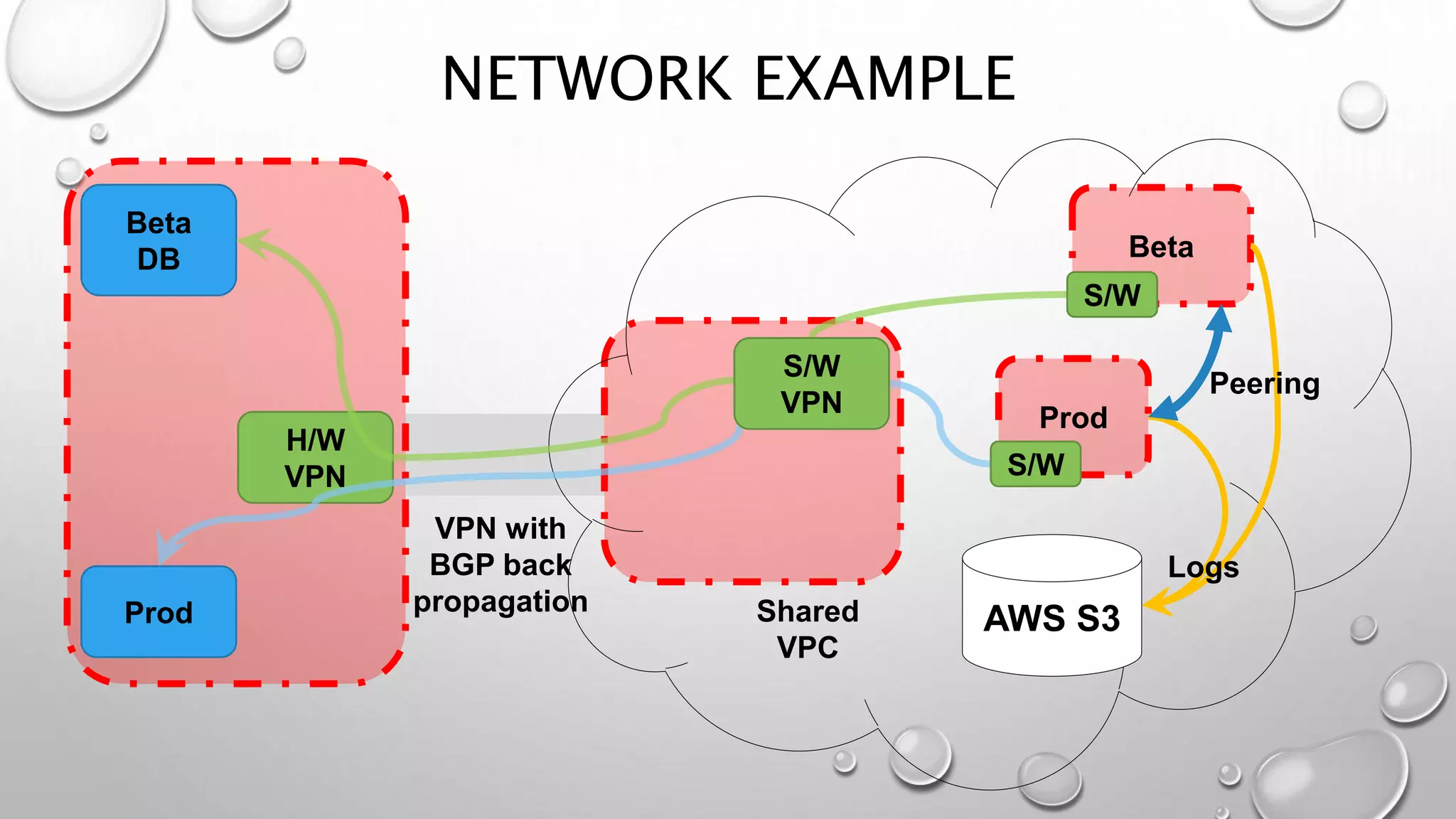
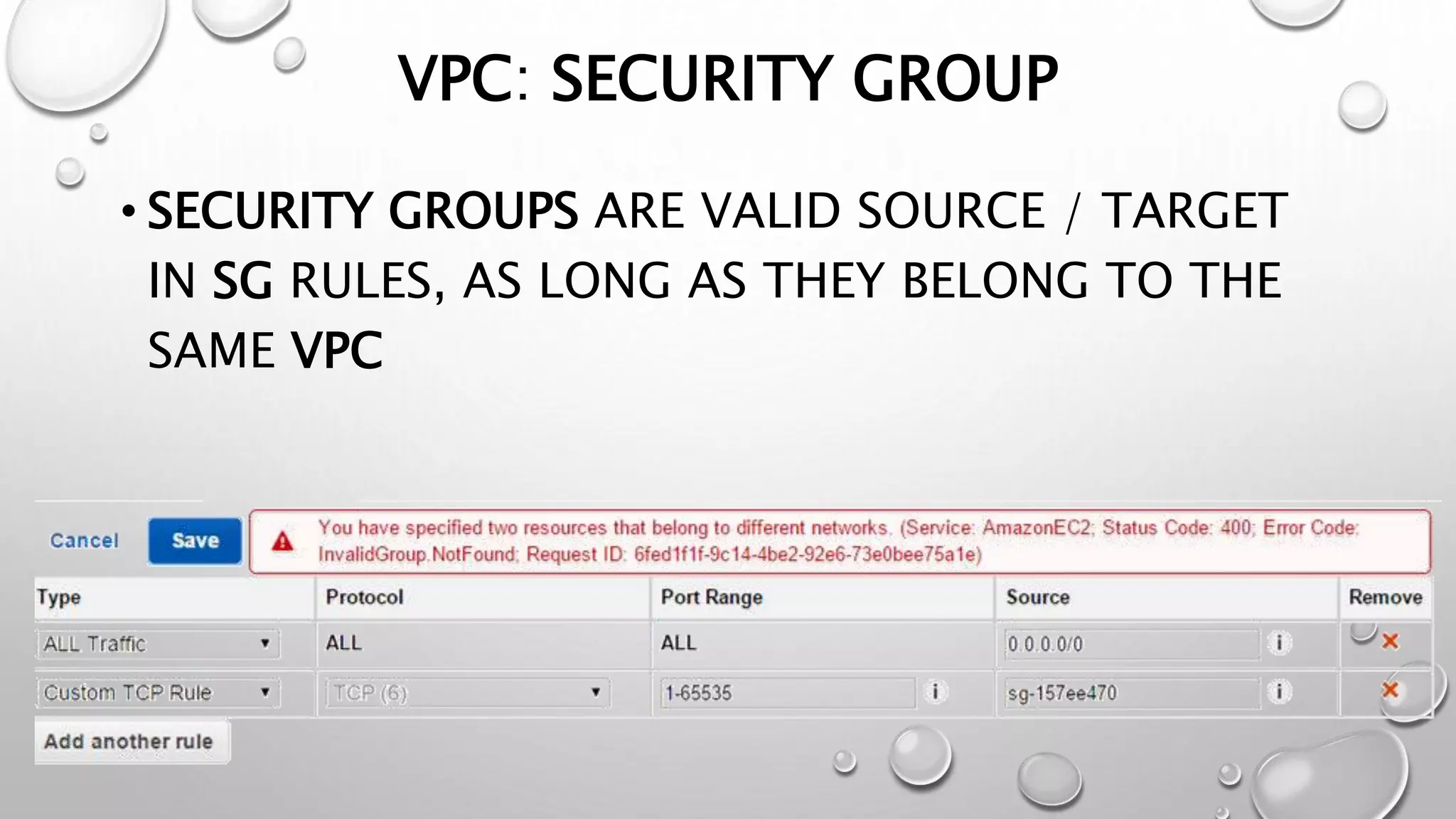
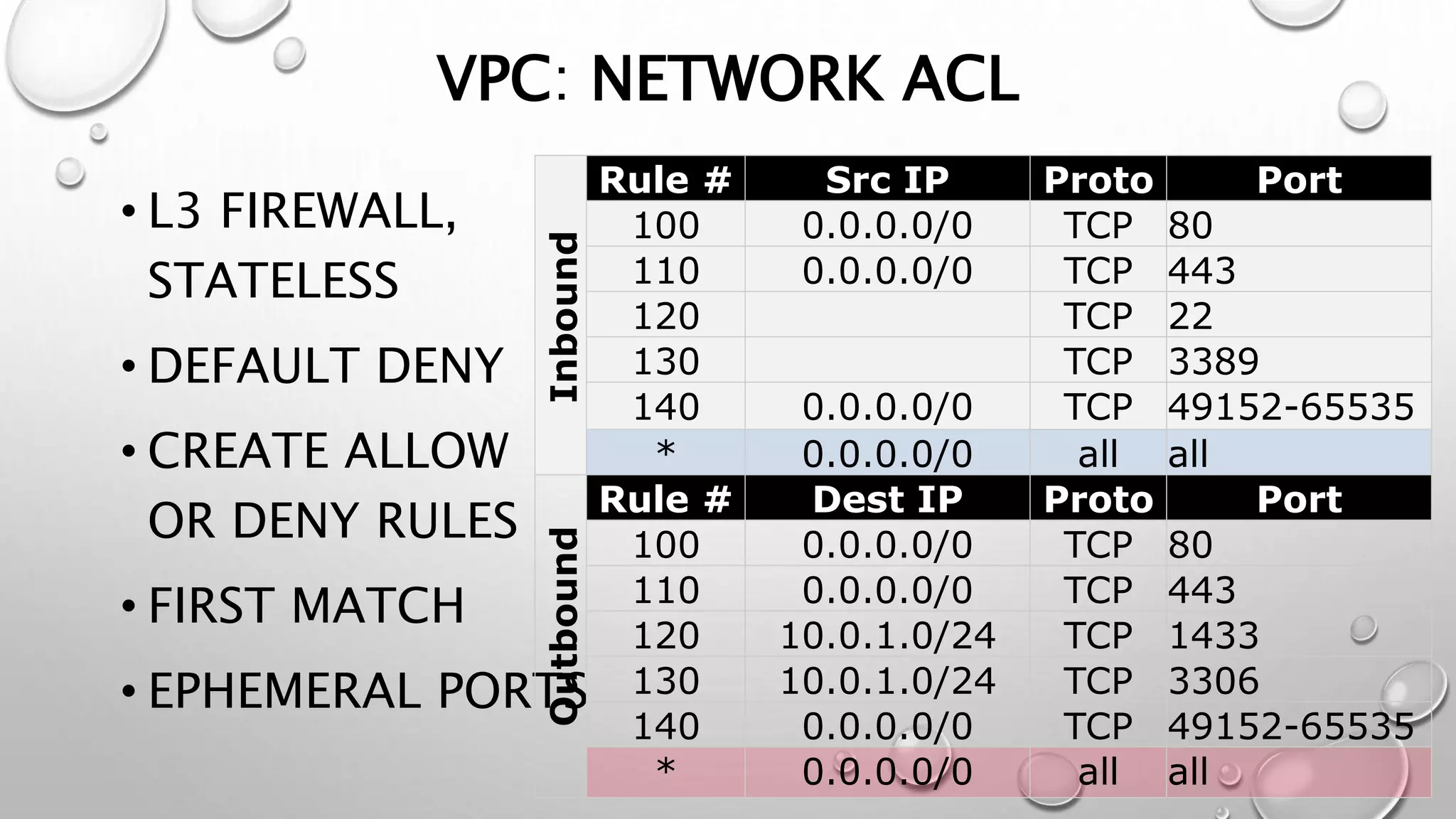
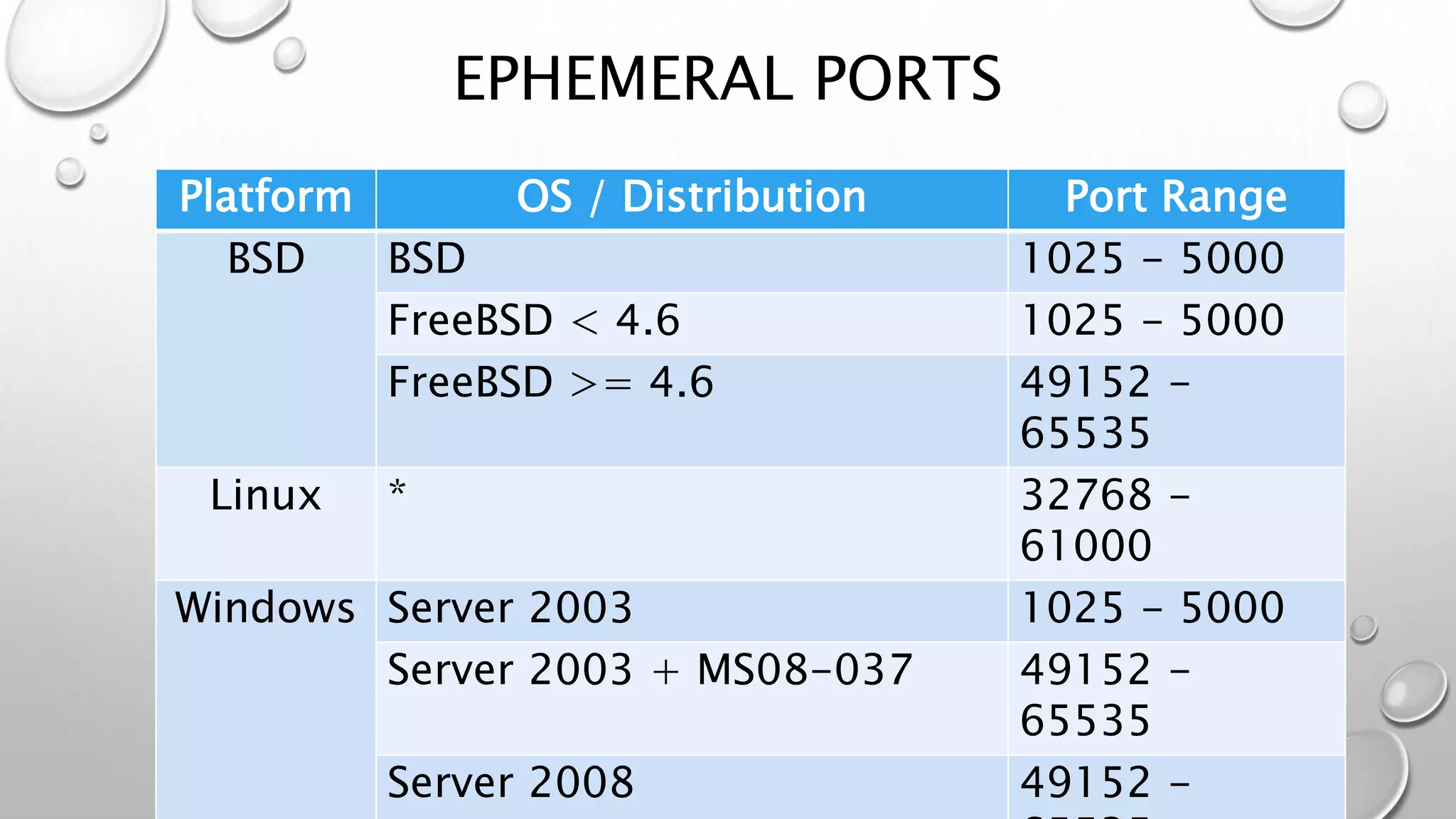
