibility. At the same time, it is crucial to consider privacy and security concerns throughout the development of open source platforms.
This webinar will delve into the motivations behind establishing LF Energy’s Carbon Data Specification Consortium. It will provide an overview of the draft specifications and the ongoing progress made by the respective working groups.
Three primary specifications will be discussed:
-Discovery and client registration, emphasizing transparent processes and secure and private access
-Customer data, centering around customer tariffs, bills, energy usage, and full consumption disclosure
-Power systems data, focusing on grid data, inclusive of transmission and distribution networks, generation, intergrid power flows, and market settlement data
Skybuffer SAM4U tool for SAP license adoption

Manage and optimize your license adoption and consumption with SAM4U, an SAP free customer software asset management tool.
SAM4U, an SAP complimentary software asset management tool for customers, delivers a detailed and well-structured overview of license inventory and usage with a user-friendly interface. We offer a hosted, cost-effective, and performance-optimized SAM4U setup in the Skybuffer Cloud environment. You retain ownership of the system and data, while we manage the ABAP 7.58 infrastructure, ensuring fixed Total Cost of Ownership (TCO) and exceptional services through the SAP Fiori interface.
The Microsoft 365 Migration Tutorial For Beginner.pptx

This presentation will help you understand the power of Microsoft 365. However, we have mentioned every productivity app included in Office 365. Additionally, we have suggested the migration situation related to Office 365 and how we can help you.
You can also read: https://www.systoolsgroup.com/updates/office-365-tenant-to-tenant-migration-step-by-step-complete-guide/
JavaLand 2024: Application Development Green Masterplan

My presentation slides I used at JavaLand 2024
Introduction of Cybersecurity with OSS at Code Europe 2024

I develop the Ruby programming language, RubyGems, and Bundler, which are package managers for Ruby. Today, I will introduce how to enhance the security of your application using open-source software (OSS) examples from Ruby and RubyGems.
The first topic is CVE (Common Vulnerabilities and Exposures). I have published CVEs many times. But what exactly is a CVE? I'll provide a basic understanding of CVEs and explain how to detect and handle vulnerabilities in OSS.
Next, let's discuss package managers. Package managers play a critical role in the OSS ecosystem. I'll explain how to manage library dependencies in your application.
I'll share insights into how the Ruby and RubyGems core team works to keep our ecosystem safe. By the end of this talk, you'll have a better understanding of how to safeguard your code.
inQuba Webinar Mastering Customer Journey Management with Dr Graham Hill

HERE IS YOUR WEBINAR CONTENT! 'Mastering Customer Journey Management with Dr. Graham Hill'. We hope you find the webinar recording both insightful and enjoyable.
In this webinar, we explored essential aspects of Customer Journey Management and personalization. Here’s a summary of the key insights and topics discussed:
Key Takeaways:
Understanding the Customer Journey: Dr. Hill emphasized the importance of mapping and understanding the complete customer journey to identify touchpoints and opportunities for improvement.
Personalization Strategies: We discussed how to leverage data and insights to create personalized experiences that resonate with customers.
Technology Integration: Insights were shared on how inQuba’s advanced technology can streamline customer interactions and drive operational efficiency.
Leveraging the Graph for Clinical Trials and Standards

Katja Glaß
OpenStudyBuilder Community Manager - Katja Glaß Consulting
Marius Conjeaud
Principal Consultant - Neo4j
[OReilly Superstream] Occupy the Space: A grassroots guide to engineering (an...![[OReilly Superstream] Occupy the Space: A grassroots guide to engineering (an...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[OReilly Superstream] Occupy the Space: A grassroots guide to engineering (an...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
The typical problem in product engineering is not bad strategy, so much as “no strategy”. This leads to confusion, lack of motivation, and incoherent action. The next time you look for a strategy and find an empty space, instead of waiting for it to be filled, I will show you how to fill it in yourself. If you’re wrong, it forces a correction. If you’re right, it helps create focus. I’ll share how I’ve approached this in the past, both what works and lessons for what didn’t work so well.
Must Know Postgres Extension for DBA and Developer during Migration

