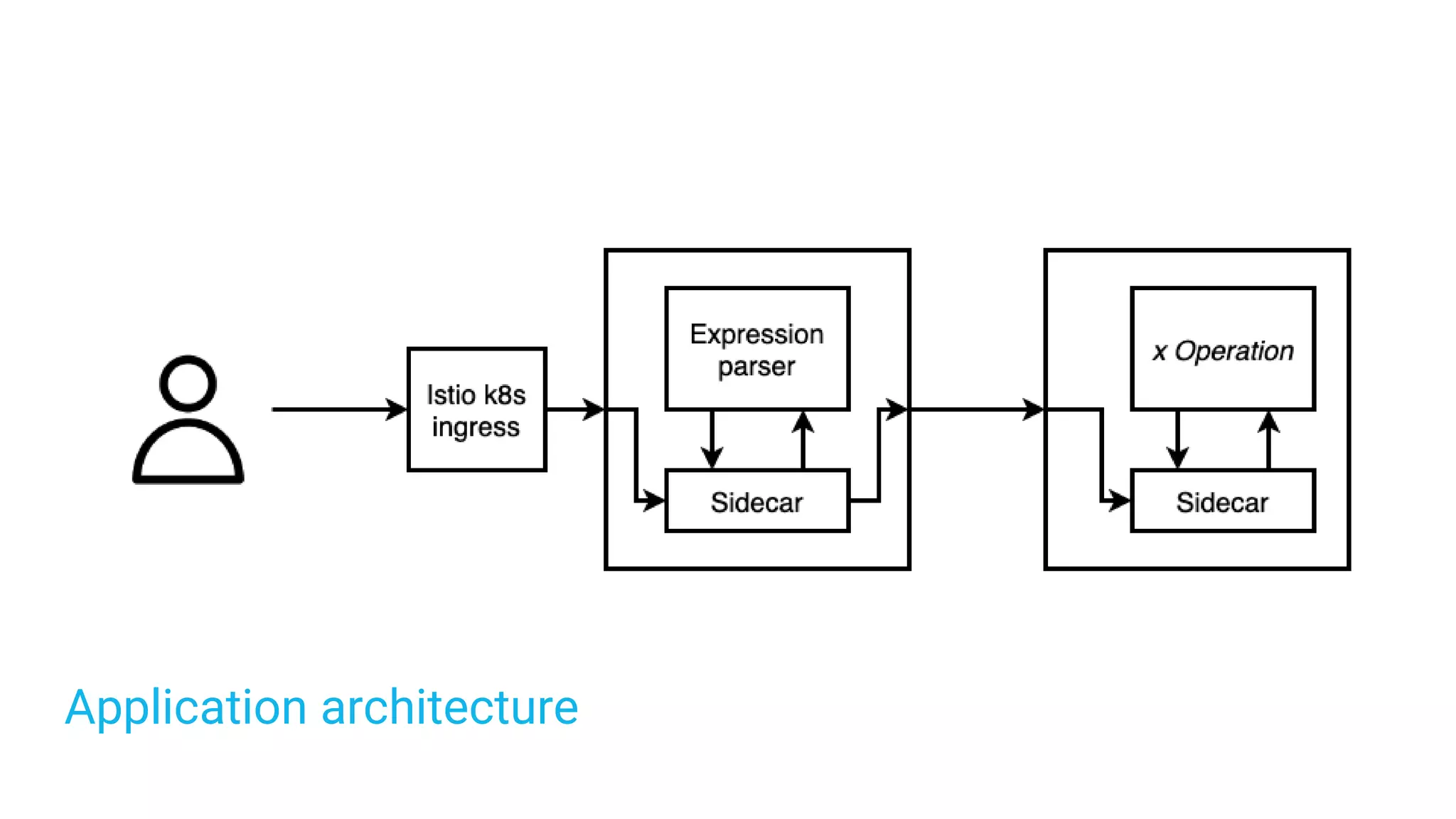
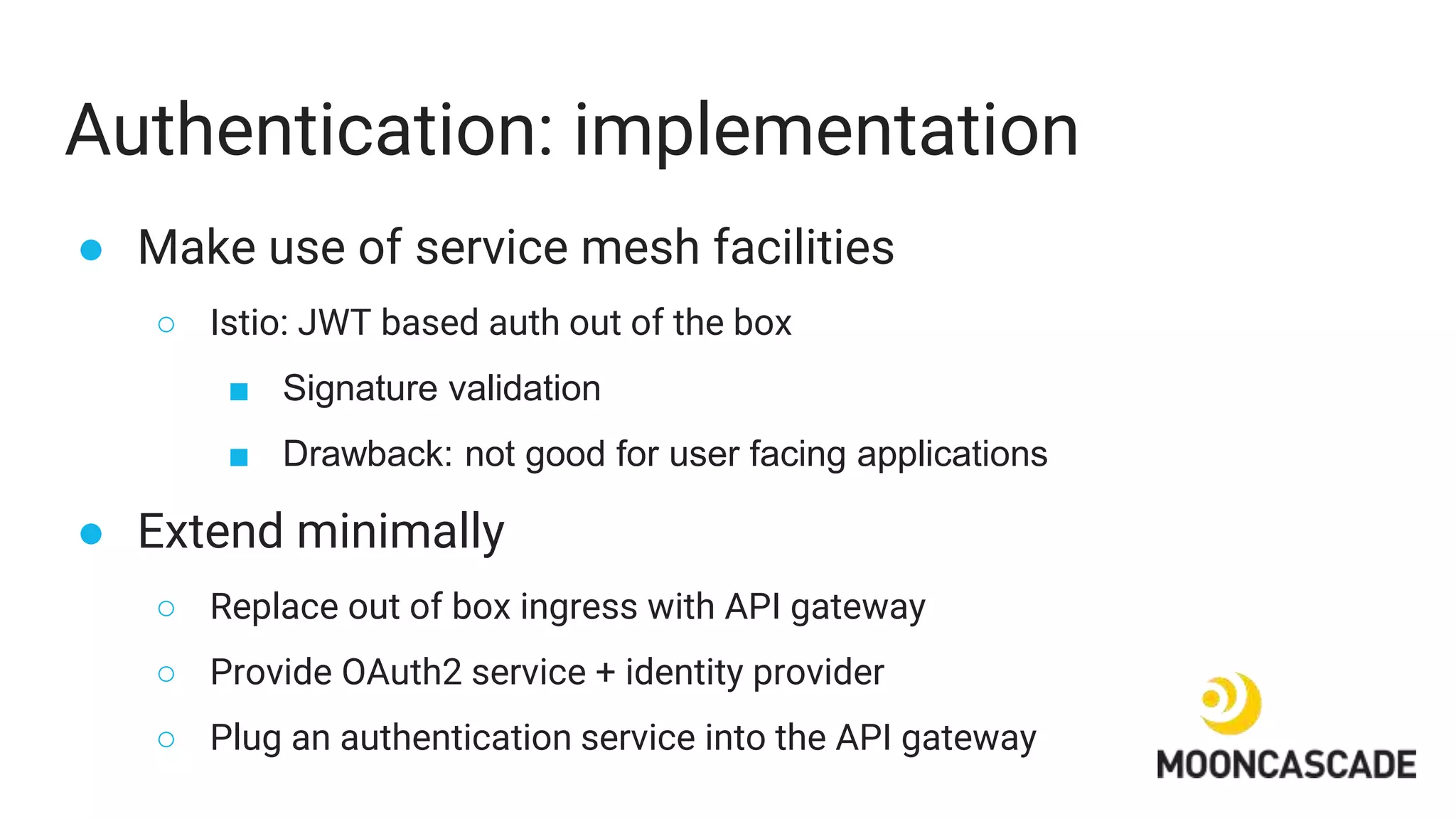
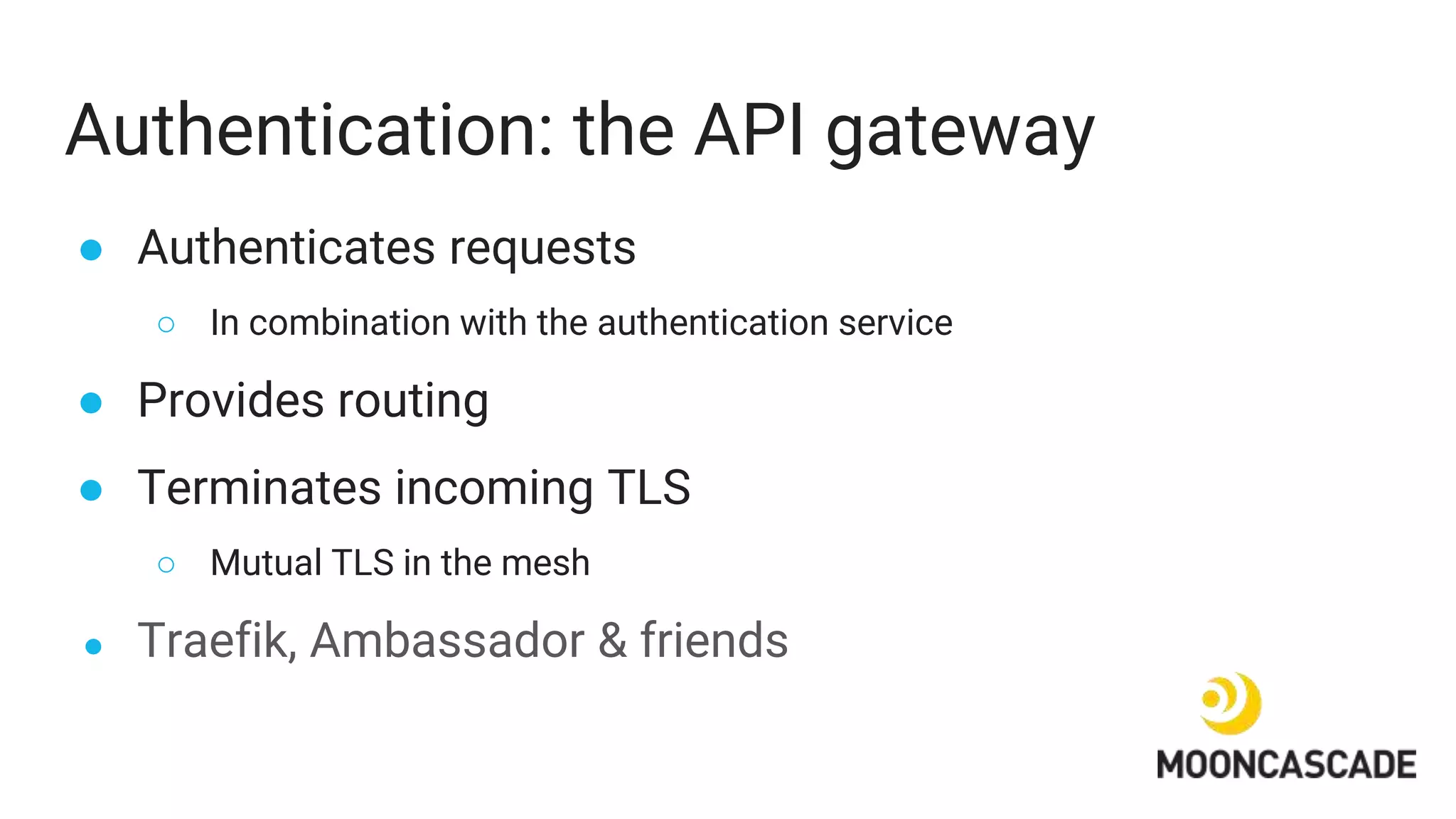
