Embed presentation
Downloaded 22 times


















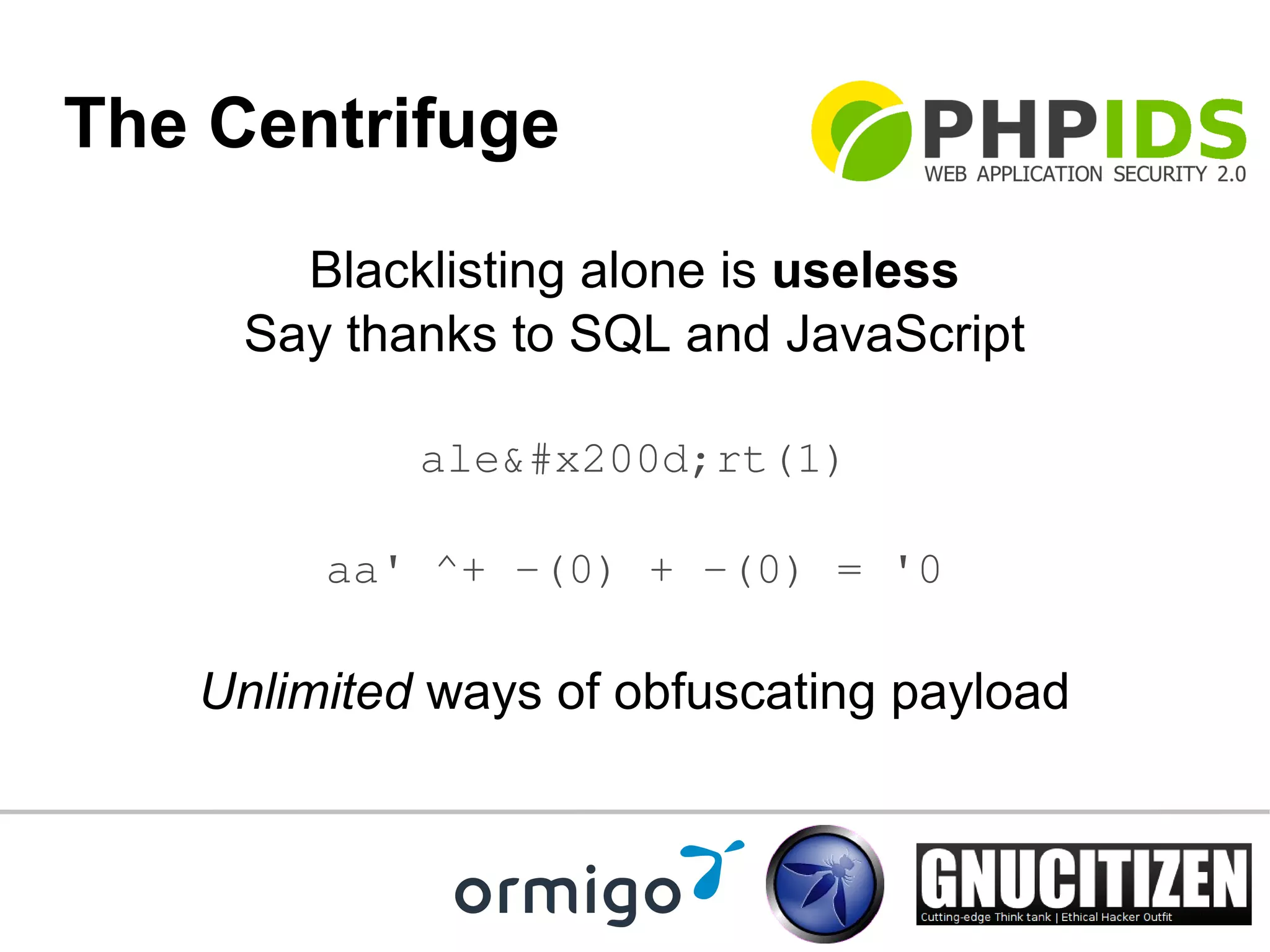





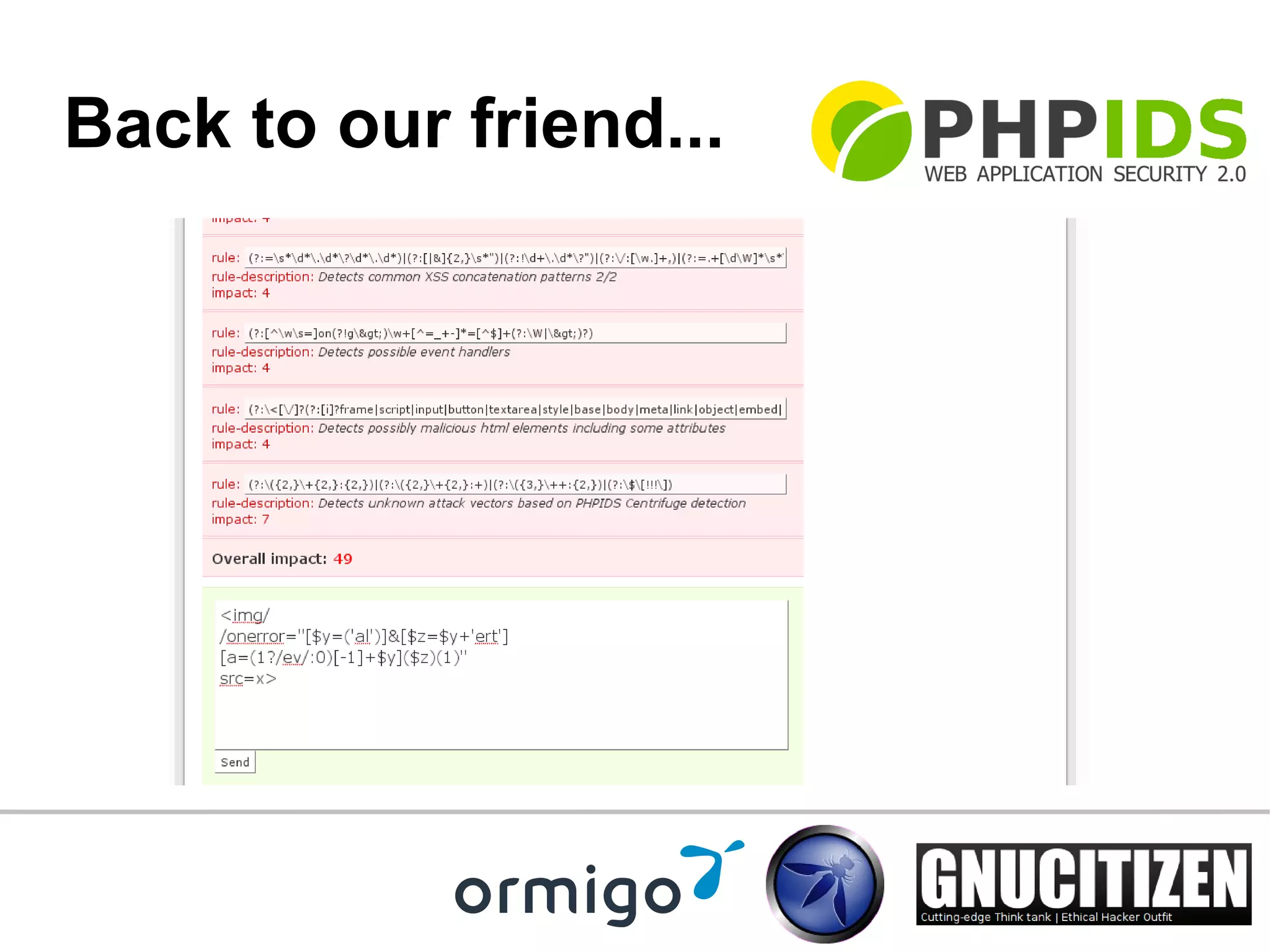




This document summarizes a presentation about PHPIDS, a tool that monitors websites for attack surface activity and detects bad inputs to help secure PHP applications. PHPIDS uses over 70 regular expressions to detect attacks like XSS, SQL injection and others. It analyzes, converts and normalizes inputs before matching them against rulesets. PHPIDS is lightweight, free and open source. It is used on many popular websites and has an active community of developers constantly improving it through testing.


































