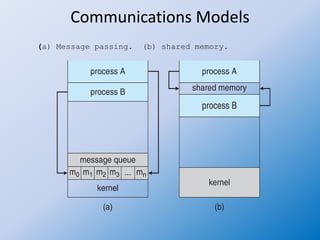
The document discusses interprocess communication (IPC) in operating systems, focusing on cooperating processes and their communication methods. It explains models of IPC, such as shared memory and message passing, along with synchronization issues and examples like the producer-consumer problem. Additionally, it differentiates between direct and indirect communication, outlining how messages are sent and received, and the implications of blocking versus non-blocking operations.




![Bounded-Buffer –
Shared-Memory Solution
• Shared data
#define BUFFER_SIZE 10
typedef struct {
. . .
} item;
item buffer[BUFFER_SIZE];
int in = 0;
int out = 0;
• Solution is correct, but can only use BUFFER_SIZE-1 elements](https://image.slidesharecdn.com/operatingsystem19interactingprocessesandipc-210603193457/85/Operating-system-19-interacting-processes-and-ipc-7-320.jpg)
![Bounded-Buffer – Producer
item next_produced;
while (true) {
/* produce an item in next produced */
while (((in + 1) % BUFFER_SIZE) == out)
; /* do nothing */
buffer[in] = next_produced;
in = (in + 1) % BUFFER_SIZE;
}](https://image.slidesharecdn.com/operatingsystem19interactingprocessesandipc-210603193457/85/Operating-system-19-interacting-processes-and-ipc-8-320.jpg)
![Bounded Buffer – Consumer
item next_consumed;
while (true) {
while (in == out)
; /* do nothing */
next_consumed = buffer[out];
out = (out + 1) % BUFFER_SIZE;
/* consume the item in next consumed */
}](https://image.slidesharecdn.com/operatingsystem19interactingprocessesandipc-210603193457/85/Operating-system-19-interacting-processes-and-ipc-9-320.jpg)











