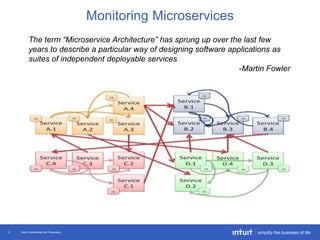
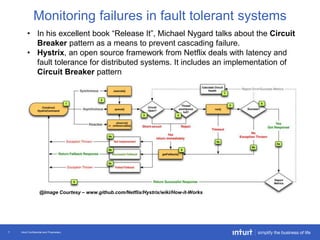
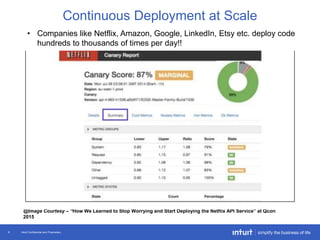
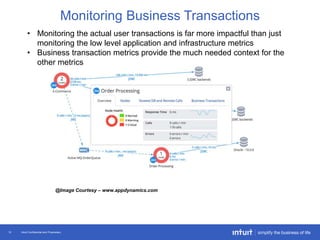
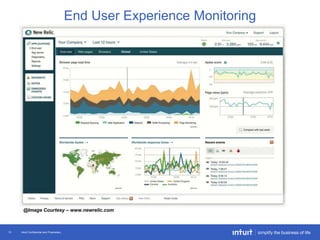
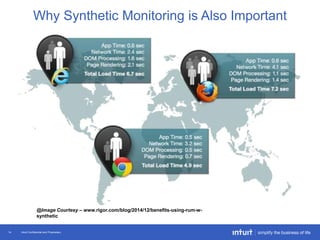
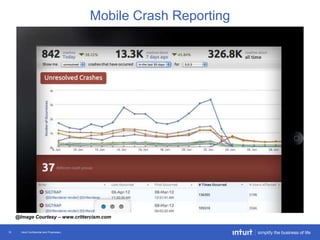
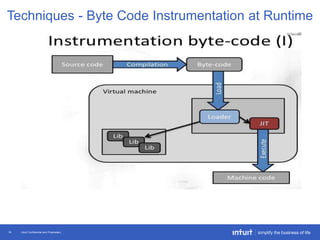
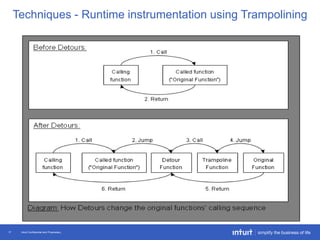
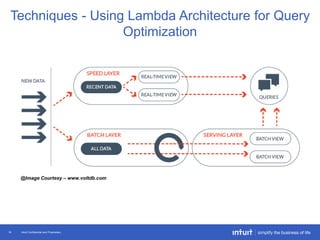
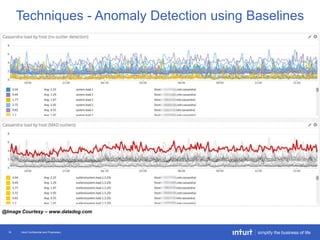
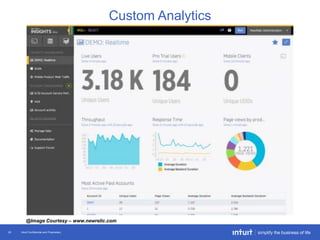
The document discusses the evolution of application monitoring, highlighting the importance of mobile monitoring and the complexities of microservice architectures. It outlines advanced techniques for monitoring, such as circuit breakers and anomaly detection, and emphasizes the significance of monitoring business transactions for understanding user experiences. Key insights include the necessity for continuous deployment and improving monitoring capabilities to prevent system failures.