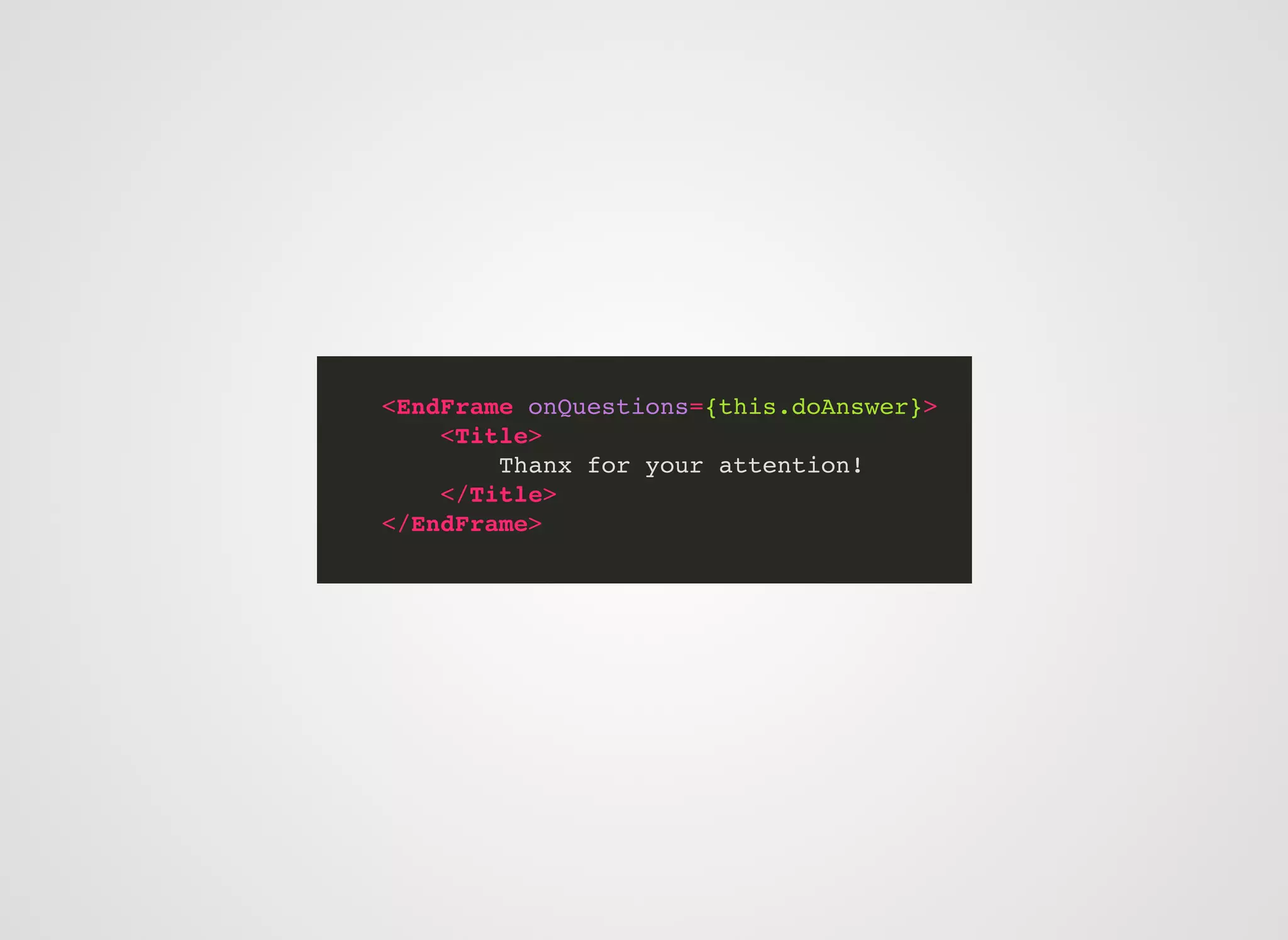
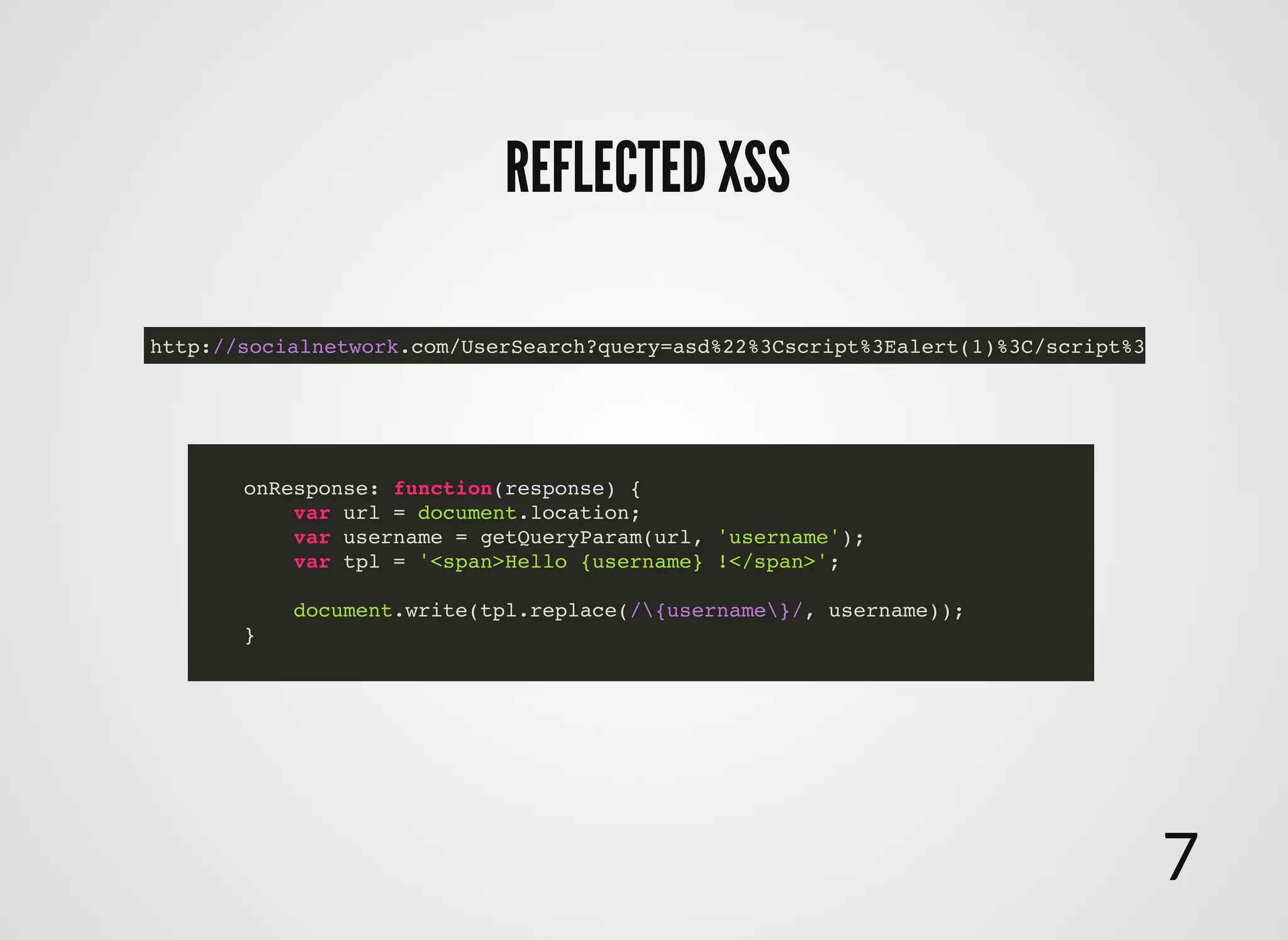
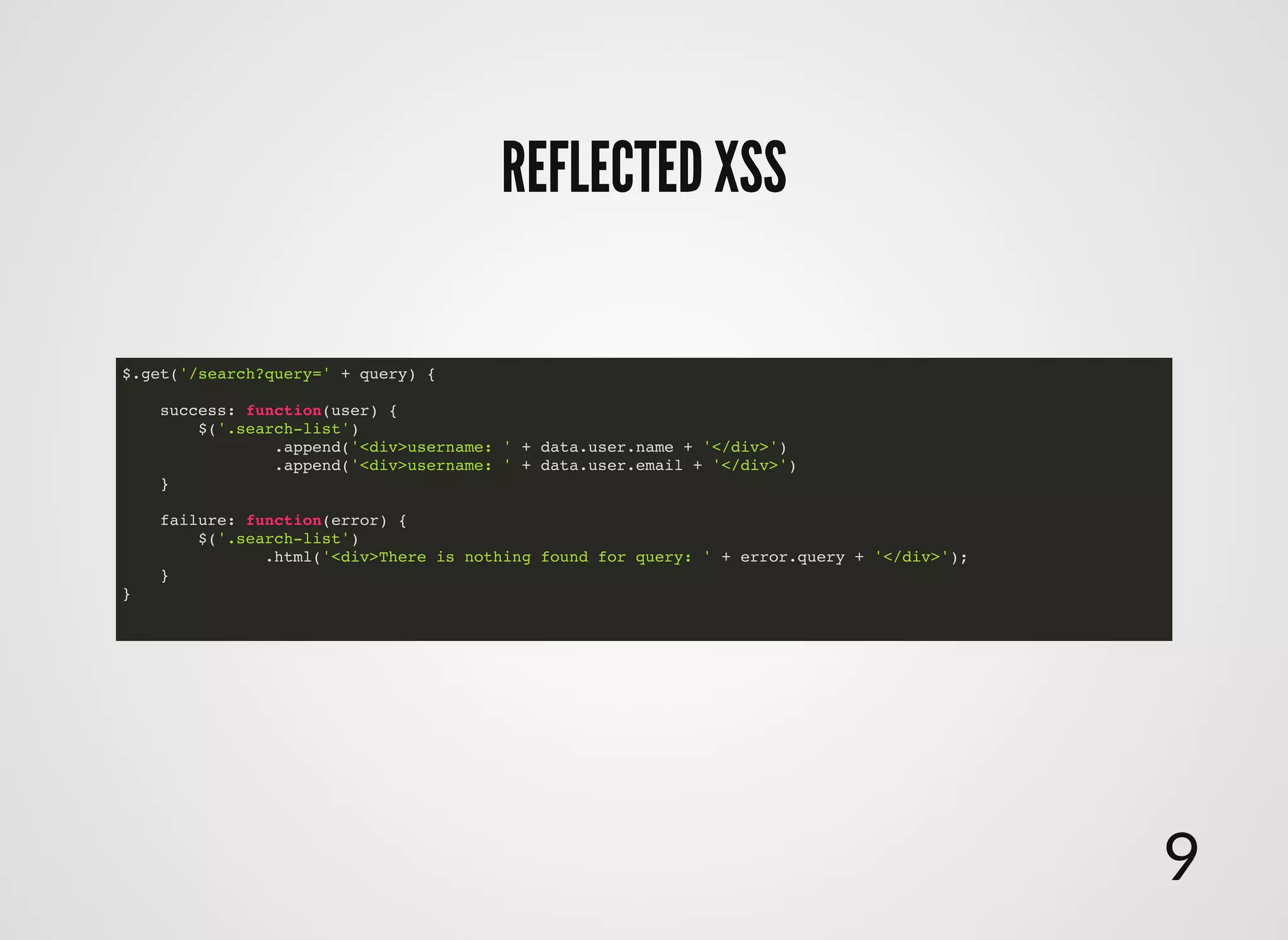
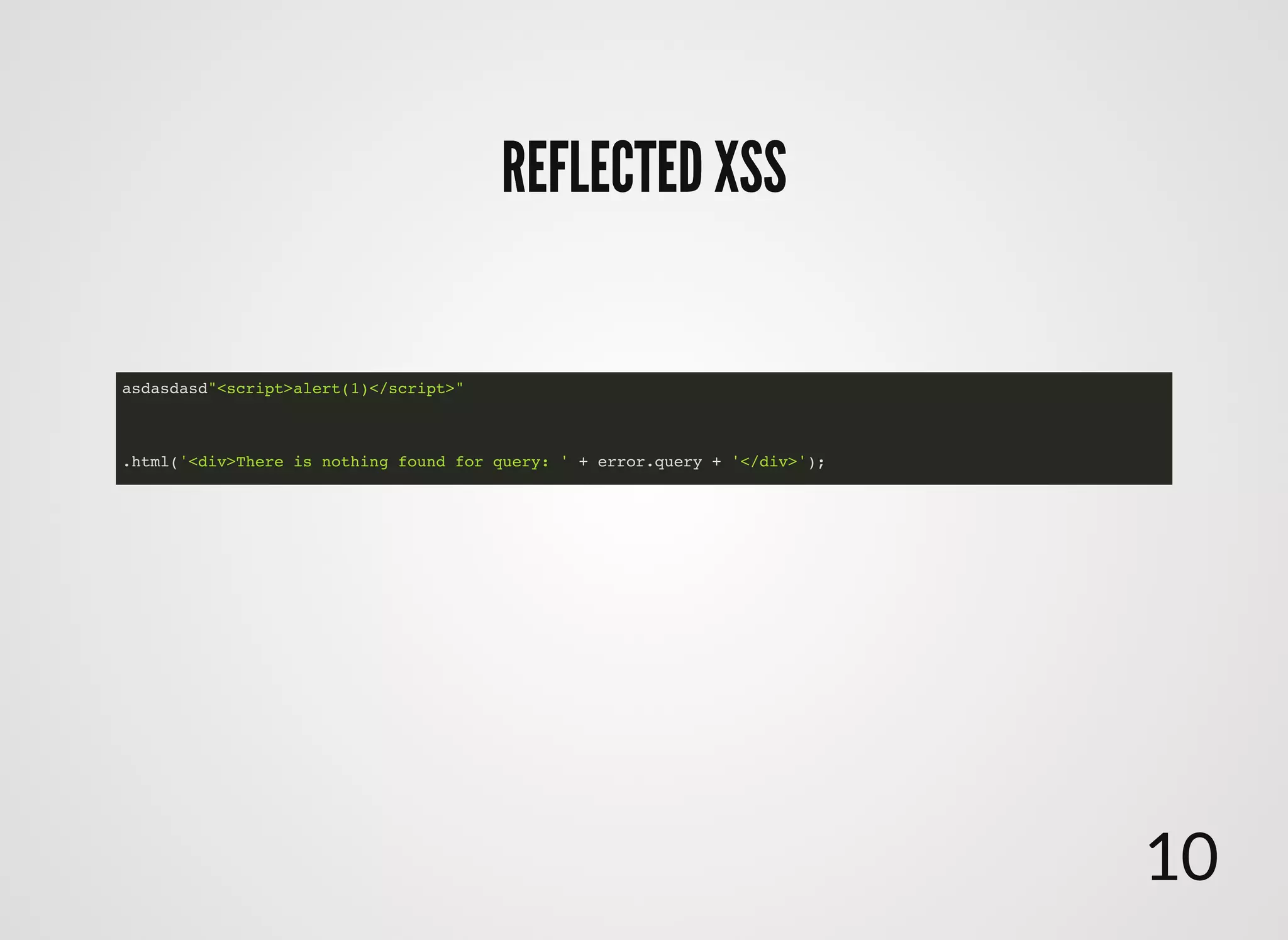
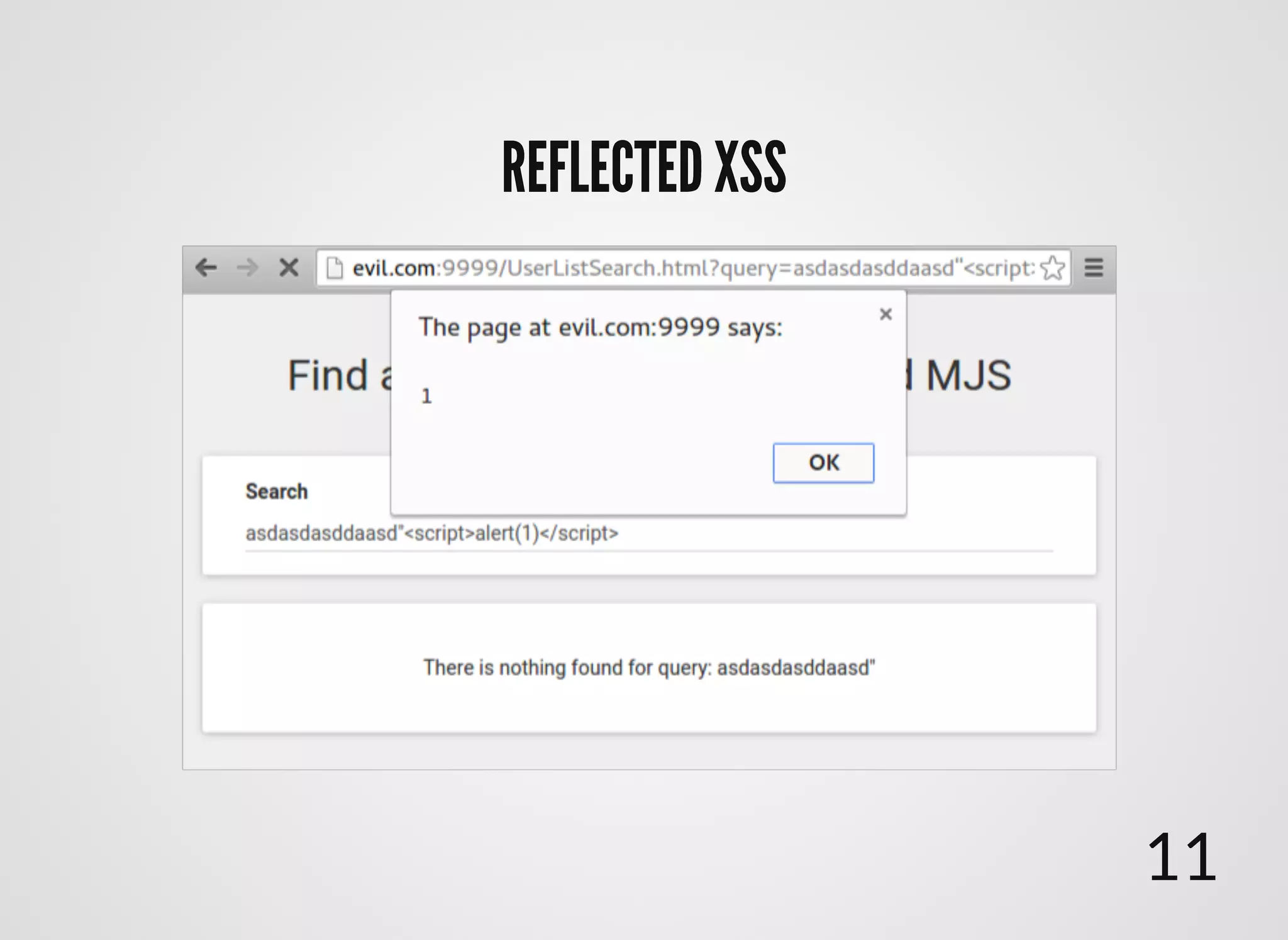
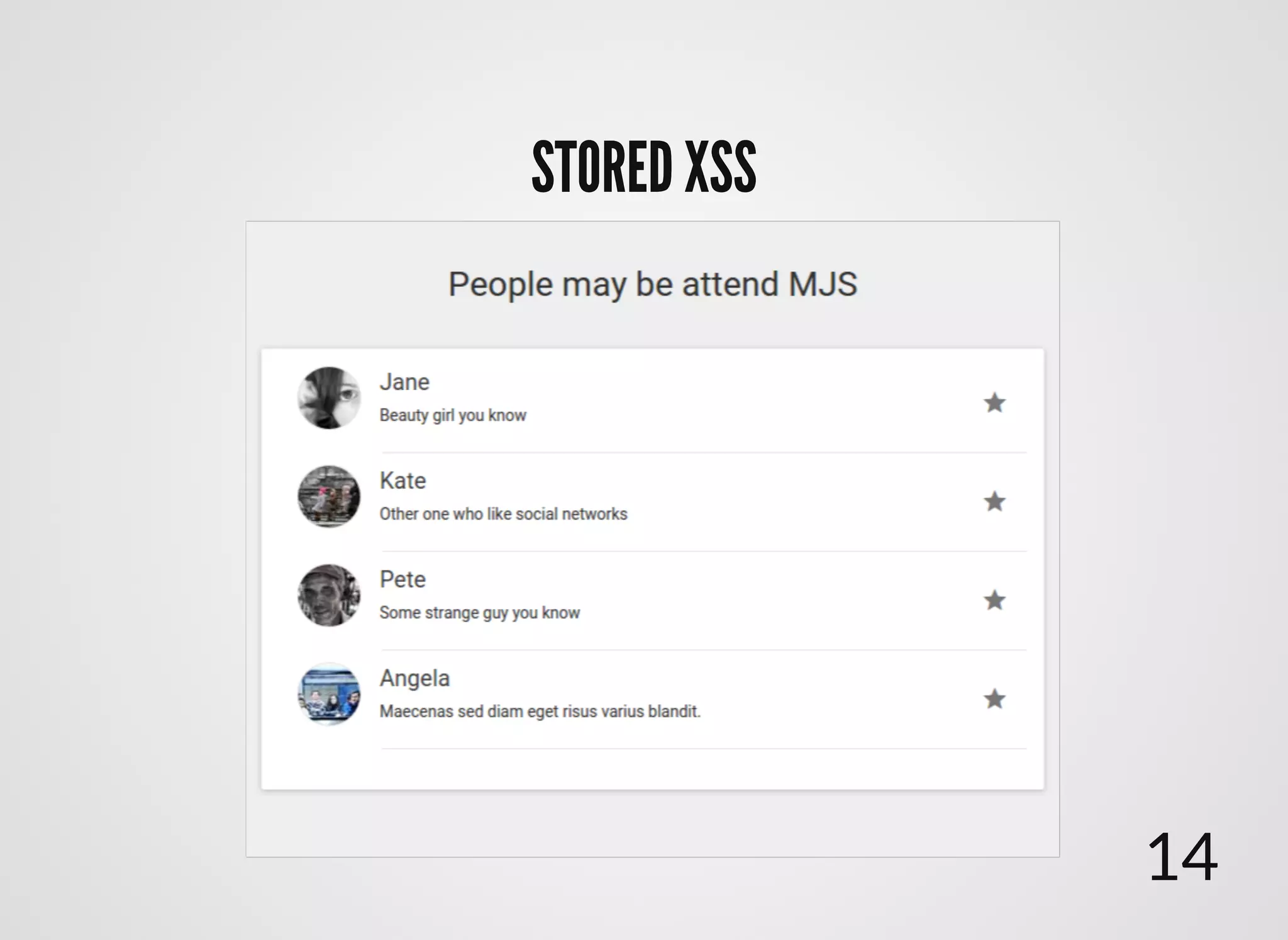
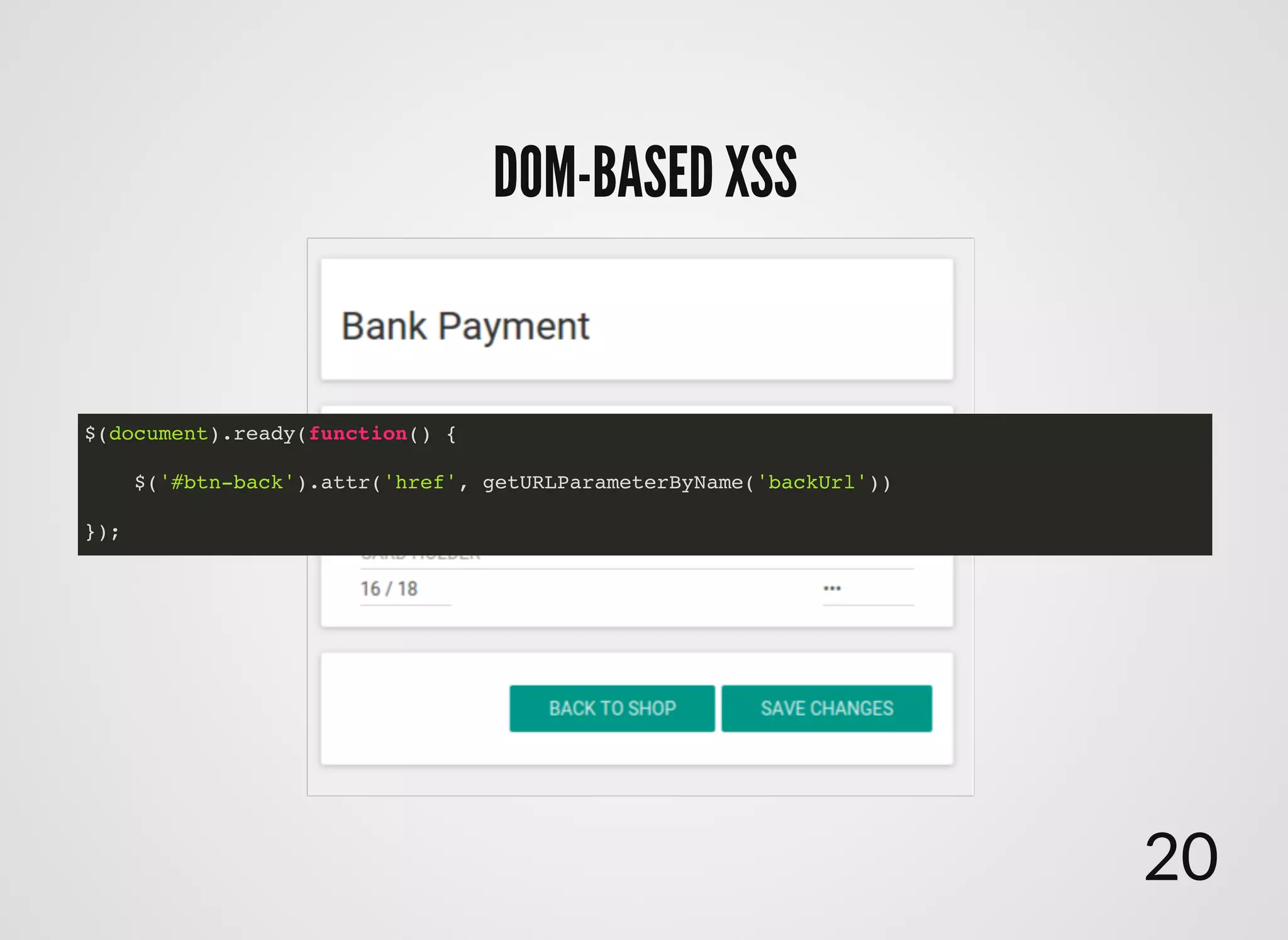
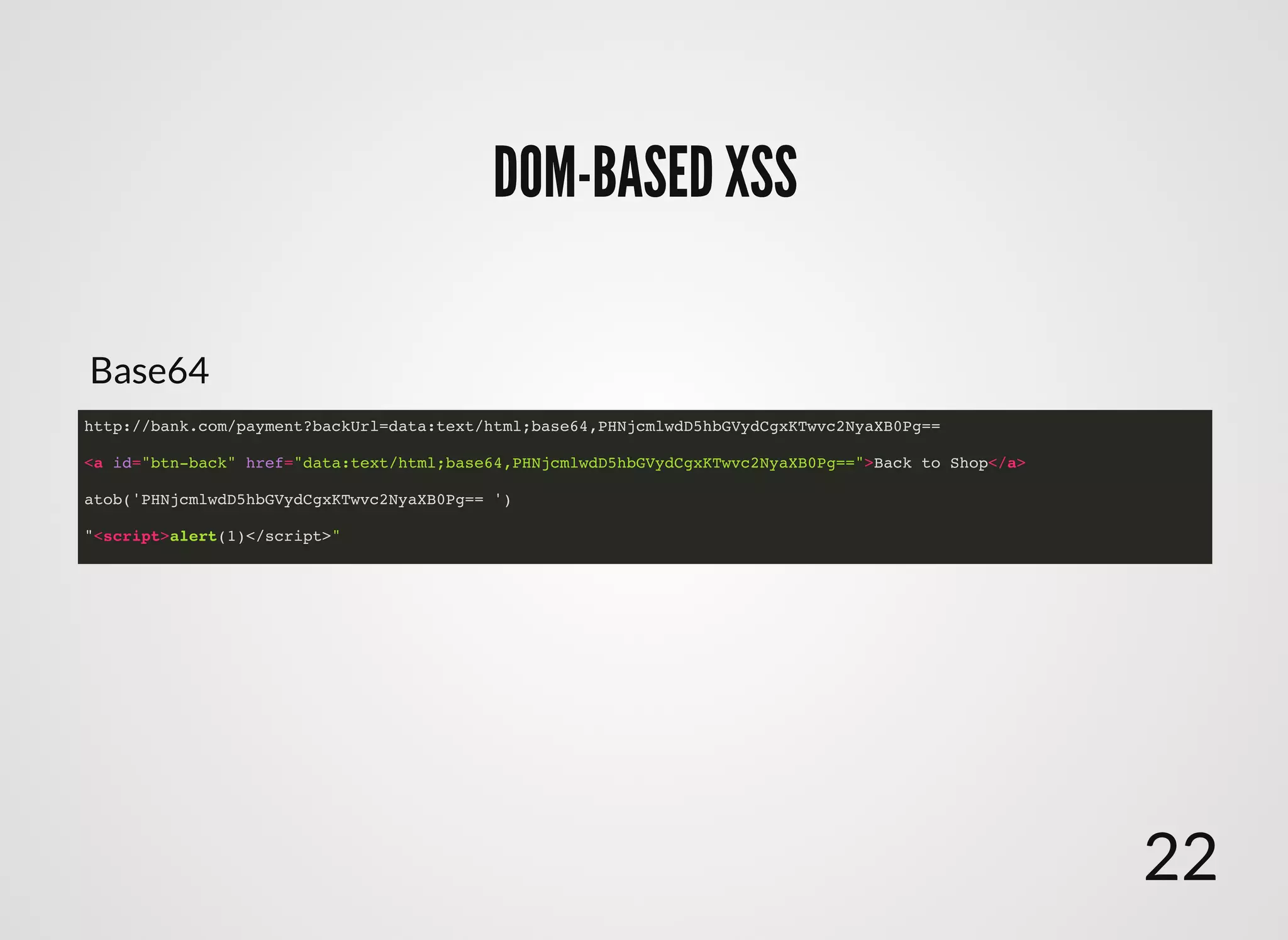
