Illustration of ssl uses both asymmetric and symmetric encryption
•Download as PPTX, PDF•
1 like•410 views
Illustration of ssl uses both asymmetric and symmetric encryption
Report
Share
Report
Share
Recommended
CRYPTOGRAPHY AND NETWORK SECURITY- Transport-level Security

CRYPTOGRAPHY AND NETWORK SECURITY- Transport-level SecurityJyothishmathi Institute of Technology and Science Karimnagar
More Related Content
Viewers also liked
Viewers also liked (7)
Chapter 3: Block Ciphers and the Data Encryption Standard

Chapter 3: Block Ciphers and the Data Encryption Standard
Classical Encryption Techniques in Network Security

Classical Encryption Techniques in Network Security
Similar to Illustration of ssl uses both asymmetric and symmetric encryption
CRYPTOGRAPHY AND NETWORK SECURITY- Transport-level Security

CRYPTOGRAPHY AND NETWORK SECURITY- Transport-level SecurityJyothishmathi Institute of Technology and Science Karimnagar
Similar to Illustration of ssl uses both asymmetric and symmetric encryption (20)
What is SSL ? The Secure Sockets Layer (SSL) Protocol

What is SSL ? The Secure Sockets Layer (SSL) Protocol
CRYPTOGRAPHY AND NETWORK SECURITY- Transport-level Security

CRYPTOGRAPHY AND NETWORK SECURITY- Transport-level Security
SSL Implementation - IBM MQ - Secure Communications 

SSL Implementation - IBM MQ - Secure Communications
Recently uploaded
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...Enterprise Knowledge
Recently uploaded (20)
Exploring the Future Potential of AI-Enabled Smartphone Processors

Exploring the Future Potential of AI-Enabled Smartphone Processors
Factors to Consider When Choosing Accounts Payable Services Providers.pptx

Factors to Consider When Choosing Accounts Payable Services Providers.pptx
08448380779 Call Girls In Diplomatic Enclave Women Seeking Men

08448380779 Call Girls In Diplomatic Enclave Women Seeking Men
Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024

Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024
Advantages of Hiring UIUX Design Service Providers for Your Business

Advantages of Hiring UIUX Design Service Providers for Your Business
Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...

Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...
2024: Domino Containers - The Next Step. News from the Domino Container commu...

2024: Domino Containers - The Next Step. News from the Domino Container commu...
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
What Are The Drone Anti-jamming Systems Technology?

What Are The Drone Anti-jamming Systems Technology?
The Codex of Business Writing Software for Real-World Solutions 2.pptx

The Codex of Business Writing Software for Real-World Solutions 2.pptx
Boost PC performance: How more available memory can improve productivity

Boost PC performance: How more available memory can improve productivity
Presentation on how to chat with PDF using ChatGPT code interpreter

Presentation on how to chat with PDF using ChatGPT code interpreter
TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments

TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments
Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...

Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...
Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...

Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...
IAC 2024 - IA Fast Track to Search Focused AI Solutions

IAC 2024 - IA Fast Track to Search Focused AI Solutions
Illustration of ssl uses both asymmetric and symmetric encryption
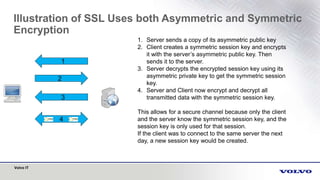
- 1. Volvo IT 4 Illustration of SSL Uses both Asymmetric and Symmetric Encryption 1 2 3 1. Server sends a copy of its asymmetric public key 2. Client creates a symmetric session key and encrypts it with the server’s asymmetric public key. Then sends it to the server. 3. Server decrypts the encrypted session key using its asymmetric private key to get the symmetric session key. 4. Server and Client now encrypt and decrypt all transmitted data with the symmetric session key. This allows for a secure channel because only the client and the server know the symmetric session key, and the session key is only used for that session. If the client was to connect to the same server the next day, a new session key would be created.
- 2. Volvo IT Steps Detail of SSL Handshake (Key Establishment) SSL Client e.g. LeaseVision SSL Server e.g. IIB (MQ) 1. Client Hello 2. Server Responds with Certificate 4. Client Encrypts Session Key with Server Certificate and Sends to Server 3. Client Creates Session Key 5. Server Decrypts Session Key 6. Session Key Used for Remainder of SSL Session • Server requires a digital certificate, which includes the server’s subject name, its public key, and a signature. • When a client establishes a connection to the server, the server authenticated to the client by submitting its certificate, the client then validates the certificate by referring to the signature.
