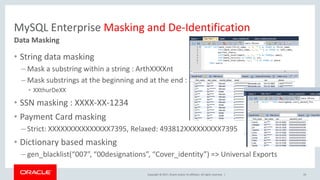
The document provides an overview of data masking, emphasizing its importance for regulatory compliance and protection against data breaches. It outlines various data masking techniques and features available in MySQL Enterprise, including string masking, dictionary-based replacements, and random data generation. Additionally, it discusses the enterprise security architecture and emphasizes the significance of proper data handling and security measures.