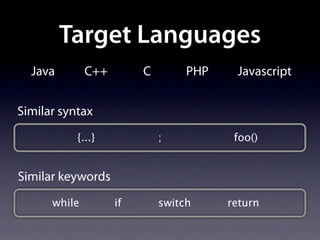
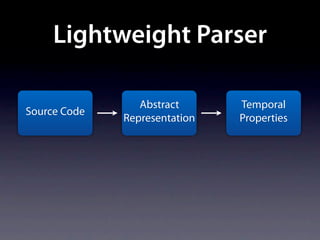
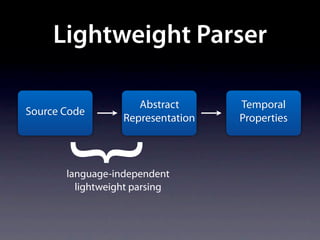
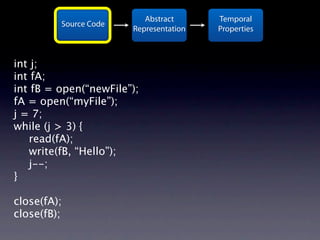
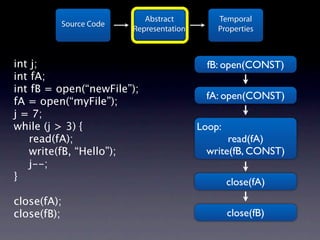
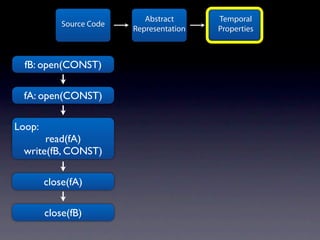
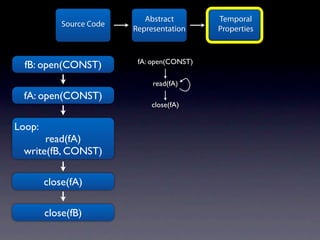
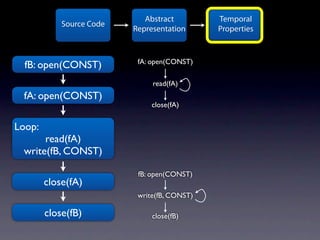
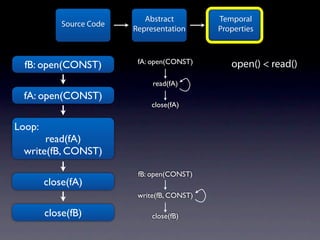
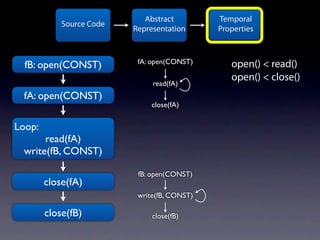
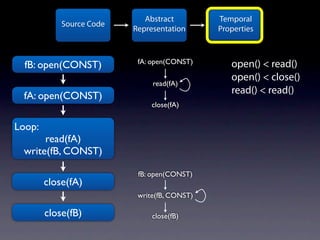
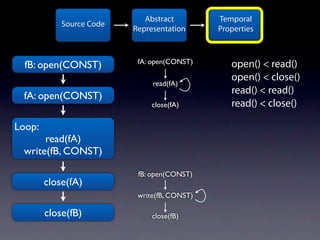
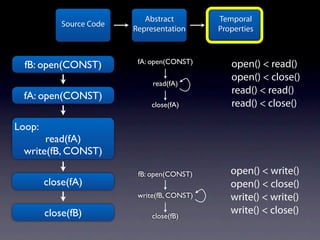
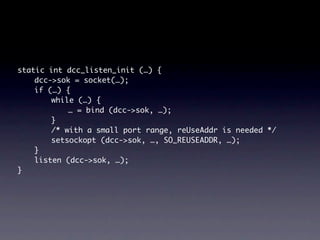
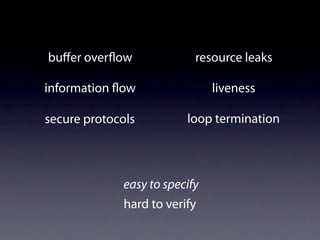
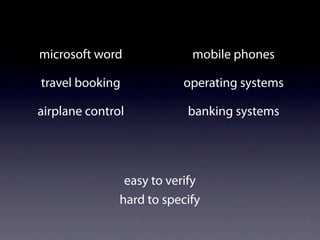
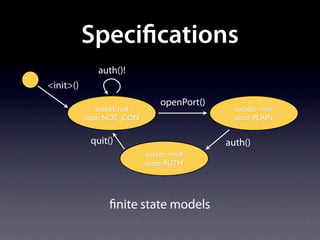
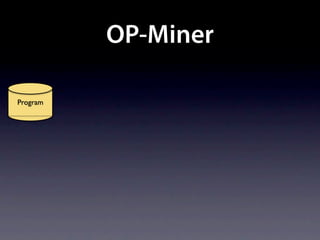
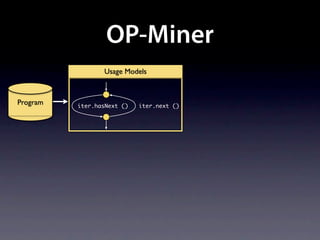
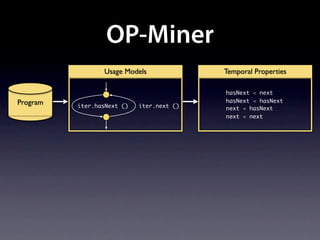
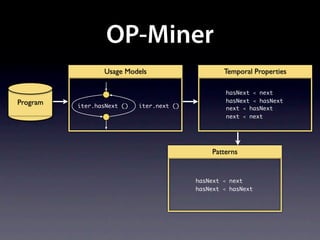
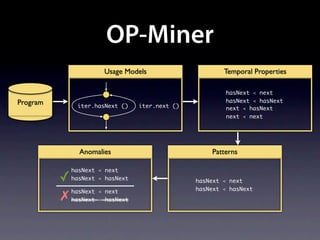
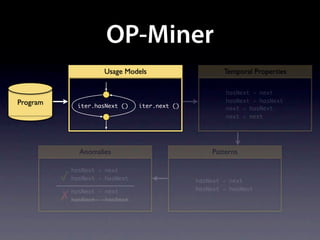
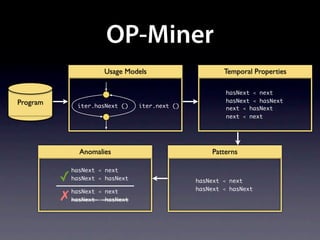
