New Cyber Security Technology
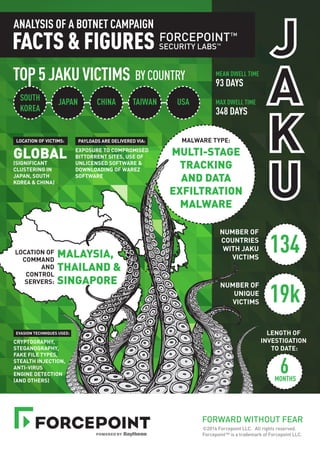
- 1. MALAYSIA, THAILAND & SINGAPORE LOCATION OF COMMAND AND CONTROL SERVERS: MALWARE TYPE: MULTI-STAGE TRACKING AND DATA EXFILTRATION MALWARE FORWARD WITHOUT FEAR ©2016 Forcepoint LLC. All rights reserved. Forcepoint™ is a trademark of Forcepoint LLC. 134 NUMBER OF COUNTRIES WITH JAKU VICTIMS 19k NUMBER OF UNIQUE VICTIMS 6MONTHS LENGTH OF INVESTIGATION TO DATE: J A K U CRYPTOGRAPHY, STEGANOGRAPHY, FAKE FILE TYPES, STEALTH INJECTION, ANTI-VIRUS ENGINE DETECTION (AND OTHERS) EVASION TECHNIQUES USED: EXPOSURE TO COMPROMISED BITTORRENT SITES, USE OF UNLICENSED SOFTWARE & DOWNLOADING OF WAREZ SOFTWARE PAYLOADS ARE DELIVERED VIA: GLOBAL(SIGNIFICANT CLUSTERING IN JAPAN, SOUTH KOREA & CHINA) LOCATION OF VICTIMS: SOUTH KOREA JAPAN CHINA TAIWAN USA BY COUNTRY ANALYSIS OF A BOTNET CAMPAIGN MEAN DWELL TIME 93 DAYS MAX DWELL TIME 348 DAYS
- 2. FORWARD WITHOUT FEAR ©2016 Forcepoint LLC. All rights reserved. Forcepoint™ is a trademark of Forcepoint LLC. JAKUistargetingspecificvictims ANALYSIS OF A BOTNET CAMPAIGN JAKU is the name of the botnet campaign investigated by the Forcepoint Security Labs Special Investigations Team. What makes JAKU unique is that within the noise of thousands of botnet victims, it targets and tracks a small number of specific individuals. These individuals include members of International Non-Governmental Organisations (NGOs), Engineering Companies, Academics, Scientists and Government Employees. North Korea (DPRK) and Pyongyang are the common theme shared between these individuals. JAKU targets its victims - 19,000 is a conservative estimate of the number of victims at any one time - primarily via 'poisoned' BitTorrent file shares. The victims are spread all over the globe, but a significant number of victims are in South Korea and Japan. Forcepoint Security Labs has determined that the botnet command and control (C2) servers identified are also located in the APAC region, including Singapore, Malaysia and Thailand. Asophisticatedbotnetcampaign JAKU uses three different C2 mechanisms, making it highly resilient. Compressed and encrypted code embedded in image files are used to deliver the second stage malware, while the botnet controllers monitor the botnet members via obfuscated SQLite databases. The controllers also cleverly re-use widely available open source software, including the UDT network transport protocol, software copied from Korean blogger sites and re-writes of previously published code. WhoisbehindtheJAKUbotnetcampaign? Forcepoint Security Labs focus on awareness and understanding of intent. This is useful to identify likely future behaviour. We do not focus on specific attribution. However, there are indicators that suggest that the author(s) of the malware identified are native Korean speakers. Foradeeperdiveintothe JAKUbotnetcampaign, downloadthereport www.forcepoint.com/jaku
