Network Administrator.docx
•Download as DOCX, PDF•
0 likes•5 views
The job posting is for a Network Administrator who will report to the Project Manager. The ideal candidate will have a Bachelor's degree in Engineering and 2-6 years of total experience including 2 years of network administration experience. Responsibilities include strong knowledge of routing, switching, firewalls and other network technologies, implementing network projects, and analyzing and solving network problems. Certifications such as CCNA, CCNP, or CISSP are preferred.
Report
Share
Report
Share
Recommended
Recommended
Network Engineer

Our latest opportunity to work with Cisco technologies in an enterprise environment!
Why You Should Replace Windows 11 with Nitrux Linux 3.5.0 for enhanced perfor...

The choice of an operating system plays a pivotal role in shaping our computing experience. For decades, Microsoft's Windows has dominated the market, offering a familiar and widely adopted platform for personal and professional use. However, as technological advancements continue to push the boundaries of innovation, alternative operating systems have emerged, challenging the status quo and offering users a fresh perspective on computing.
One such alternative that has garnered significant attention and acclaim is Nitrux Linux 3.5.0, a sleek, powerful, and user-friendly Linux distribution that promises to redefine the way we interact with our devices. With its focus on performance, security, and customization, Nitrux Linux presents a compelling case for those seeking to break free from the constraints of proprietary software and embrace the freedom and flexibility of open-source computing.
FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf

FIDO Alliance Osaka Seminar
More Related Content
Similar to Network Administrator.docx
Network Engineer

Our latest opportunity to work with Cisco technologies in an enterprise environment!
Similar to Network Administrator.docx (20)
Recently uploaded
Why You Should Replace Windows 11 with Nitrux Linux 3.5.0 for enhanced perfor...

The choice of an operating system plays a pivotal role in shaping our computing experience. For decades, Microsoft's Windows has dominated the market, offering a familiar and widely adopted platform for personal and professional use. However, as technological advancements continue to push the boundaries of innovation, alternative operating systems have emerged, challenging the status quo and offering users a fresh perspective on computing.
One such alternative that has garnered significant attention and acclaim is Nitrux Linux 3.5.0, a sleek, powerful, and user-friendly Linux distribution that promises to redefine the way we interact with our devices. With its focus on performance, security, and customization, Nitrux Linux presents a compelling case for those seeking to break free from the constraints of proprietary software and embrace the freedom and flexibility of open-source computing.
FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf

FIDO Alliance Osaka Seminar
Communications Mining Series - Zero to Hero - Session 1

This session provides introduction to UiPath Communication Mining, importance and platform overview. You will acquire a good understand of the phases in Communication Mining as we go over the platform with you. Topics covered:
• Communication Mining Overview
• Why is it important?
• How can it help today’s business and the benefits
• Phases in Communication Mining
• Demo on Platform overview
• Q/A
GraphSummit Singapore | The Art of the Possible with Graph - Q2 2024

Neha Bajwa, Vice President of Product Marketing, Neo4j
Join us as we explore breakthrough innovations enabled by interconnected data and AI. Discover firsthand how organizations use relationships in data to uncover contextual insights and solve our most pressing challenges – from optimizing supply chains, detecting fraud, and improving customer experiences to accelerating drug discoveries.
Alt. GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using ...

Effective Application Security in Software Delivery lifecycle using Deployment Firewall and DBOM
The modern software delivery process (or the CI/CD process) includes many tools, distributed teams, open-source code, and cloud platforms. Constant focus on speed to release software to market, along with the traditional slow and manual security checks has caused gaps in continuous security as an important piece in the software supply chain. Today organizations feel more susceptible to external and internal cyber threats due to the vast attack surface in their applications supply chain and the lack of end-to-end governance and risk management.
The software team must secure its software delivery process to avoid vulnerability and security breaches. This needs to be achieved with existing tool chains and without extensive rework of the delivery processes. This talk will present strategies and techniques for providing visibility into the true risk of the existing vulnerabilities, preventing the introduction of security issues in the software, resolving vulnerabilities in production environments quickly, and capturing the deployment bill of materials (DBOM).
Speakers:
Bob Boule
Robert Boule is a technology enthusiast with PASSION for technology and making things work along with a knack for helping others understand how things work. He comes with around 20 years of solution engineering experience in application security, software continuous delivery, and SaaS platforms. He is known for his dynamic presentations in CI/CD and application security integrated in software delivery lifecycle.
Gopinath Rebala
Gopinath Rebala is the CTO of OpsMx, where he has overall responsibility for the machine learning and data processing architectures for Secure Software Delivery. Gopi also has a strong connection with our customers, leading design and architecture for strategic implementations. Gopi is a frequent speaker and well-known leader in continuous delivery and integrating security into software delivery.
SAP Sapphire 2024 - ASUG301 building better apps with SAP Fiori.pdf

