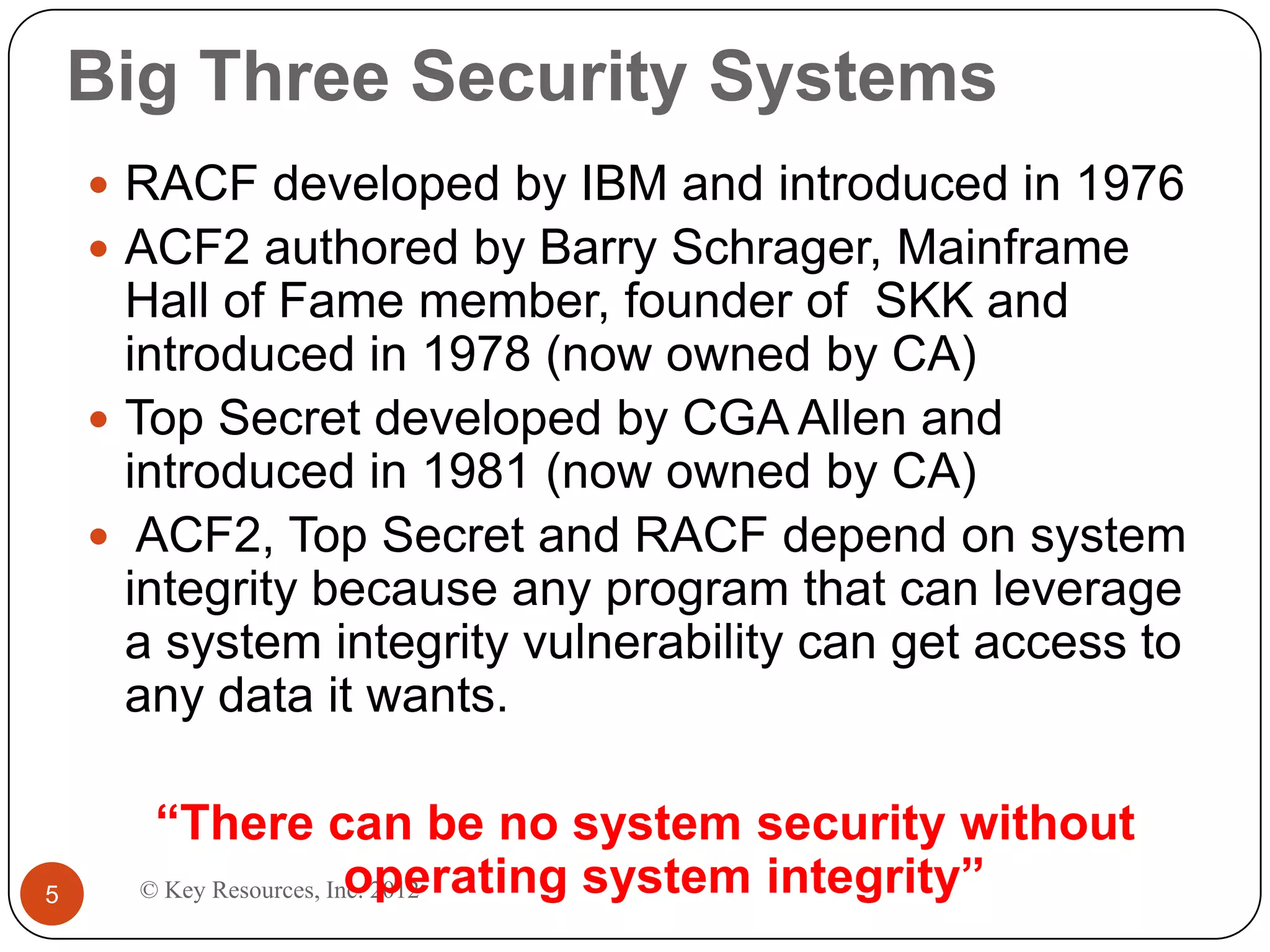
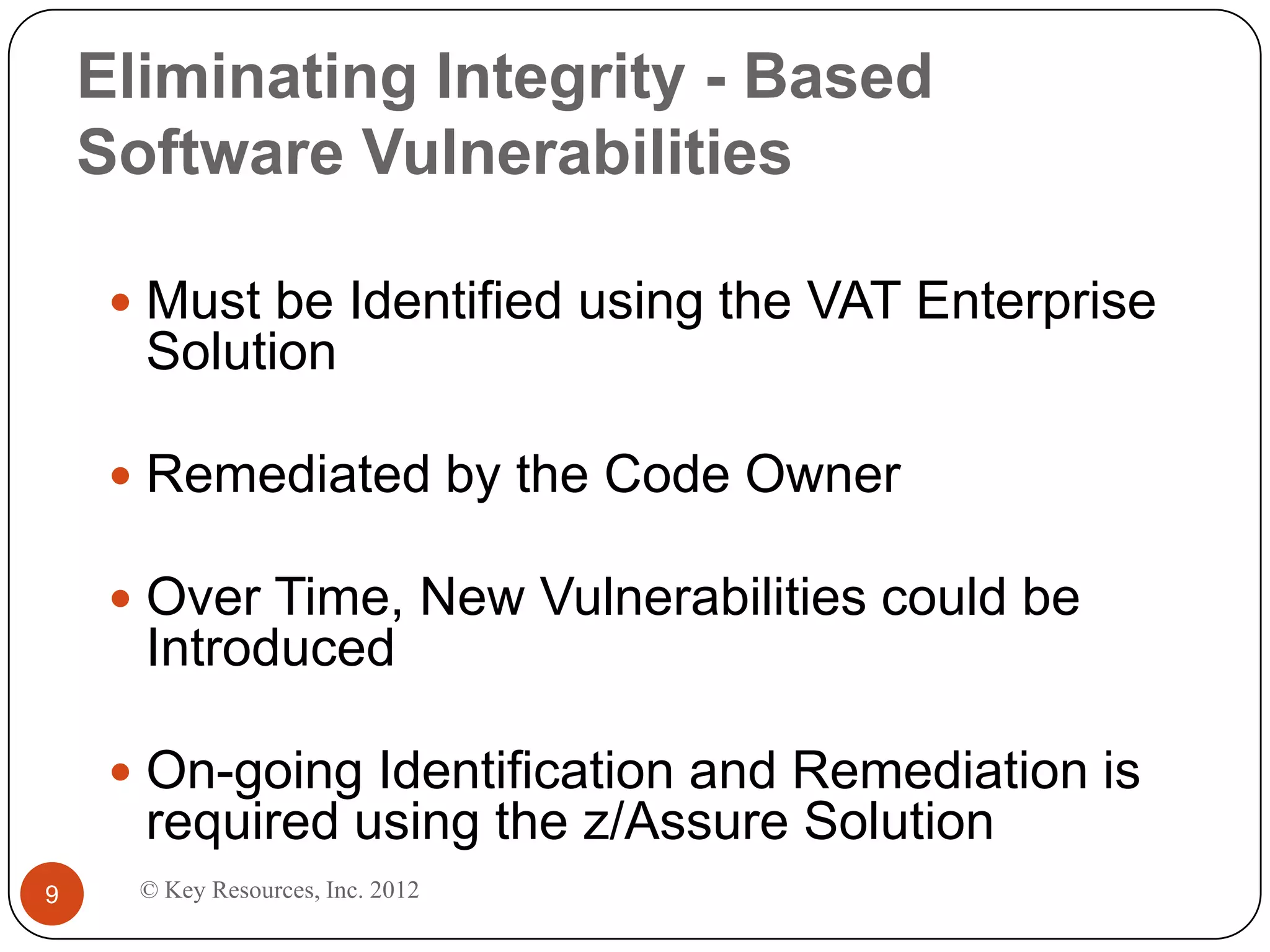
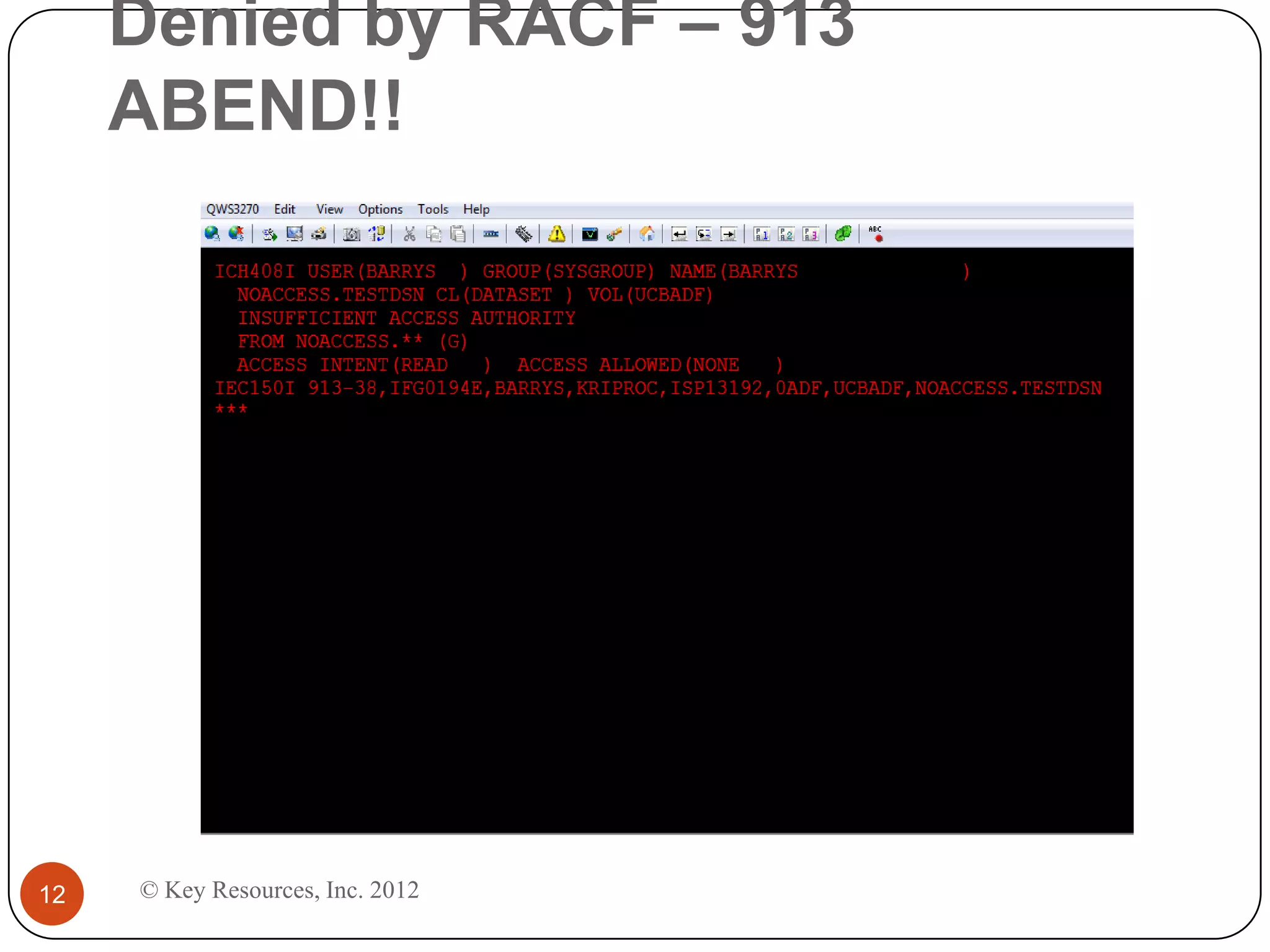
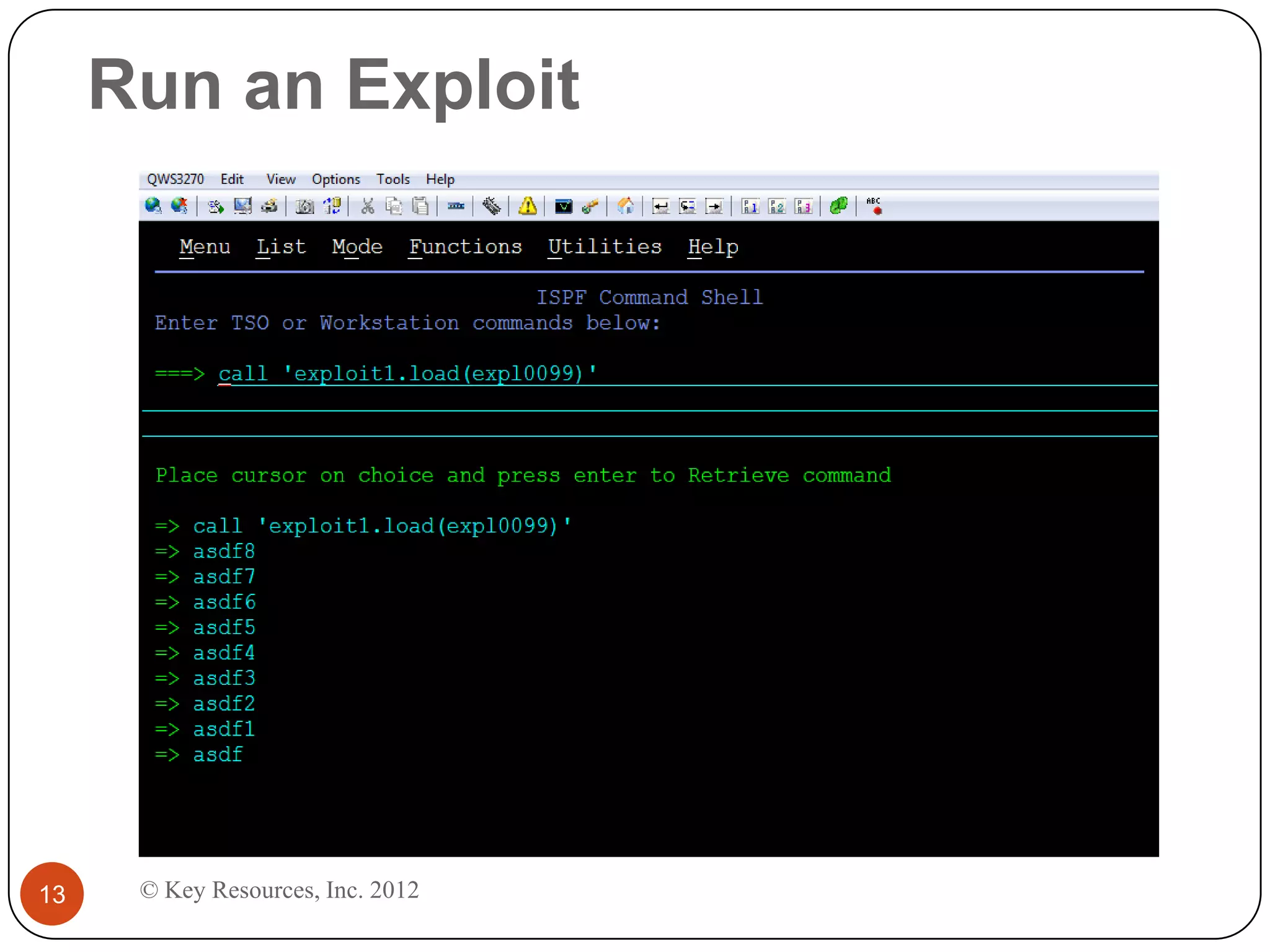