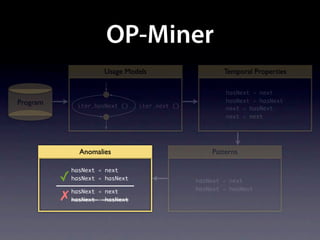
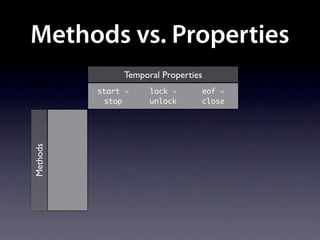
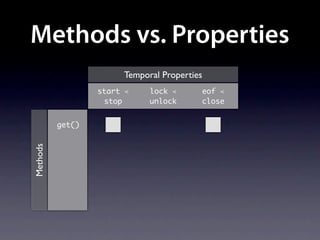
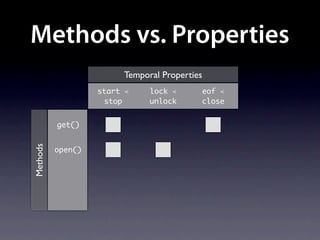
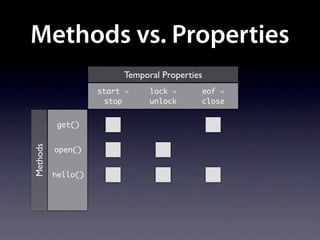
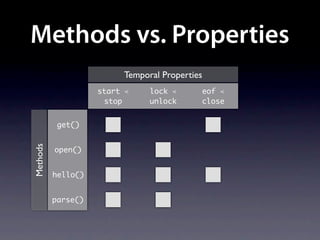
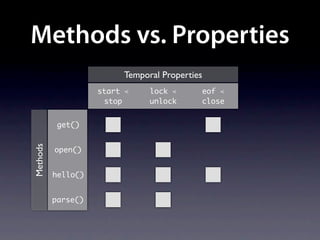
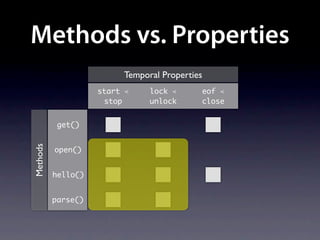
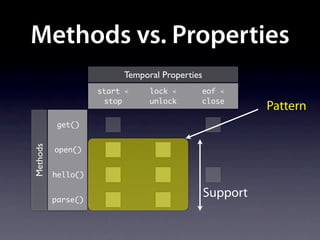
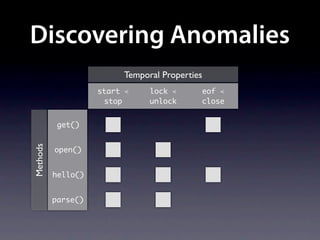
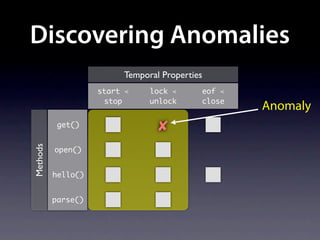
The document presents data from a study involving 6,000 software projects at Saarland University, focusing on the challenges of formal specifications in programming and the properties of various programming languages. It highlights the significant number of PhD advisors and students involved, alongside details about graduates, stipends, and the complexity of verifying secure protocols. The findings also cover the use of temporal properties and the prevalence of defects or code smells in software development.






















