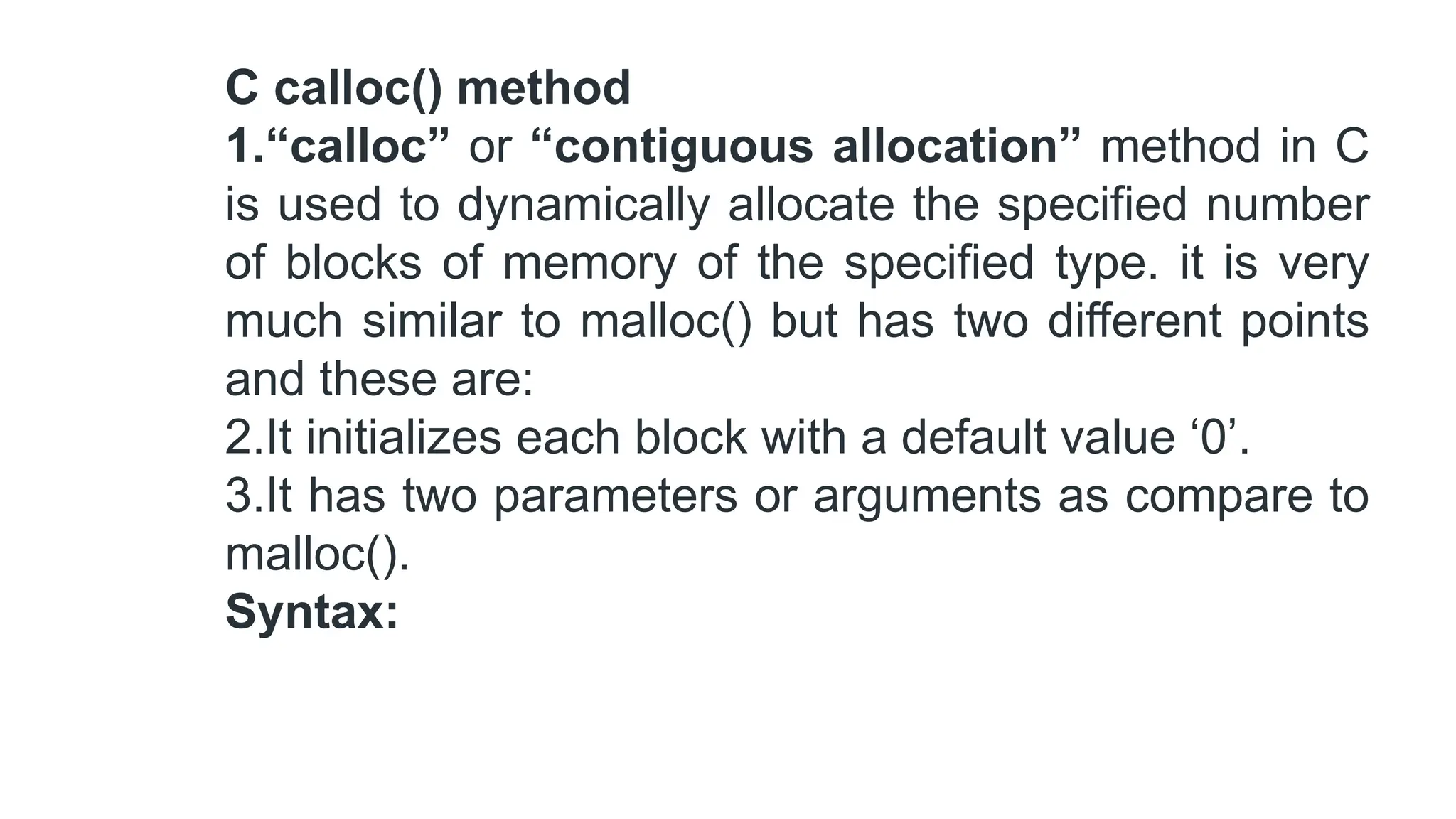
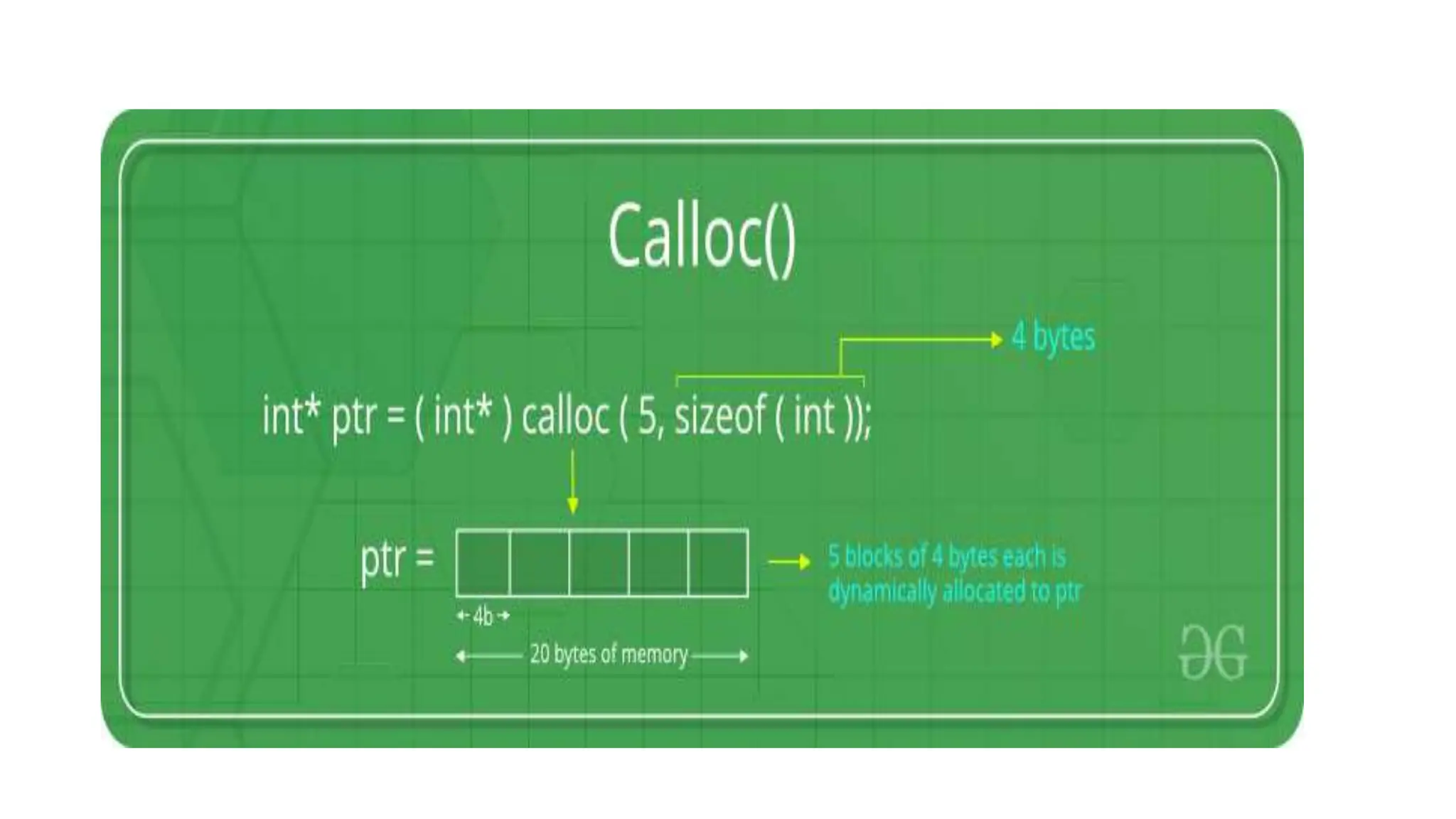
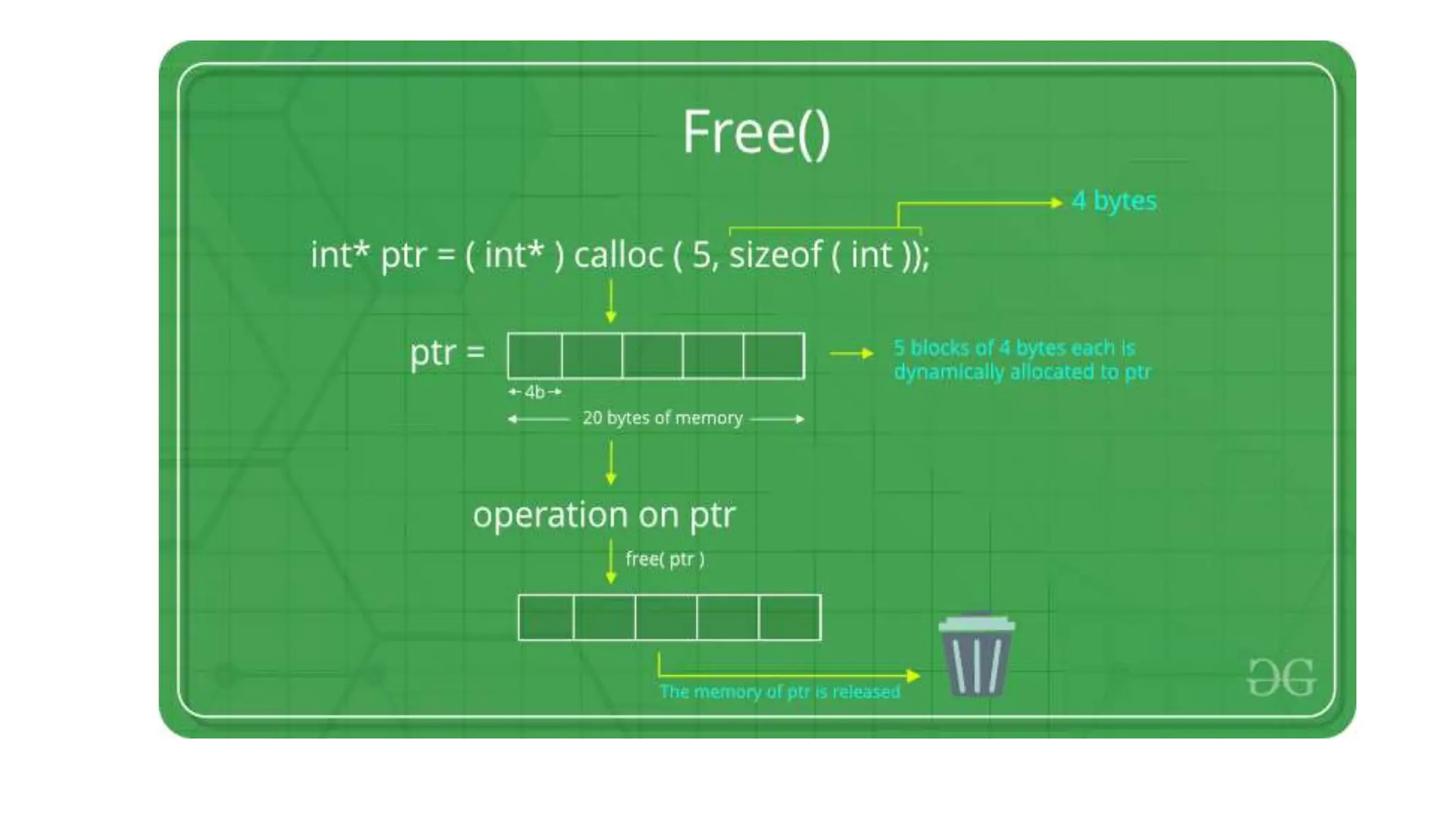
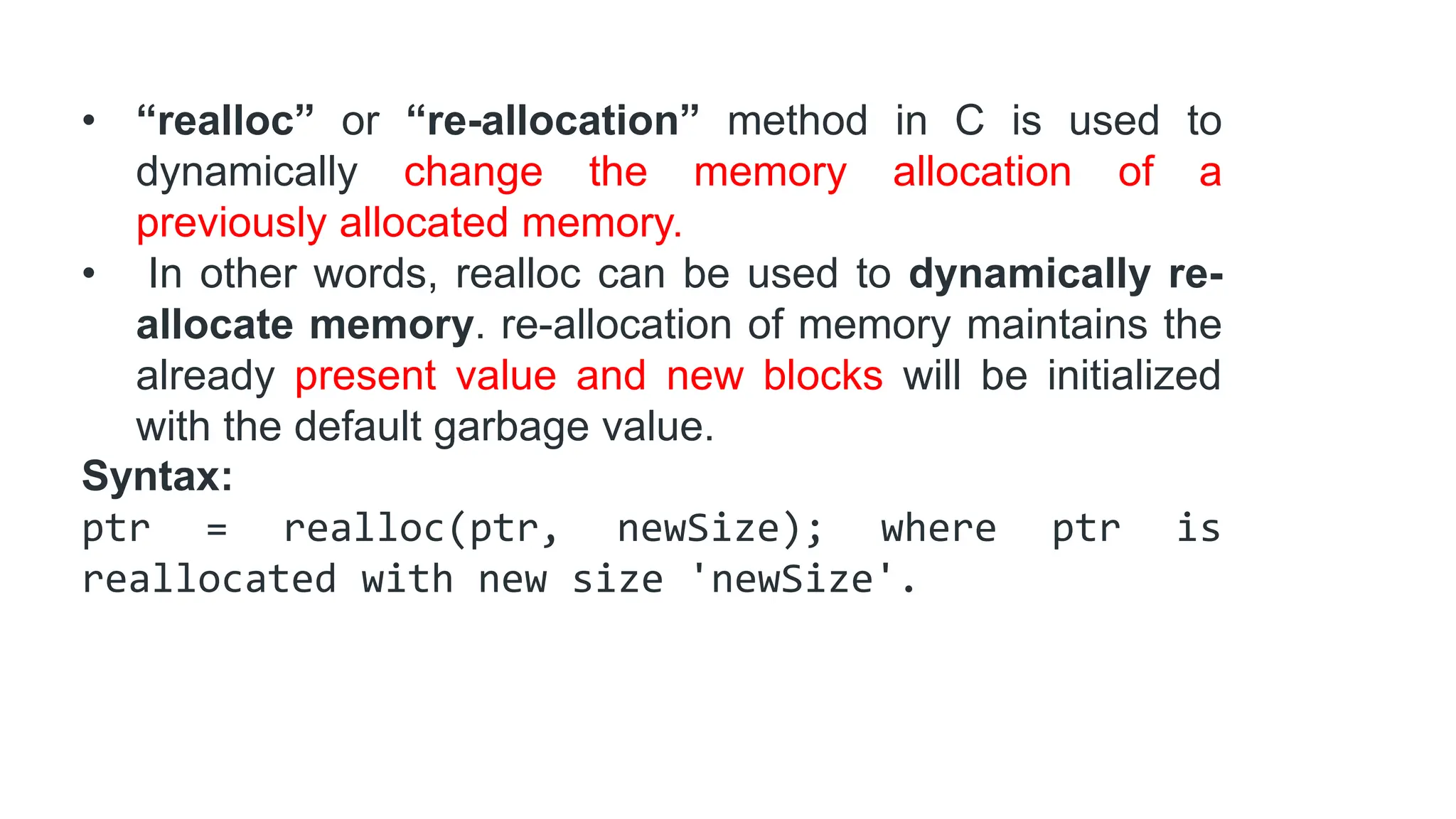
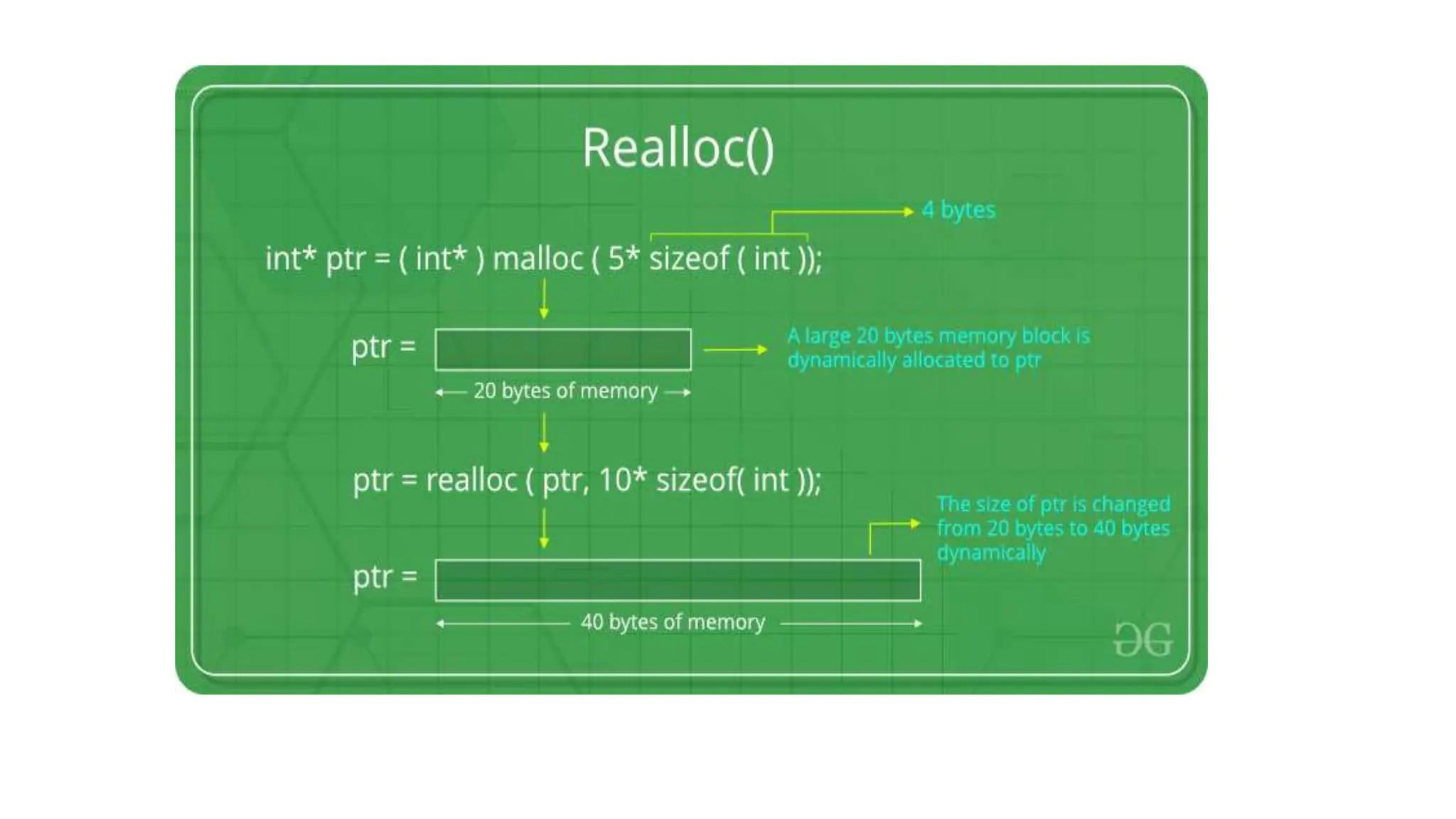
