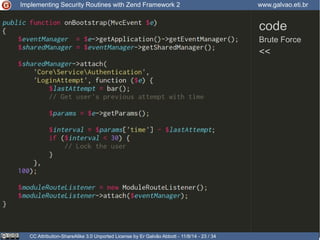
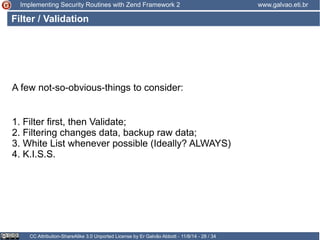
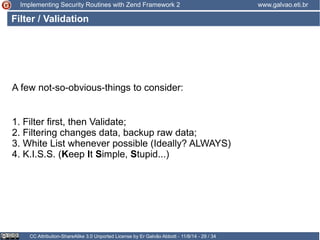
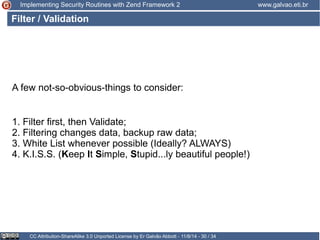
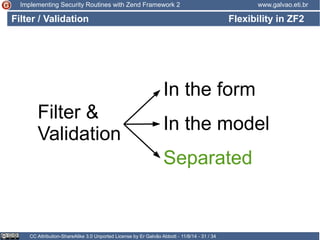
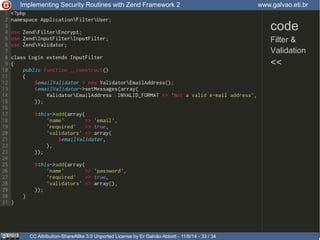
The document discusses implementing security routines in Zend Framework 2, covering topics like authentication, brute force protection, password recovery, cryptography, authorization, and data filtering/validation. It provides code examples and best practices for each topic, such as using services for authentication and cryptography, logging authentication attempts as events, and using the Zend\Permission\Acl component for authorization.







![Implementing Security Routines with Zend Framework 2 www.galvao.eti.br
Let's talk about wheels...
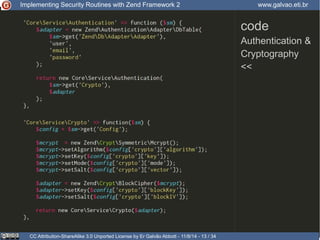
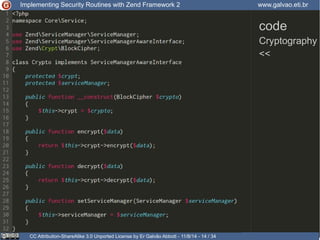
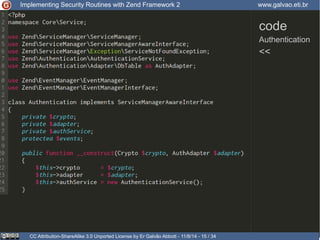
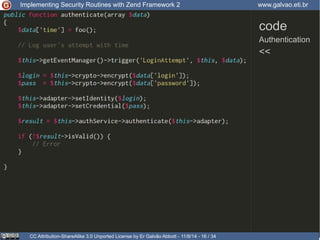
Authentication
If you don't [want to]know much about security...
http://modules.zendframework.com/ZF-Commons/ZfcUser
CC Attribution-ShareAlike 3.0 Unported License by Er Galvão Abbott - 11/8/14 - 9 / 34](https://image.slidesharecdn.com/implementingsecurityroutineswithzf2-141108171752-conversion-gate02/85/Implementing-security-routines-with-zf2-9-320.jpg)
![Implementing Security Routines with Zend Framework 2 www.galvao.eti.br
Let's talk about wheels...
Authentication
If you don't [want to]know much about security...
http://modules.zendframework.com/ZF-Commons/ZfcUser
if you do...
Authentication
Crypt
Filter
Form
CC Attribution-ShareAlike 3.0 Unported License by Er Galvão Abbott - 11/8/14 - 10 / 34](https://image.slidesharecdn.com/implementingsecurityroutineswithzf2-141108171752-conversion-gate02/85/Implementing-security-routines-with-zf2-10-320.jpg)