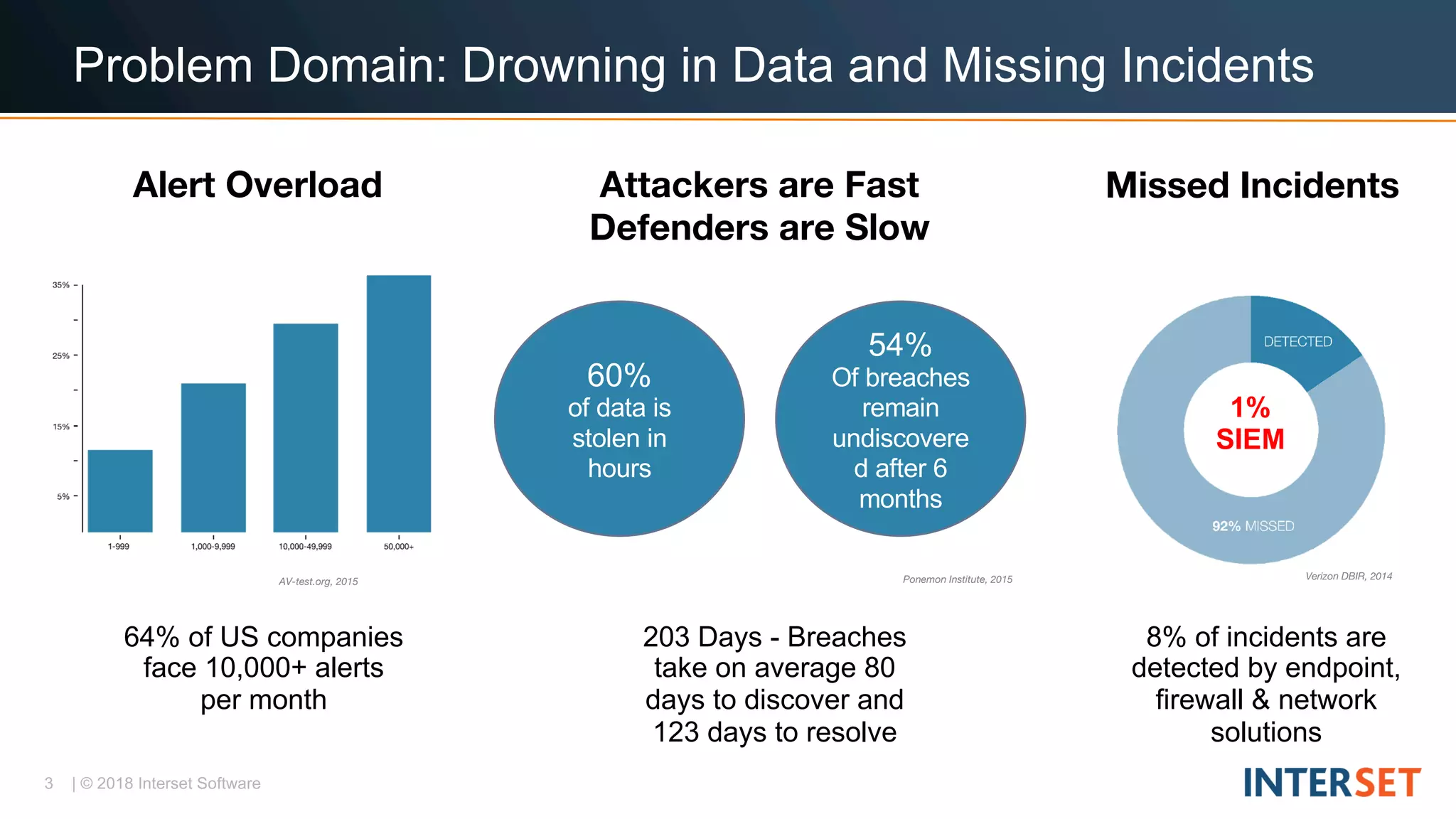
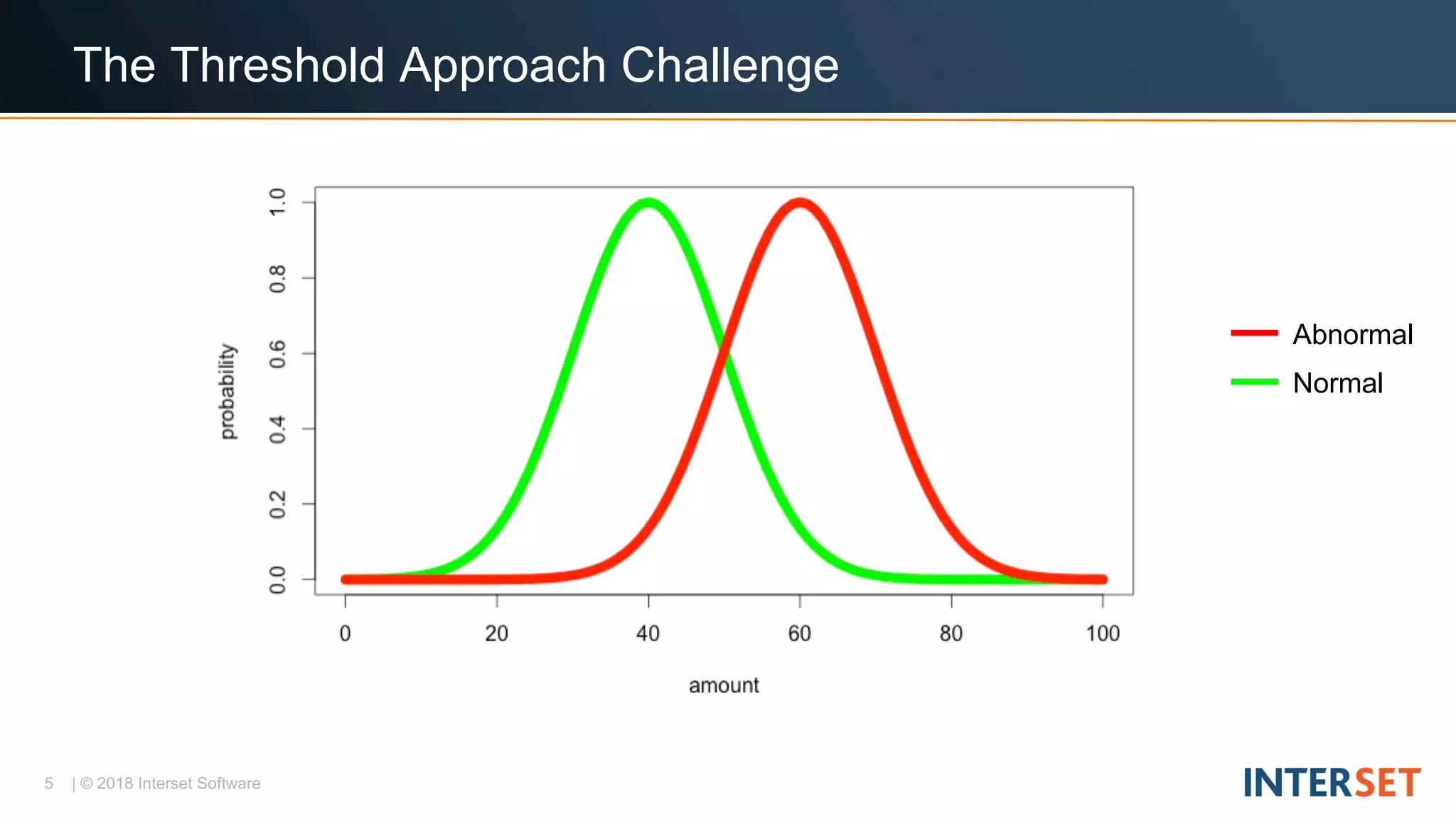
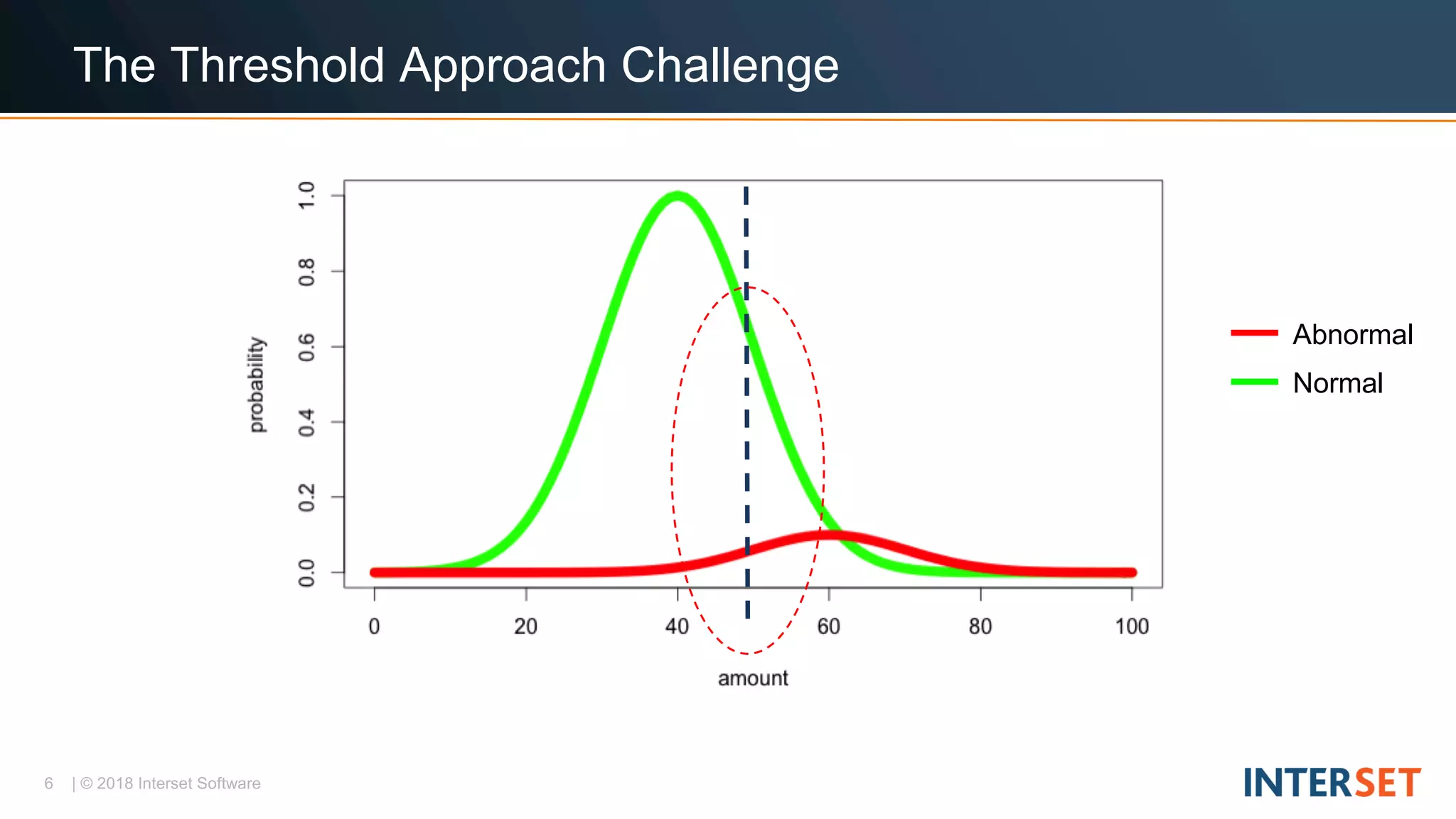
