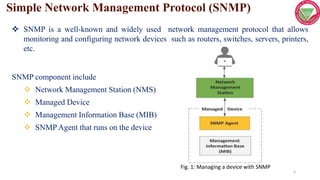
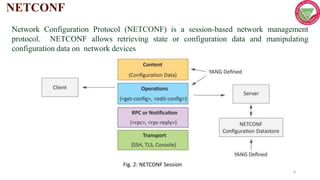
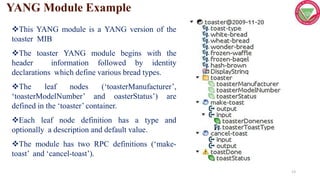
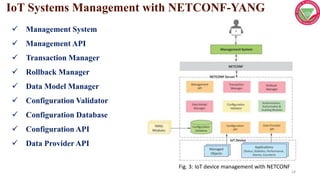
This document discusses managing IoT systems and describes SNMP, NETCONF, and YANG. SNMP allows monitoring and configuring network devices but has limitations. NETCONF is a network configuration protocol that uses XML and SSH for reliable device configuration. YANG is a data modeling language used to define schemas for NETCONF configuration and state data exchange. Together, NETCONF and YANG provide an improved approach for IoT system management.