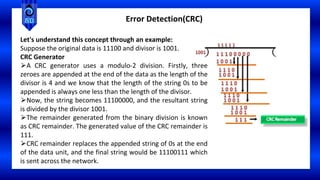
This document provides an overview of data link layer concepts including error control, flow control, error detection, error correction, and elementary data link protocols. It discusses the purposes and examples of error control using ARQ, flow control to prevent receiver overload, and various error detection techniques like parity checks, checksums, and cyclic redundancy checks (CRCs). Error correction codes are also introduced for detecting and correcting errors using additional redundant bits. Common data link protocols like stop-and-wait and sliding window protocols are listed for discussion in the course.