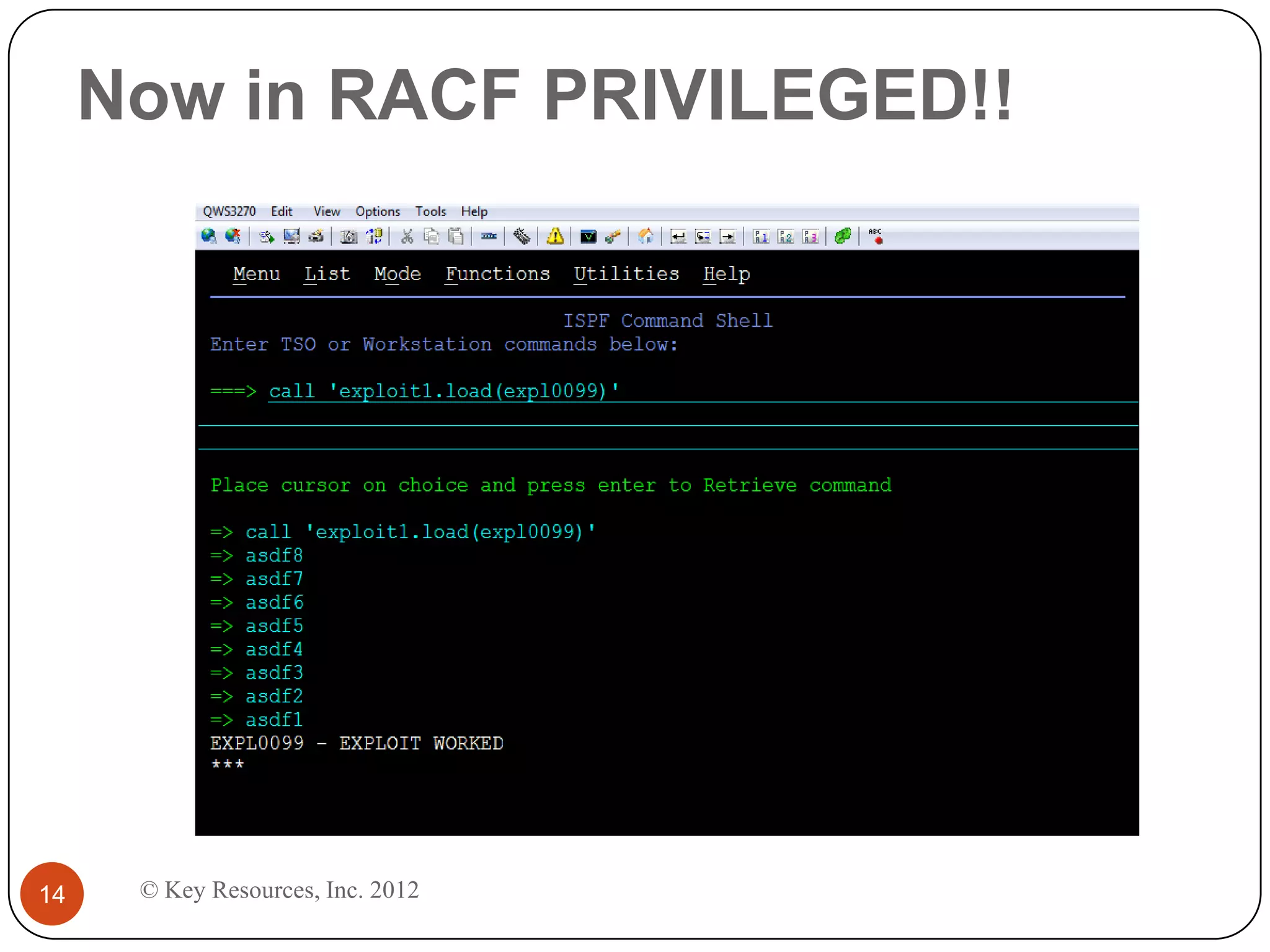
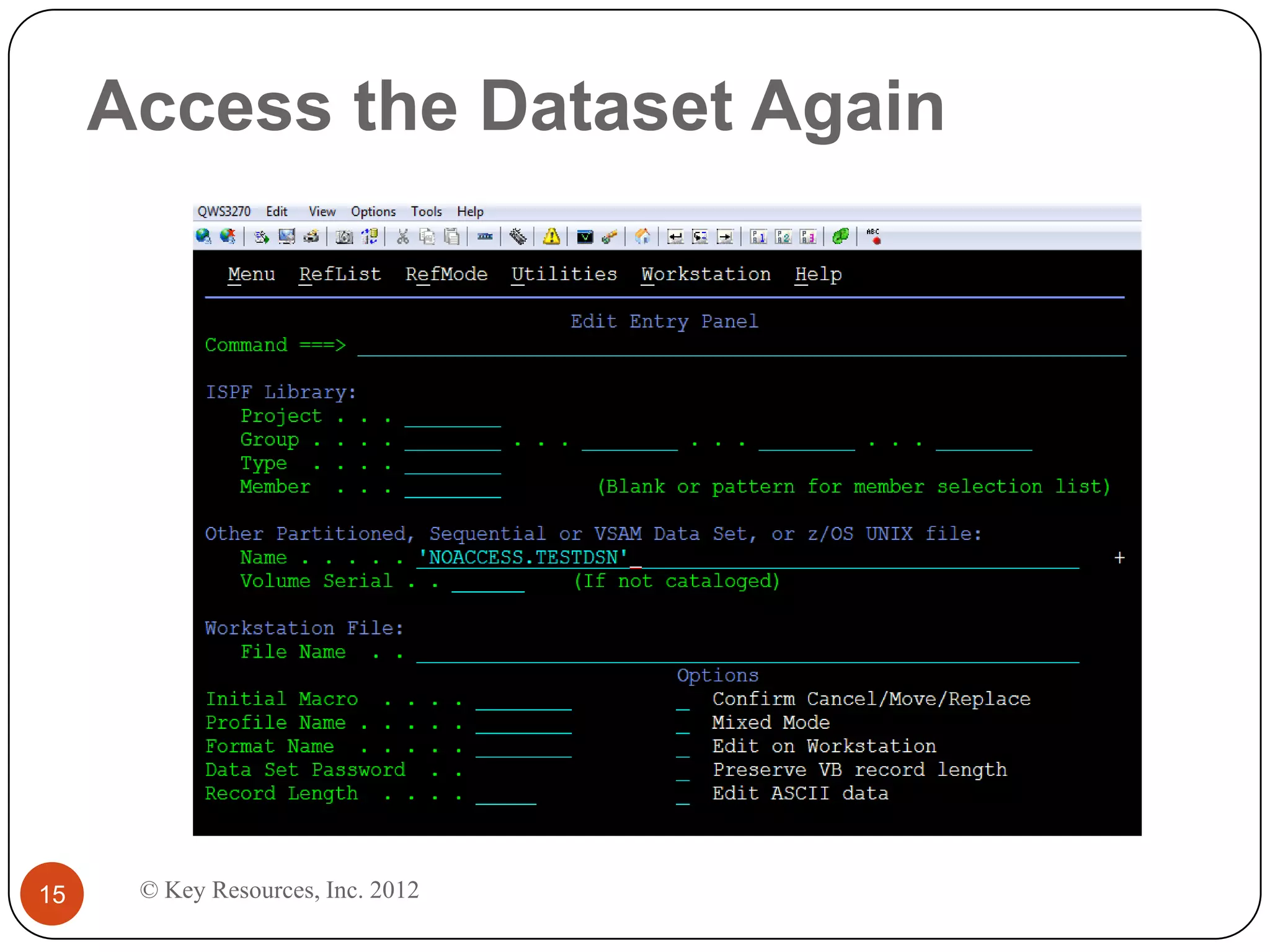
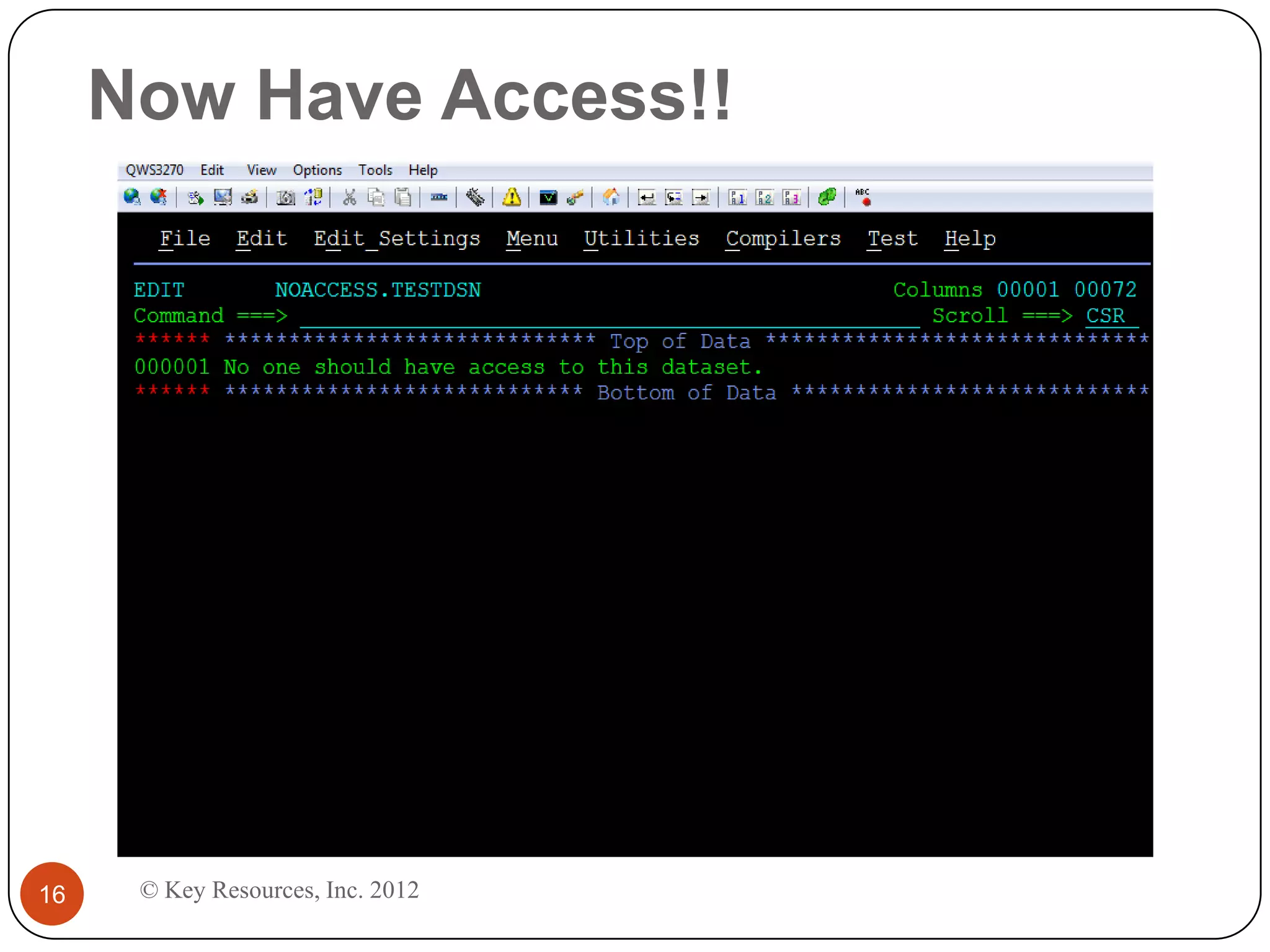
This document describes z/Assure, an IBM z/OS vulnerability analysis solution created by security developers. It performs penetration tests on z/OS systems and applications to identify integrity-based software vulnerabilities. These vulnerabilities can allow attackers to bypass security controls and access sensitive data without authorization. While security systems like RACF aim to prevent this, vulnerabilities in IBM and third-party software leave systems at risk. z/Assure can help organizations identify these vulnerabilities and ensure NIST, PCI, and SOX compliance. Customers can choose to conduct an initial assessment or deploy z/Assure enterprise-wide for ongoing monitoring and remediation of vulnerabilities over time.