Mydbops Opensource Database Meetup 16
Topic: Must-Know PostgreSQL Extensions for Developers and DBAs During Migration
Speaker: Deepak Mahto, Founder of DataCloudGaze Consulting
Date & Time: 8th June | 10 AM - 1 PM IST
Venue: Bangalore International Centre, Bangalore
Abstract: Discover how PostgreSQL extensions can be your secret weapon! This talk explores how key extensions enhance database capabilities and streamline the migration process for users moving from other relational databases like Oracle.
Key Takeaways:
* Learn about crucial extensions like oracle_fdw, pgtt, and pg_audit that ease migration complexities.
* Gain valuable strategies for implementing these extensions in PostgreSQL to achieve license freedom.
* Discover how these key extensions can empower both developers and DBAs during the migration process.
* Don't miss this chance to gain practical knowledge from an industry expert and stay updated on the latest open-source database trends.
Mydbops Managed Services specializes in taking the pain out of database management while optimizing performance. Since 2015, we have been providing top-notch support and assistance for the top three open-source databases: MySQL, MongoDB, and PostgreSQL.
Our team offers a wide range of services, including assistance, support, consulting, 24/7 operations, and expertise in all relevant technologies. We help organizations improve their database's performance, scalability, efficiency, and availability.
Contact us: info@mydbops.com
Visit: https://www.mydbops.com/
Follow us on LinkedIn: https://in.linkedin.com/company/mydbops
For more details and updates, please follow up the below links.
Meetup Page : https://www.meetup.com/mydbops-databa...
Twitter: https://twitter.com/mydbopsofficial
Blogs: https://www.mydbops.com/blog/
Facebook(Meta): https://www.facebook.com/mydbops/
5th LF Energy Power Grid Model Meet-up Slides

5th Power Grid Model Meet-up
It is with great pleasure that we extend to you an invitation to the 5th Power Grid Model Meet-up, scheduled for 6th June 2024. This event will adopt a hybrid format, allowing participants to join us either through an online Mircosoft Teams session or in person at TU/e located at Den Dolech 2, Eindhoven, Netherlands. The meet-up will be hosted by Eindhoven University of Technology (TU/e), a research university specializing in engineering science & technology.
Power Grid Model
The global energy transition is placing new and unprecedented demands on Distribution System Operators (DSOs). Alongside upgrades to grid capacity, processes such as digitization, capacity optimization, and congestion management are becoming vital for delivering reliable services.
Power Grid Model is an open source project from Linux Foundation Energy and provides a calculation engine that is increasingly essential for DSOs. It offers a standards-based foundation enabling real-time power systems analysis, simulations of electrical power grids, and sophisticated what-if analysis. In addition, it enables in-depth studies and analysis of the electrical power grid’s behavior and performance. This comprehensive model incorporates essential factors such as power generation capacity, electrical losses, voltage levels, power flows, and system stability.
Power Grid Model is currently being applied in a wide variety of use cases, including grid planning, expansion, reliability, and congestion studies. It can also help in analyzing the impact of renewable energy integration, assessing the effects of disturbances or faults, and developing strategies for grid control and optimization.
What to expect
For the upcoming meetup we are organizing, we have an exciting lineup of activities planned:
-Insightful presentations covering two practical applications of the Power Grid Model.
-An update on the latest advancements in Power Grid -Model technology during the first and second quarters of 2024.
-An interactive brainstorming session to discuss and propose new feature requests.
-An opportunity to connect with fellow Power Grid Model enthusiasts and users.
Recently uploaded (20)
Connector Corner: Seamlessly power UiPath Apps, GenAI with prebuilt connectors

Connector Corner: Seamlessly power UiPath Apps, GenAI with prebuilt connectors
zkStudyClub - LatticeFold: A Lattice-based Folding Scheme and its Application...

zkStudyClub - LatticeFold: A Lattice-based Folding Scheme and its Application...
Demystifying Knowledge Management through Storytelling

Demystifying Knowledge Management through Storytelling
Crafting Excellence: A Comprehensive Guide to iOS Mobile App Development Serv...