![∀i ∈ {0, . . . , |x |} : x [i] < x [i + 1]
|x| = |x |
∀i ∈ {0, . . . , |x|} : ιi ∈ {0, . . . , |x |} : x[i] = x [i ]
∀i ∈ {0, . . . , |x |} : ιi ∈ {0, . . . , |x|} : x [i ] = x[i]
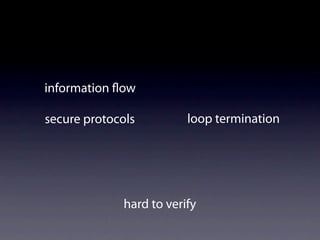
hard to specify](https://image.slidesharecdn.com/learningfrom6000projects-miningspecificationsinthelarge-100913034806-phpapp02/85/Learning-from-6-000-projects-mining-specifications-in-the-large-32-320.jpg)
![∀i ∈ {0, . . . , |x |} : x [i] < x [i + 1]
|x| = |x |
∀i ∈ {0, . . . , |x|} : ιi ∈ {0, . . . , |x |} : x[i] = x [i ]
∀i ∈ {0, . . . , |x |} : ιi ∈ {0, . . . , |x|} : x [i ] = x[i]
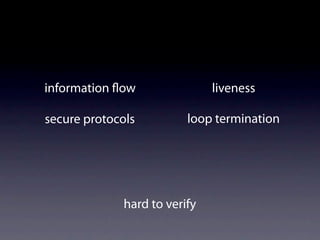
easy to verify
hard to specify](https://image.slidesharecdn.com/learningfrom6000projects-miningspecificationsinthelarge-100913034806-phpapp02/85/Learning-from-6-000-projects-mining-specifications-in-the-large-33-320.jpg)















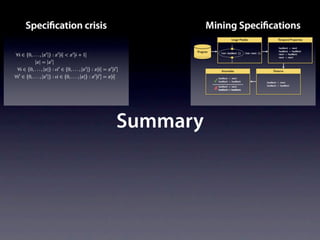
![Speci cations
∀i ∈ {0, . . . , |x |} : x [i] < x [i + 1]
|x| = |x |
∀i ∈ {0, . . . , |x|} : ιi ∈ {0, . . . , |x |} : x[i] = x [i ]
∀i ∈ {0, . . . , |x |} : ιi ∈ {0, . . . , |x|} : x [i ] = x[i]
pre- and postconditions](https://image.slidesharecdn.com/learningfrom6000projects-miningspecificationsinthelarge-100913034806-phpapp02/85/Learning-from-6-000-projects-mining-specifications-in-the-large-50-320.jpg)


