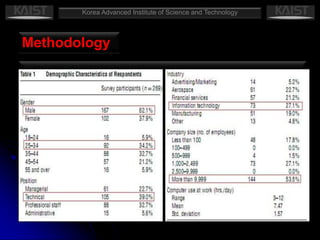
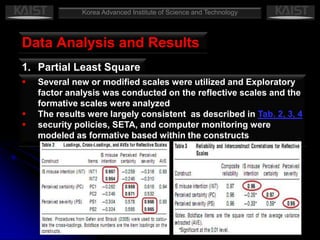
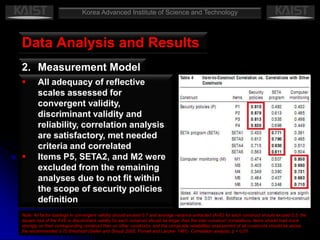
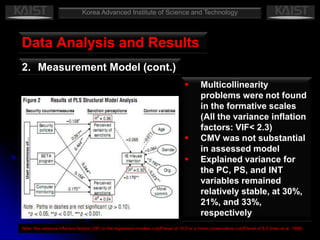
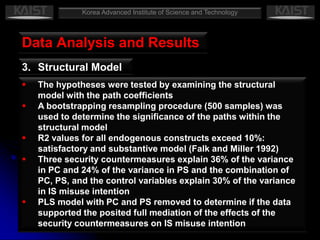
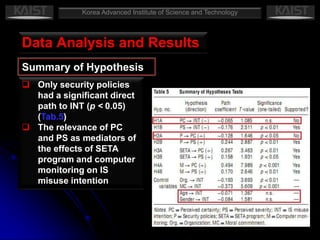
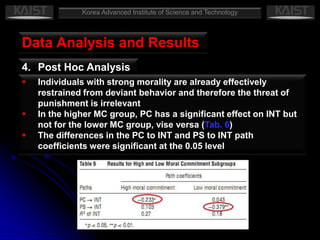
This document summarizes a research paper that empirically tests a model based on general deterrence theory regarding how user awareness of security countermeasures impacts perceptions of punishment certainty and severity for information systems misuse. The study developed hypotheses about the relationships between security policies, security education/training/awareness programs, computer monitoring, perceived certainty and severity of sanctions, and intentions for systems misuse. Data was collected through an online survey of professionals and analyzed using partial least squares and other statistical techniques. The results provided support for most of the hypotheses and showed that security countermeasures influence perceptions of punishment, which impact misuse intentions.