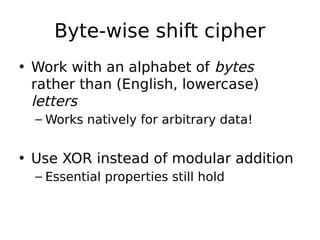
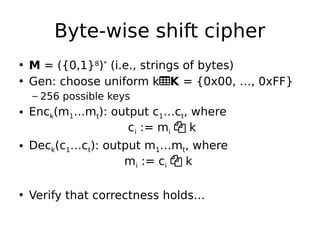
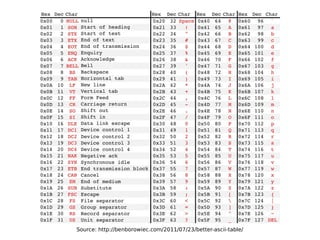
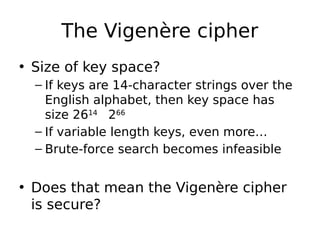
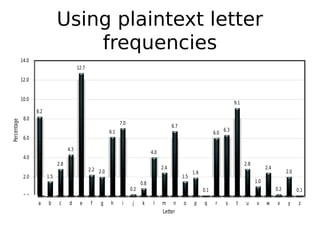
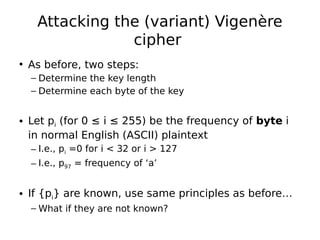
This document describes a byte-wise shift cipher and Vigenère cipher. It discusses attacks that can be used to decrypt ciphertexts encrypted with these ciphers without knowing the key. For the byte-wise shift cipher, it is noted that the key space is too small at 256 keys to be secure. For the Vigenère cipher, frequency analysis of letters in different positions of the ciphertext can be used to determine the key length and individual bytes of the key. The same techniques can be applied to a byte-wise variant of the Vigenère cipher by analyzing frequencies of bytes in different ciphertext streams.