Crafting Excellence: A Comprehensive Guide to iOS Mobile App Development Serv...
"Frontline Battles with DDoS: Best practices and Lessons Learned", Igor Ivaniuk

"Frontline Battles with DDoS: Best practices and Lessons Learned", Igor Ivaniuk
Astute Business Solutions | Oracle Cloud Partner |

Astute Business Solutions | Oracle Cloud Partner |
LF Energy Webinar: Carbon Data Specifications: Mechanisms to Improve Data Acc...

LF Energy Webinar: Carbon Data Specifications: Mechanisms to Improve Data Acc...
The Microsoft 365 Migration Tutorial For Beginner.pptx

The Microsoft 365 Migration Tutorial For Beginner.pptx
9 CEO's who hit $100m ARR Share Their Top Growth Tactics Nathan Latka, Founde...

9 CEO's who hit $100m ARR Share Their Top Growth Tactics Nathan Latka, Founde...
JavaLand 2024: Application Development Green Masterplan

JavaLand 2024: Application Development Green Masterplan
Introduction of Cybersecurity with OSS at Code Europe 2024

Introduction of Cybersecurity with OSS at Code Europe 2024
inQuba Webinar Mastering Customer Journey Management with Dr Graham Hill

inQuba Webinar Mastering Customer Journey Management with Dr Graham Hill
Leveraging the Graph for Clinical Trials and Standards

Leveraging the Graph for Clinical Trials and Standards
[OReilly Superstream] Occupy the Space: A grassroots guide to engineering (an...![[OReilly Superstream] Occupy the Space: A grassroots guide to engineering (an...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[OReilly Superstream] Occupy the Space: A grassroots guide to engineering (an...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[OReilly Superstream] Occupy the Space: A grassroots guide to engineering (an...
Must Know Postgres Extension for DBA and Developer during Migration

Must Know Postgres Extension for DBA and Developer during Migration
Paper nctsn
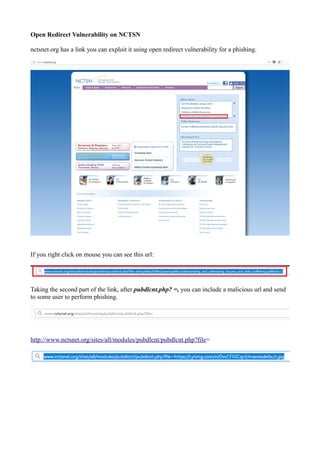
- 1. Open Redirect Vulnerability on NCTSN nctsnet.org has a link you can exploit it using open redirect vulnerability for a phishing. If you right click on mouse you can see this url: Taking the second part of the link, after pubdlcnt.php? =, you can include a malicious url and send to some user to perform phishing. http://www.nctsnet.org/sites/all/modules/pubdlcnt/pubdlcnt.php?file=
- 2. Analyzing the source code, we can observe that there is no validation or verification of the link to where the user will be redirected. But what are Open Redirect Vulnerabilities? An open redirect vulnerability occurs when a victim visits a particular URL for a given website and that website instructs the victim’s browser to visit a completely different URL, on a separate domain. When you visit the URL, the main page would receive a GET HTTP request and use the variable to parameter's value to determine where the visitor's browser should be redirected. After doing só, another page would return a 302 HTTP response, instructing the user's broswer to make a GET request to another page, the variable parameter's value. The Open Web Application Security Project (OWASP), which is a community dedicated to application security that curates a list of the most critical security flaws in web applications, has listed this vulnerability in ther 2014 Top Ten vulnerabilities list. Open redirects exploit the trust of a given domain, www.nctsnet.org, to lure victims to a malicious website. This can be used in phishing attack to trick users into believing theu are submitting information to the trusted site, when their valuable information is actually going to a malicious site. This also enables attackers to distribute malware from the malicious site or steal Oauth tokens.
- 3. Not all vulnerabilities are complex. This open redirect simply required changing the domain_name parameter to an external site, which would have resulted in a user being redirected off-site from NCTSNET. This type of vulnerability relies on an abuse of trust, where victims are tricked into visiting an attacker's site thinking they will be visiting a site they recognize. When you spot likely vulnerable parameters, be sure to test them out thoroughly and add special characters, like a period, if some part of the URL is hard-coded.