Building better applications for business users with SAP Fiori.
• What is SAP Fiori and why it matters to you
• How a better user experience drives measurable business benefits
• How to get started with SAP Fiori today
• How SAP Fiori elements accelerates application development
• How SAP Build Code includes SAP Fiori tools and other generative artificial intelligence capabilities
• How SAP Fiori paves the way for using AI in SAP apps
Microsoft - Power Platform_G.Aspiotis.pdf

Revolutionizing Application Development
with AI-powered low-code, presentation by George Aspiotis, Sr. Partner Development Manager, Microsoft
Encryption in Microsoft 365 - ExpertsLive Netherlands 2024

In this session I delve into the encryption technology used in Microsoft 365 and Microsoft Purview. Including the concepts of Customer Key and Double Key Encryption.
DevOps and Testing slides at DASA Connect

My and Rik Marselis slides at 30.5.2024 DASA Connect conference. We discuss about what is testing, then what is agile testing and finally what is Testing in DevOps. Finally we had lovely workshop with the participants trying to find out different ways to think about quality and testing in different parts of the DevOps infinity loop.
Epistemic Interaction - tuning interfaces to provide information for AI support

Paper presented at SYNERGY workshop at AVI 2024, Genoa, Italy. 3rd June 2024
https://alandix.com/academic/papers/synergy2024-epistemic/
As machine learning integrates deeper into human-computer interactions, the concept of epistemic interaction emerges, aiming to refine these interactions to enhance system adaptability. This approach encourages minor, intentional adjustments in user behaviour to enrich the data available for system learning. This paper introduces epistemic interaction within the context of human-system communication, illustrating how deliberate interaction design can improve system understanding and adaptation. Through concrete examples, we demonstrate the potential of epistemic interaction to significantly advance human-computer interaction by leveraging intuitive human communication strategies to inform system design and functionality, offering a novel pathway for enriching user-system engagements.
UiPath Test Automation using UiPath Test Suite series, part 5

Welcome to UiPath Test Automation using UiPath Test Suite series part 5. In this session, we will cover CI/CD with devops.
Topics covered:
CI/CD with in UiPath
End-to-end overview of CI/CD pipeline with Azure devops
Speaker:
Lyndsey Byblow, Test Suite Sales Engineer @ UiPath, Inc.
LF Energy Webinar: Electrical Grid Modelling and Simulation Through PowSyBl -...

Do you want to learn how to model and simulate an electrical network from scratch in under an hour?
Then welcome to this PowSyBl workshop, hosted by Rte, the French Transmission System Operator (TSO)!
During the webinar, you will discover the PowSyBl ecosystem as well as handle and study an electrical network through an interactive Python notebook.
PowSyBl is an open source project hosted by LF Energy, which offers a comprehensive set of features for electrical grid modelling and simulation. Among other advanced features, PowSyBl provides:
- A fully editable and extendable library for grid component modelling;
- Visualization tools to display your network;
- Grid simulation tools, such as power flows, security analyses (with or without remedial actions) and sensitivity analyses;
The framework is mostly written in Java, with a Python binding so that Python developers can access PowSyBl functionalities as well.
What you will learn during the webinar:
- For beginners: discover PowSyBl's functionalities through a quick general presentation and the notebook, without needing any expert coding skills;
- For advanced developers: master the skills to efficiently apply PowSyBl functionalities to your real-world scenarios.
Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf

Monitoring and observability aren’t traditionally found in software curriculums and many of us cobble this knowledge together from whatever vendor or ecosystem we were first introduced to and whatever is a part of your current company’s observability stack.
While the dev and ops silo continues to crumble….many organizations still relegate monitoring & observability as the purview of ops, infra and SRE teams. This is a mistake - achieving a highly observable system requires collaboration up and down the stack.
I, a former op, would like to extend an invitation to all application developers to join the observability party will share these foundational concepts to build on:
Recently uploaded (20)
Why You Should Replace Windows 11 with Nitrux Linux 3.5.0 for enhanced perfor...

