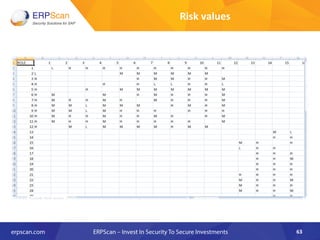
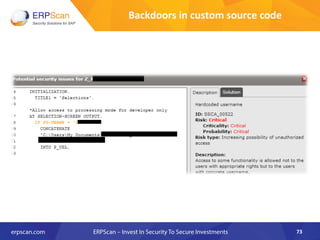
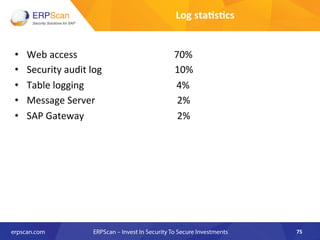
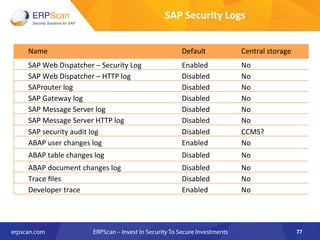
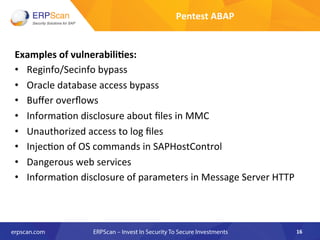
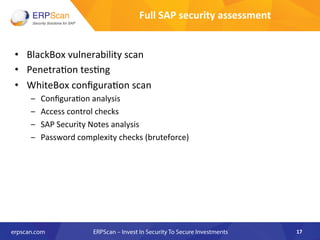
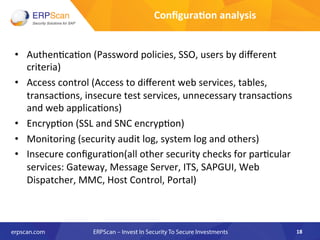
The document outlines the importance of SAP security, detailing the risks associated with various business applications and the need for a structured approach to safeguarding these systems. It emphasizes the implementation of security measures such as penetration testing, compliance checks, and vulnerability assessments to mitigate threats from espionage, sabotage, and fraud. Additionally, the text introduces several guidelines and resources, like ISACA and DSAG, to aid organizations in enhancing their SAP security posture.

















![• Ques'ons
like
"why?"
and
"what
for?"
are
the
alpha
and
omega
of
every
research
• The
most
frequent
ques'on
we
were
asked:
“Guys,
you
are
awesome!
You
are
doing
a
great
job
so
far,
finding
so
many
problems
in
our
installaCons.
It's
absolutely
fantasCc,
but
we
don’t
know
where
to
start
solving
them.
Could
you
provide
us
with
top
10/20/50/100/[your
favorite
number]
most
criCcal
bugs
in
every
area?”
26
Why?
(1)](https://image.slidesharecdn.com/2014cisoplatform-150630121951-lva1-app6891/85/Implementing-SAP-security-in-5-steps-26-320.jpg)
















![• [EASAI-‐NA-‐01]
Component
updates
• [EASAI-‐NA-‐02]
Kernel
updated
What’s
next:
Other
components
should
be
be
updated
separately
–
SAProuter,
SAP
GUI,
SAP
NetWeaver
J2EE,
SAP
BusinessObjects.
Also,
OS
and
database
44
Lack
of
patch
management](https://image.slidesharecdn.com/2014cisoplatform-150630121951-lva1-app6891/85/Implementing-SAP-security-in-5-steps-44-320.jpg)
![• [EASAI-‐NA-‐03]
Default
password
check
for
user
SAP*
• [EASAI-‐NA-‐04]
Default
password
check
for
user
DDIC
• [EASAI-‐NA-‐05]
Default
password
check
for
user
SAPCPIC
• [EASAI-‐NA-‐06]
Default
password
check
for
user
MSADM
• [EASAI-‐NA-‐07]
Default
password
check
for
user
EARLYWATCH
What’s
next:
A
couple
of
addiConal
SAP
components,
like
old
versions
of
SAP
SDM
and
SAP
ITS,
have
default
passwords.
Ajer
you
check
all
default
passwords,
you
can
start
bruteforcing
for
simple
passwords
45
Default
passwords](https://image.slidesharecdn.com/2014cisoplatform-150630121951-lva1-app6891/85/Implementing-SAP-security-in-5-steps-45-320.jpg)
![• [EASAI-‐NA-‐08]
Access
to
RFC-‐func'ons
using
SOAP
interface
• [EASAI-‐NA-‐09]
Access
to
RFC-‐func'ons
using
FORM
interface
• [EASAI-‐NA-‐10]
Access
to
XI
service
using
SOAP
interface
What’s
next:
Analyze
about
1500
other
services
which
are
remotely
enabled
to
see
if
they
are
really
needed.
