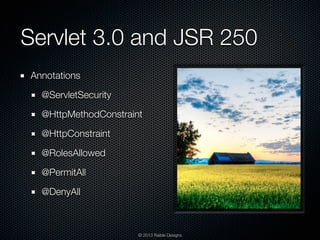
The document is a presentation by Matt Raible focused on Java web application security, outlining goals for enhancing security knowledge and skills. It covers topics such as Java EE 6, Spring Security, Apache Shiro, and penetration testing methods, along with best practices for securing web applications. Additionally, it references the OWASP Top 10 security vulnerabilities and provides resources for further learning and implementation of security measures.











![Securing Methods
<global-method-security secured-annotations="enabled"/>
@Secured("IS_AUTHENTICATED_ANONYMOUSLY")
public Account readAccount(Long id);
@Secured("IS_AUTHENTICATED_ANONYMOUSLY")
public Account[] findAccounts();
@Secured("ROLE_TELLER")
public Account post(Account account, double amount);
<global-method-security jsr250-annotations="enabled"/>
© 2013 Raible Designs](https://image.slidesharecdn.com/javawebapplicationsecurity-denverjug2013-130213181636-phpapp02/85/Java-Web-Application-Security-Denver-JUG-2013-15-320.jpg)
![Securing Methods 3.x
<global-method-security pre-post-annotations="enabled"/>
@PreAuthorize("isAnonymous()")
public Account readAccount(Long id);
@PreAuthorize("isAnonymous()")
public Account[] findAccounts();
@PreAuthorize("hasAuthority('ROLE_TELLER')")
public Account post(Account account, double amount);
© 2013 Raible Designs](https://image.slidesharecdn.com/javawebapplicationsecurity-denverjug2013-130213181636-phpapp02/85/Java-Web-Application-Security-Denver-JUG-2013-16-320.jpg)

![Apache Shiro
Filter defined in web.xml
shiro.ini loaded from classpath
[main], [urls], [roles]
Cryptography
Session Management
© 2013 Raible Designs](https://image.slidesharecdn.com/javawebapplicationsecurity-denverjug2013-130213181636-phpapp02/85/Java-Web-Application-Security-Denver-JUG-2013-18-320.jpg)



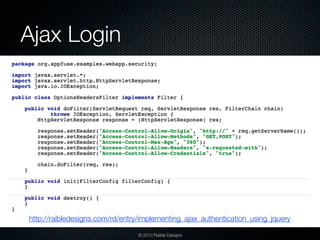

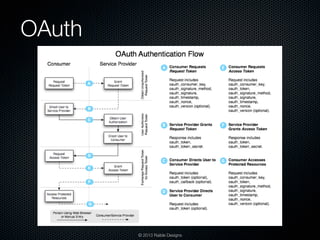








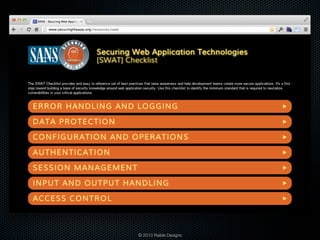
![Protect
[SWAT] Checklist
Firewalls
IDS and IDPs
Audits
Penetration Tests
Code Reviews with Static
Analysis Tools
© 2013 Raible Designs](https://image.slidesharecdn.com/javawebapplicationsecurity-denverjug2013-130213181636-phpapp02/85/Java-Web-Application-Security-Denver-JUG-2013-37-320.jpg)