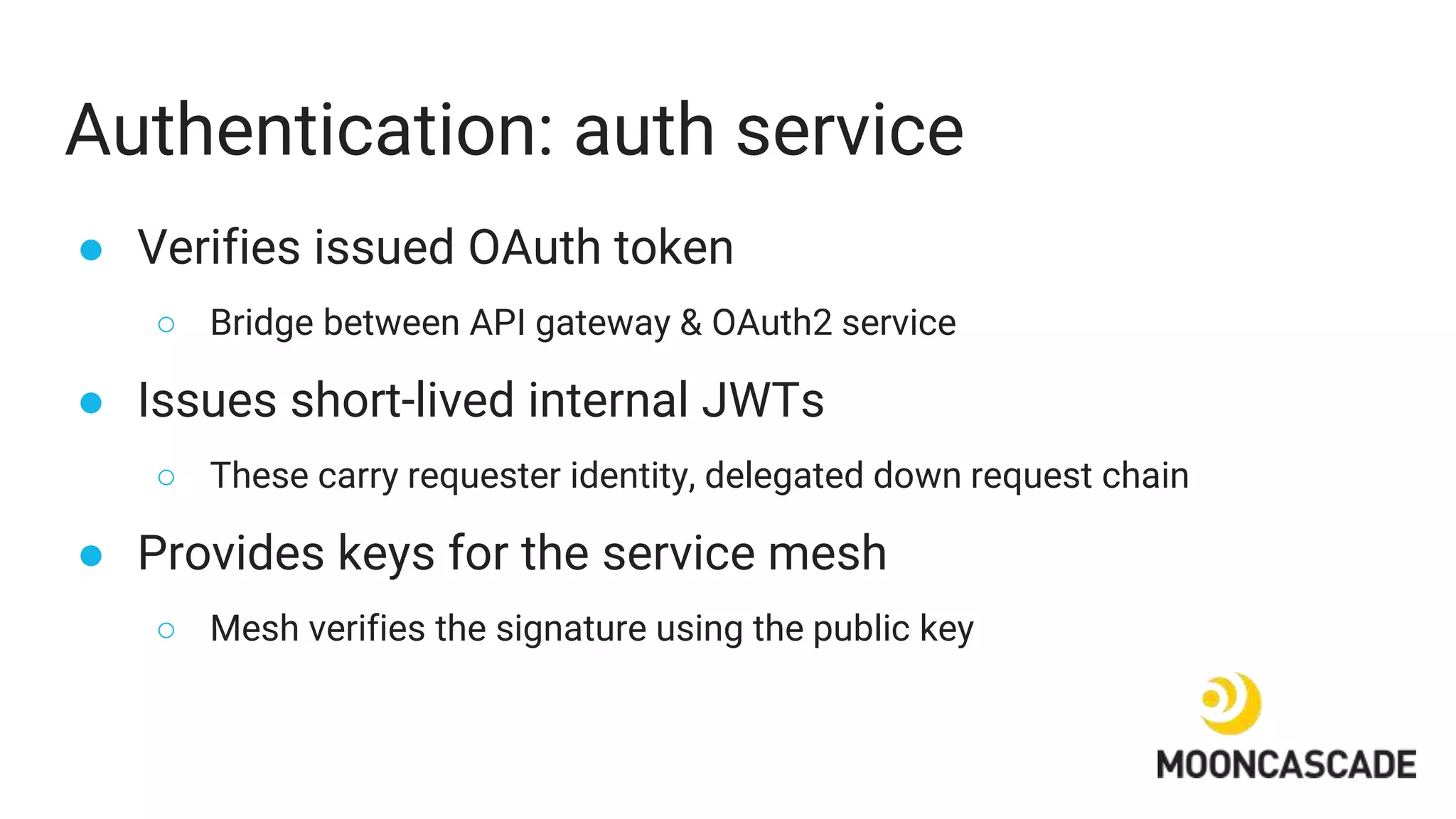
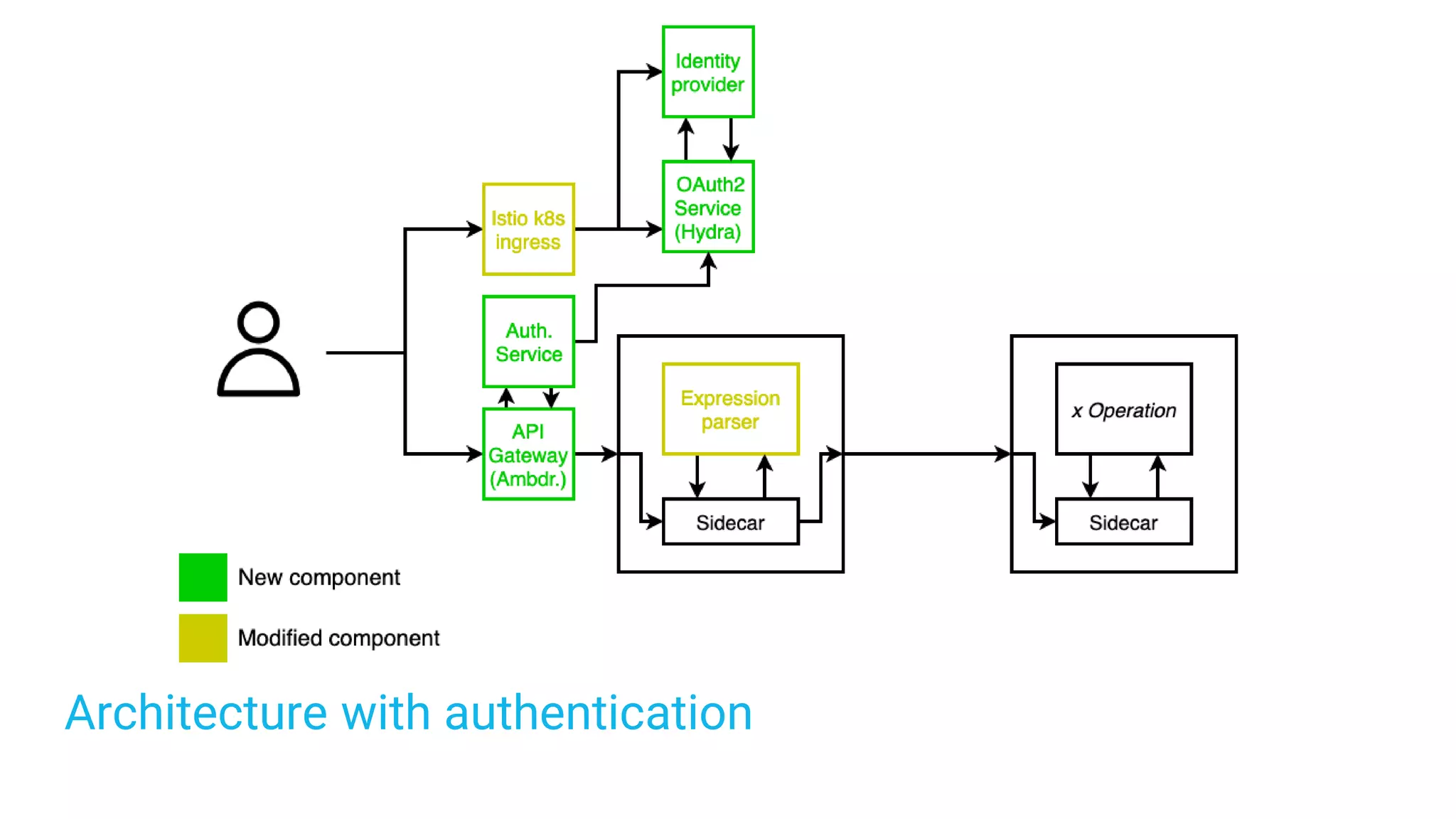
