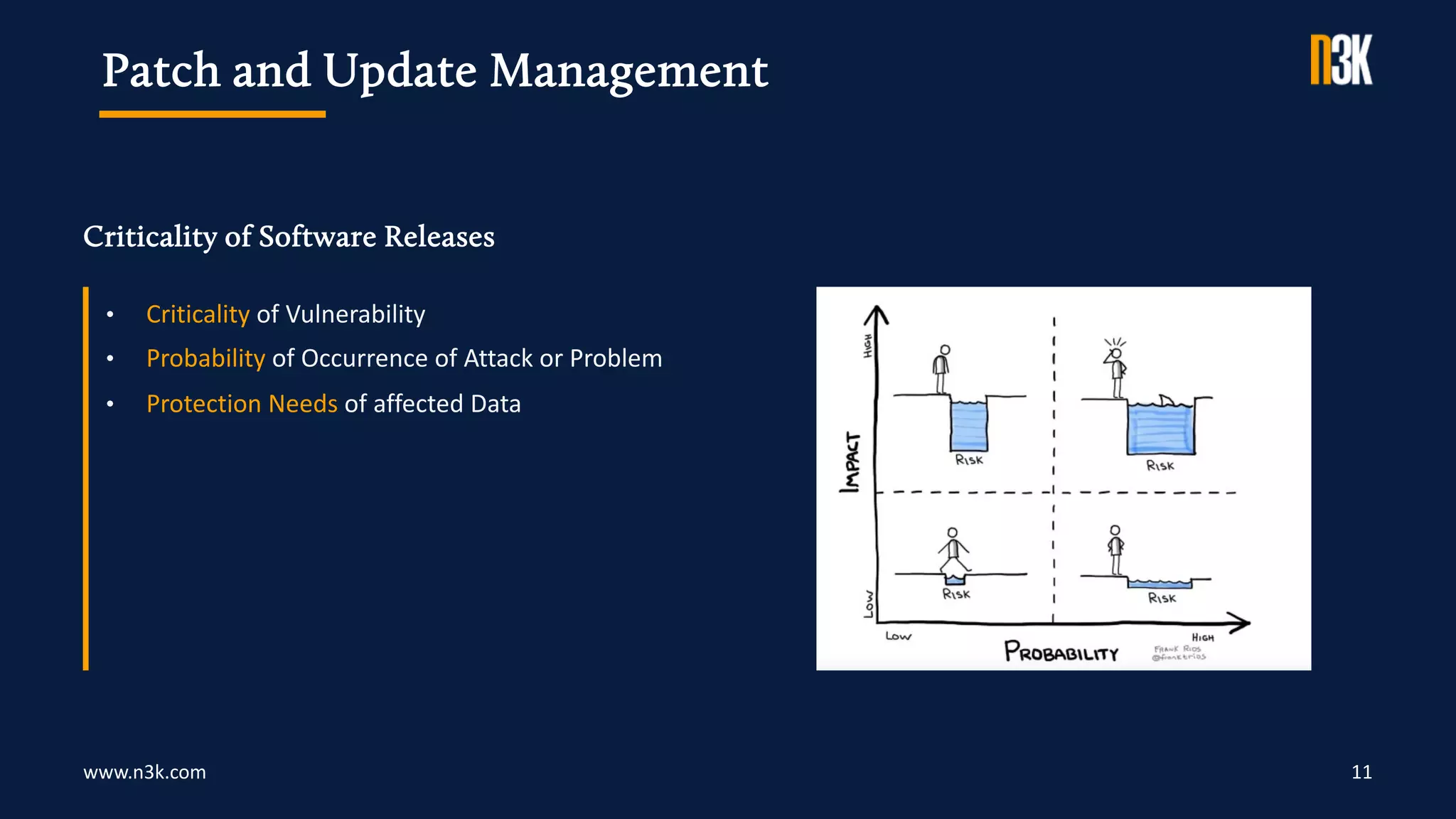
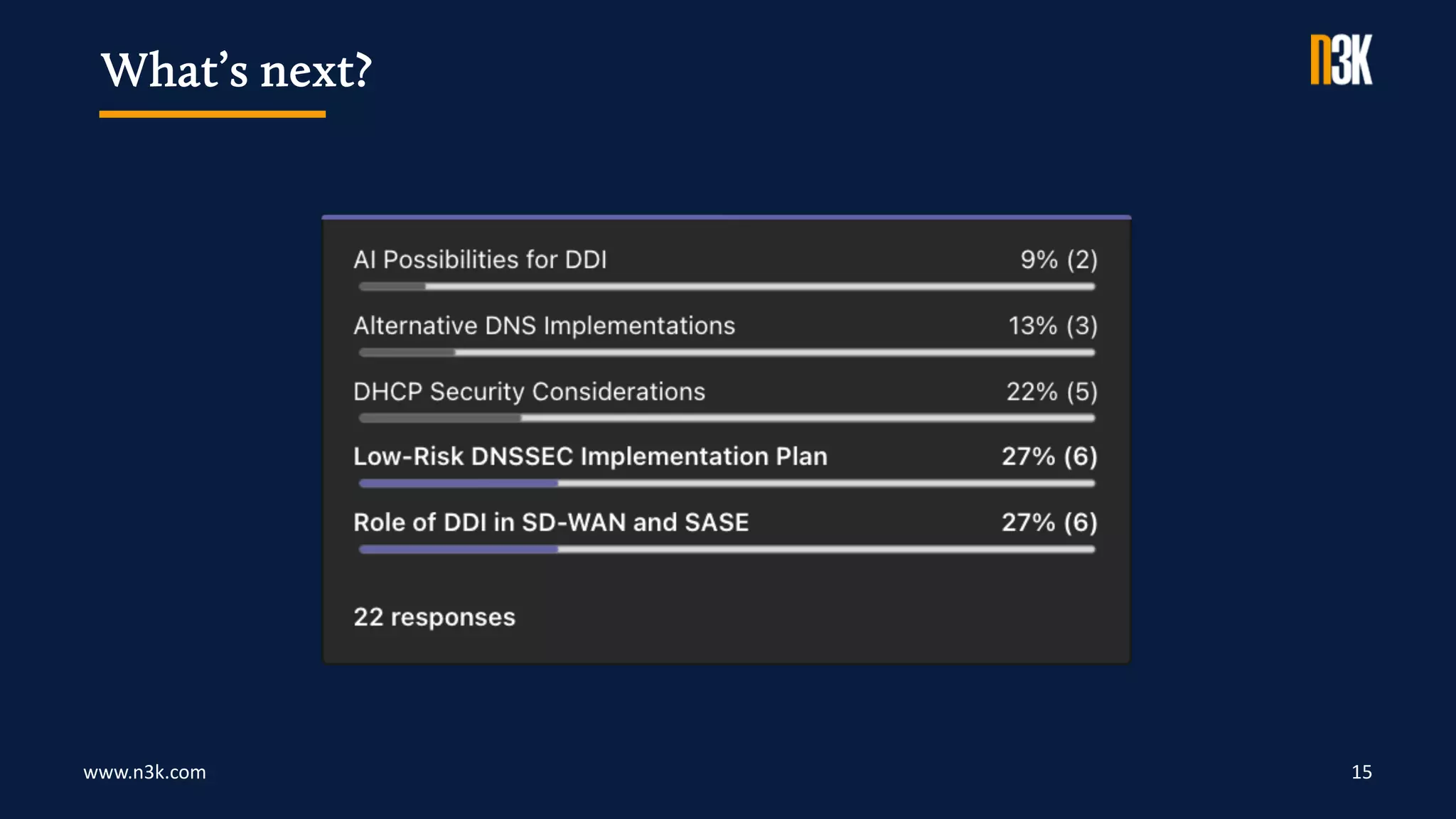
The document outlines security considerations for IP Address Management (IPAM) discussed in a webinar, emphasizing the importance of encrypted access, role-based account management, and the use of external authentication systems. It covers user classes, access rights, password management practices, and a structured approach to software updates and maintenance. Additionally, it highlights the need for regular health checks, security reviews, and architecture assessments to ensure system reliability and security.