The document provides information about Module 5 of a Networking Essentials course, including:
- The module is divided into an instructor planning guide and class presentation slides.
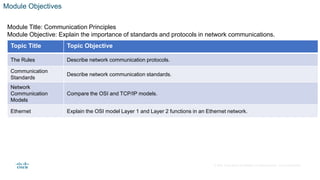
- The planning guide outlines topics, objectives, activities, best practices, and a quiz for the module.
- The class presentation covers communication principles like protocols, standards, networking models, and Ethernet. It includes slides, videos, and labs to facilitate student learning.
- Instructors are provided guidance on preparing for and teaching the topics to optimize learning.