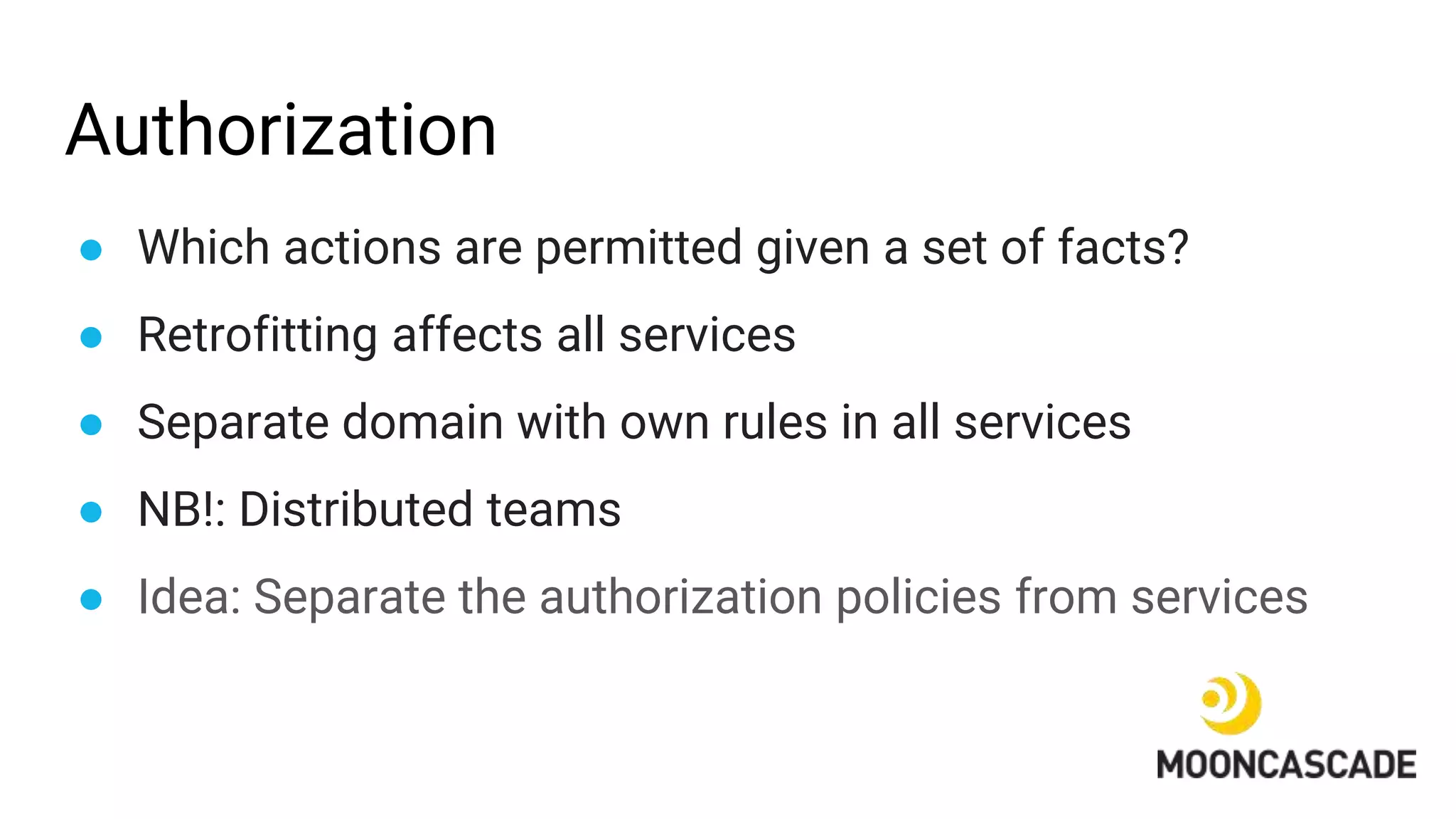
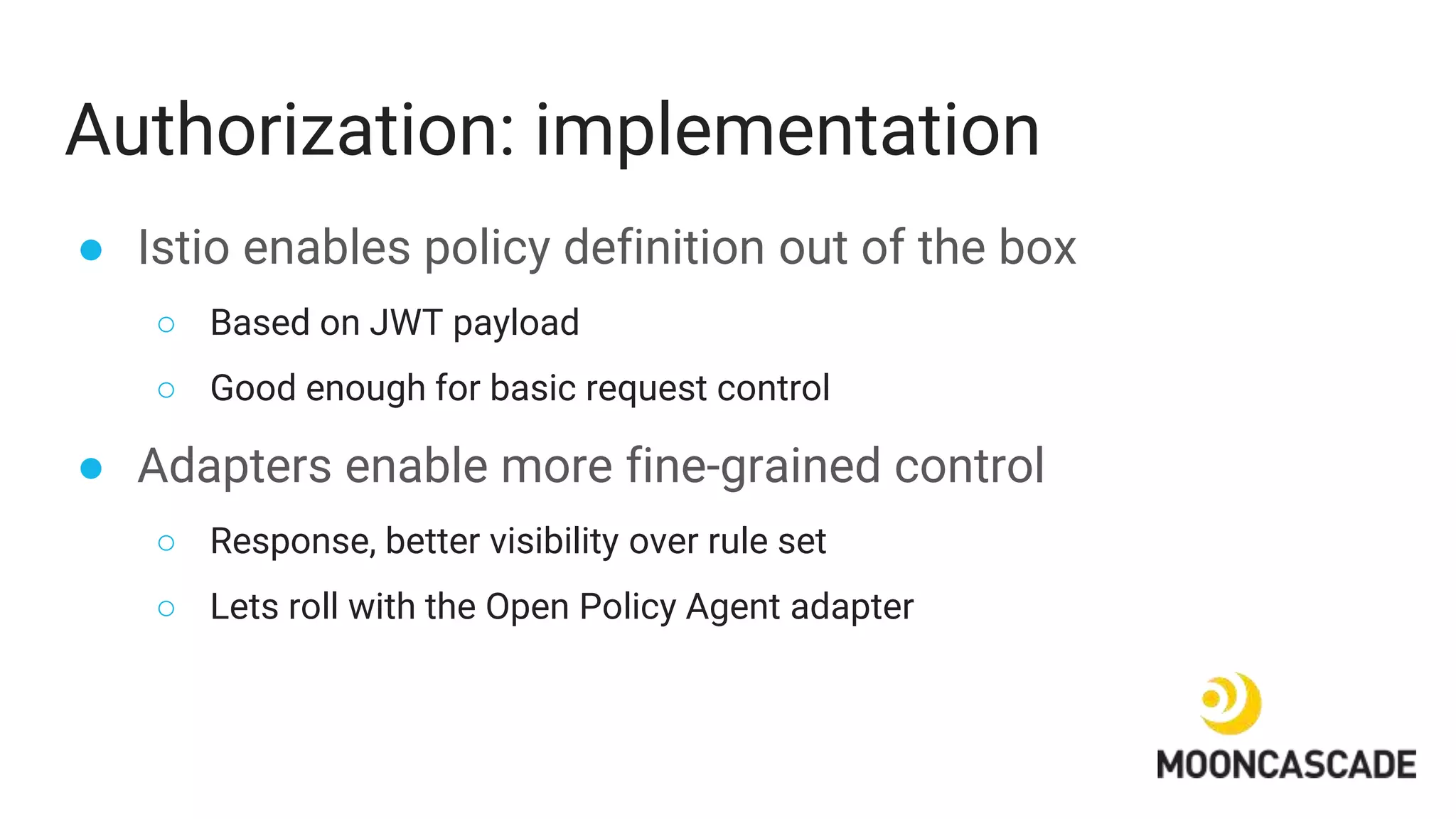
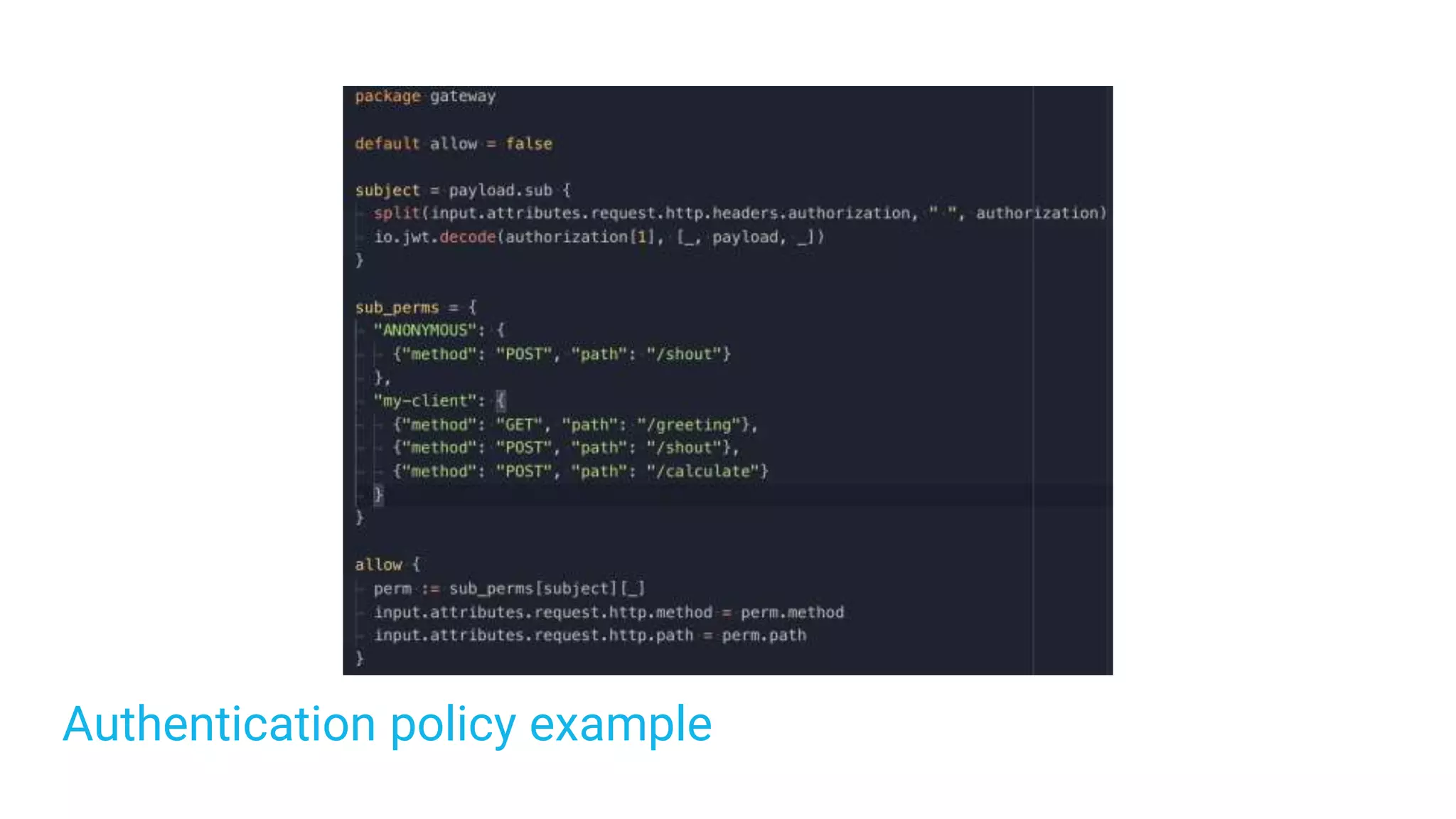
