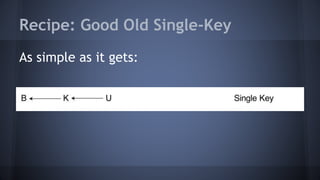
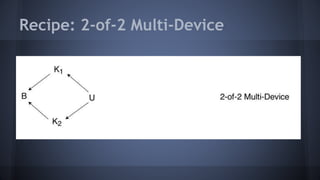
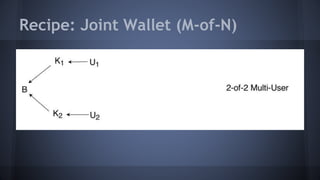
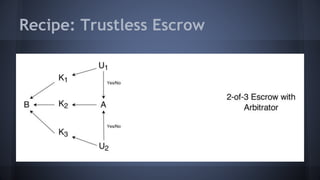
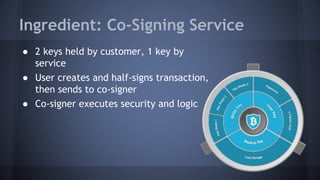
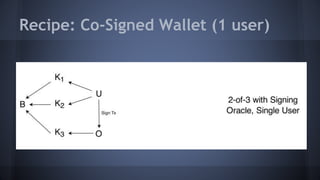
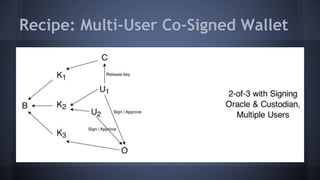
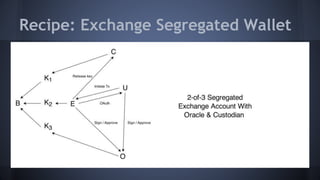
The document outlines the use of multi-signature (multi-sig) technologies to enhance security for Bitcoin transactions, detailing various recipes and real-world applications. It introduces essential components like P2SH and multi-sig wallets, alongside practical examples such as joint wallets, trustless escrow, and co-signed wallets. The goal is to improve security and operational efficiency for users and businesses in the cryptocurrency space.