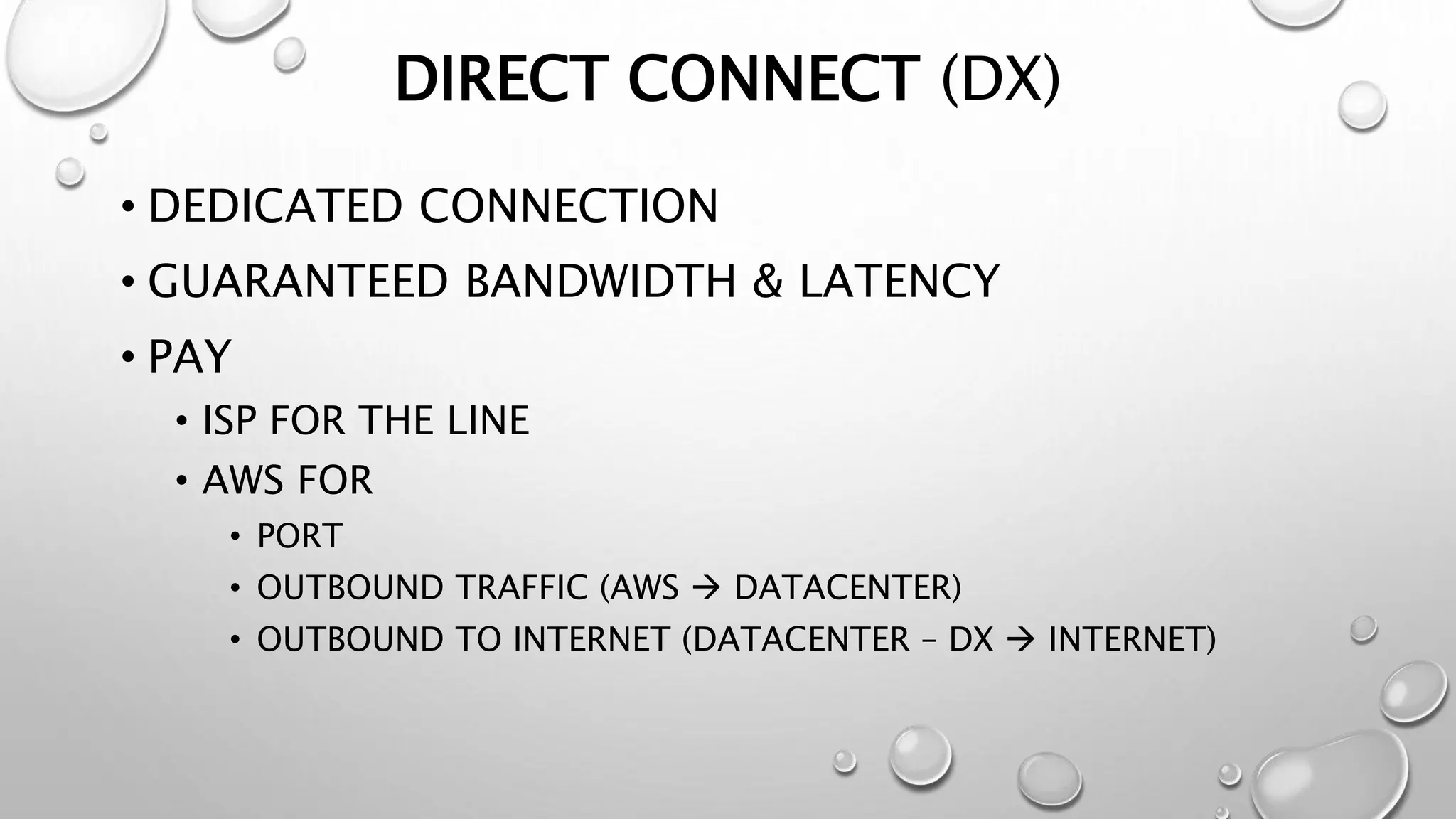
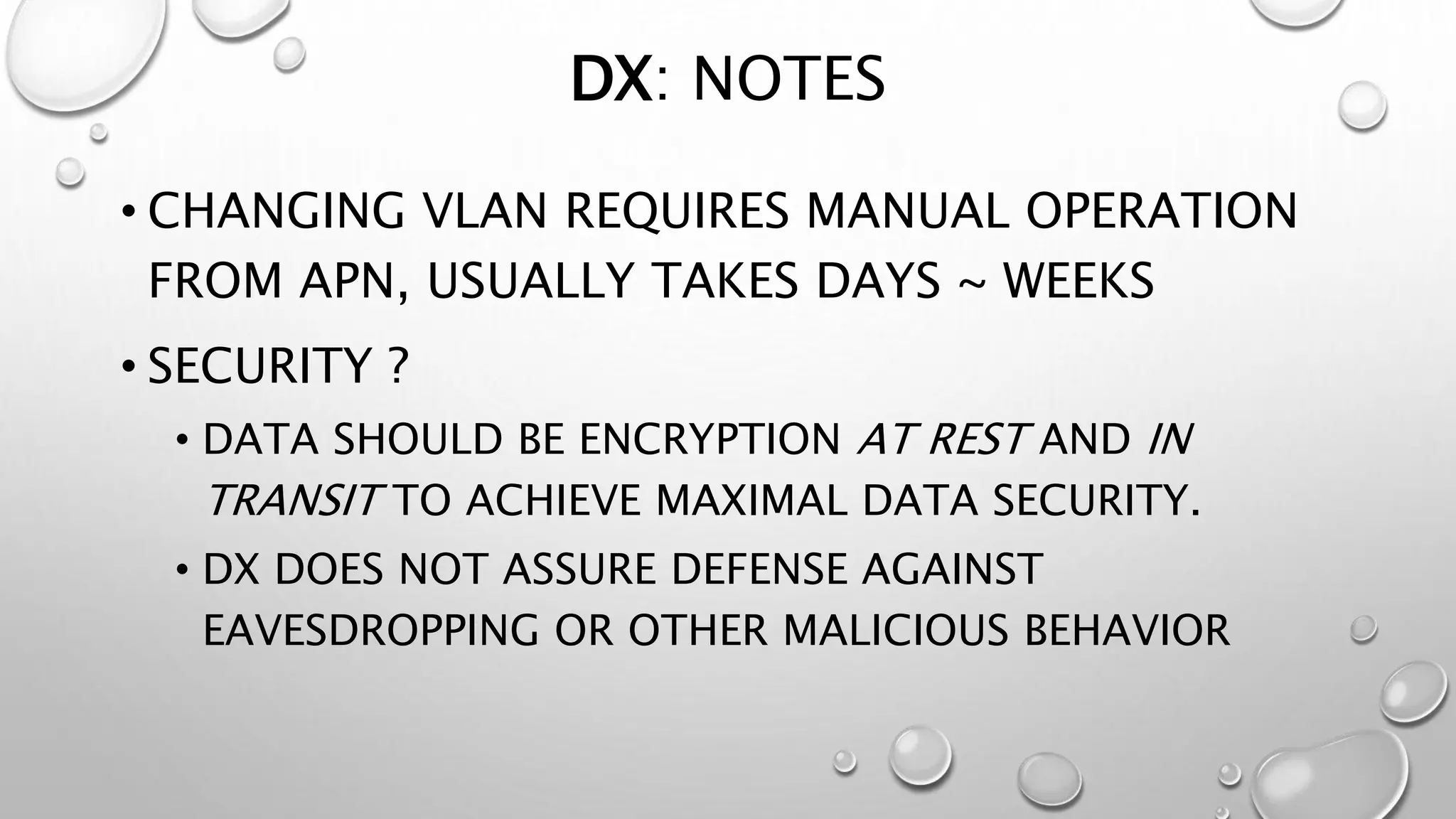
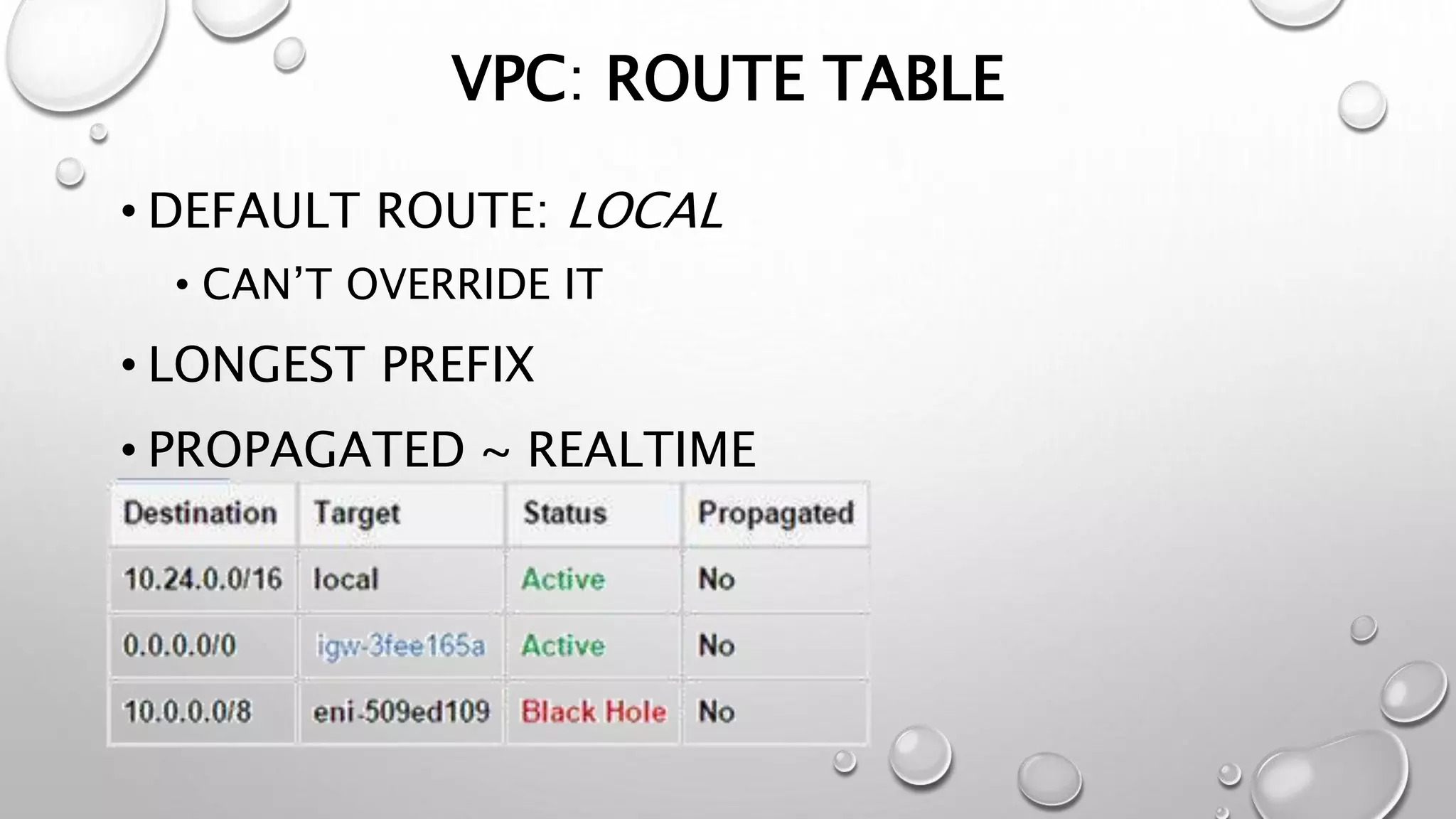
