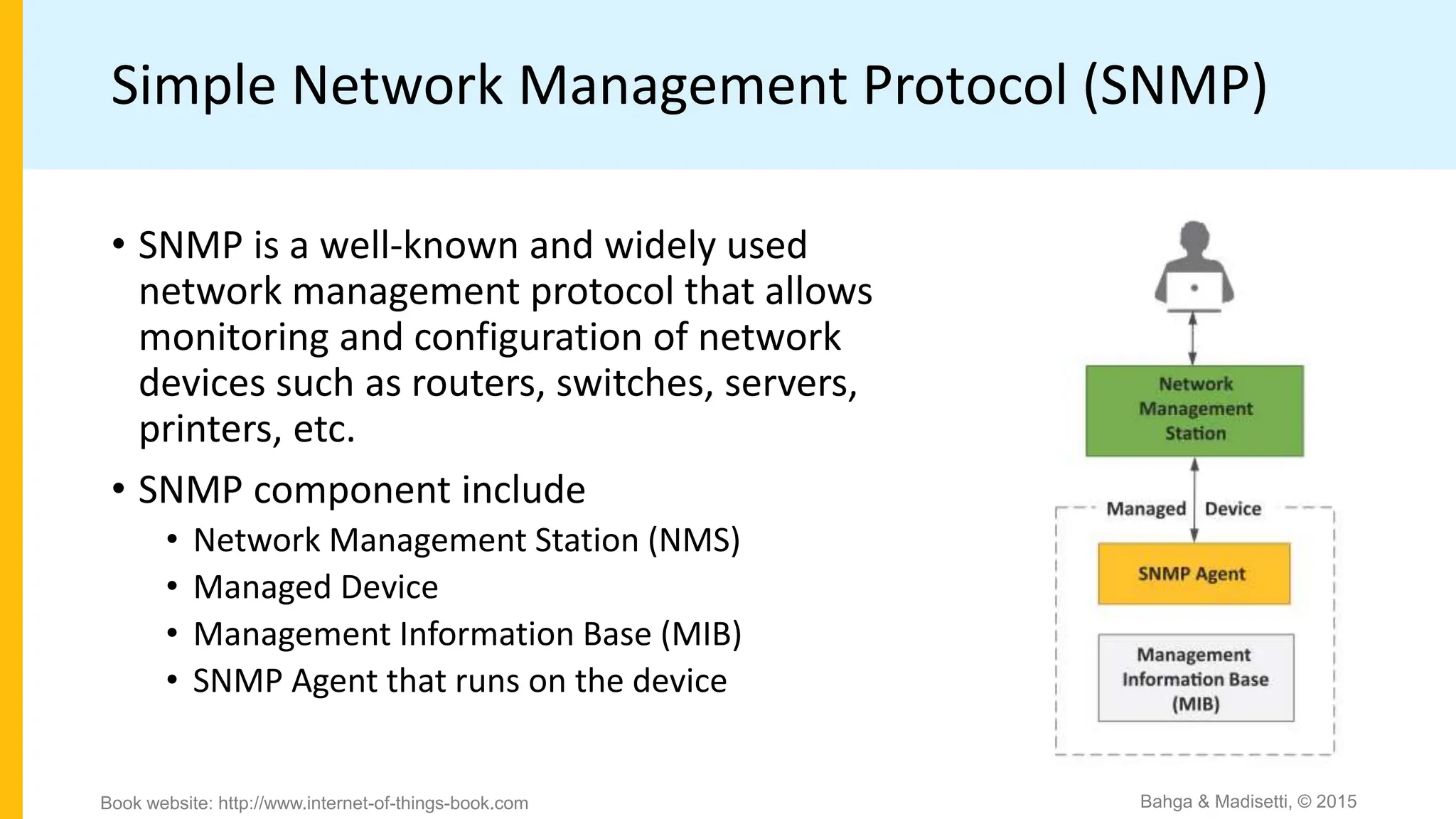
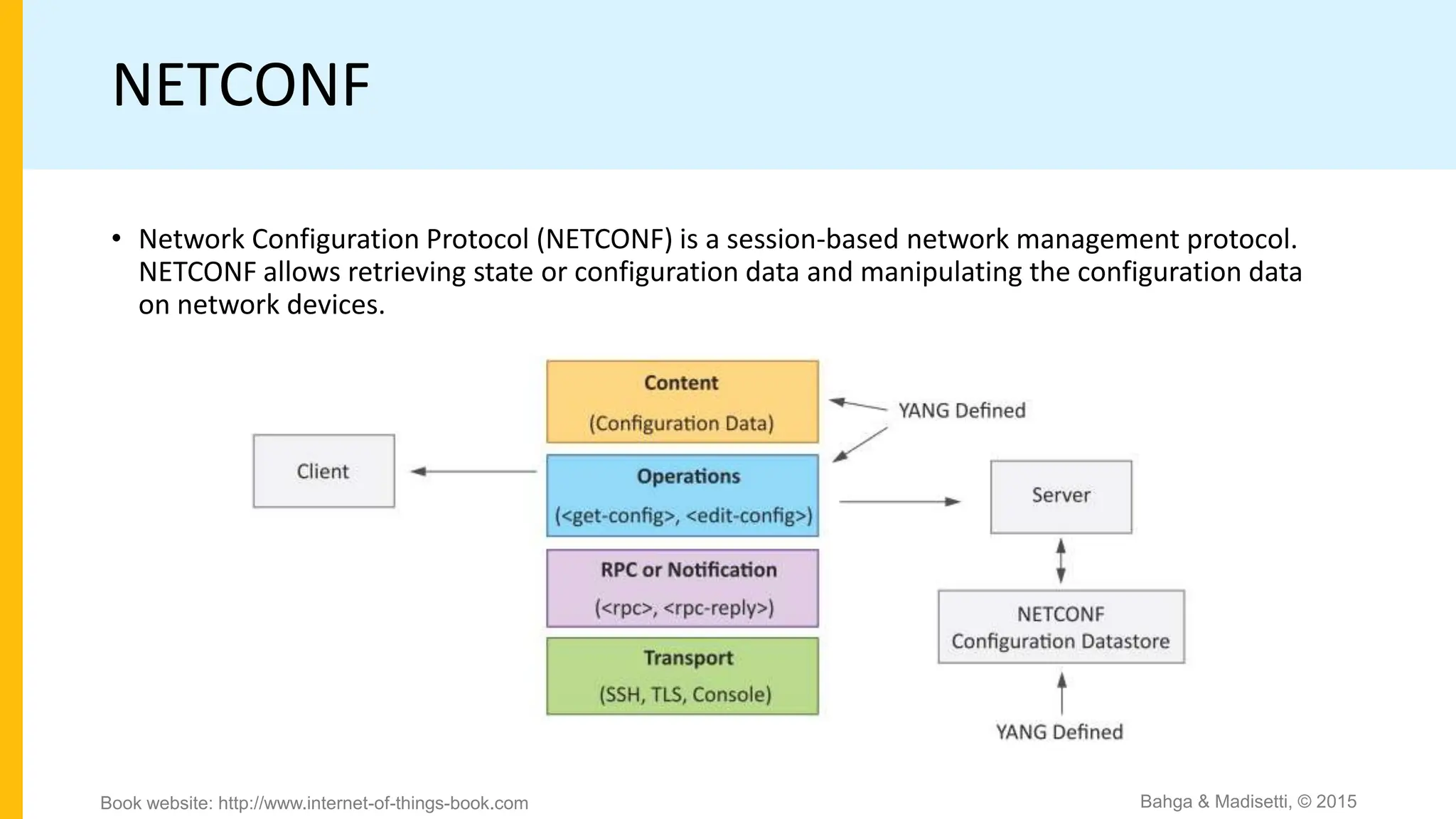
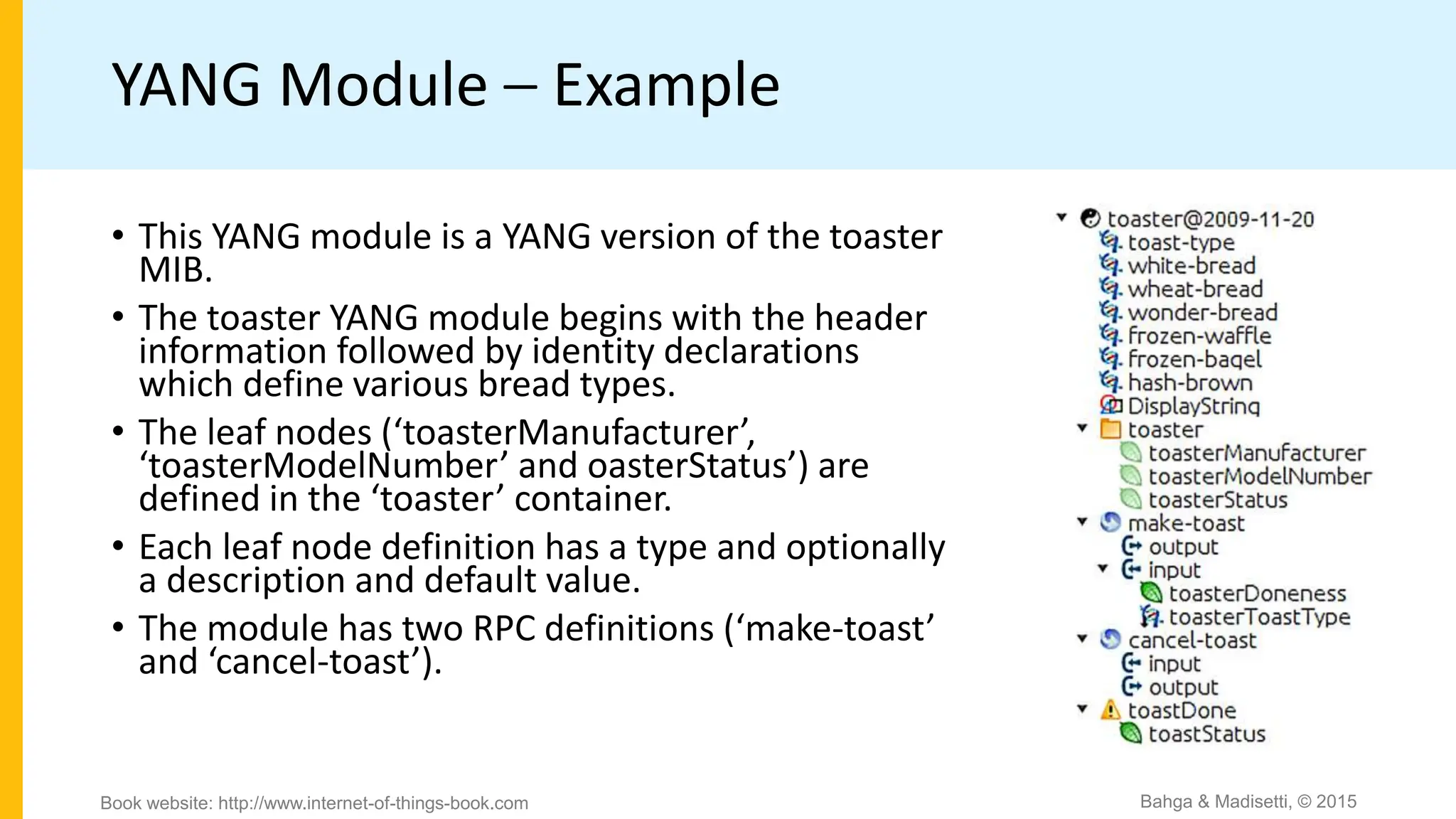
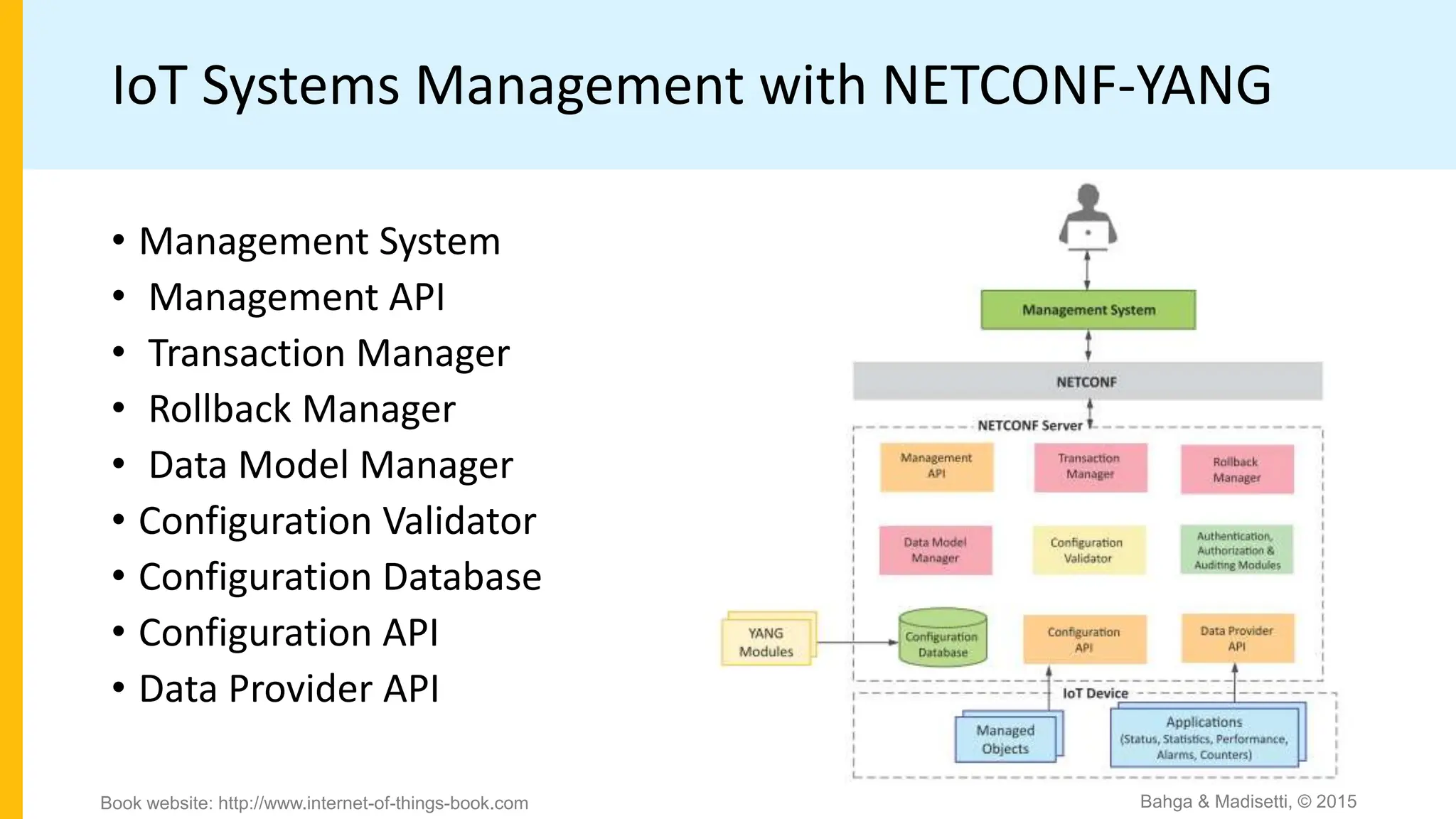
The document discusses IoT system management using NETCONF and YANG. It provides an overview of NETCONF, which is a network configuration protocol that allows retrieving and manipulating configuration data on network devices using XML-encoded RPCs over SSH. YANG is introduced as a data modeling language used to define the schema of configuration and state data exchanged with NETCONF. Examples are provided of a YANG module to model a toaster device and the components involved in an IoT management system that uses NETCONF and YANG.