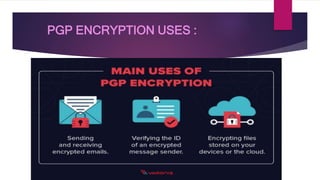
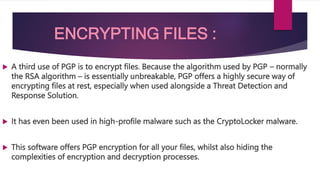
PGP (Pretty Good Privacy) is a widely used email encryption standard that uses both symmetric and public-key encryption. It works by first generating a random session key, encrypting the session key with the recipient's public key, and then using the session key to encrypt the actual message. This allows two parties who have never met to securely communicate via encrypted email without having to exchange private keys. PGP can also be used to digitally sign messages to verify a sender's identity and detect any tampering, as well as to encrypt files for storage.