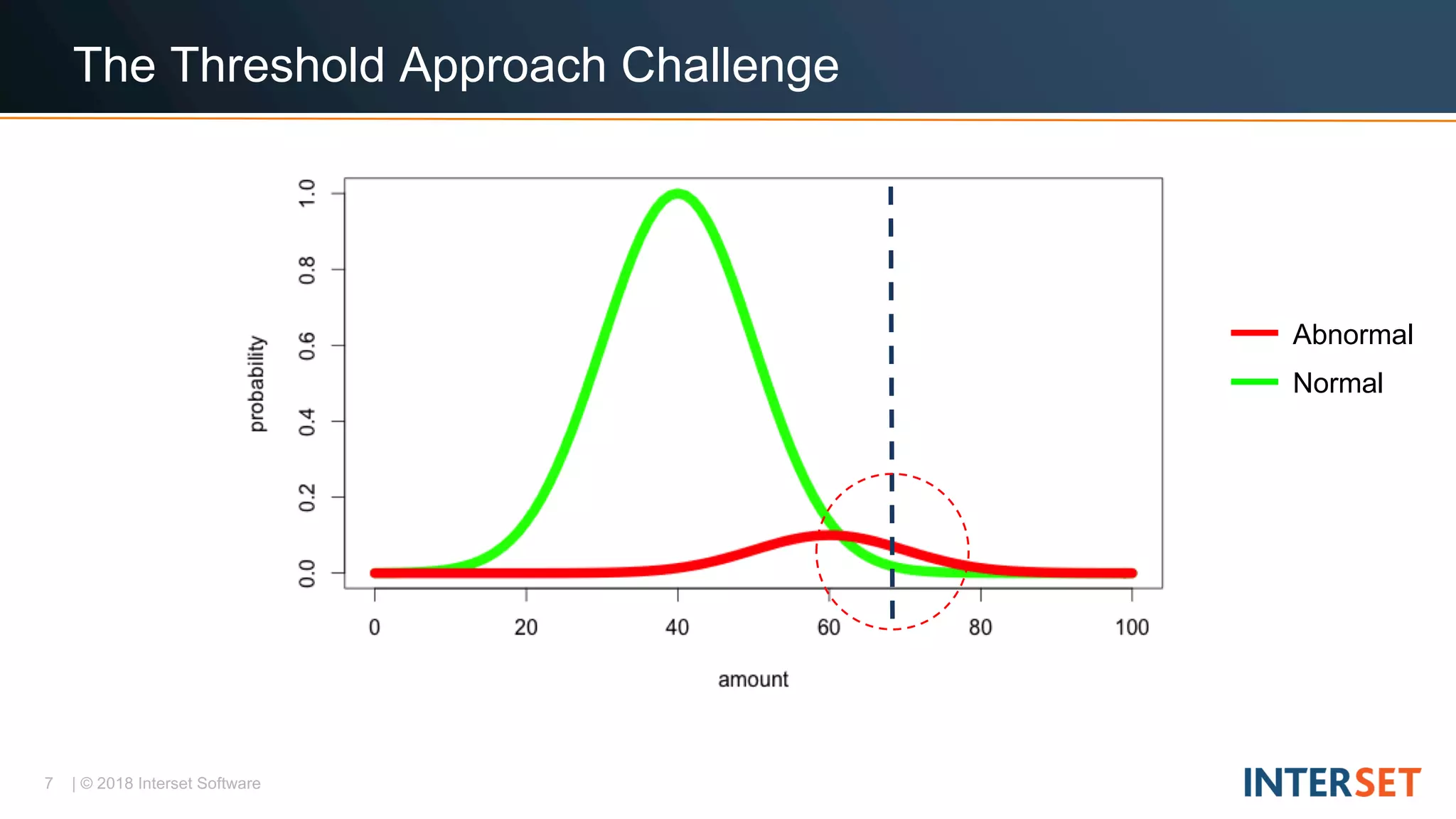
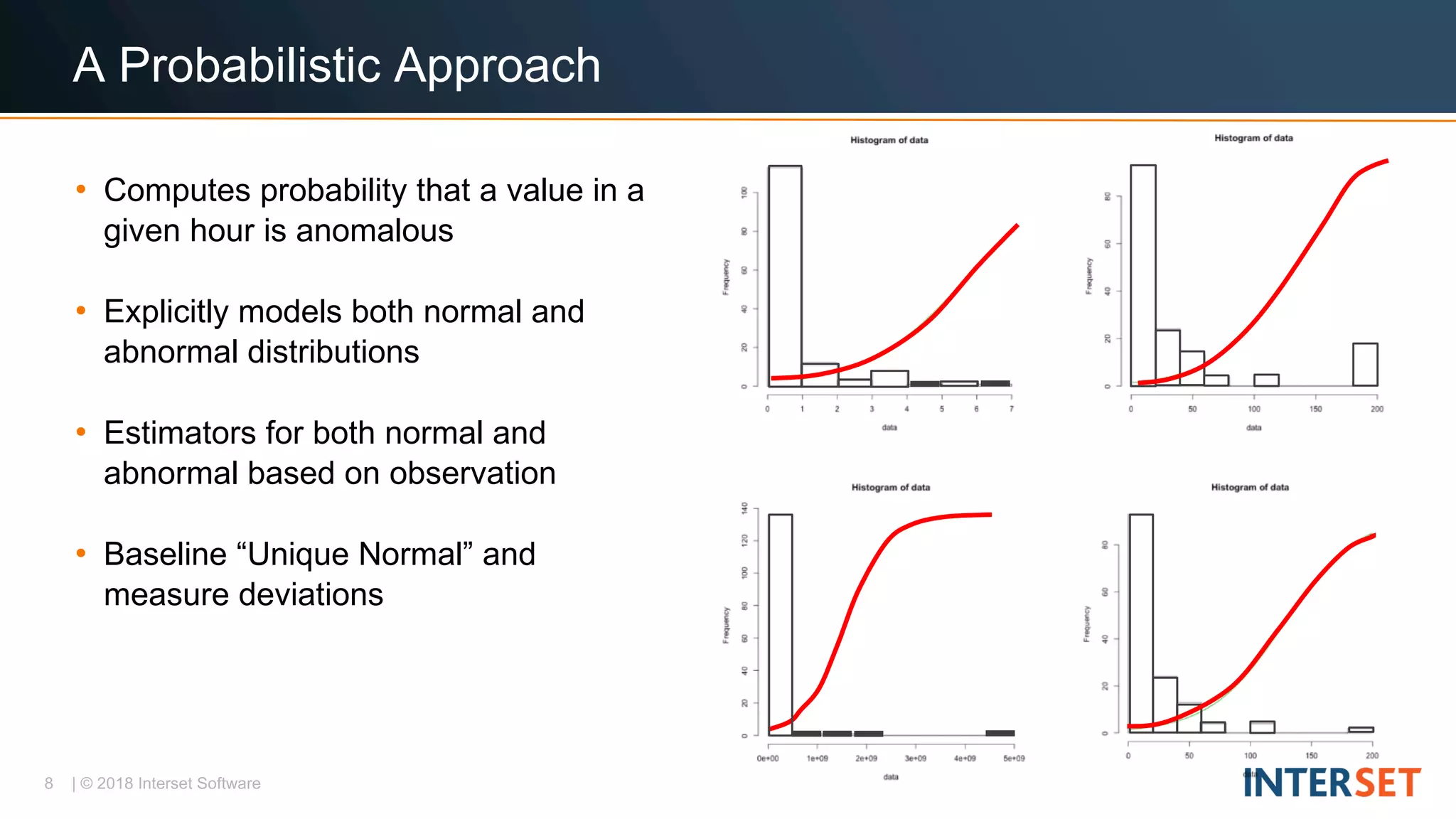
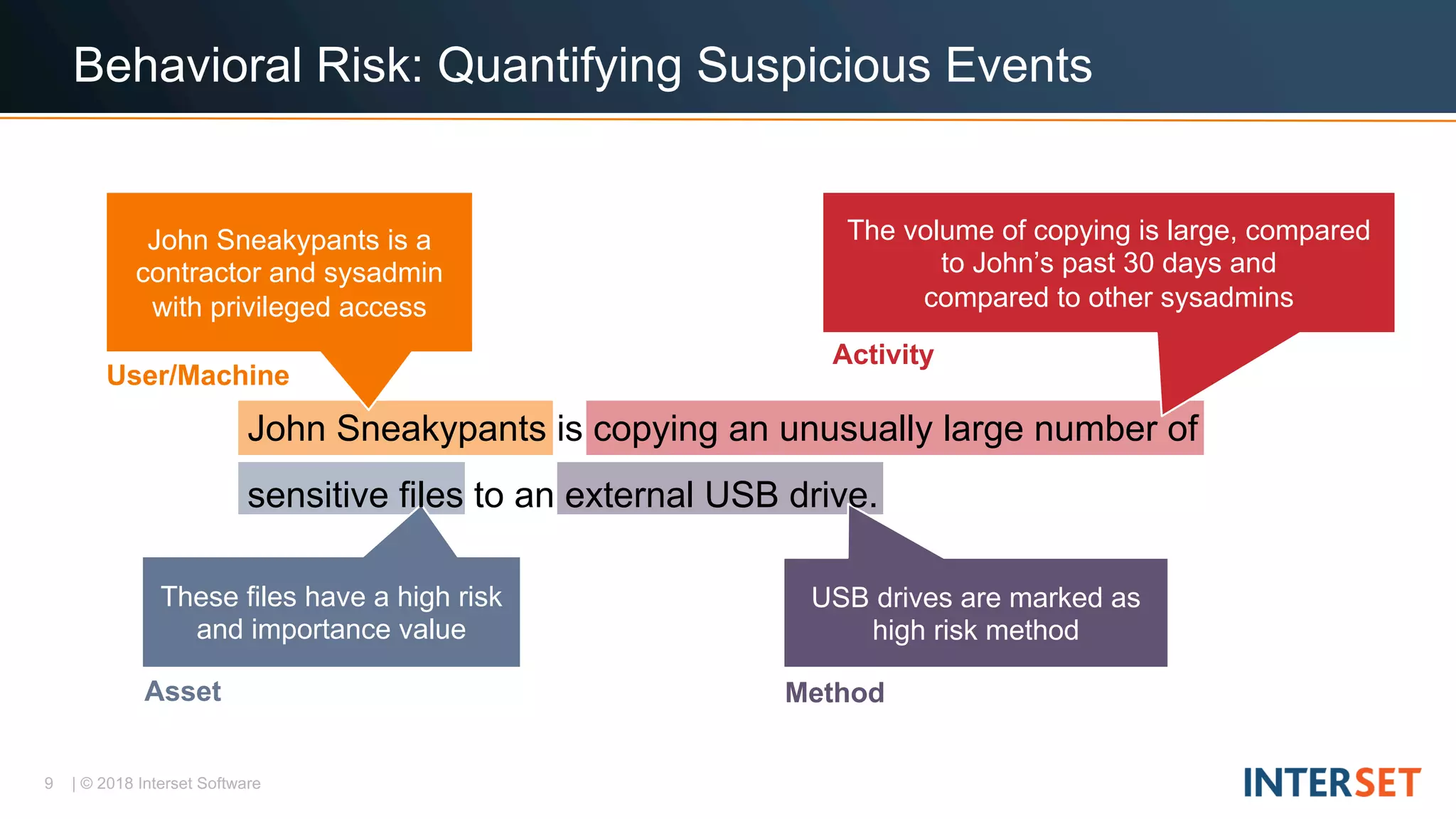
