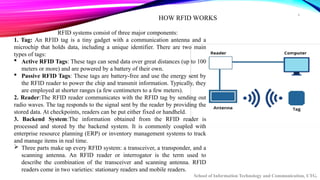
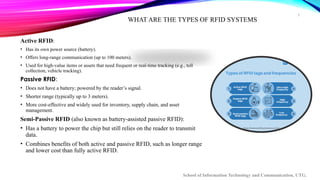
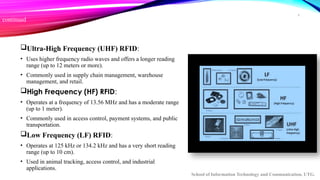
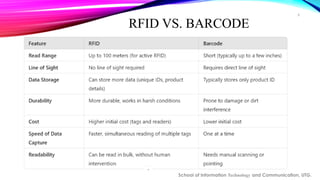
The document provides an overview of Radio Frequency Identification (RFID) technology, including its definition, components, types, applications, challenges, and a comparison with barcodes. RFID systems, which consist of tags, readers, and backend systems, are employed across various industries like retail, logistics, healthcare, and security for automated identification. Despite its advantages, challenges such as cost, privacy concerns, and the complexity of integration remain significant obstacles to widespread adoption.