This document provides guidance on identifying and preventing the spread of malware through emails. It discusses how malicious emails try to trick recipients through spoofing, phishing links and attachments. Examples are given of common types of malicious emails, like those disguised as package tracking notifications but containing viruses. The document advises users to be wary of emails from unknown senders or containing strange formatting, links or large attachments meant to infect computers. Proper precautions can help safeguard systems from data loss or theft resulting from malware spread through emails.
![1
[Type the company name]
Triboro Safe Email and
Computer Practices
A guide to understanding Malware and
preventing the spread of computer
viruses.
Triboro Quilt Manufacturing Information Services Department
2/28/2014](https://image.slidesharecdn.com/ed383abd-9afc-4271-983f-b65da937c784-160801214957/75/Safe-Email-Practices-1-2048.jpg)


![4
The Anatomy of an Email message
This is an example of an honest email message between two recipients. When viewed the Message Header.
This is what the real message looks like when it is received by the recipient’s mail server.
Return-Path: <lzacharias@triboro.com>
Received: from mail2.aceinnovative.com ([unix socket])
by mail2 with LMTPA;
Tue, 25 Feb 2014 13:37:08 -0500
X-Sieve: CMU Sieve 2.3
Received: from mail1.aceinnovative.com (mail1.aceinnovative.com [66.114.74.12])
by mail2.aceinnovative.com (8.13.8/8.13.8) with ESMTP id s1PIb1ZP017496
for <jslavin@cuddletime.com>; Tue, 25 Feb 2014 13:37:01 -0500
Received: from B042VF1LD (static-72-68-128-74.nycmny.fios.verizon.net [72.68.128.74])
(authenticated bits=0)
by mail1.aceinnovative.com (8.13.8/8.13.8) with ESMTP id s1PIb19X016315
for <jslavin@triboro.com>; Tue, 25 Feb 2014 13:37:01 -0500
Reply-To: <lzacharias@triboro.com>
From: "Lindsey Zacharias" <lzacharias@triboro.com>
To: <jslavin@triboro.com>
Subject: test
Date: Tue, 25 Feb 2014 13:37:01 -0500
Organization: Triboro Quilt Mgf. Corp.
Message-ID: <003e01cf3258$92d97770$b88c6650$@com>
MIME-Version: 1.0
Content-Type: multipart/alternative;
boundary="----=_NextPart_000_003F_01CF322E.AA036F70"
X-Mailer: Microsoft Office Outlook 12.0
Thread-Index: Ac8yWJK6bNzYjaHlSiydjqqVxgDIkQ==
Content-Language: en-us
X-Spam-Status-Local: No (-970/50)
Anatomy of malicious and erroneous emails
Recently many employees have received an increased level of emails from unknown senders that contained
questionable content, such as attached zip files, foul and inappropriate material, or embedded web site links.
What type of email to look out for?
Normally email messages are from a known sender such as a purchase confirmation, from a family, friend, and or a
business contact. On the other hand you could receive a message in your inbox that does not look just right. When this
does happen be on the alert and not open the email. The sender will attempt to trick you into opening and reading the
message content.
How to distinguish a fake email?
Emails with the intention of doing harm are sent from a Bank or Express Mail shipping service that might have been
“spoofed” or commandeered to hide the true sender’s address that is relying on the lazy habits of the reader, to trick
them into thinking the email is from a legitimate source. The intentions of such a letter are an attempt to infiltrate your
PC to install software as a means to gain unauthorized access to it and the network that it associated with if it is
attached to a corporate domain.](https://image.slidesharecdn.com/ed383abd-9afc-4271-983f-b65da937c784-160801214957/85/Safe-Email-Practices-4-320.jpg)

![7
Not a Triboro site
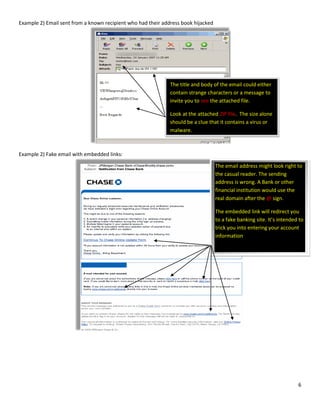
Example 4) Email sent from a fake administrator’s account that contains improper English.
From: Admin@cuddletime.com
Sent: Tuesday, October 30, 2012 10:20 AM
Subject: Important Message From Helpdesk!!
Dear Email Owner (Email Owner? Who says that?)