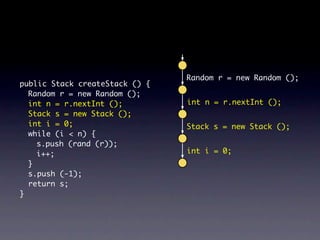
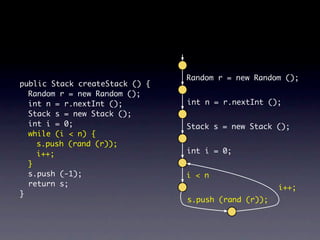
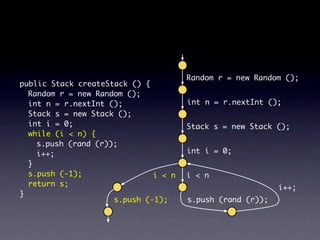
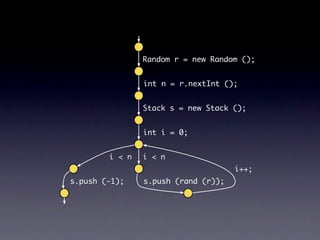
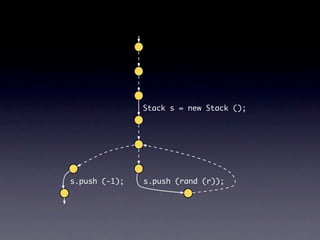
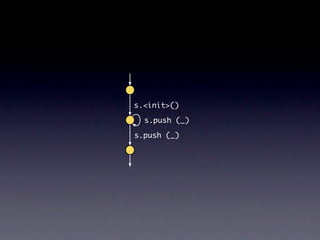
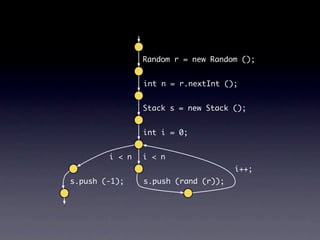
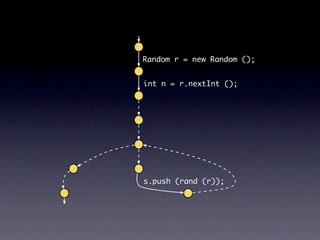
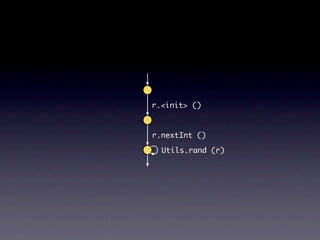
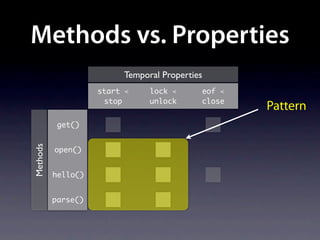





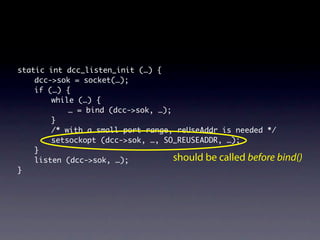
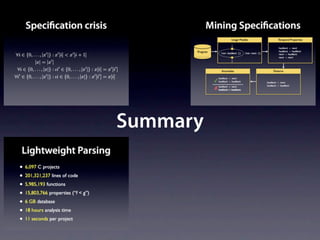
![Name internalNewName (String[] identifiers)
...
for (int i = 1; i < count; i++) {
SimpleName name = new SimpleName(this);
name.internalSetIdentifier(identifiers[i]);
...
}
...
}](https://image.slidesharecdn.com/learningfrom6000projects-miningspecificationsinthelarge-100913034806-phpapp02/85/Learning-from-6-000-projects-mining-specifications-in-the-large-91-320.jpg)
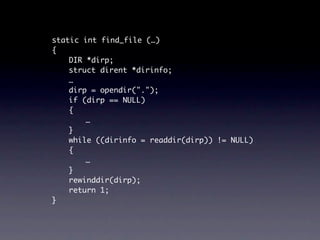
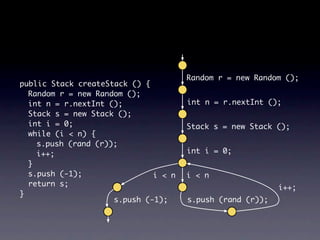
![Name internalNewName (String[] identifiers)
...
for (int i = 1; i < count; i++) {
SimpleName name = new SimpleName(this);
name.internalSetIdentifier(identifiers[i]);
...
} should stay as is
...
}](https://image.slidesharecdn.com/learningfrom6000projects-miningspecificationsinthelarge-100913034806-phpapp02/85/Learning-from-6-000-projects-mining-specifications-in-the-large-92-320.jpg)