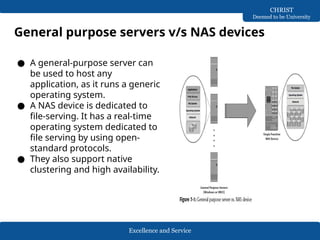
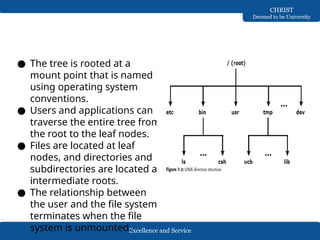
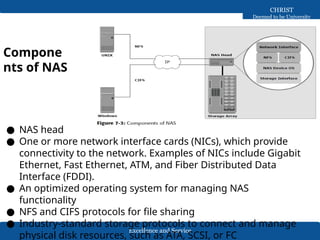
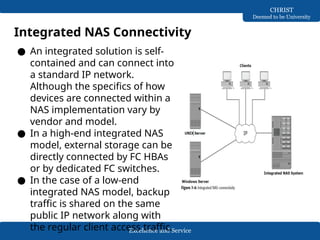
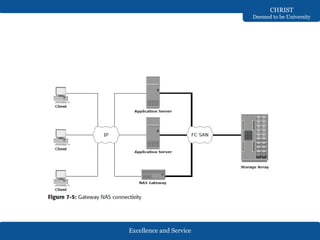
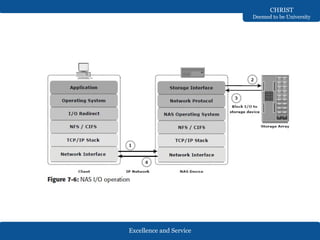
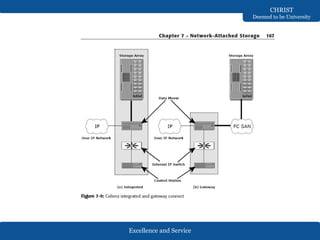
The document discusses Network-Attached Storage (NAS), highlighting its role in providing a high-performance, dedicated file-serving system that consolidates storage and enhances efficiency in data sharing. It outlines the components and implementations of NAS, such as integrated and gateway solutions, and details the protocols (e.g., NFS and CIFS) used for file sharing and management. It also addresses factors affecting NAS performance, including network configurations and optimizations to improve latency and throughput.