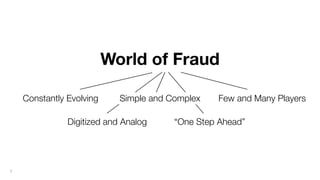
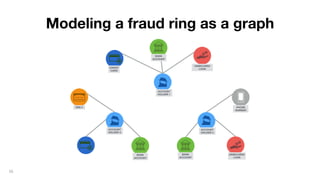
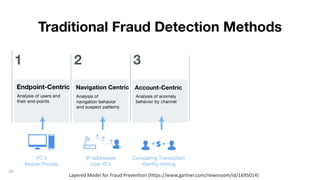
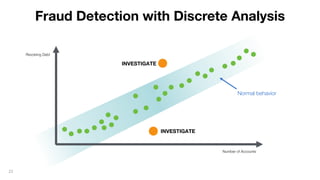
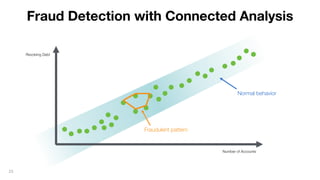
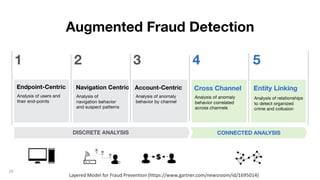
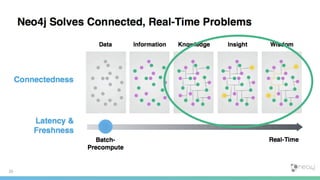
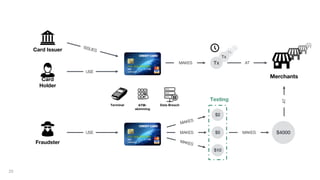
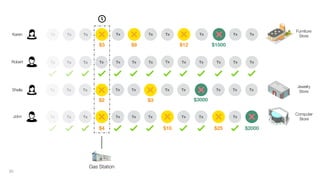
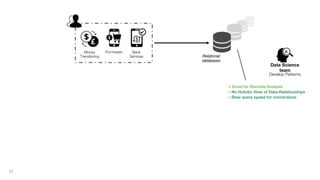
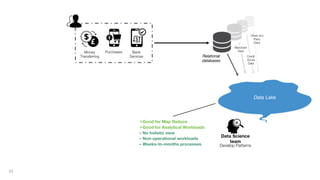
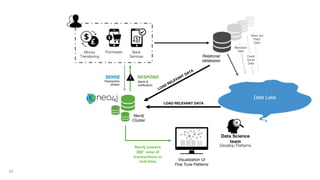
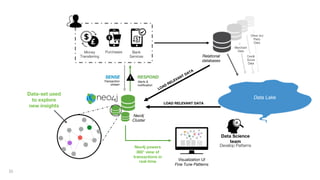
This document discusses how to build a fraud detection solution using Neo4j graph database. It covers typical fraudsters and types of fraud, challenges with traditional fraud detection methods, and how graph databases can provide a more holistic view of relationships to better detect fraud rings and organized crime. The document also outlines a typical fraud detection architecture with Neo4j at the core to power a 360-degree view of transactions in real-time and help detect patterns. It concludes with a demo and Q&A section.