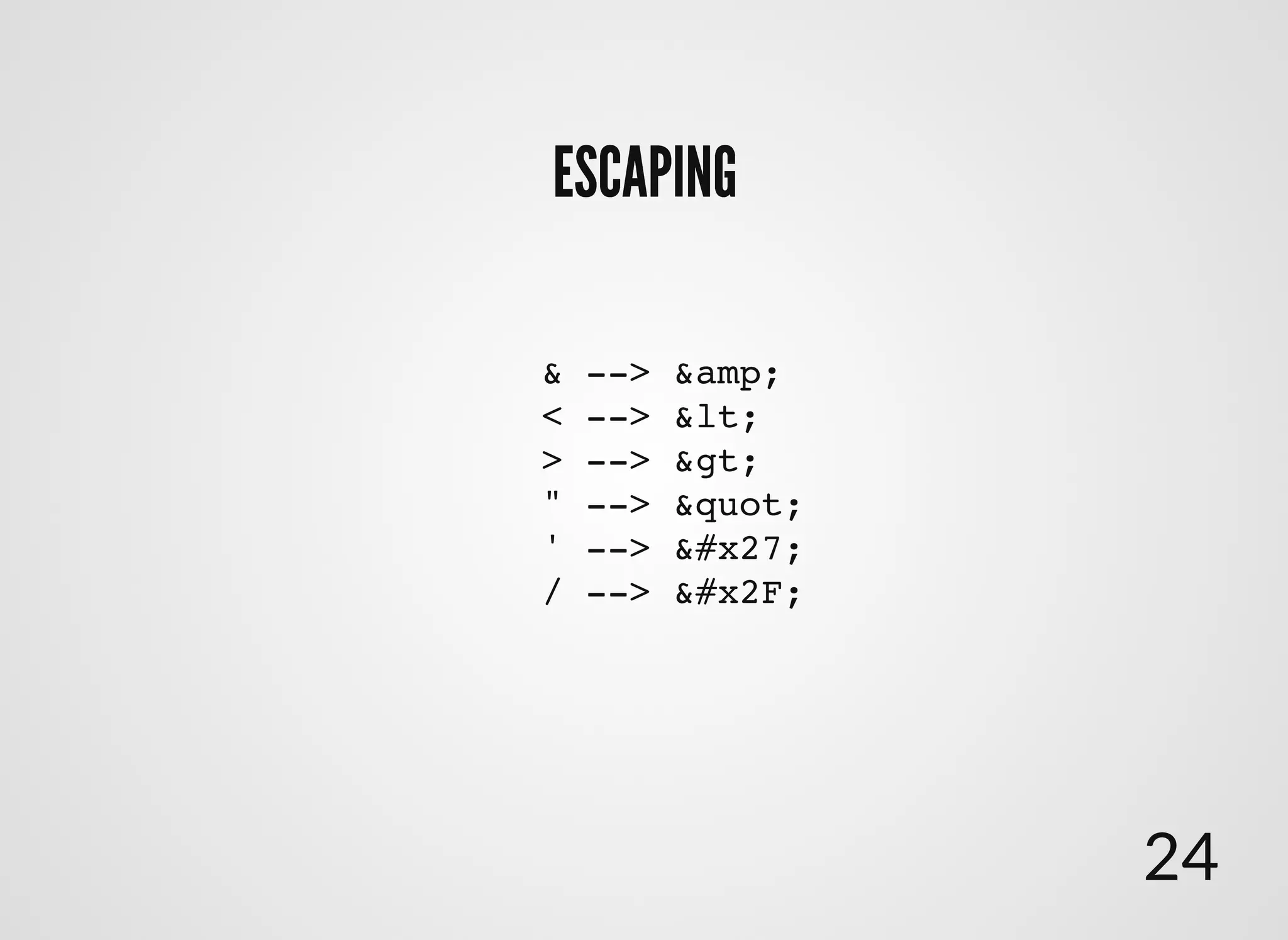
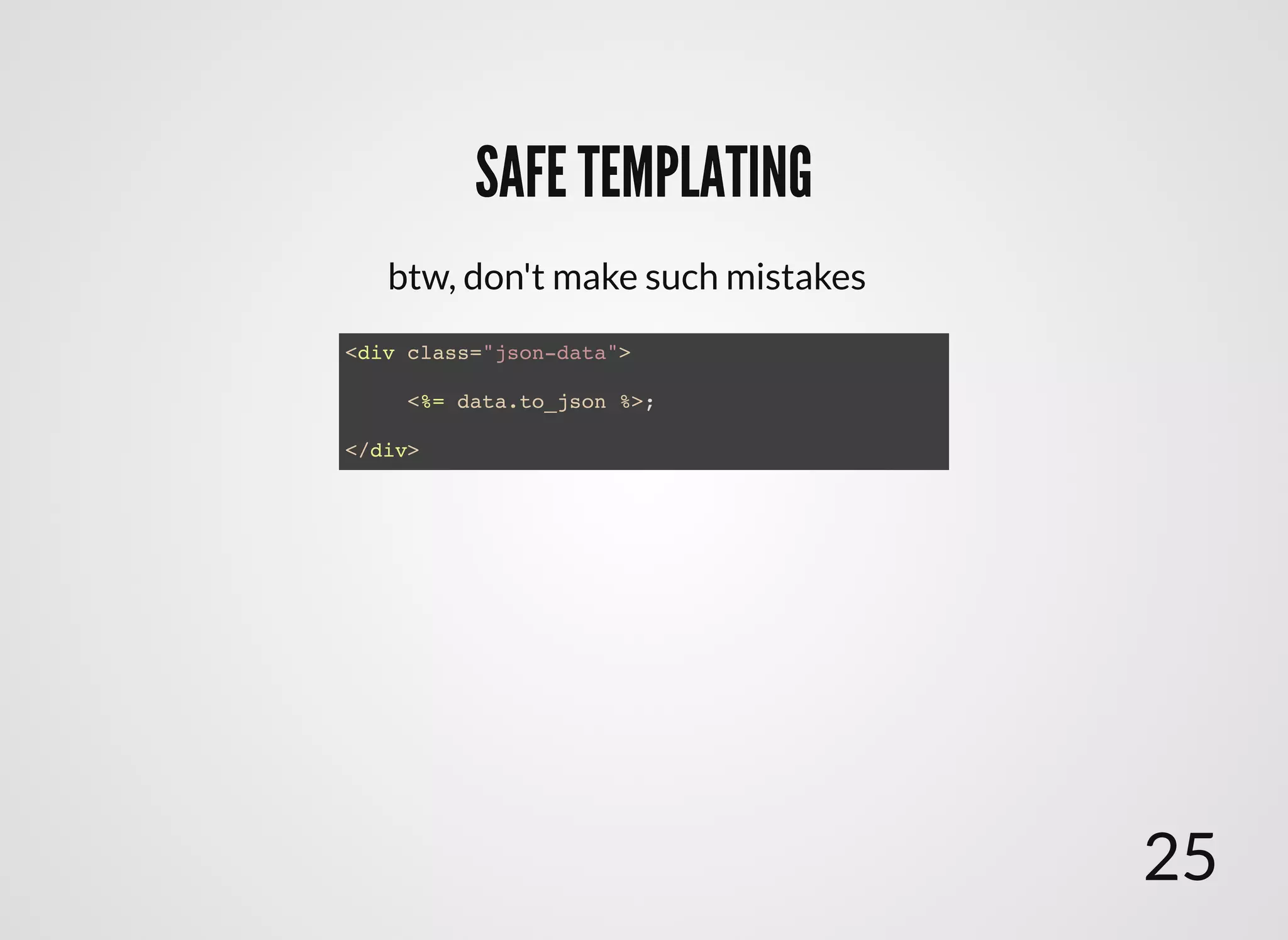
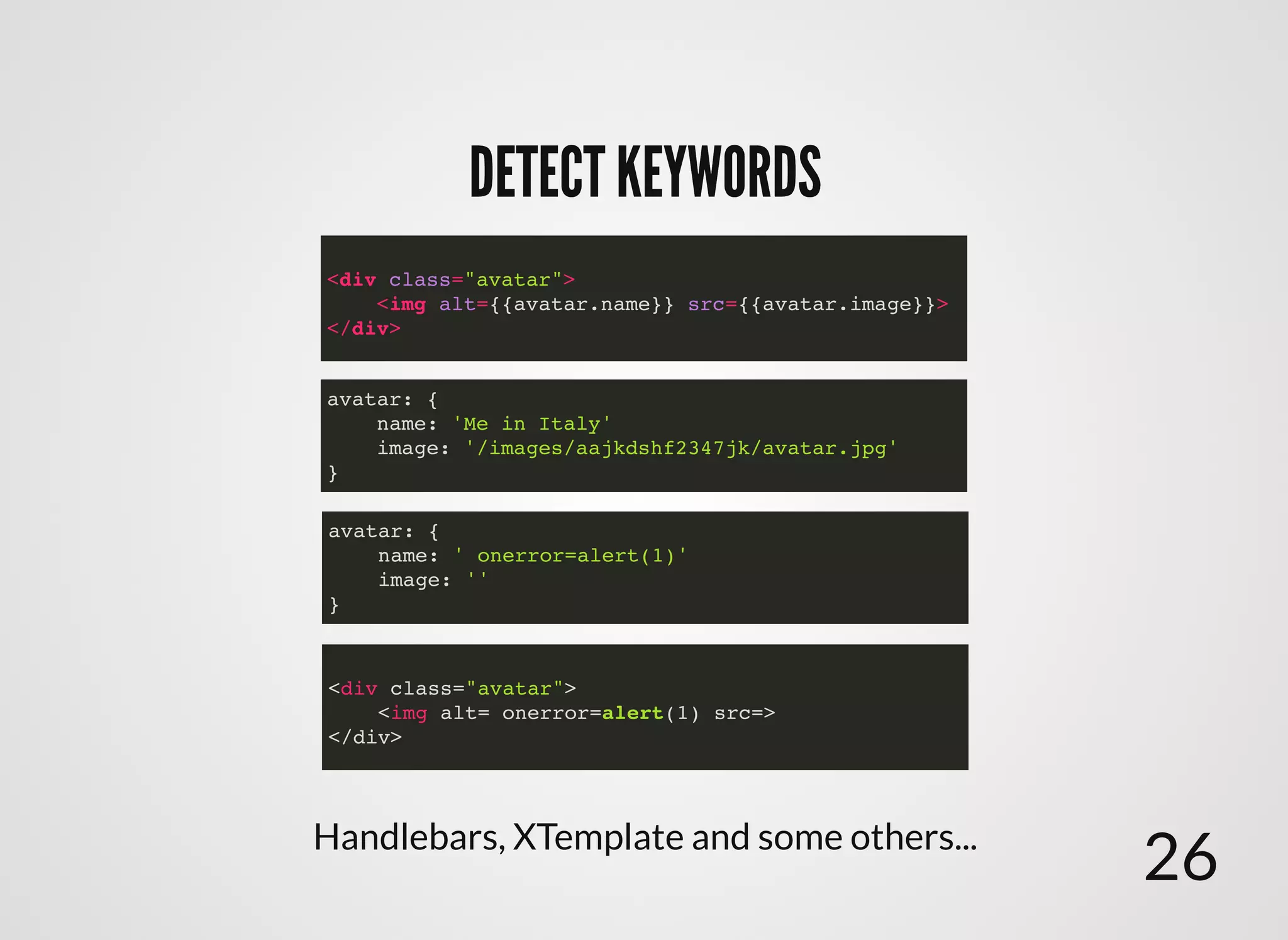
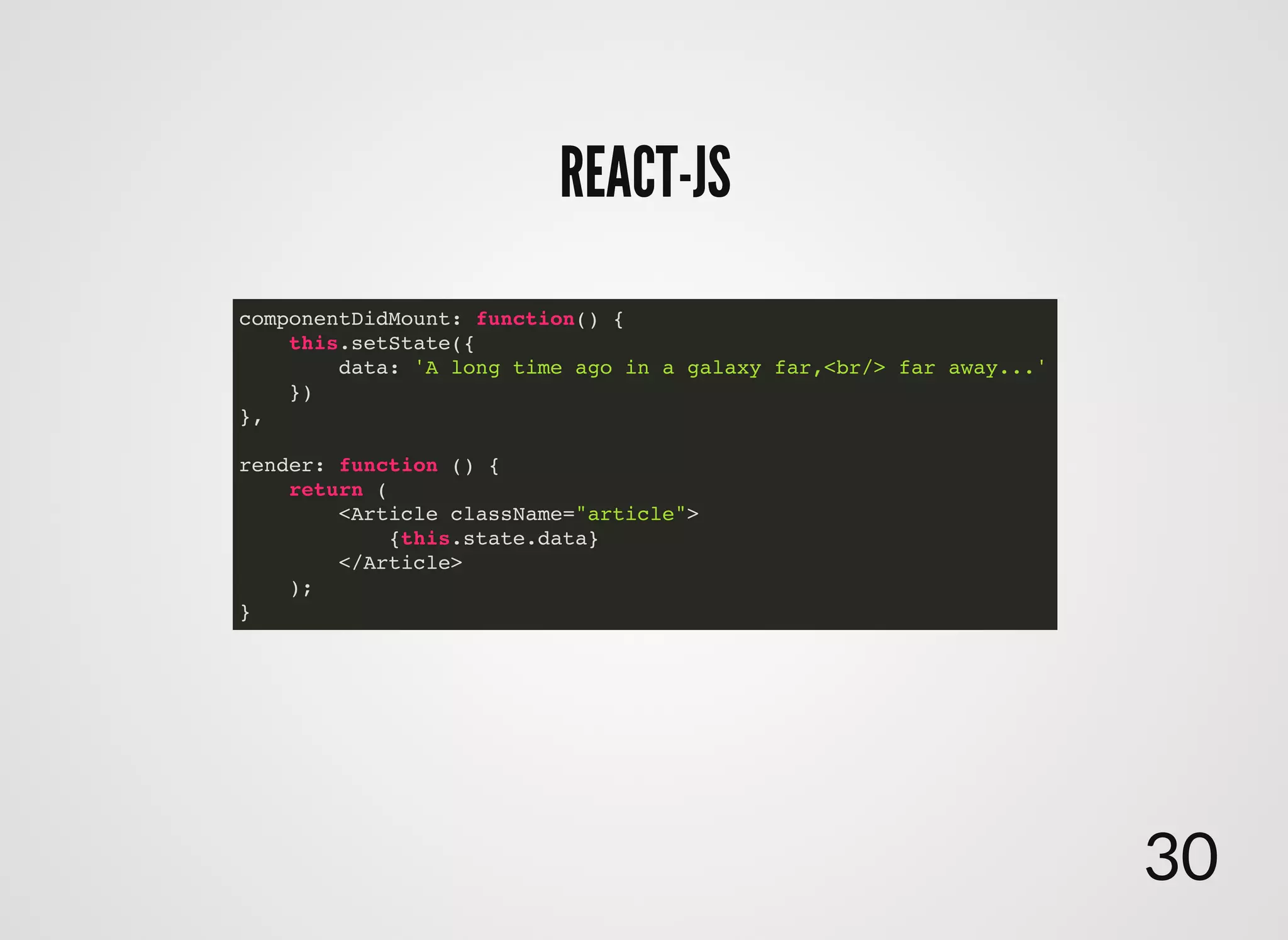
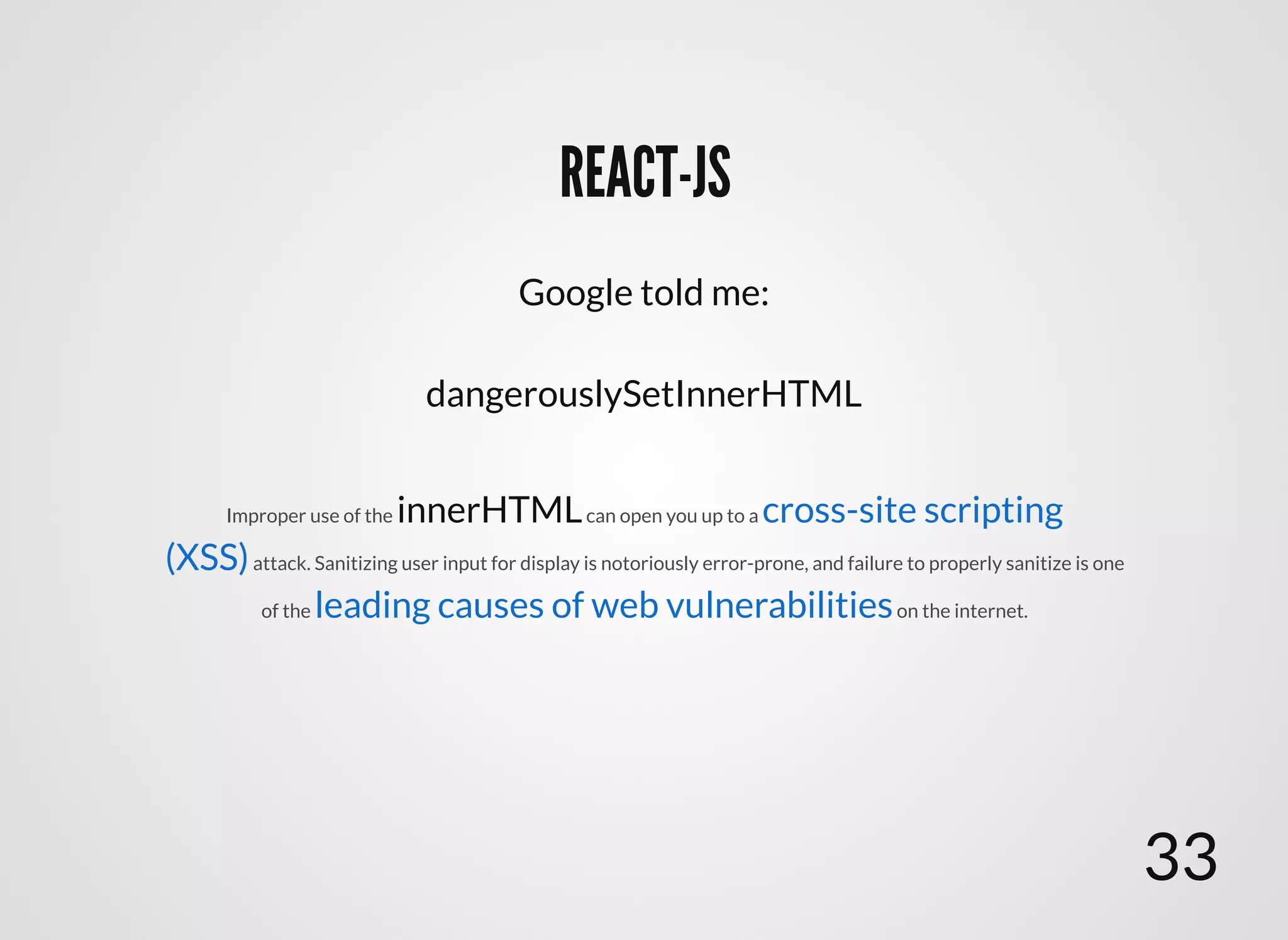
The document discusses approaches to writing secure frontend code in the context of ReactJS. It