The document discusses bug hunting in the Linux kernel, emphasizing its complexity with millions of lines of code and frequent updates. It covers various debugging techniques, tools, and the use of eBPF for performance monitoring and tracing. The conclusion highlights the benefits of virtualization and tracing in kernel development, encouraging a fun approach to understanding and improving the kernel.
![LINUX KERNEL IS COMPLEXLINUX KERNEL IS COMPLEX
26,947,416 lines of code right now
438 patches last week
813 files changed, 7714 insertions(+), 31289
deletions(-)
find -type f -name '*.[chS]' -exec wc -l {} ; |
awk 'BEGIN{sum=0}{sum+=$1}END{print sum}'
git log --oneline v5.10-rc1..v5.10-rc2 | wc -l
git diff --stat v5.10-rc1..v5.10-rc2 | tail -1](https://image.slidesharecdn.com/kernel-bug-hunting-201117171443/85/Linux-kernel-bug-hunting-2-320.jpg)





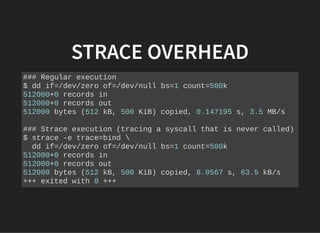





![KEYLOGGER WITH BPFTRACE:KEYLOGGER WITH BPFTRACE:
COMMANDSCOMMANDS
sudo bpftrace -e 'kprobe:*interrupt* { @[probe] = count() }'
sudo bpftrace -e 'kprobe:atkbd_interrupt
{ printf("%xn", arg1) }'](https://image.slidesharecdn.com/kernel-bug-hunting-201117171443/85/Linux-kernel-bug-hunting-19-320.jpg)

![TRACING 'PING' WITH BPFTRACE:TRACING 'PING' WITH BPFTRACE:
COMMANDSCOMMANDS
sudo bpftrace -e 'kprobe:*icmp* { @[probe] = count(); }'
sudo bpftrace -e 'kprobe:icmp_out_count
{ printf("%s: type=%d%sn", probe, arg1, kstack); }'](https://image.slidesharecdn.com/kernel-bug-hunting-201117171443/85/Linux-kernel-bug-hunting-21-320.jpg)
![TRACING TASK WAIT / WAKUPTRACING TASK WAIT / WAKUP
EVENTS WITH BPFTRACEEVENTS WITH BPFTRACE
#!/usr/bin/env bpftrace
#include <linux/sched.h>
BEGIN
{
printf("Tracing off-CPU time (us) with waker stacks. Ctrl-C
}
kprobe:try_to_wake_up
{
$p = (struct task_struct *)arg0;
@waker[$p->pid] = kstack;
}](https://image.slidesharecdn.com/kernel-bug-hunting-201117171443/85/Linux-kernel-bug-hunting-22-320.jpg)


