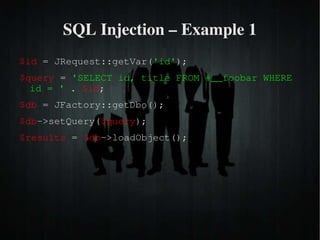
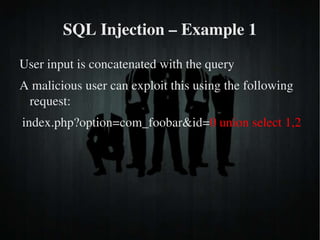
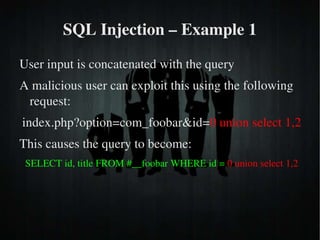
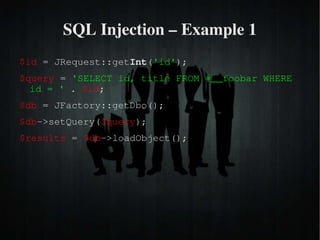
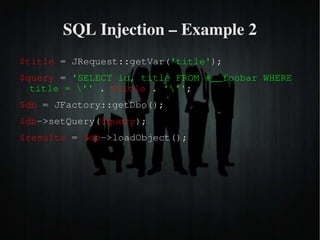
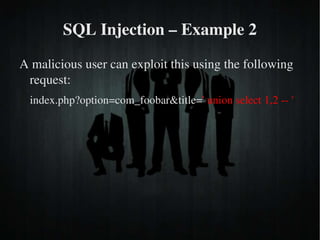
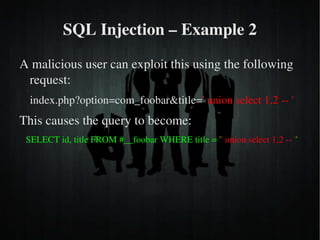
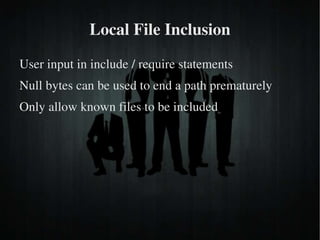
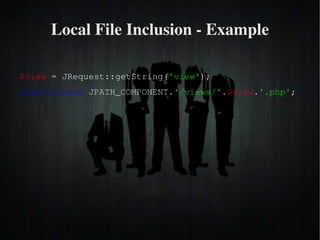
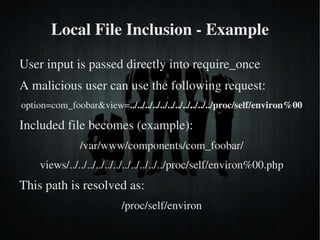
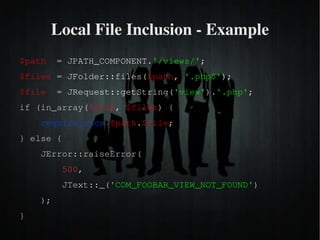
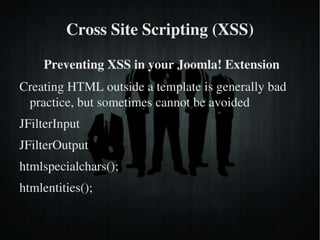
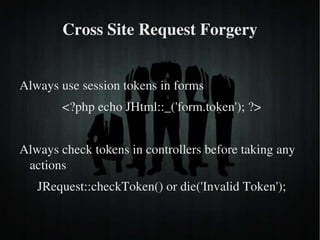
The document discusses secure PHP coding practices and emphasizes the importance of mitigating vulnerabilities that could lead to reputation loss, financial damages, or data disclosure. It highlights common vulnerabilities such as SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF), providing examples of exploitation techniques and prevention strategies. Key recommendations include escaping user input, using session tokens, and implementing strict input validation to enhance security in web applications.