You have exceeded the limit of your mailbox set by our IT
Service, and from now you cannot be receiving (you
cannot be receiving?) all incoming emails and also
some of your outgoing emails will not be delivered and LASTLY, your account will be 'DE-
ACTIVATED' within 24 hours from now. To prevent this, you are advised to click on the link below to
reset your account. Failure to do this, will result to (will result to?) limited access to your mailbox
while your account will remain IN-ACTIVE within the next 24 hours. Click link:
https://mail.cuddletime.net/blah%20blah%20blah
Thanks for letting us serve you better!
Regards,
Management.
Upgrade Department (Upgrade Department?)
This email message is for the sole use of the intended recipient(s) and may contain confidential and privileged information. Any unauthorized review, use,
disclosure or distribution is prohibited. If you are not the intended recipient, please contact the sender by reply email and destroy all copies of the original message.
If you are the intended recipient, please be advised that the content of this message is subject to access, review and disclosure by the sender's Email System
Administrator.
IRS Circular 230 disclosure: To ensure compliance with requirements imposed by the IRS, we inform you that any U.S. federal tax advice contained in this
communication (including any attachment) is not intended or written by us to be used, and cannot be used, (i) by any taxpayer for the purpose of avoiding tax
penalties under the Internal Revenue Code or (ii) for promoting, marketing or recommending to another party any transaction or matter addressed herein.
Example viewing the Message Header of a spoof email.
Return-Path: <AmericanExpress@welcome.aexp.com>
Received: from mail2.aceinnovative.com ([unix socket])
by mail2 with LMTPA;
Mon, 18 Nov 2013 10:56:07 -0500
X-Sieve: CMU Sieve 2.3
The title of the email could look harmless
and get you to read it. Don’t be fooled!
Why would Admin@cuddletime.com
send you a Help Desk message? We do
not have an email address in our
system called Administrator or Admin
@cuddletime
It appears that this email was written
by someone who has a poor grasp of
the English Language. That alone
should be a warning sign.
Foreign Computer criminals will include official looking water
marks. Look closely, what does this email have to do with Internal
Revenue Service?](https://image.slidesharecdn.com/ed383abd-9afc-4271-983f-b65da937c784-160801214957/85/Safe-Email-Practices-7-320.jpg)
![8
Received: from mail1.aceinnovative.com (mail1.aceinnovative.com [66.114.74.12])
by mail2.aceinnovative.com (8.13.8/8.13.8) with ESMTP id rAIFu0k9010009;
Mon, 18 Nov 2013 10:56:00 -0500
Received: from [38.104.61.38] ([38.104.61.38])
by mail1.aceinnovative.com (8.13.8/8.13.8) with ESMTP id rAIFtx80015649;
Mon, 18 Nov 2013 10:55:59 -0500
Received: from [252.133.121.214] (port=47689 helo=[192.168.6.08]) by 38.104.61.38 with asmtp id 1rqLaL-00048-00 for
aasrar@cuddletime.com; Mon, 18 Nov 2013 09:55:58 -0600
Message-ID: <528A37D5.6080609@cuddletime.com>
Date: Mon, 18 Nov 2013 09:55:58 -0600
From: "DocuCentre-IV" <fxC4477@cuddletime.com>
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:7.0.1) Gecko/20110929 Thunderbird/7.0.1
MIME-Version: 1.0
To: aasrar@cuddletime.com
Subject: Scan Data
Content-Type: multipart/mixed;
boundary="----=_Part_52620_4226026627.0566228937852"
X-Spam: Not detected
X-Mras: Ok
X-Badrcpts-Local: 7
X-Spam-Status-Local: No (-450/50)
The same message when viewed in the in the receiver's inbox.
Procedures to Decipher and remove malicious emails
The following procedures should be followed in order to safeguard your computer and the office network that includes
other user computers and file servers.
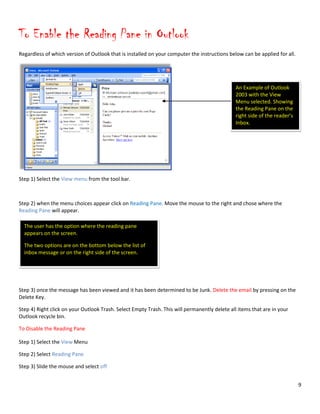
When you receive a questionable email in Outlook you should change the settings to enable the Reading Pane. The
default behavior of viewing emails under the reading pane is “not read”. Outlook treats the message as not read and
you can then decide to delete the message from your inbox and PC.](https://image.slidesharecdn.com/ed383abd-9afc-4271-983f-b65da937c784-160801214957/85/Safe-Email-Practices-8-320.jpg)