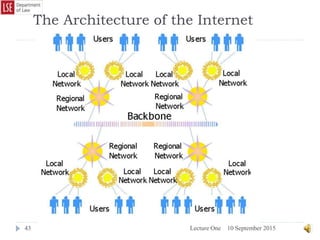
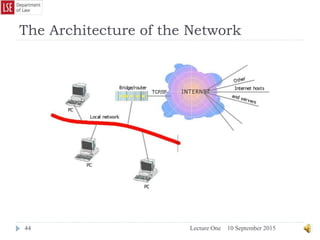
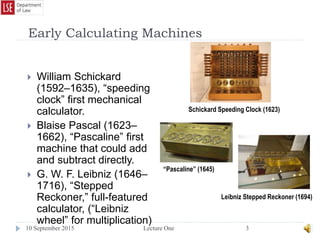
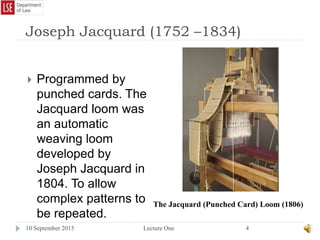
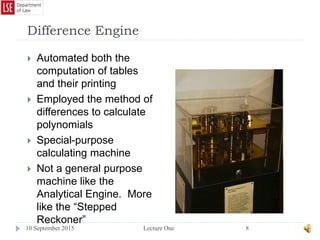
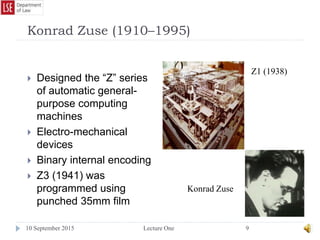
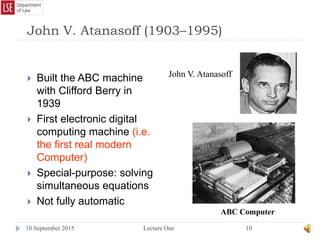
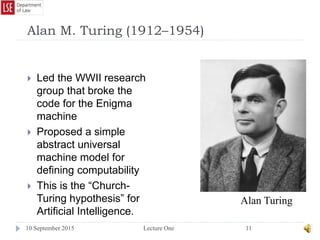
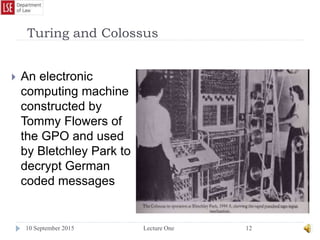
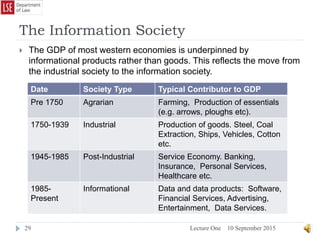
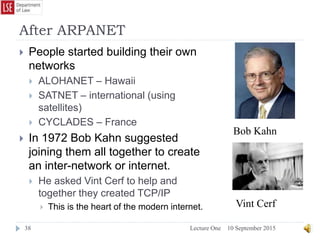
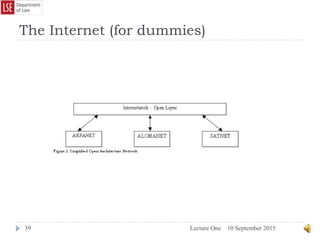
The document provides a history of the development of digital computers and the internet. It discusses early calculating machines developed in the 17th-18th centuries by figures like Pascal and Leibniz. In the 19th-20th centuries, important developments included Babbage's Analytical Engine concept, Zuse's mechanical computers, and the electronic computers developed by Atanasoff, Turing, and von Neumann. The internet evolved from ARPANET in the 1960s and packet switching/TCP/IP protocols allowed different networks to connect as the internet in the 1970s-1980s. Today billions of devices are connected through vast global networks that underpin the information society.

















![Alastair and Barbara
10 September 2015Lecture One42
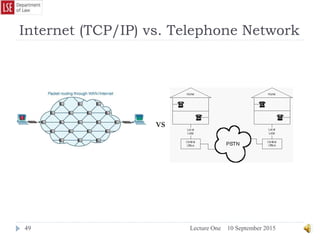
The easiest way to imagine this working is to think of traditional postal
communications.
If Alistair wants to send a message to Barbara he will write his message on a
piece of paper and then place in inside an envelope before sealing the
envelope and addressing it. He then places the envelope in the care of the
Royal Mail who carry the envelope to Barbara. She then opens the envelope
and reads the message.
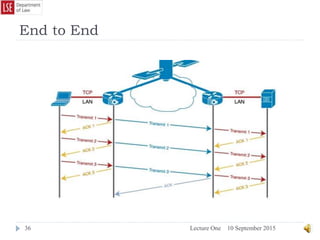
TCP/IP works in a similar fashion, except in place of a single envelope the
message is split into “packets” before being sent.
Thus if we were to use TCP/IP technology to send the simple message
“Meet me at 2pm” from Alistair to Barbara, the following operations would
take place.
Firstly TCP would split the message into packets and numbers each packet [Meet]1
[me at]2 [2pm]3. Then it places each packet into a digital envelope before passing
these envelopes on to the IP protocol. IP would then address the envelopes before
sending them out across the network.
The network acts like the Royal Mail and carries these envelopes to their
destination. Upon arrival TCP opens the envelopes, checks all packets have been
delivered safely and reassembles the message.
This digital envelope is valuable as it allows the system to carry a variety of digital
products such as sounds, images, text or raw data without having to differentiate
between them in the same way the Royal Mail will carry photographs, letters,
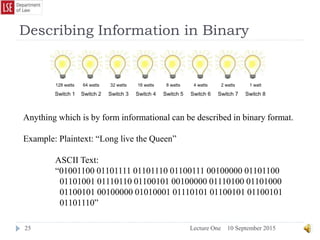
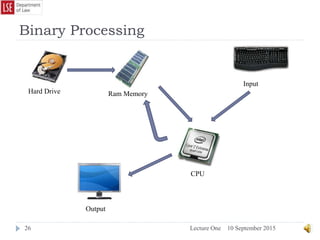
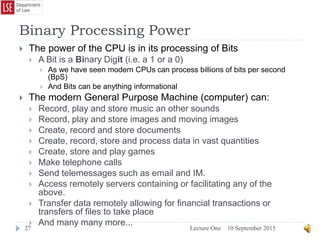
magazines or computer games on CD without needing to know what is inside the
envelope. This, in digital terms is known as Net Neutrality and is discussed in
greater depth below.](https://image.slidesharecdn.com/lectureonehistoryofcomputing-150910140256-lva1-app6891/85/Lecture-one-history-of-computing-42-320.jpg)