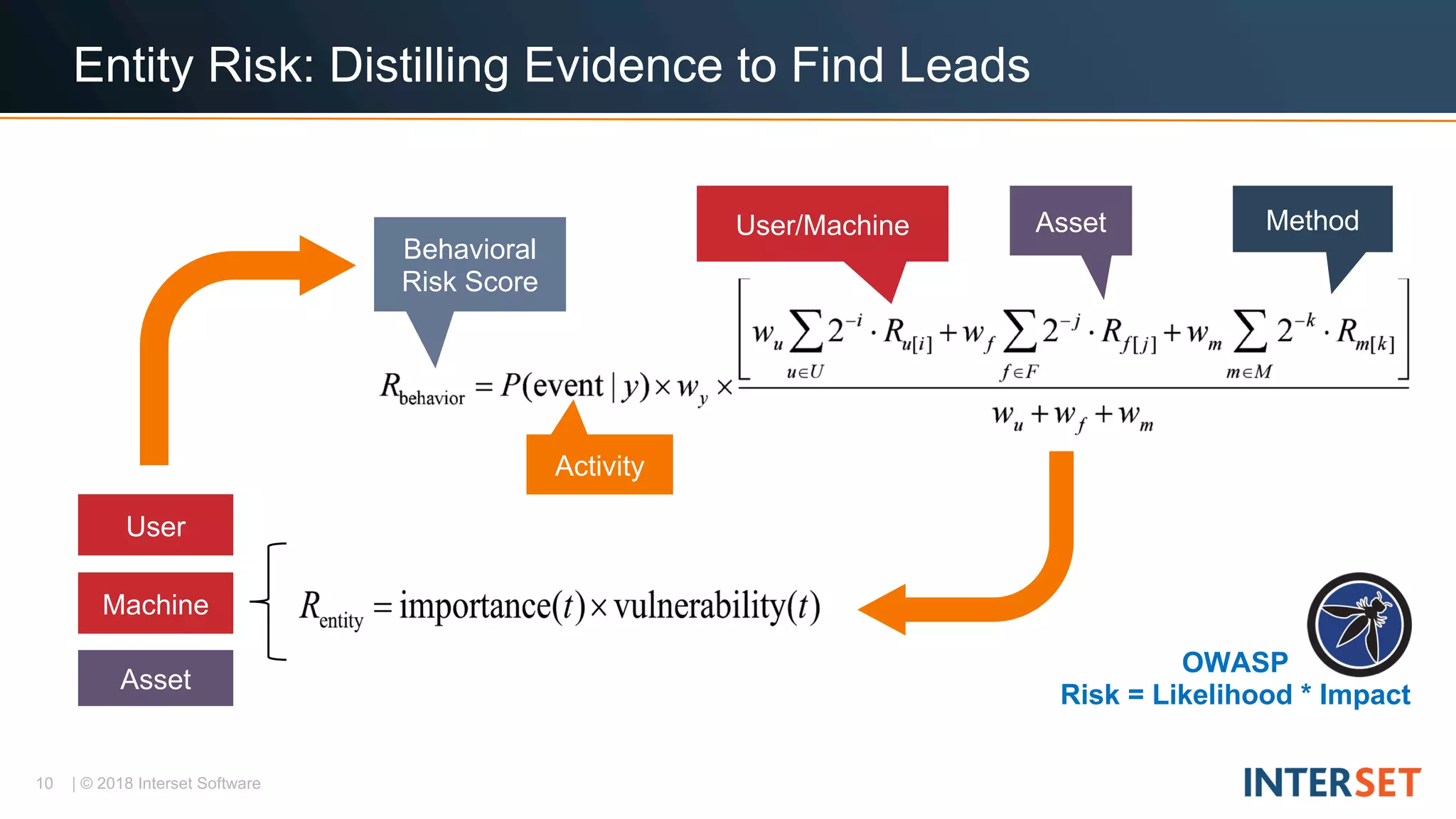
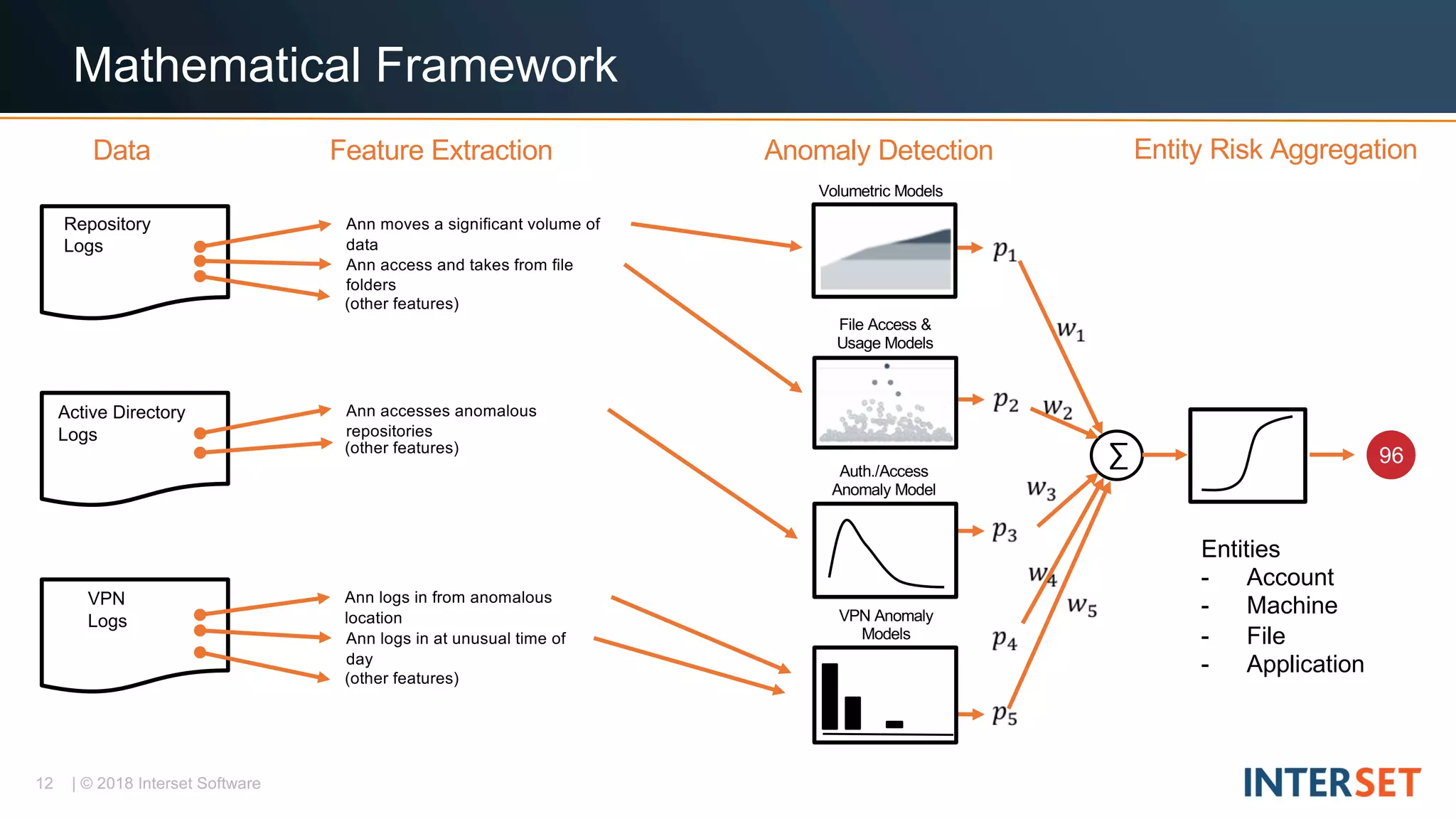
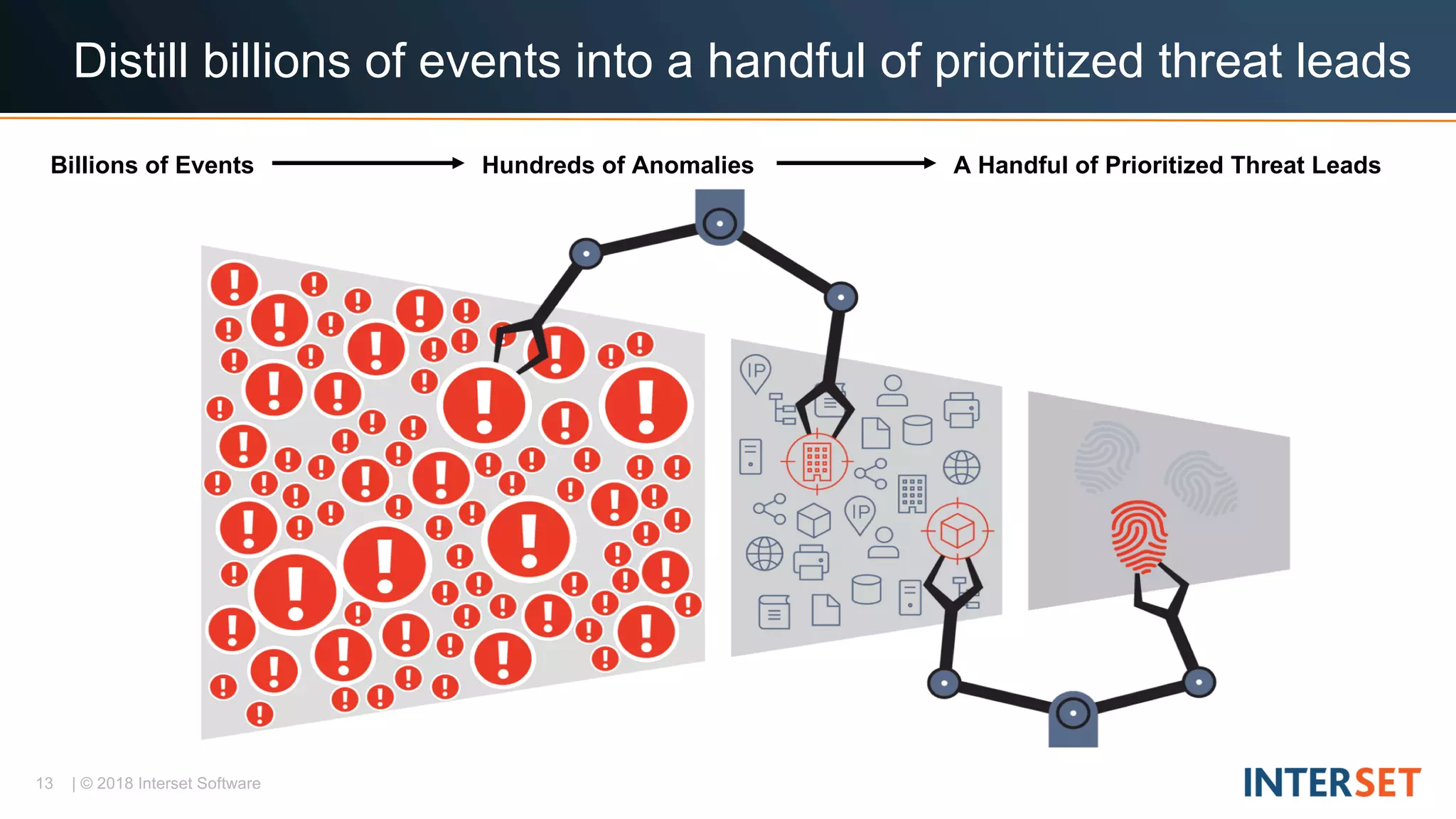