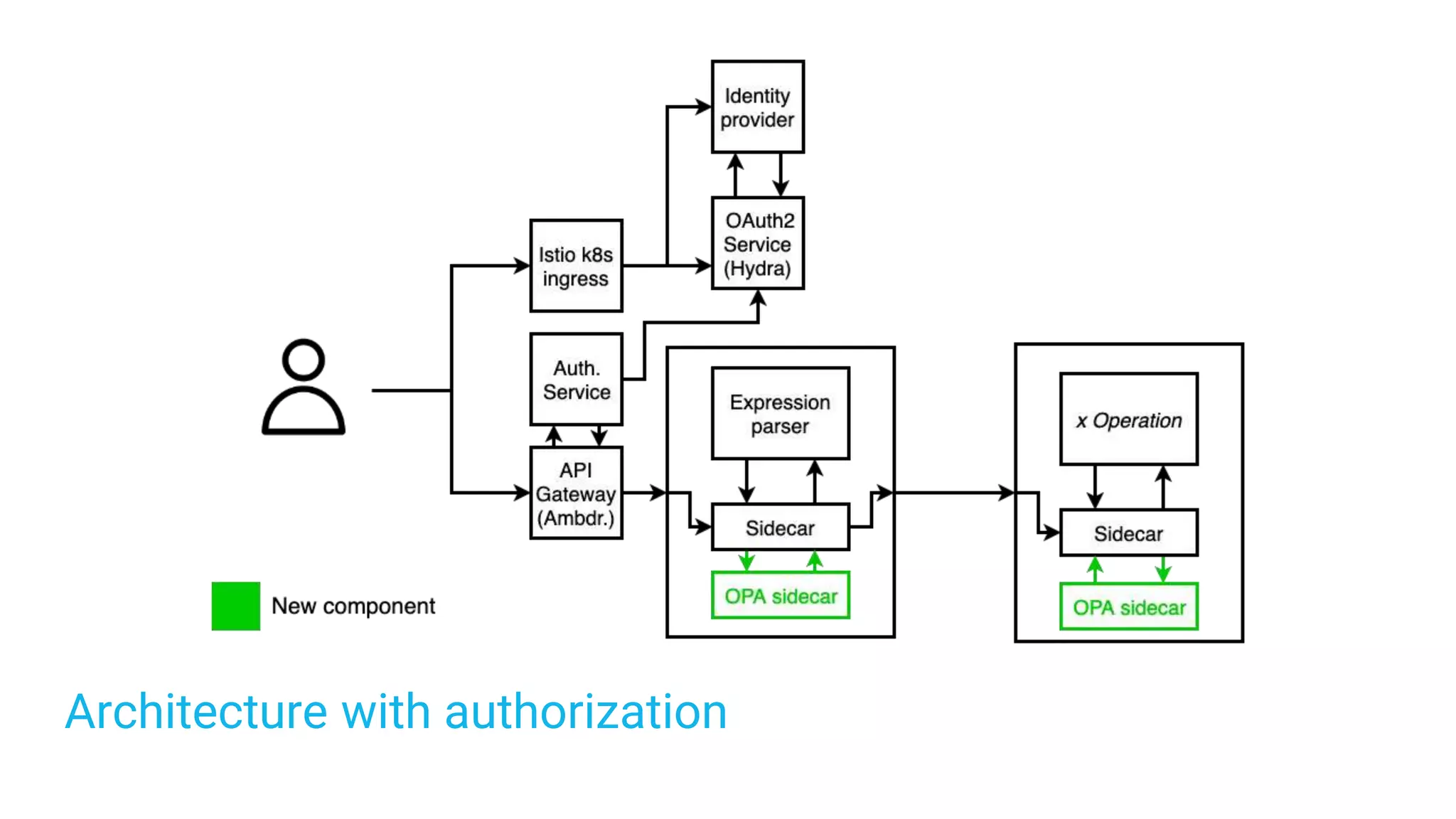
The document discusses adding authentication and authorization to an externally facing service mesh application. It introduces authentication using the OAuth 2.0 framework with an API gateway and authentication service. Authorization is implemented using Open Policy Agent to define policies separately from services. The resulting architecture separates authentication, authorization, and application services for improved scalability and team autonomy.