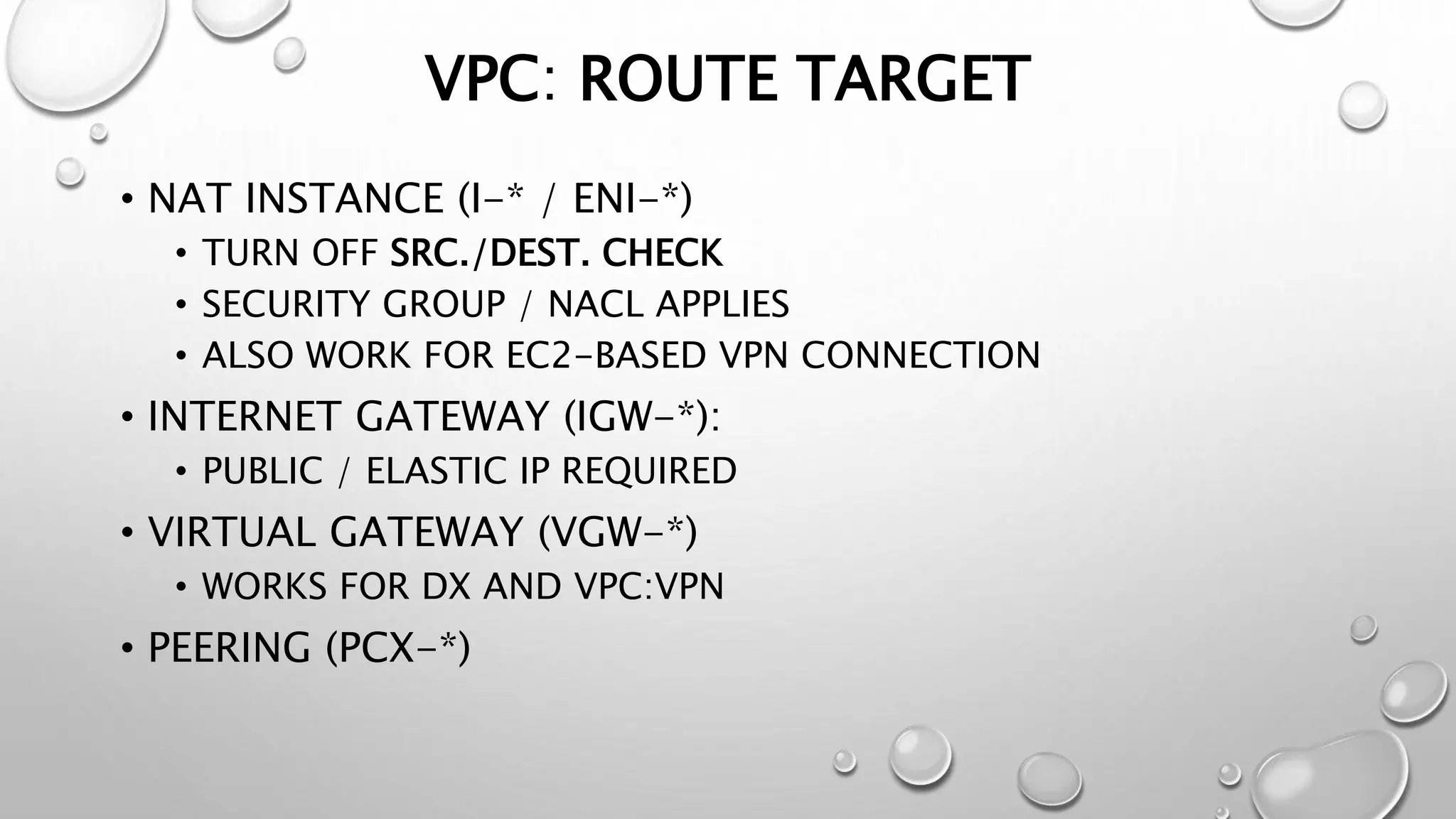
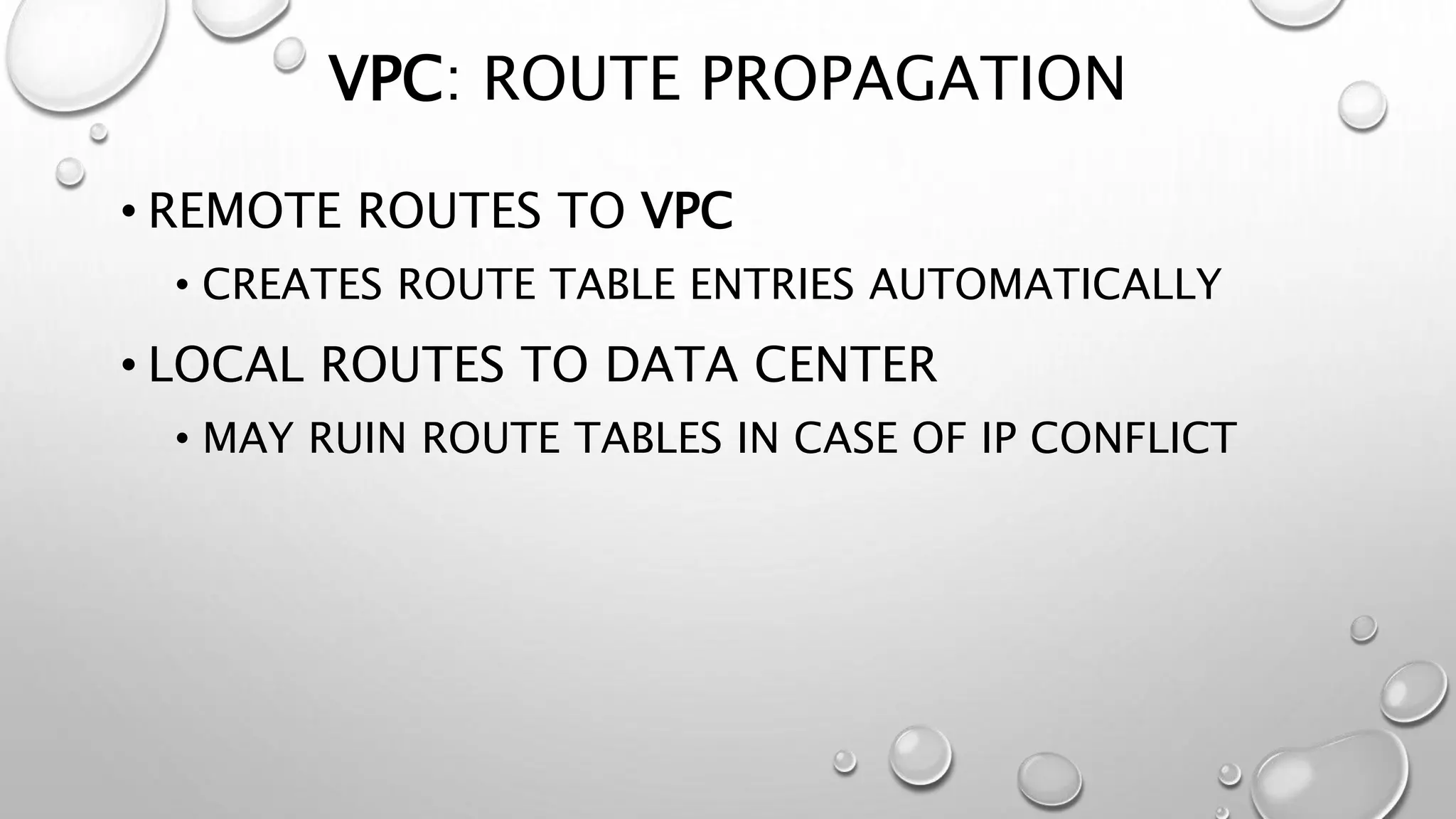
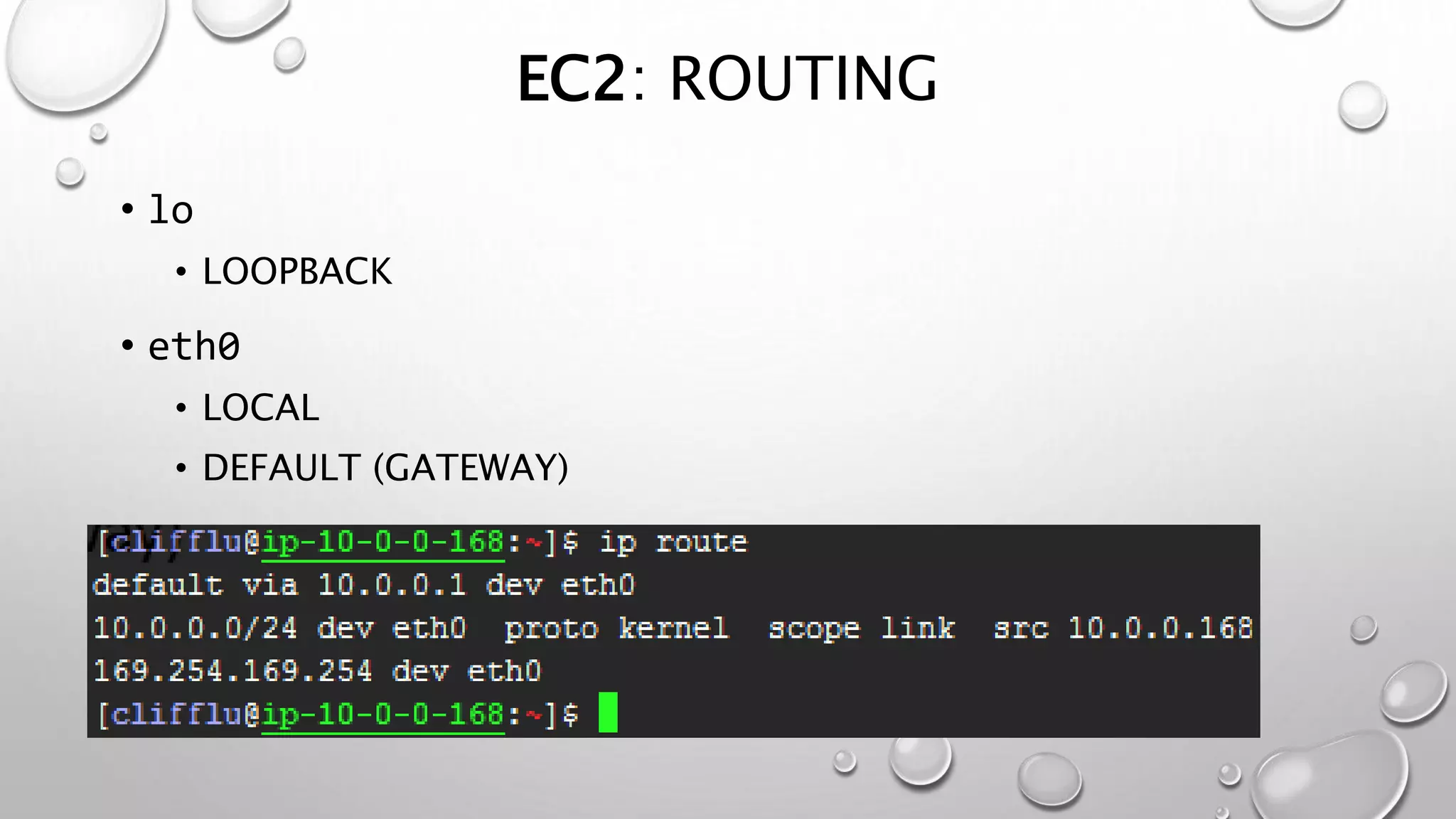
This document discusses networking in the AWS cloud. It covers VPC components like security groups, network ACLs, route tables and how they control traffic and routing. It also discusses connectivity options between on-premises networks and VPCs like Direct Connect, VPN connections and VPC peering. The document provides examples of routing and networking tricks that can be used with EC2 instances and VPC configurations.










![EC2: NETWORK TRICKS
• MULTIPLE ENI
• AS LONG AS THEY BELONG TO THE SAME AZ
• SG APPLIES TO ENI, NOT EC2
• SECONDARY PRIVATE IP
• CONFIGURE OVER MANAGEMENT CONSOLE / API
• ENABLE IN EC2
• ifconfig eth0:0 [SECONDARY_IP] netmask [NETMASK]](https://image.slidesharecdn.com/networkinginthecloud-141127001619-conversion-gate02/75/Networking-in-the-cloud-20-2048.jpg)