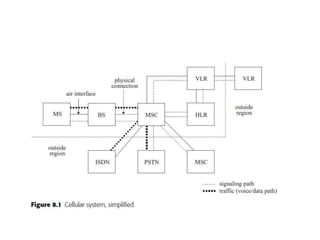
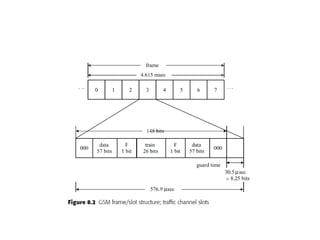
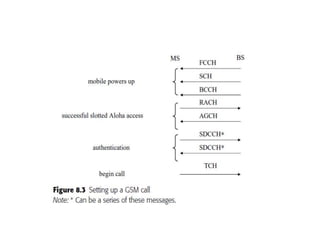
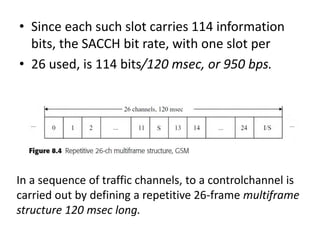
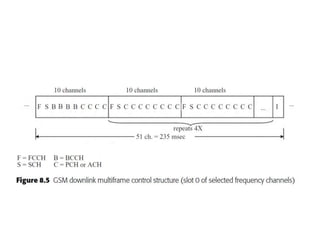
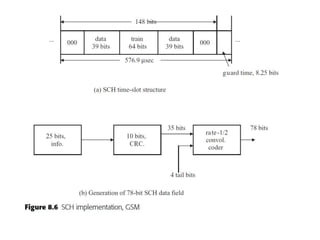
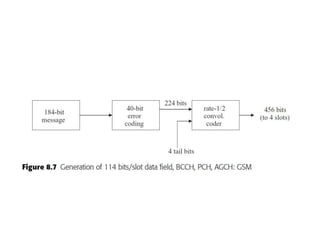
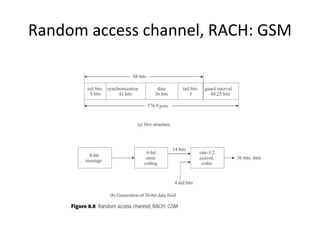
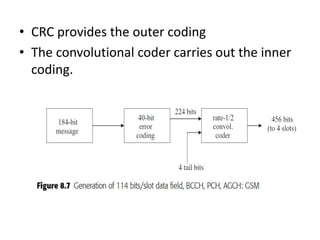
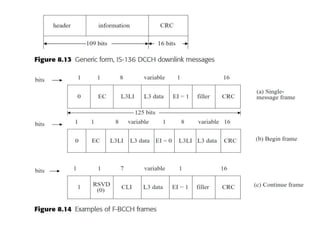
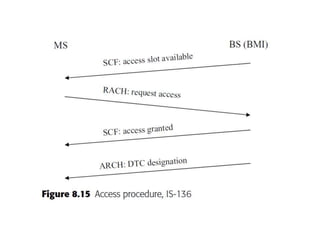
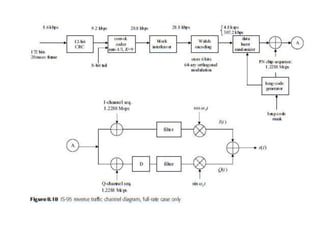
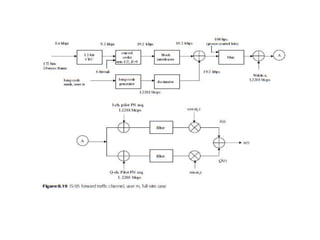
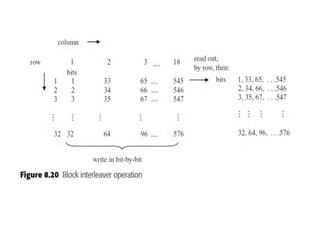
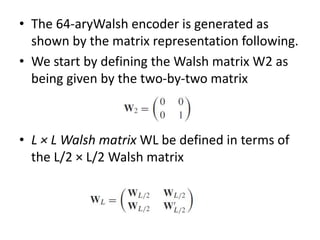
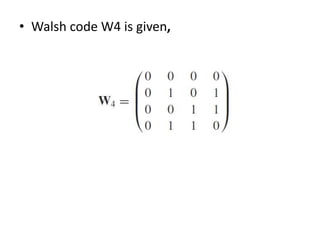
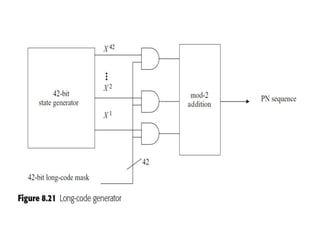
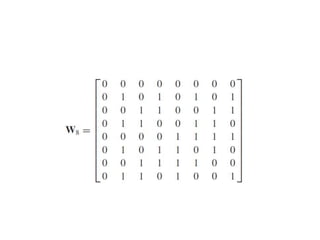
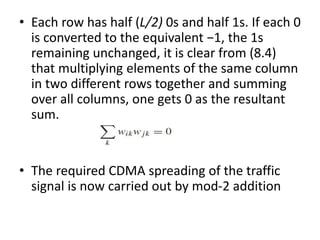
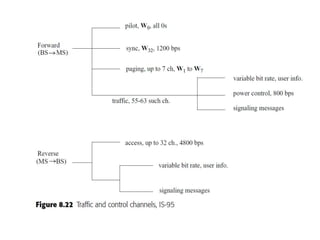