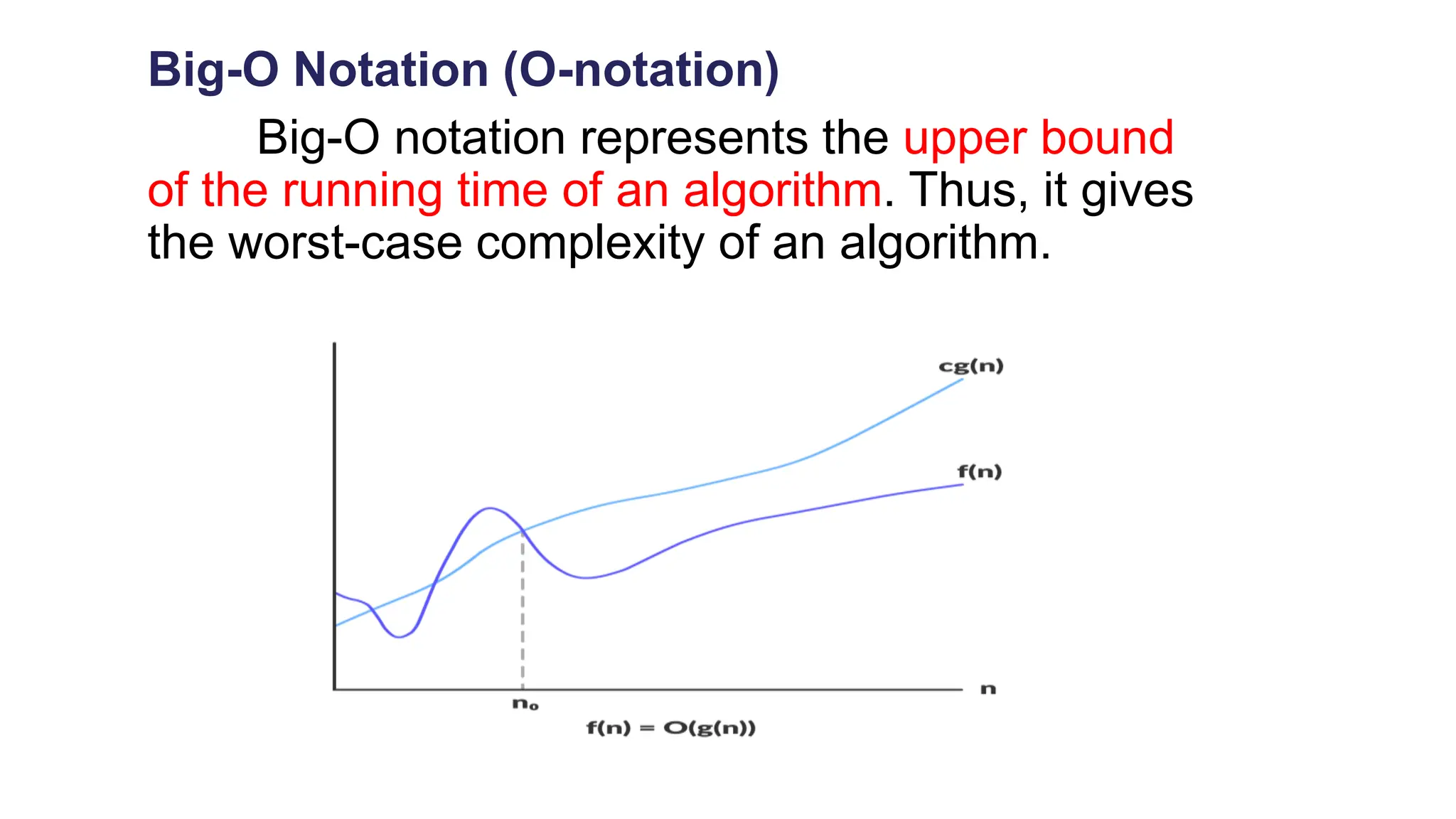
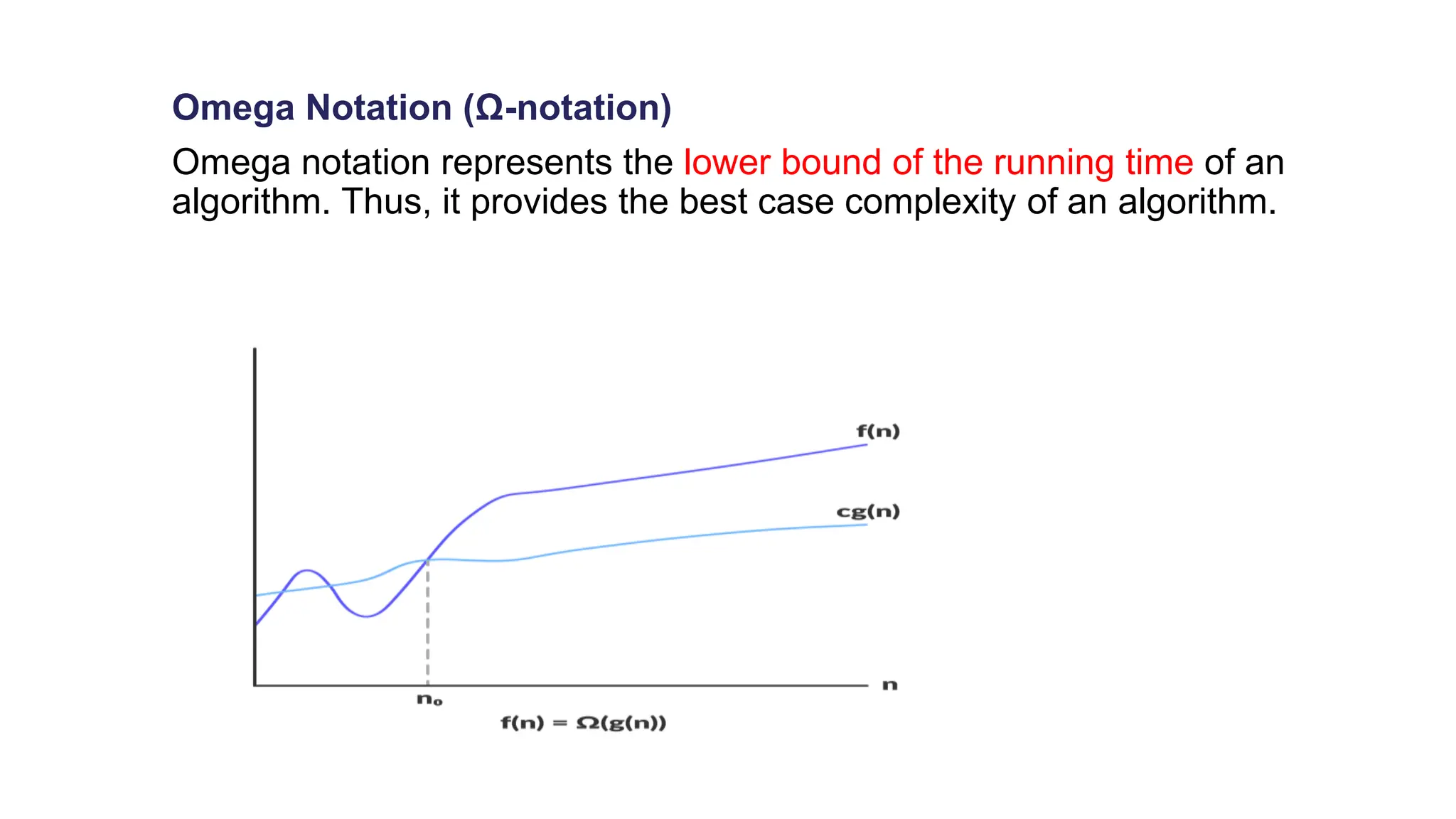
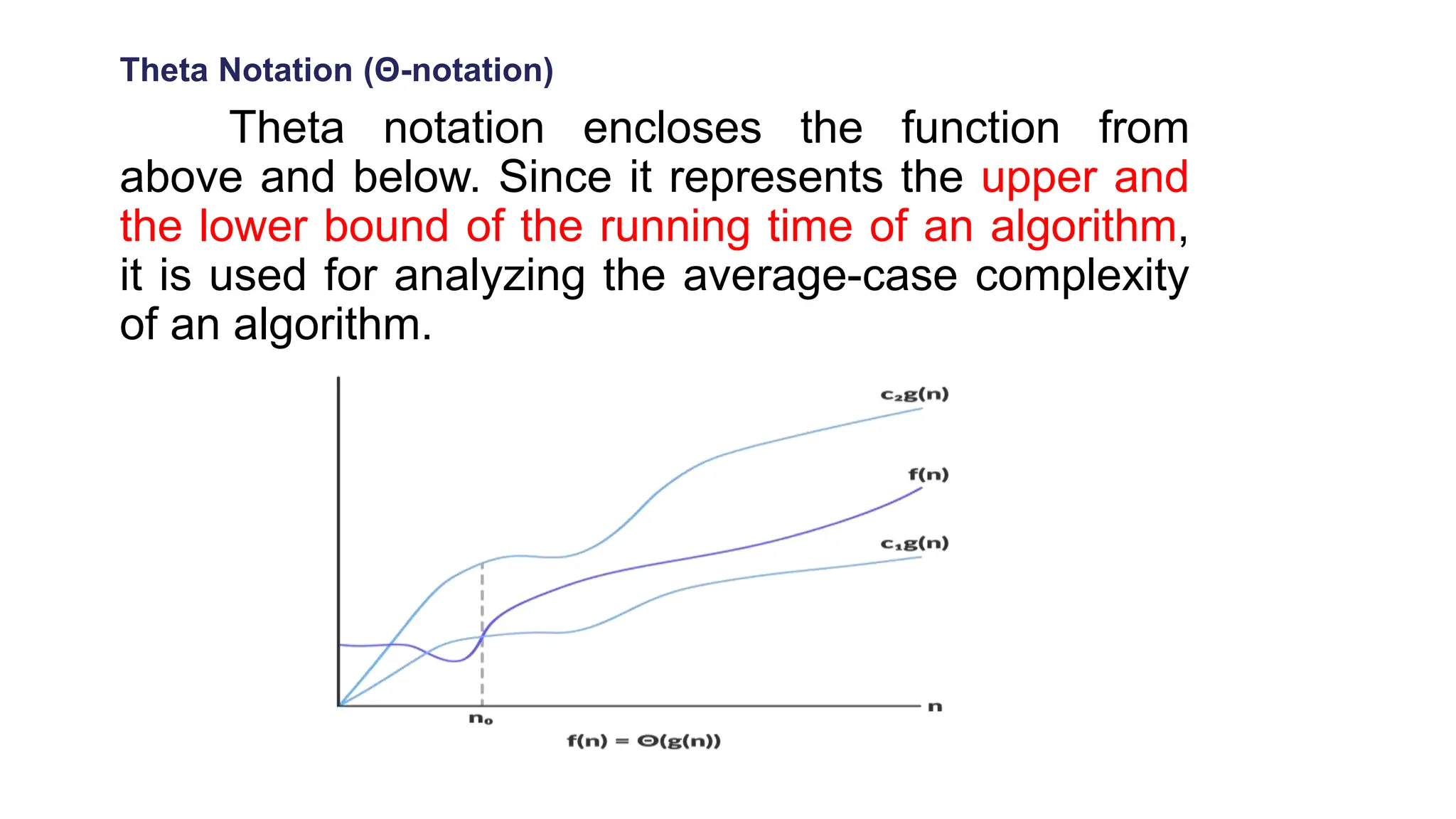
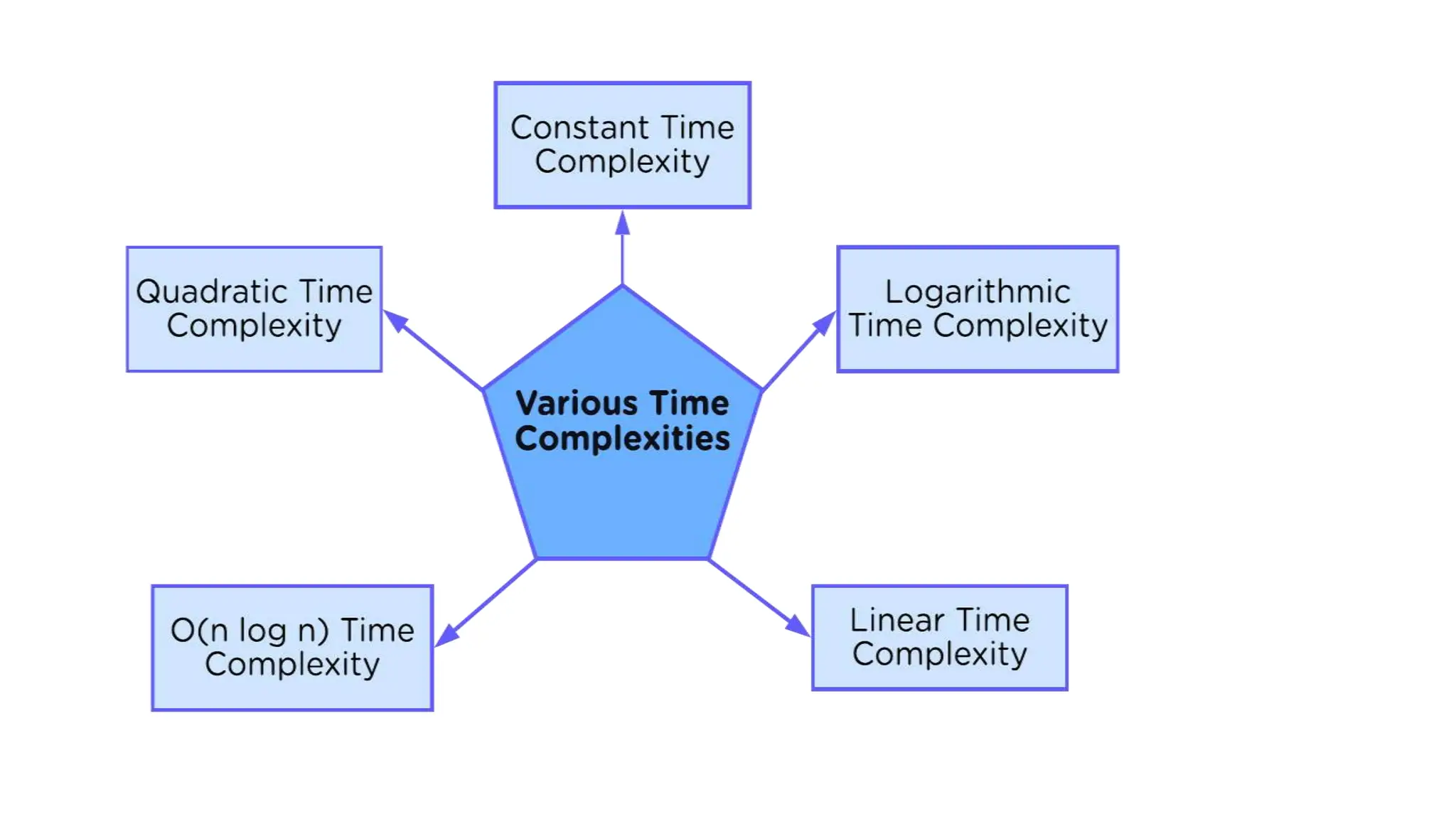
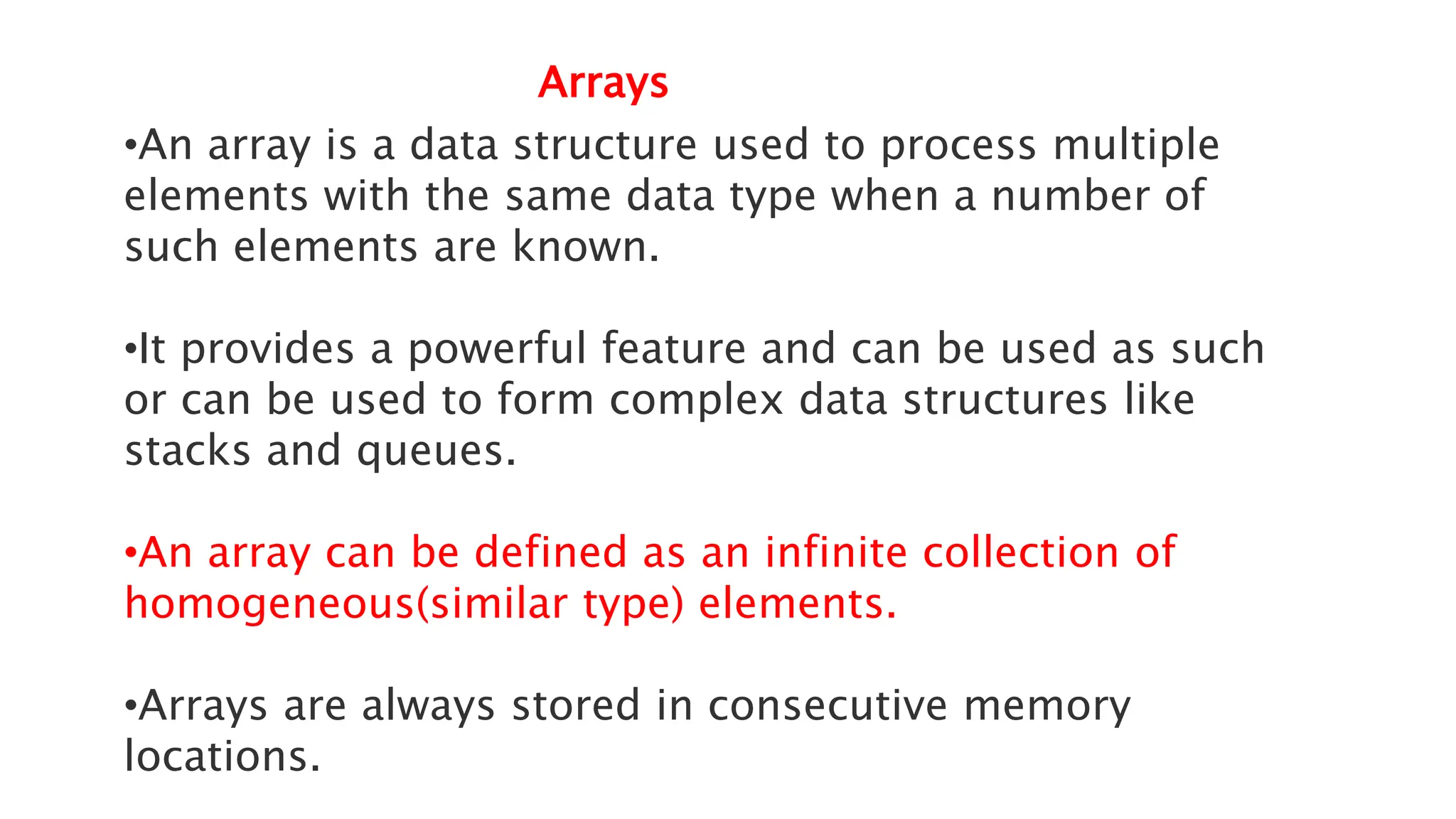
