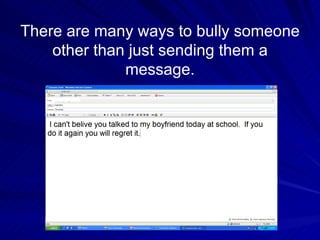
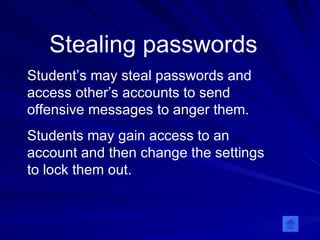
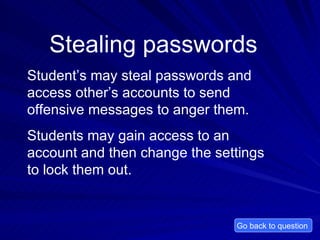
Cyberbullying involves negative virtual communication such as threatening messages, stealing passwords, impersonation, and spreading photos online. Common forms of cyberbullying include instant messaging, blogs, websites, email, and social media. To prevent cyberbullying, understand that teasing and threats are bullying, and tell parents or teachers if it happens. Parents should inform the school of any cyberbullying and consider counseling.