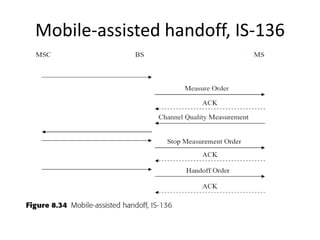
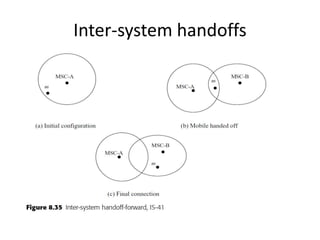
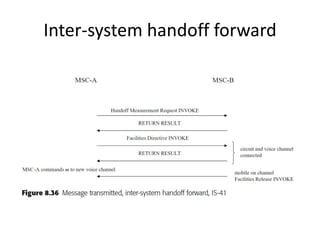
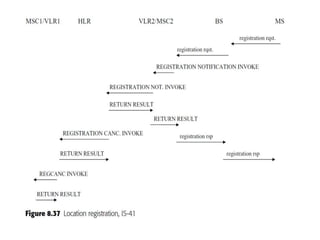
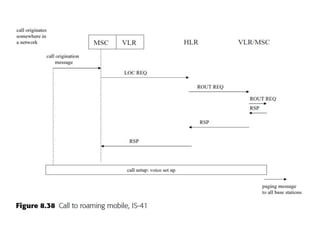
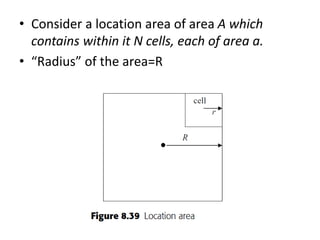
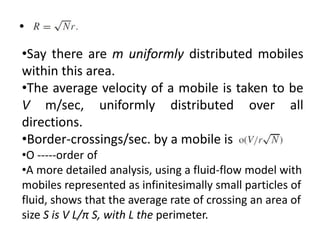
This document summarizes key aspects of second-generation digital wireless systems including TDMA-based IS-136 and GSM as well as CDMA-based IS-95. It describes the basic infrastructure components including base stations, mobile switching centers, home and visitor location registers. It also provides overviews of channel structures and framing in GSM, IS-136 and IS-95 including descriptions of broadcast, traffic and control channels. Mobile registration, authentication and handoff procedures are also summarized.