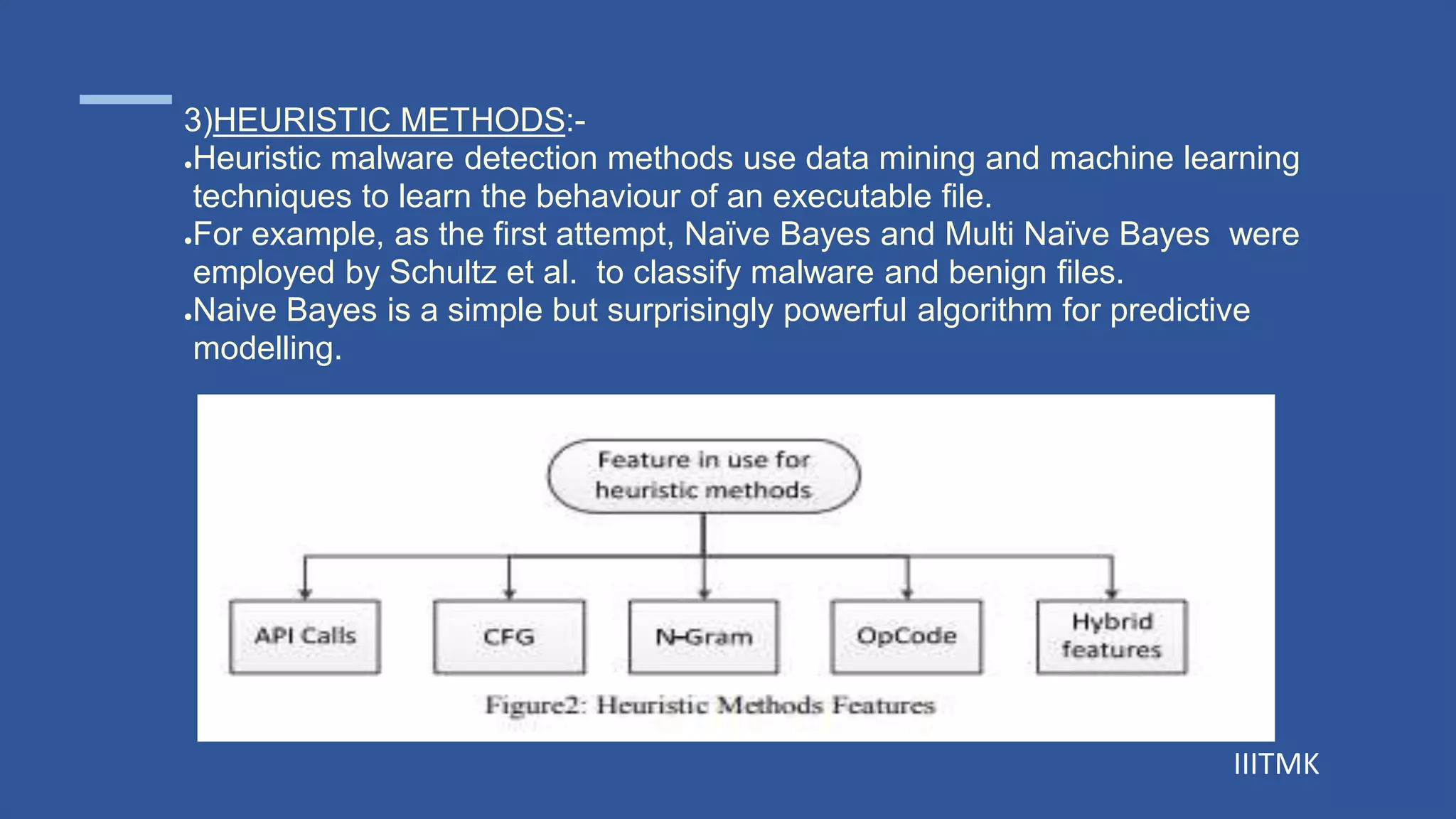
This document discusses obfuscation and mutations in malware. It begins by defining obfuscation as deliberately creating code that is difficult for humans to understand. It then describes various obfuscation techniques used in malware including dead code insertion, register reassignment, and subroutine reordering. The document also discusses different types of malware like viruses, worms, and trojans. It classifies malware into first and second generation and describes techniques used in second generation malware like encryption, oligomorphism, polymorphism, and metamorphism. The document concludes by explaining various malware detection methods such as signature-based, behavior-based, heuristic, and hybrid approaches.