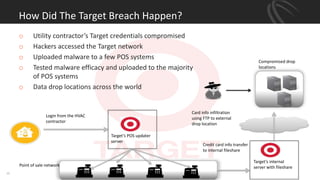
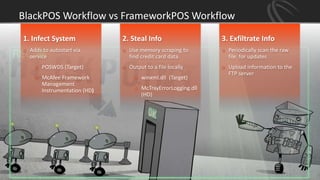
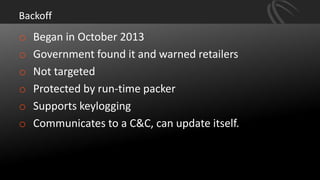
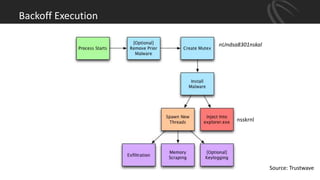
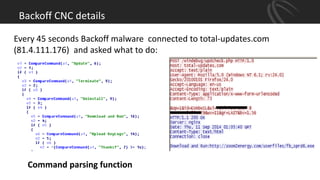
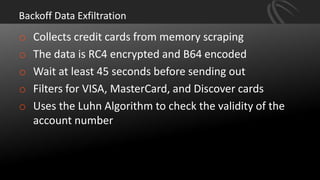
The document discusses recent point-of-sale (POS) malware breaches, specifically focusing on BlackPOS and FrameworkPOS, detailing their operation and the significant financial impacts they had, such as the Target breach of 2013 which resulted in the theft of 40 million credit card records. It also covers the evolution of POS malware, its detection, and mitigation strategies for retailers to protect against such threats. Key recommendations include rigorous risk assessments, network separation, and ongoing updates to security protocols.