begins by outlining common client-side vulnerabilities like XSS, including reflected, stored, and DOM-based XSS. It then discusses how to prevent vulnerabilities in ReactJS by escaping HTML, attributes, JS data, and JSON data. It also recommends using a whitelist of allowed attributes rather than a blacklist of forbidden ones. Finally, it outlines some simple rules for ReactJS like using safe user input by default, only unsafe input for special forms, allowing only known attributes, and not allowing inline attribute data.















![DETECT KEYWORDSDETECT KEYWORDS
var forbidden = [
'onerror',
'onmouseover',
'onclick'
];
if (attribute in forbidden) {
return false;
}
What about onblur, onchange, onselect, etc. ?
Black Lists
27](https://image.slidesharecdn.com/43534ac8-3d66-4952-9055-4ae21f574b31-161116210957/75/mjs-28-2048.jpg)
![var allowed = [
'title',
'class',
'hidden',
....
];
if (attribute in allowed) {
add(attribute);
}
BE ON A WHITE SIDEBE ON A WHITE SIDE
28](https://image.slidesharecdn.com/43534ac8-3d66-4952-9055-4ae21f574b31-161116210957/75/mjs-29-2048.jpg)









![REACT-JS ATTRIBUTESREACT-JS ATTRIBUTES
var HTMLDOMPropertyConfig = {
isCustomAttribute: RegExp.prototype.test.bind(
/^(data|aria)-[a-z_][a-zd_.-]*$/
),
Properties: {
/**
* Standard Properties
*/
accept: null,
acceptCharset: null,
accessKey: null,
action: null,
allowFullScreen: MUST_USE_ATTRIBUTE | HAS_BOOLEAN_VALUE,
allowTransparency: MUST_USE_ATTRIBUTE,
alt: null,
async: HAS_BOOLEAN_VALUE,
autoComplete: null,
// autoFocus is polyfilled/normalized by AutoFocusMixin
// autoFocus: HAS_BOOLEAN_VALUE,
autoPlay: HAS_BOOLEAN_VALUE,
cellPadding: null,
cellSpacing: null,
charSet: MUST_USE_ATTRIBUTE,
checked: MUST_USE_PROPERTY | HAS_BOOLEAN_VALUE,
classID: MUST_USE_ATTRIBUTE,
40](https://image.slidesharecdn.com/43534ac8-3d66-4952-9055-4ae21f574b31-161116210957/75/mjs-41-2048.jpg)