Why You Should Replace Windows 11 with Nitrux Linux 3.5.0 for enhanced perfor...
FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf

FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf
Communications Mining Series - Zero to Hero - Session 1

Communications Mining Series - Zero to Hero - Session 1
GraphSummit Singapore | The Art of the Possible with Graph - Q2 2024

GraphSummit Singapore | The Art of the Possible with Graph - Q2 2024
Alt. GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using ...

Alt. GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using ...
SAP Sapphire 2024 - ASUG301 building better apps with SAP Fiori.pdf

SAP Sapphire 2024 - ASUG301 building better apps with SAP Fiori.pdf
Monitoring Java Application Security with JDK Tools and JFR Events

Monitoring Java Application Security with JDK Tools and JFR Events
Encryption in Microsoft 365 - ExpertsLive Netherlands 2024

Encryption in Microsoft 365 - ExpertsLive Netherlands 2024
Epistemic Interaction - tuning interfaces to provide information for AI support

Epistemic Interaction - tuning interfaces to provide information for AI support
UiPath Test Automation using UiPath Test Suite series, part 5

UiPath Test Automation using UiPath Test Suite series, part 5
FIDO Alliance Osaka Seminar: Passkeys and the Road Ahead.pdf

FIDO Alliance Osaka Seminar: Passkeys and the Road Ahead.pdf
Secstrike : Reverse Engineering & Pwnable tools for CTF.pptx

Secstrike : Reverse Engineering & Pwnable tools for CTF.pptx
LF Energy Webinar: Electrical Grid Modelling and Simulation Through PowSyBl -...

LF Energy Webinar: Electrical Grid Modelling and Simulation Through PowSyBl -...
Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf

Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf
Free Complete Python - A step towards Data Science

Free Complete Python - A step towards Data Science
FIDO Alliance Osaka Seminar: FIDO Security Aspects.pdf

FIDO Alliance Osaka Seminar: FIDO Security Aspects.pdf
Network Administrator.docx
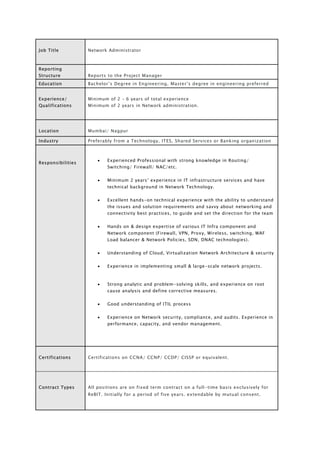
- 1. Job Title Network Administrator Reporting Structure Reports to the Project Manager Education Bachelor’s Degree in Engineering, Master’s degree in engineering preferred Experience/ Qualifications Minimum of 2 – 6 years of total experience Minimum of 2 years in Network administration. Location Mumbai/ Nagpur Industry Preferably from a Technology, ITES, Shared Services or Banking organization Responsibilities Experienced Professional with strong knowledge in Routing/ Switching/ Firewall/ NAC/etc. Minimum 2 years’ experience in IT infrastructure services and have technical background in Network Technology. Excellent hands-on technical experience with the ability to understand the issues and solution requirements and savvy about networking and connectivity best practices, to guide and set the direction for the team Hands on & design expertise of various IT Infra component and Network component (Firewall, VPN, Proxy, Wireless, switching, WAF Load balancer & Network Policies, SDN, DNAC technologies). Understanding of Cloud, Virtualization Network Architecture & security Experience in implementing small & large-scale network projects. Strong analytic and problem-solving skills, and experience on root cause analysis and define corrective measures. Good understanding of ITIL process Experience on Network security, compliance, and audits. Experience in performance, capacity, and vendor management. Certifications Certifications on CCNA/ CCNP/ CCDP/ CISSP or equivalent. Contract Types All positions are on fixed term contract on a full-time basis exclusively for ReBIT. Initially for a period of five years. extendable by mutual consent.