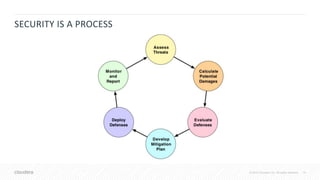
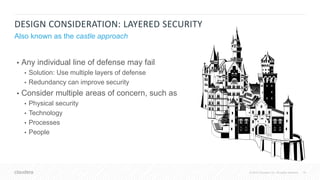
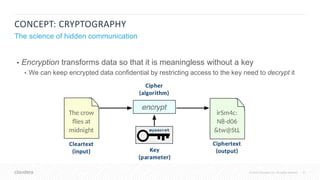
The Cloudera Security Training Course teaches essential security principles and tools for managing security in Cloudera's platform. It is delivered through on-demand formats and targets system administrators with a background in Linux, focusing on skills like threat assessment, data encryption, and access control. Topics covered include security architecture, authentication with Kerberos, and the use of Apache Sentry for authorization.