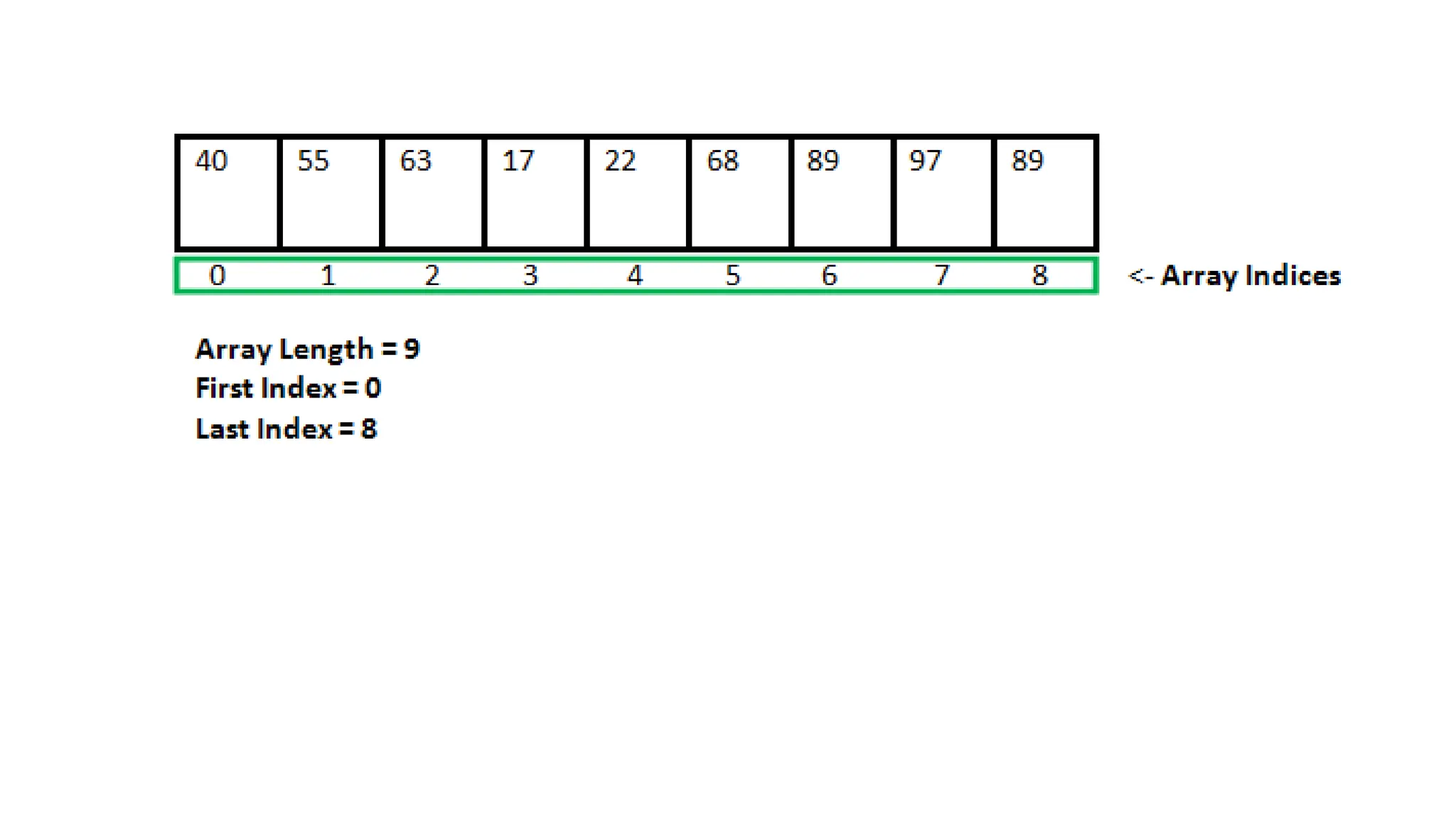
The document discusses asymptotic analysis and algorithm complexity. It defines asymptotic notations like Big-O, Omega, and Theta notations which are used to describe the time complexity of algorithms. Big-O gives the upper bound/worst case, Omega gives the lower bound/best case, and Theta gives both upper and lower bounds for average case. It also discusses space and time complexity analysis of algorithms and different types of time complexities including constant, logarithmic, linear, quadratic, and nlogn time. Finally, it covers arrays, types of arrays, dynamic memory allocation functions in C like malloc, calloc, free, and realloc.








![2]={0,1,2,3,4,5,6,7,8,9,3,2}
In this type of declaration,
we have an array of type integer,
block size is 3,
row size is 2, column size is 2 and we have mentioned the values
inside the curly braces during the declaration of array.
So all the values will be stored one by one in the array cells.
int arr[3][2][2]={0,1,2,3,4,5,6,7,8,9,3,2}
block(1) 0 1 block(2) 4 5 block(3) 8 9
2 3 6 7 3 2
2x2 2x2 2x2](https://image.slidesharecdn.com/module1-240105045918-c8a550af/75/Module-1-notes-of-data-warehousing-and-data-19-2048.jpg)