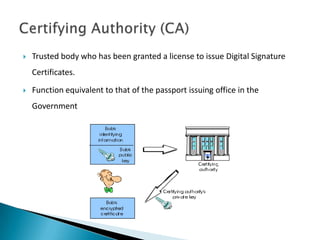
The document outlines the objectives and framework of the Information Technology Act in India, which aims to provide legal recognition of electronic records and facilitate e-governance. It details the functions of the Act, including authentication of electronic records and addressing cyber crimes, while also reviewing legal repercussions for various offenses. Additionally, it highlights the role of regulatory bodies and evolving trends in e-business transactions, emphasizing the need for a secure digital environment.