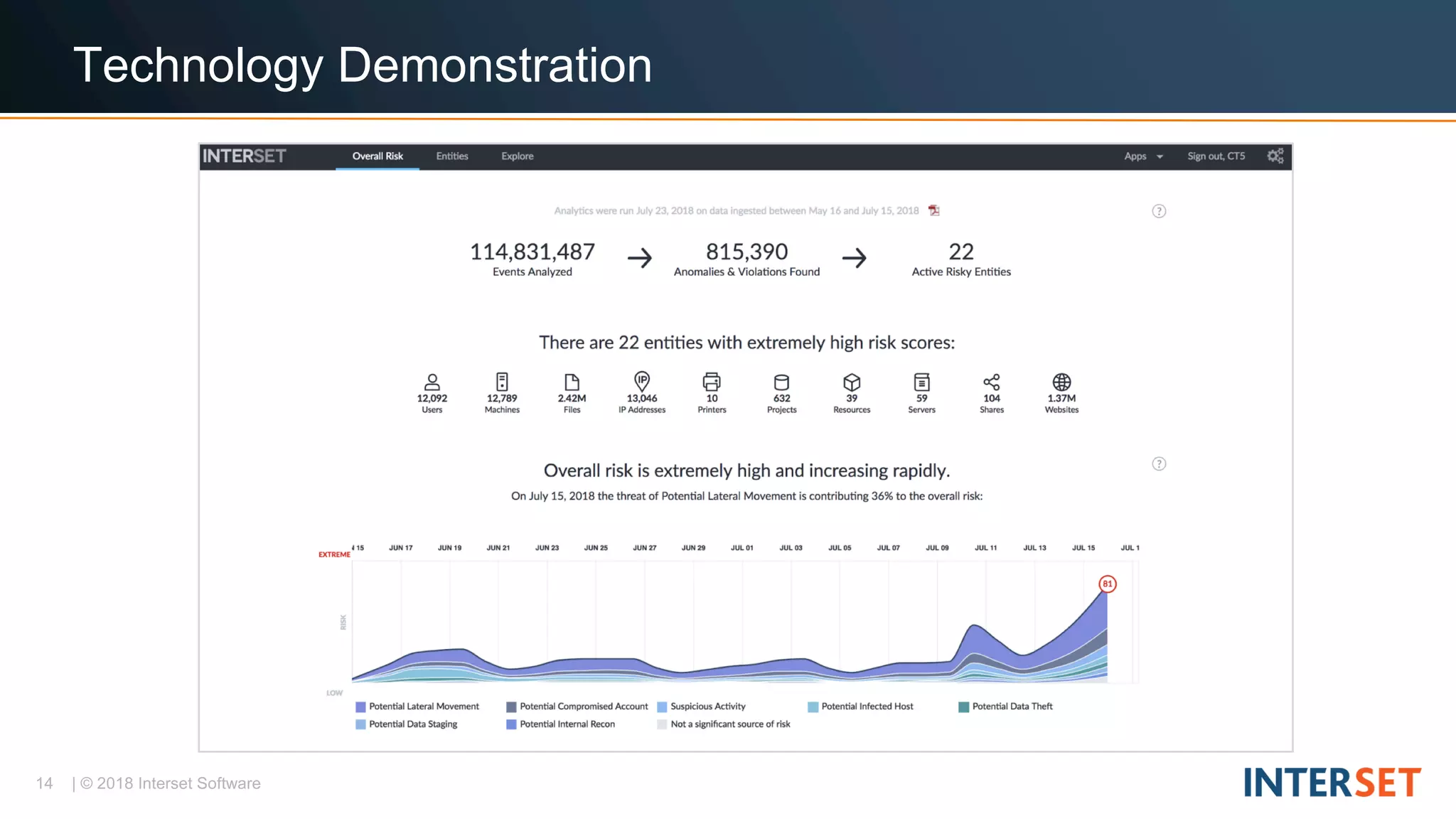
The document discusses operationalizing big data security analytics. It notes that attackers are fast while defenders are slow, with many security alerts overwhelming analysts. A standard rules-based approach to detecting anomalies is challenged by abnormalities appearing normal. The document proposes a probabilistic approach that models both normal and abnormal distributions to better detect anomalies. It describes using behavioral risk scoring to quantify suspicious user activities and entity risk aggregation to distill billions of events into a handful of prioritized leads for further analysis.