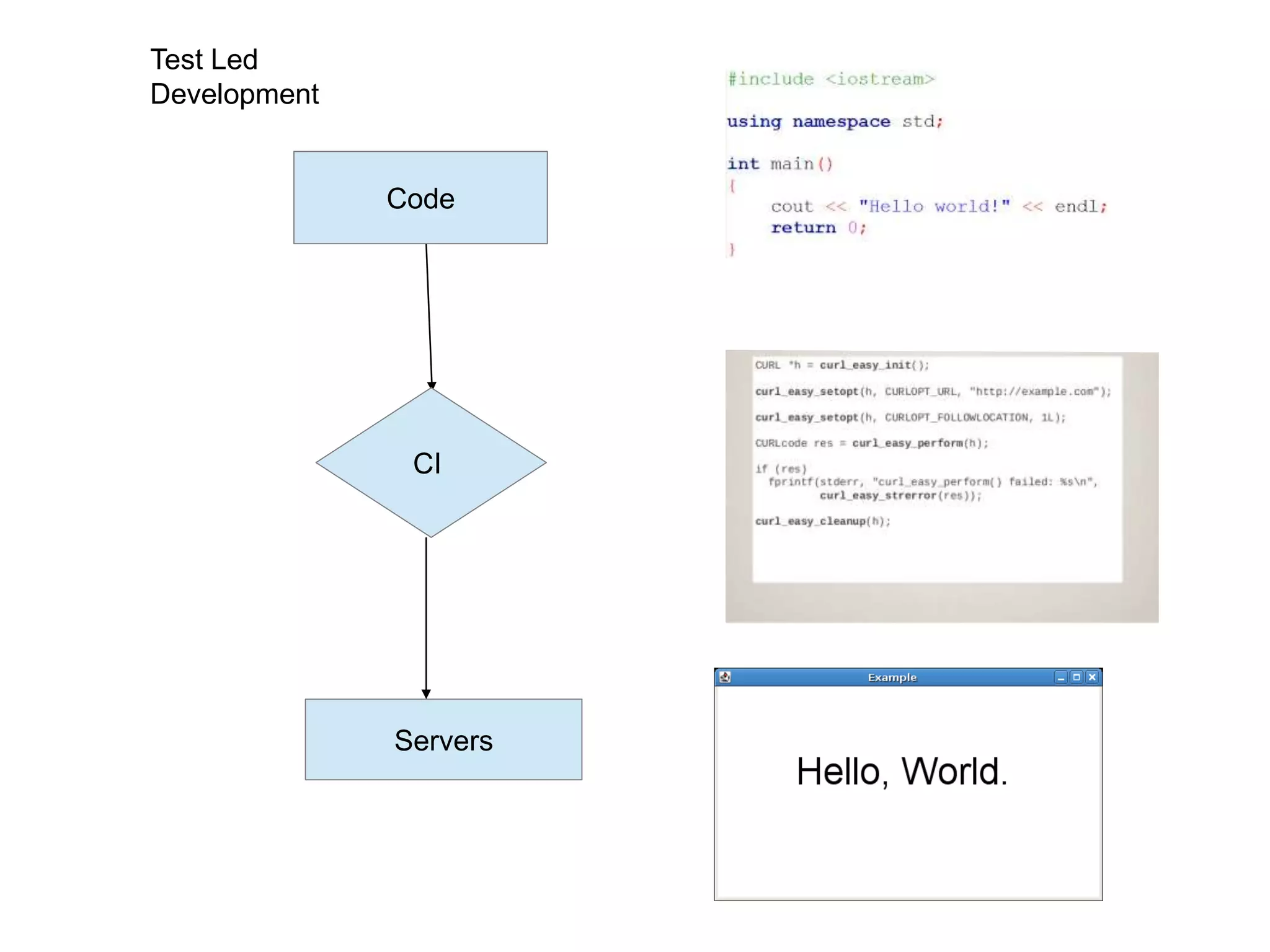
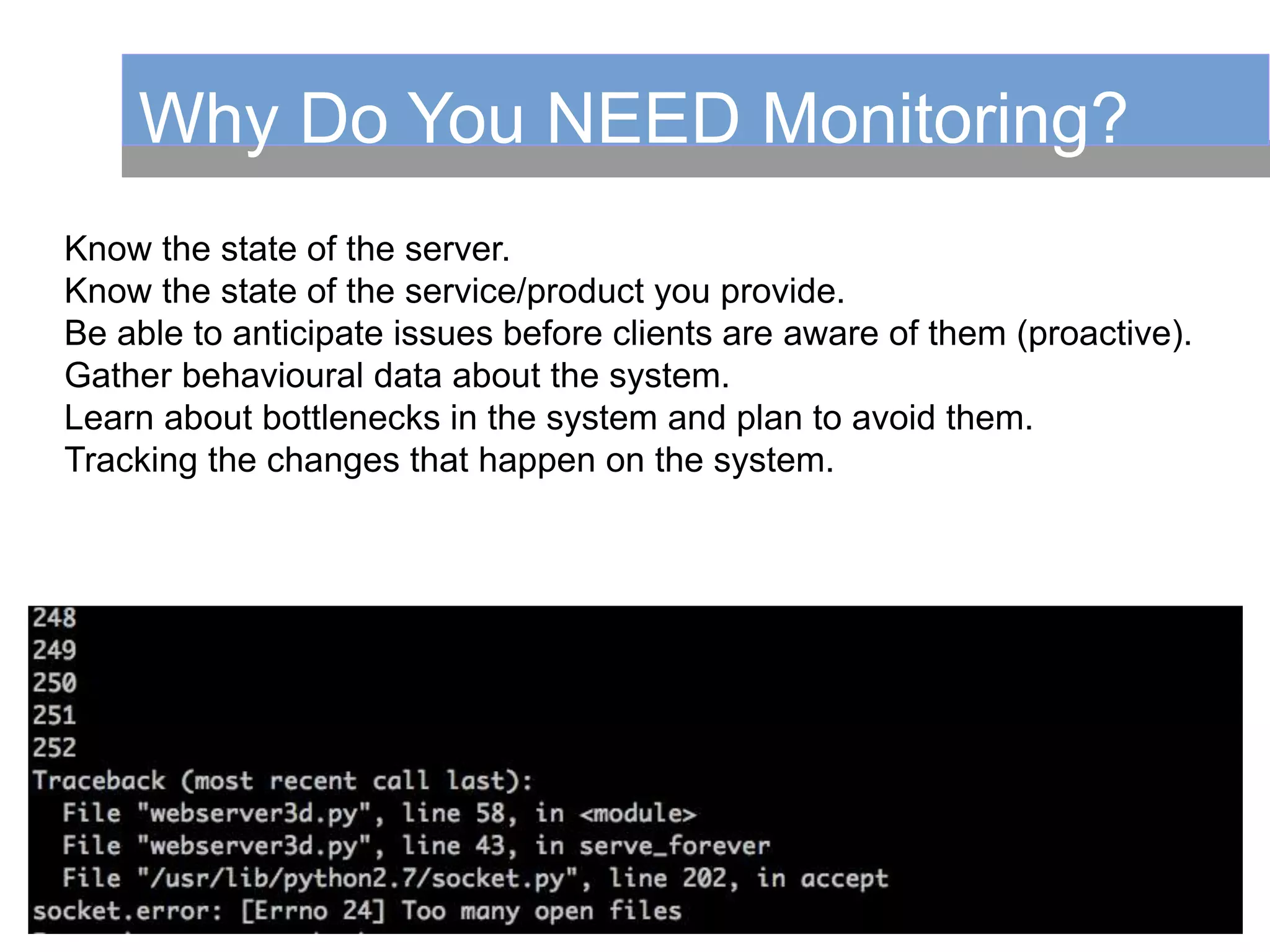
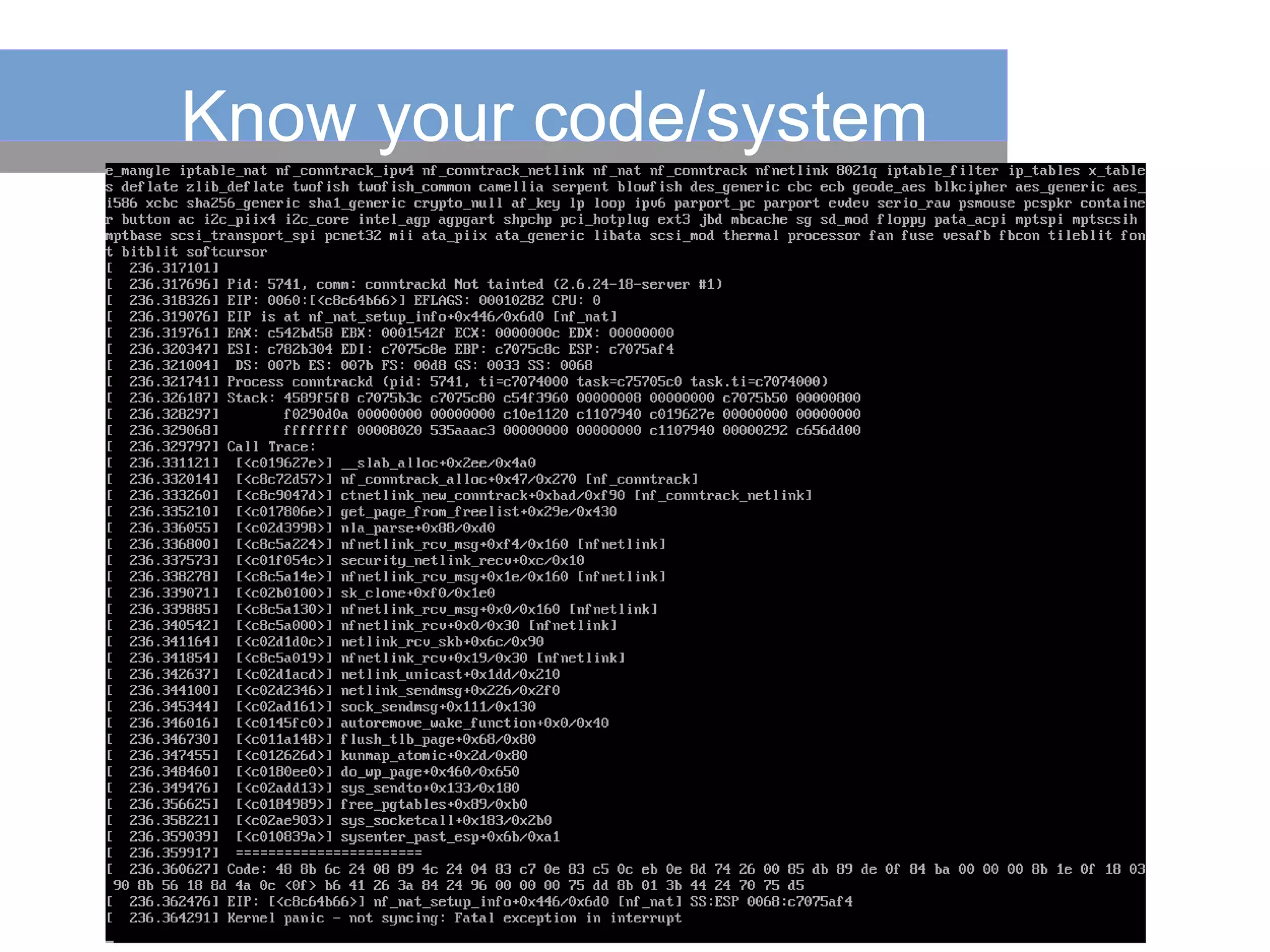
