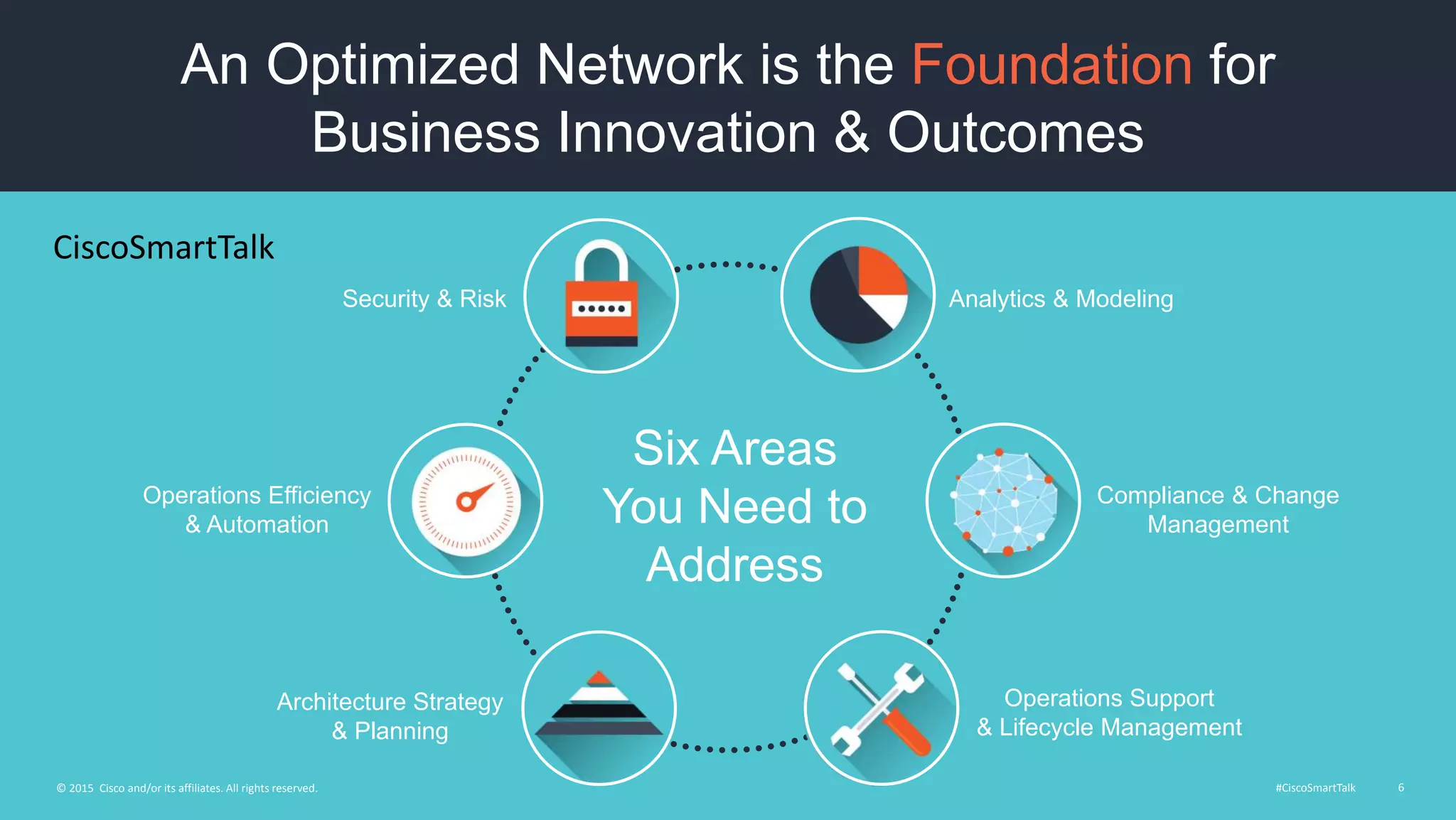
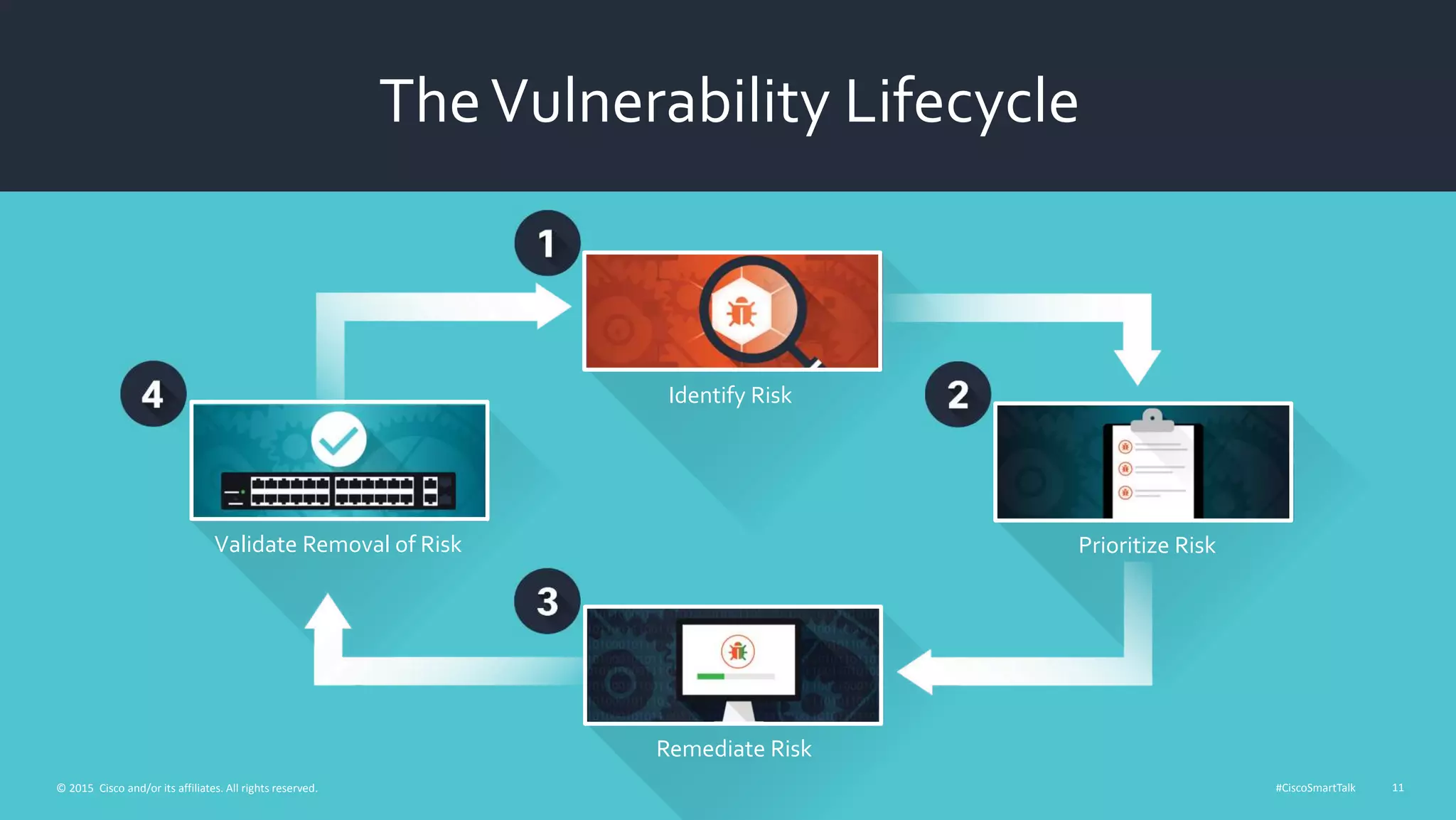
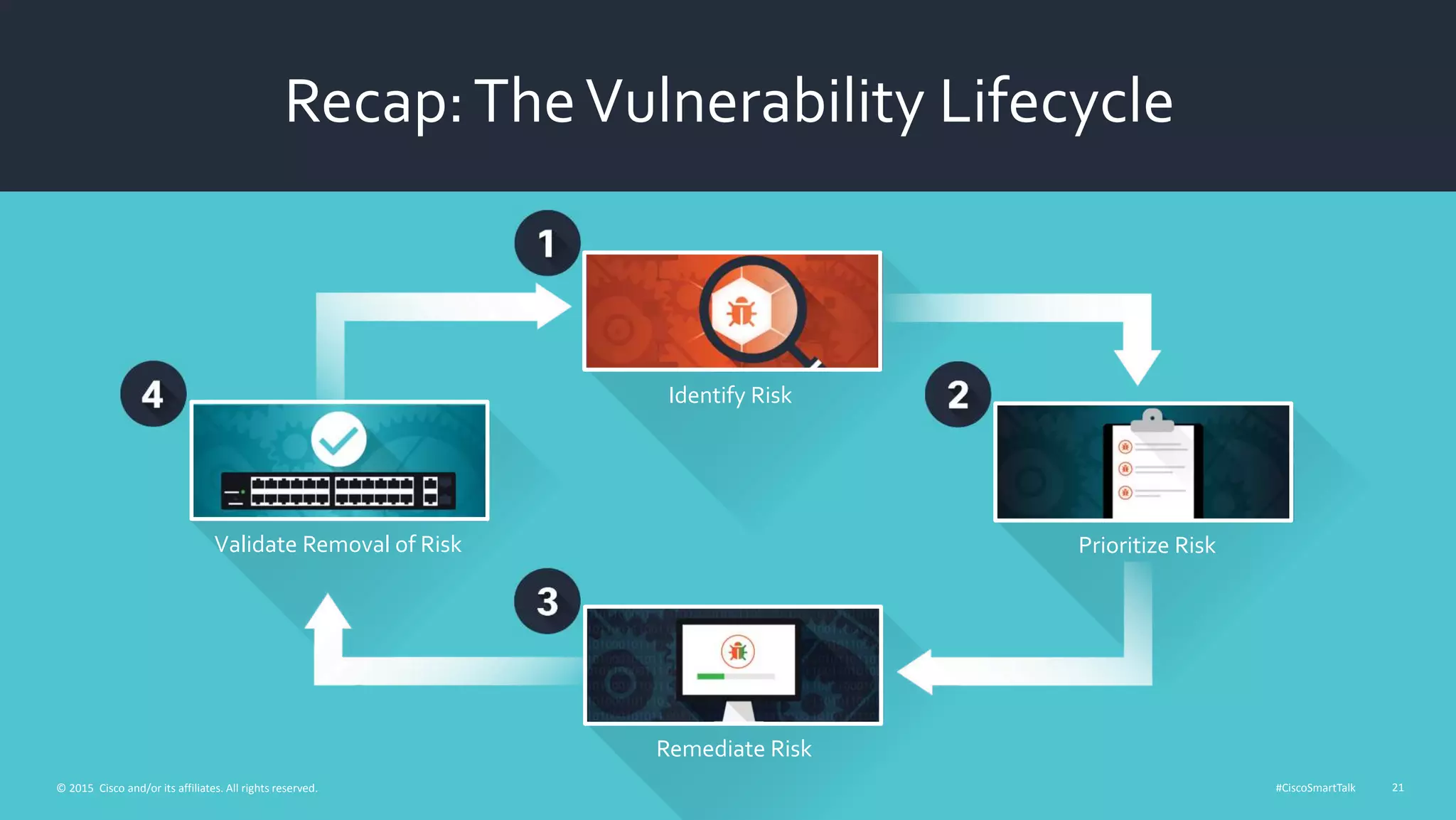
This document outlines a webinar from Cisco on reducing security risks to protect networks. The webinar will discuss assessing and evolving security strategies, maintaining security postures, and security services to prepare networks. It promotes following the vulnerability lifecycle of identifying, prioritizing, remediating, and validating the removal of risks. The webinar will also cover Cisco's security services to help secure networks.