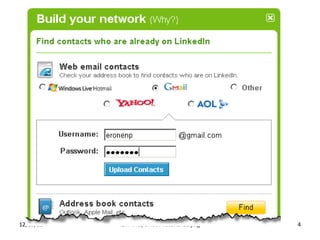
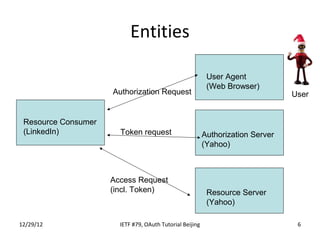
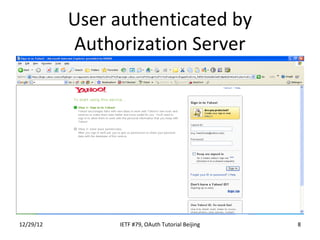
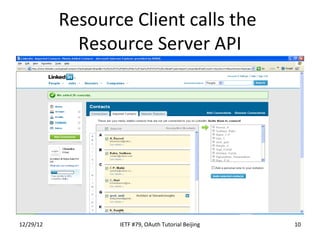
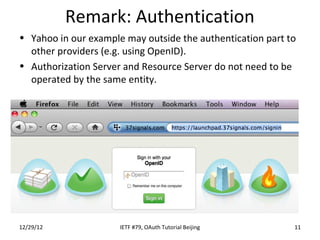
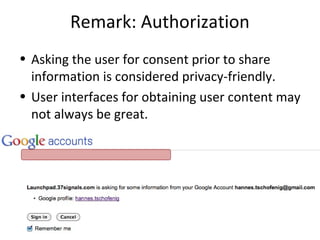
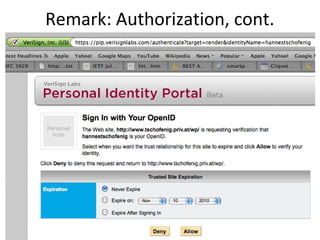
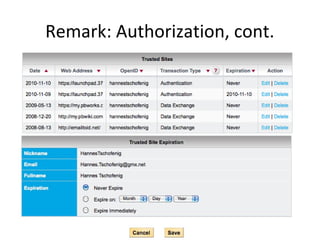
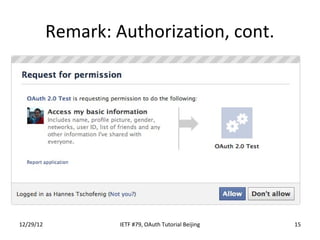
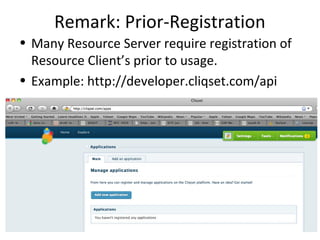
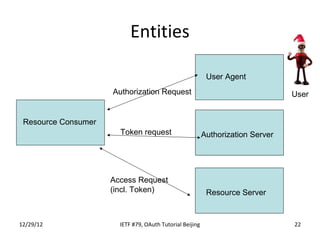
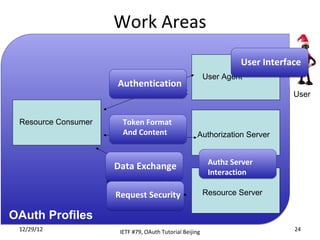
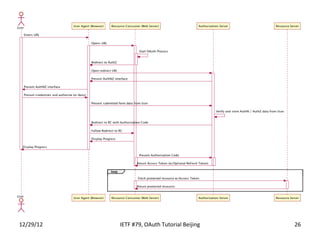
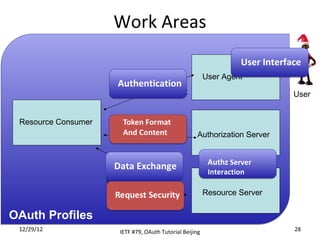
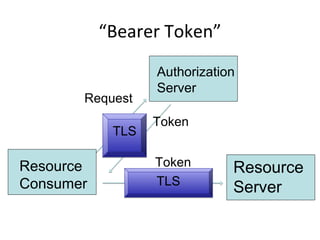
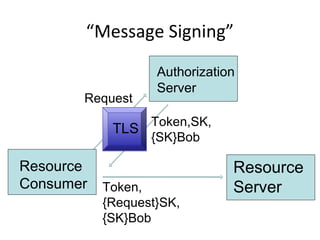
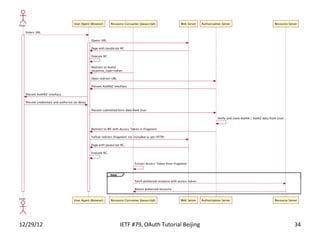
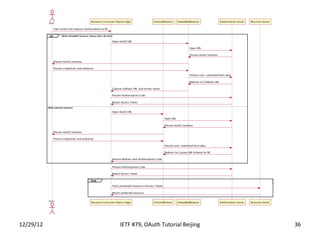
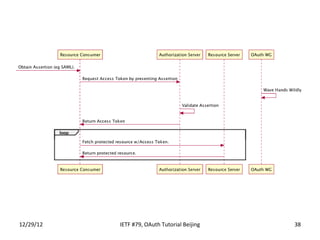
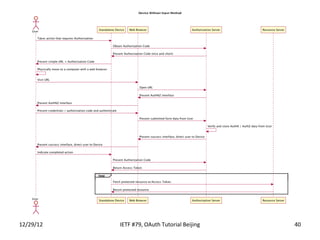
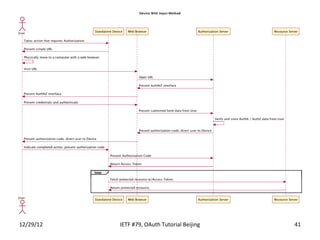
The document summarizes an OAuth tutorial presentation given at IETF #79 in Beijing. It discusses the problem of secure data sharing that OAuth addresses, provides examples of OAuth flows and exchanges, and describes the involved entities. The history of OAuth is outlined, from its inception in 2006 to its standardization efforts in the IETF. Security aspects like access tokens and message signing are also summarized.