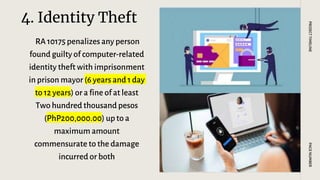
The document discusses online safety and cybercrime laws in the Philippines. It outlines key provisions of Republic Act 10175, also known as the Cybercrime Prevention Act of 2012. The Act aims to address legal issues concerning online interactions and defines cybercrimes such as illegal access, cybersex, child pornography, cyber squatting, and identity theft. It establishes penalties for perpetrators and grants law enforcement authorities expanded powers to investigate cybercrimes. The document also provides tips for being a safe and responsible digital citizen online.