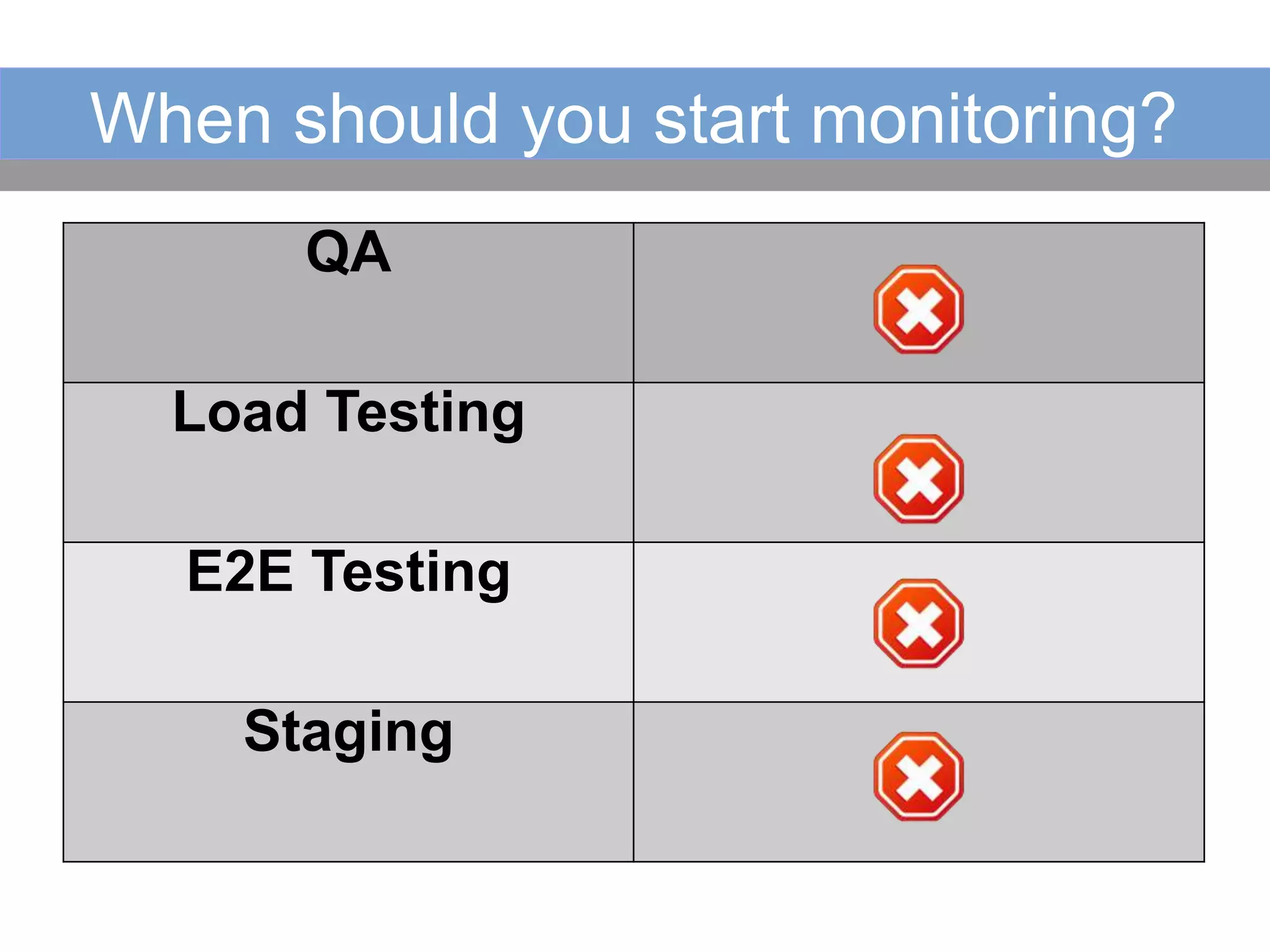
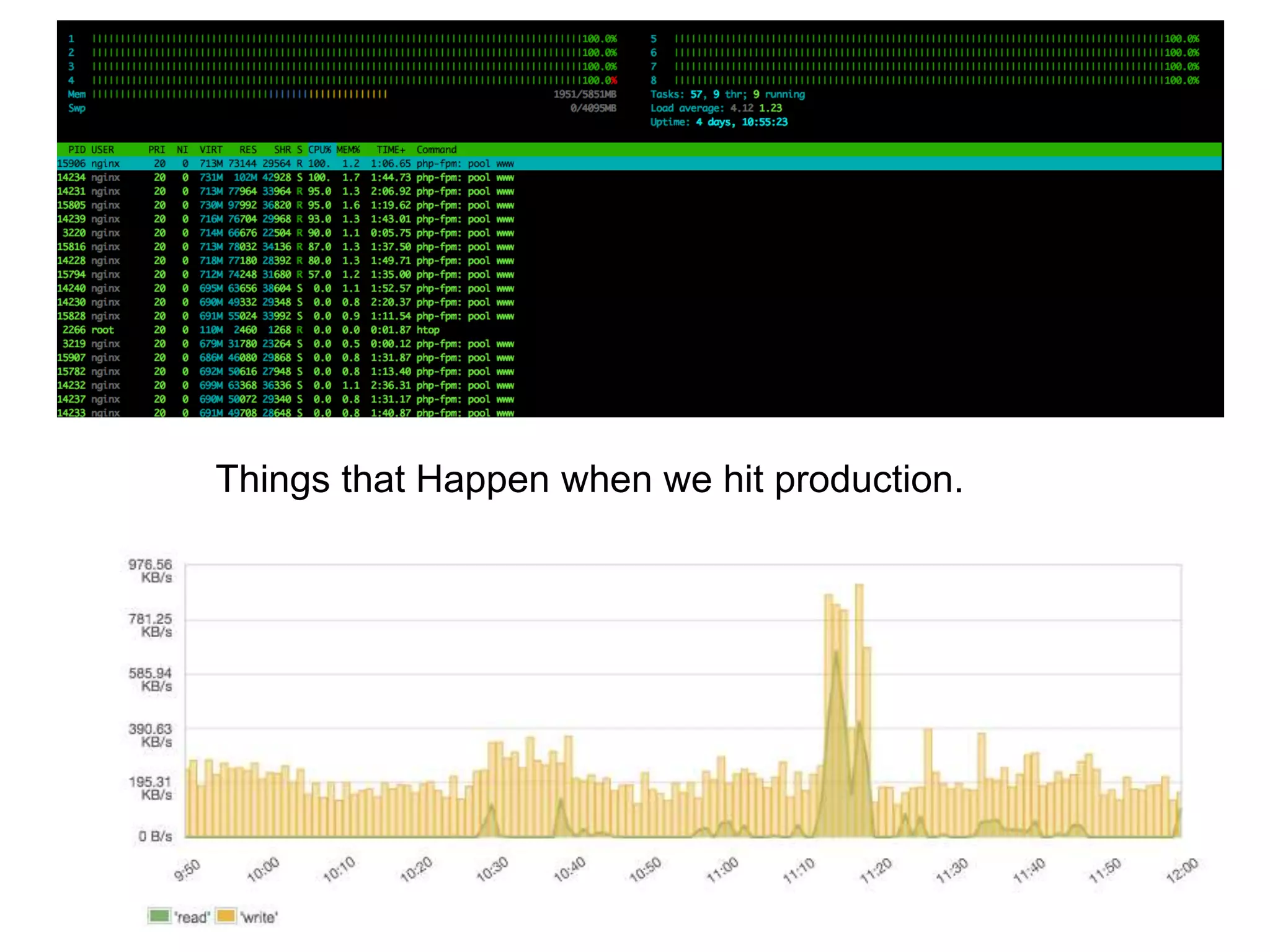