Disable
unused
transacCons,
programs
and
reports
46
Unnecessary
enabled
func=onality](https://image.slidesharecdn.com/2014cisoplatform-150630121951-lva1-app6891/85/Implementing-SAP-security-in-5-steps-46-320.jpg)
![• [EASAI-‐NA-‐11]
Unauthorized
access
to
SAPControl
service
• [EASAI-‐NA-‐12]
Unauthorized
access
to
SAPHostControl
service
• [EASAI-‐NA-‐13]
Unauthorized
access
to
Message
Server
service
• [EASAI-‐NA-‐14]
Unauthorized
access
to
Oracle
database
What’s
next:
Full
list
of
SAP
services
is
available
here:
TCP/IP
Ports
Used
by
SAP
ApplicaCons.
Also,
take
care
of
3rd
party
services
which
can
be
enabled
on
this
server
47
Open
remote
management
interfaces](https://image.slidesharecdn.com/2014cisoplatform-150630121951-lva1-app6891/85/Implementing-SAP-security-in-5-steps-47-320.jpg)
![• [EASAI-‐NA-‐15]
Minimum
password
length
• [EASAI-‐NA-‐16]
User
locking
policy
• [EASAI-‐NA-‐17]
Password
compliance
to
current
standards
• [EASAI-‐NA-‐18]
Access
control
to
RFC
(reginfo.dat)
• [EASAI-‐NA-‐19]
Access
control
to
RFC
(secinfo.dat)
What’s
next:
First
of
all,
look
to
Secure
ConfiguraCon
of
SAP
NetWeaver®
ApplicaCon
Server
Using
ABAP
for
detailed
configuraCon
checks.
Ajerwards,
pass
through
detailed
documents
for
each
and
every
SAP
service
and
module
h4p://help.sap.com/saphelp_nw70/helpdata/en/8c/
2ec59131d7f84ea514a67d628925a9/frameset.htm
48
Insecure
configura=on](https://image.slidesharecdn.com/2014cisoplatform-150630121951-lva1-app6891/85/Implementing-SAP-security-in-5-steps-48-320.jpg)
![• [EASAI-‐NA-‐20]
Users
with
SAP_ALL
profile
• [EASAI-‐NA-‐21]
Users
which
can
run
any
program
• [EASAI-‐NA-‐22]
Users
which
can
modify
cri'cal
table
USR02
• [EASAI-‐NA-‐23]
Users
which
can
execute
any
OS
command
• [EASAI-‐NA-‐24]
Disabled
authoriza'on
checks
What’s
next:
There
are
at
least
100
criCcal
transacCons
only
in
BASIS
and
approximately
the
same
number
in
any
other
module.
Detailed
informaCon
can
be
found
in
ISACA
guidelines.
Ajer
that,
you
can
start
SegregaCon
of
DuCes
49
Access
control
and
SoD
conflicts](https://image.slidesharecdn.com/2014cisoplatform-150630121951-lva1-app6891/85/Implementing-SAP-security-in-5-steps-49-320.jpg)
![• [EASAI-‐NA-‐25]
Use
of
SSL
for
securing
HTTP
connec'ons
• [EASAI-‐NA-‐26]
Use
of
SNC
for
securing
SAP
GUI
connec'ons
• [EASAI-‐NA-‐27]
Use
of
SNC
for
securing
RFC
connec'ons
What’s
next:
Even
if
you
use
encrypCon,
check
how
it
is
configured
for
every
encrypCon
type
and
for
every
service
because
there
are
different
complex
configuraCons
for
each
encrypCon
type.
For
example,
the
latest
a4acks
on
SSL
(BEAST
and
CRIME)
require
companies
to
use
more
complex
SSL
configuraCons
50
Unencrypted
connec=ons](https://image.slidesharecdn.com/2014cisoplatform-150630121951-lva1-app6891/85/Implementing-SAP-security-in-5-steps-50-320.jpg)
![• [EASAI-‐NA-‐28]
RFC
connec'ons
with
stored
authen'ca'on
data
• [EASAI-‐NA-‐29]
Trusted
systems
with
lower
security
What’s
next:
Check
other
ways
to
get
access
to
trusted
systems,
such
as
database
links,
use
of
the
same
OS
user,
or
use
of
similar
passwords
for
different
systems
51
Insecure
trusted
connec=ons](https://image.slidesharecdn.com/2014cisoplatform-150630121951-lva1-app6891/85/Implementing-SAP-security-in-5-steps-51-320.jpg)
![• [EASAI-‐NA-‐30]
Logging
of
security
events
• [EASAI-‐NA-‐31]
Logging
of
HTTP
requests
• [EASAI-‐NA-‐32]
Logging
of
table
changes
• [EASAI-‐NA-‐33]
Logging
of
access
to
Gateway
What’s
next:
There
are
about
30
different
types
of
log
files
in
SAP.
Upon
properly
enabling
the
main
ones,
you
should
properly
configure
complex
opCons,
such
as
which
specific
tables
to
monitor
for
changes,
what
kind
of
events
to
analyze
in
security
events
log,
what
types
of
Gateway
a4acks
should
be
collected.
Next
step
is
to
enable
their
centralized
collecCon
and
storage
and
then
add
other
log
events
52
Logging
and
monitoring](https://image.slidesharecdn.com/2014cisoplatform-150630121951-lva1-app6891/85/Implementing-SAP-security-in-5-steps-52-320.jpg)