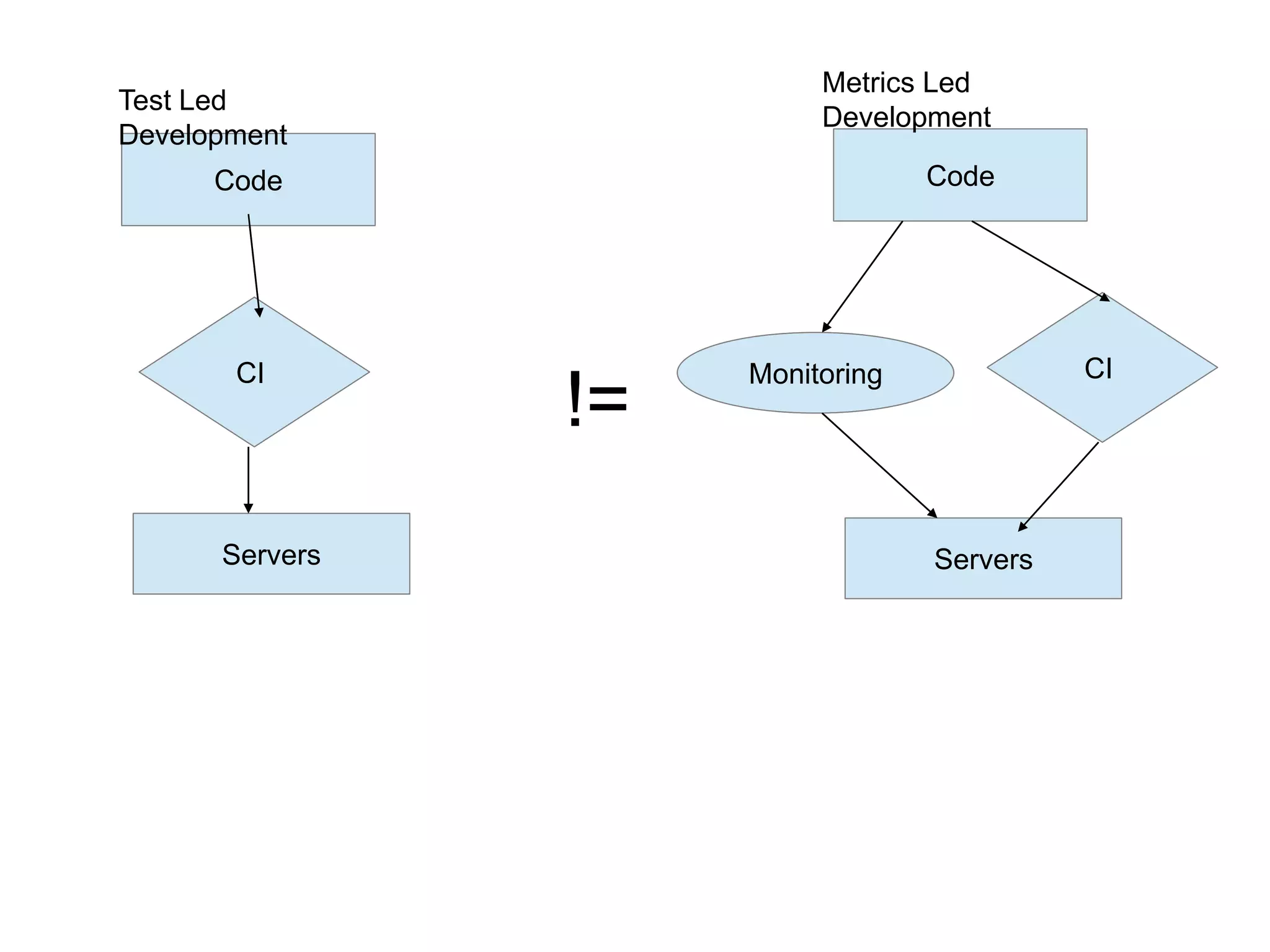
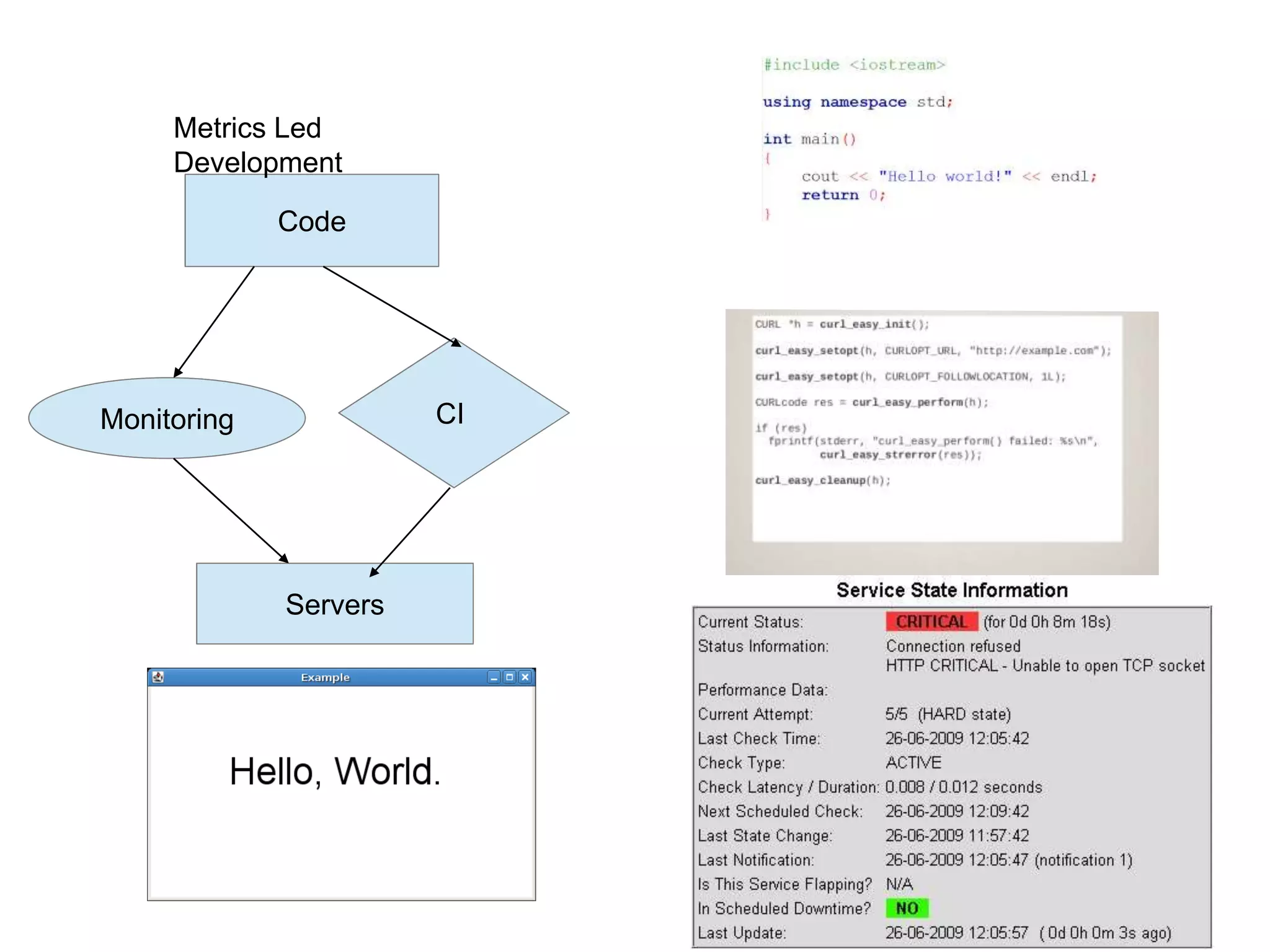
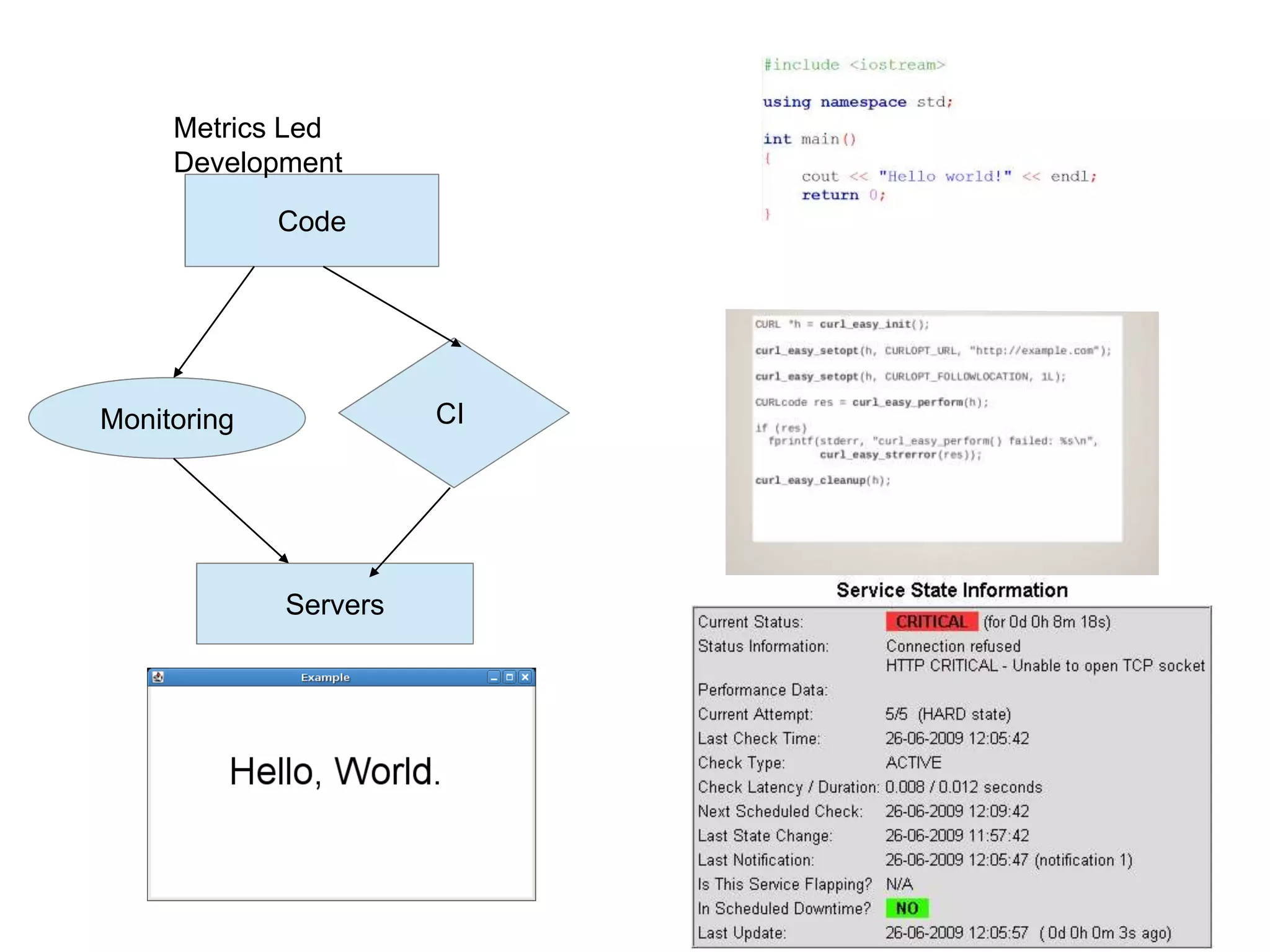
This document summarizes a presentation on monitoring best practices. It recommends starting monitoring early in the development process during testing and staging rather than waiting until production. Monitoring should be integrated into continuous integration to gather metrics and detect issues early. The development team should be involved in setting up monitoring to ensure the right metrics are collected. The goal is to get a comprehensive view of system behavior and performance from an early stage using monitoring.